You may have heard that Samsung Push is an incredible service that all Android users absolutely love. For one, Push provides extremely useful notifications for Samsung apps to assist you in all aspects of your life.

While there are many good reasons to update to Apple's newest mobile software, a bug has made it to where you may want to double-check your iCloud settings after doing so.

As you may have heard, Verizon has jumped on the "giving up users' data to whomever will pay" bandwagon with its new AppFlash spyware app that's all set to be pre-installed on at least one of the Android phones they sell.
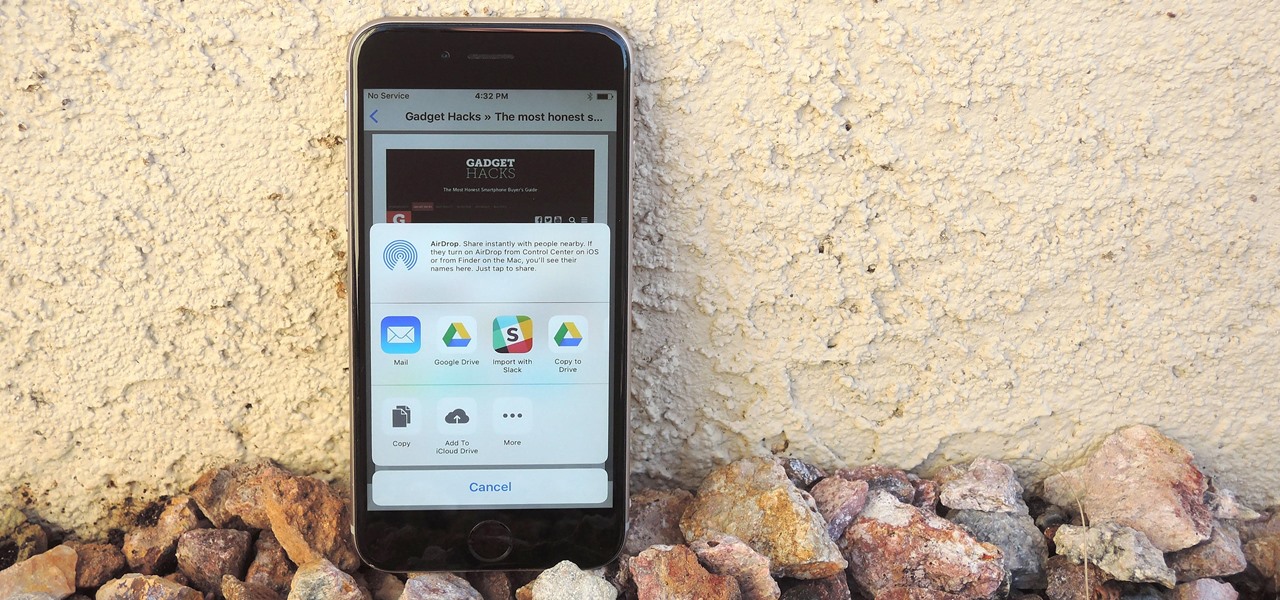
Apple lets you save webpages as PDF files in iOS 10, but the only obvious way to do this is by using iBooks. The thing is, most people would probably rather save their PDFs to a service like Google Drive or Dropbox to make sharing a bit easier. Plus, iBooks isn't officially available for Windows or Android, so there are some cross-platform problems there, too.
The next generation in mobile communications has officially arrived. A new "Universal Profile" was just published to help carriers and OEMs enable Rich Communication Services (RCS) on any of their smartphones, and the standard hopes to replace SMS with a feature-rich, iMessage-like experience on all phones.

No matter how far technology advances, battery life continues to be an issue. Powerful new hardware is introduced each year, but smartphone batteries only get a few extra milliamp-hours to compensate.

Google Maps, once considered superior to Apple Maps, has contributed to a terrible mistake for one woman. A group of demolition workers in Texas were using the service to find a worksite, and to the dismay of homeowner Lindsay Diaz, Google was entirely inaccurate.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

Recently the newly famous ProtonMail service was under attack by DDoS attack. This attack was believed to be the hacking group Armada Collective.

When I started to go to this site I found it fascinating and found myself coming here all day I have used a lot of the info I have gotten from here in my professional career and on my own. I currently am the VP of RND for a small IT company. I have been pushing toward Penetration Testing as a service for our clients and future clients. For the past 10 years here it has been a very long uphill battle and have hit a lot of road blocks. So I decided to work on this on my own of course as soon as...

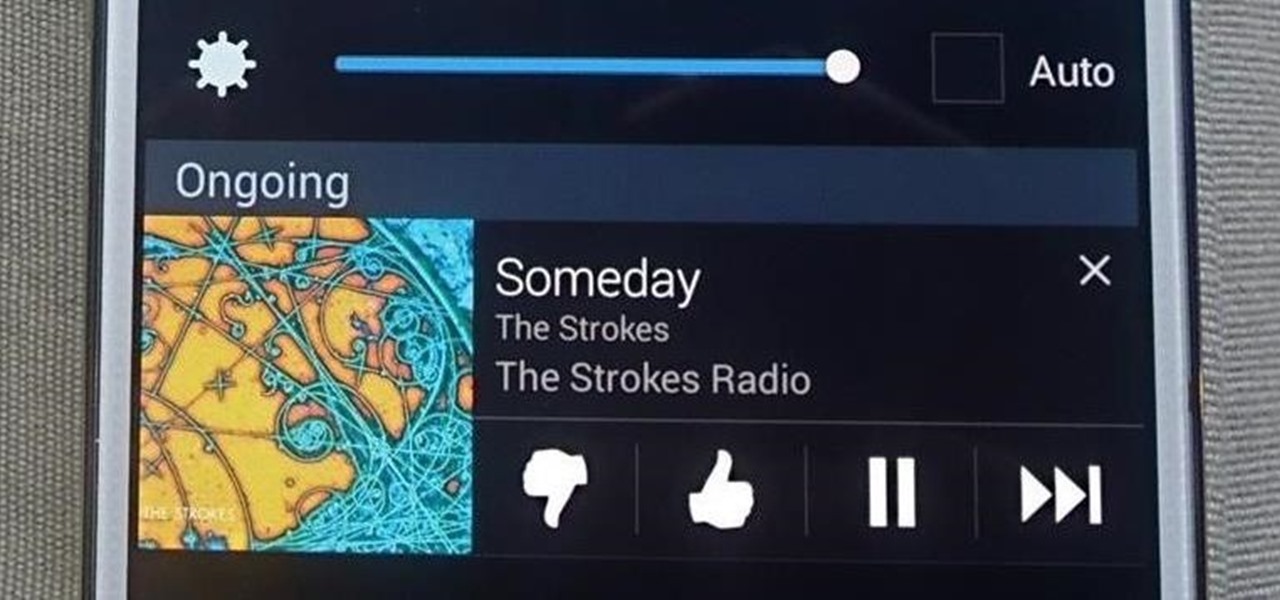
Although I am a loyal premium Spotify subscriber, I still regularly use Pandora in hopes of stumbling across new artists and songs. If I'm fortunate enough to come across something I enjoy, it's easy to use the Like feature in Pandora to locate the song later.

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

Dropping upwards of $60 on a new game can really break the bank, and being a struggling college student leaves me having to decide whether to pick up the latest title or, you know, eat. But often my more primitive urges win out, meaning the only way to enjoy the latest and greatest games are vicariously, using increasingly-popular live streams.

If you're having a "Netflix and chill" night, the last thing you want to worry about is finding something to watch—after all, you have better things planned for the night.

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

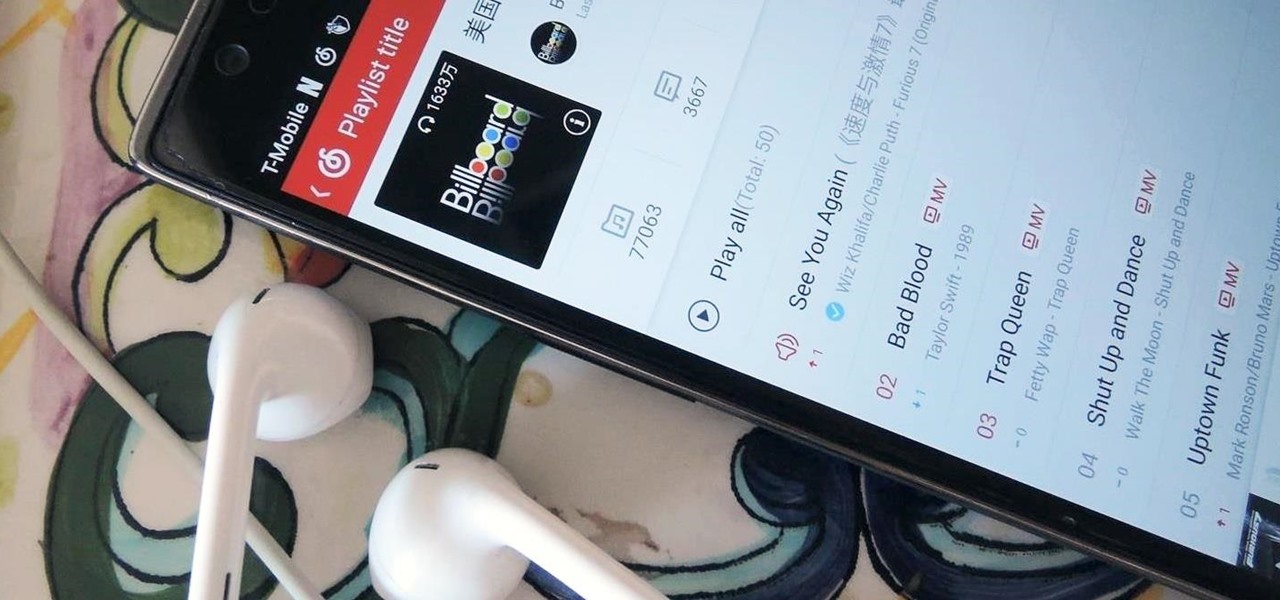
We recently lost Grooveshark, the free music streaming service that supplied users with a huge catalog of free music anytime, anywhere. Since its shutdown, I have been scrambling to find a half-decent alternative, and my expectations were more than exceeded when I found NetEase Music.

In a study attempting to observe virality in real time, two Microsoft engineers, Corom Thompson and Santosh Balasubramanian, used Microsoft's recently released Face detection API to create How-Old.net and track its usage in real time.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Google recently rolled out a new Smart Lock option labeled "On-body detection" for Android Lollipop via an update to Google Play Services. As I'm sure you can gather from the name, this new function keeps your phone or tablet unlocked using the built-in accelerometer to determine whether or not your device is being carried on your body, allowing you to set it down and walk away carefree knowing that's it's locked again.

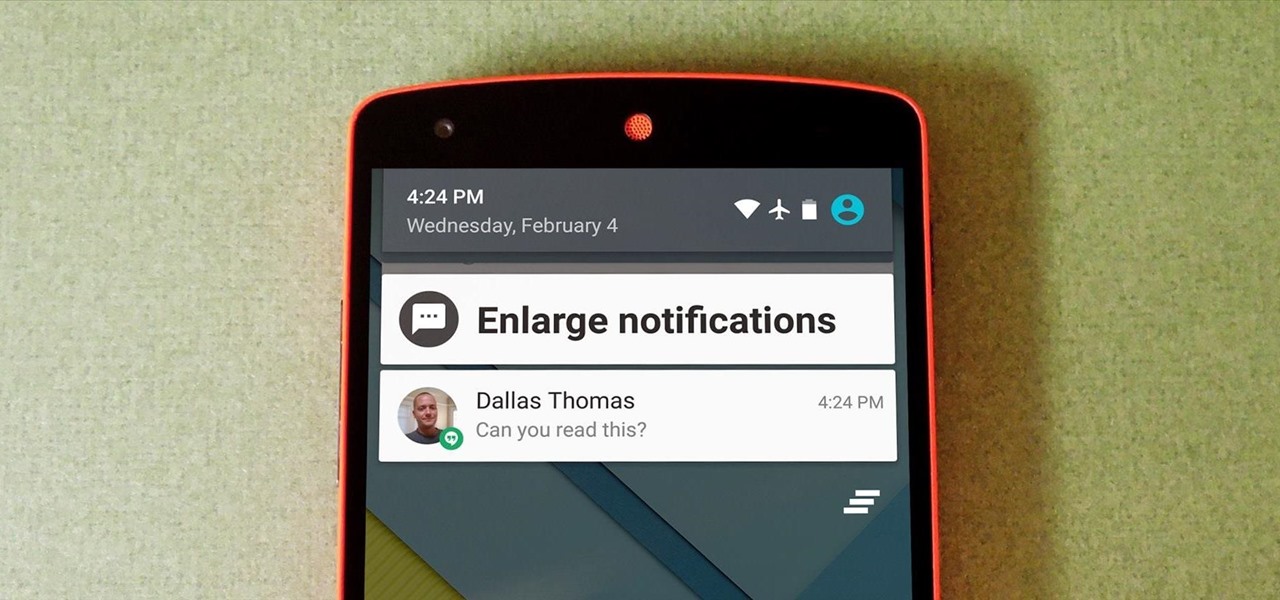
Problems with eyesight affect people of all ages and walks of life. And while it is possible to increase font sizes on Android, even the "Huge" setting is neither big nor clear enough for a lot of folks.

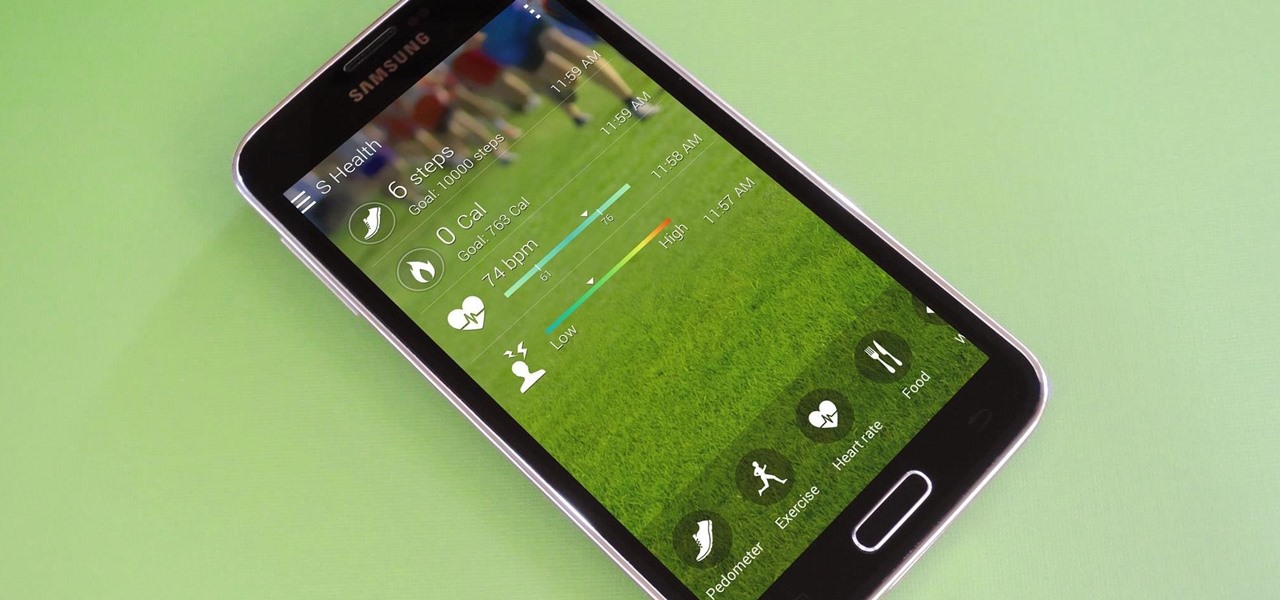
S Health is one of the biggest selling points for newer Samsung Galaxy devices. It offers a centralized place to view and manage data collected by all of the various sensors like the heart rate monitor.

Google's original messaging service got a nice version bump today. Hangouts now sports stickers, video chat filters, an updated Material Design interface, and a few new features that should make the service a little more fun and easy to use.

I'm the type of person that rarely has an audible ringer enabled on my phone. Haptic feedback (vibration) is enough for me... most of the time. When my phone isn't in my pocket, I become the type of person who frequently misses calls and texts—and no one likes that person.

As competition for Spotify and Pandora, Samsung released Milk Music earlier in 2014, a free music streaming service for their Android devices. While Milk was unique to Galaxy owners only, it was popular enough that we showed you ways to get it on non-Galaxy devices as well.

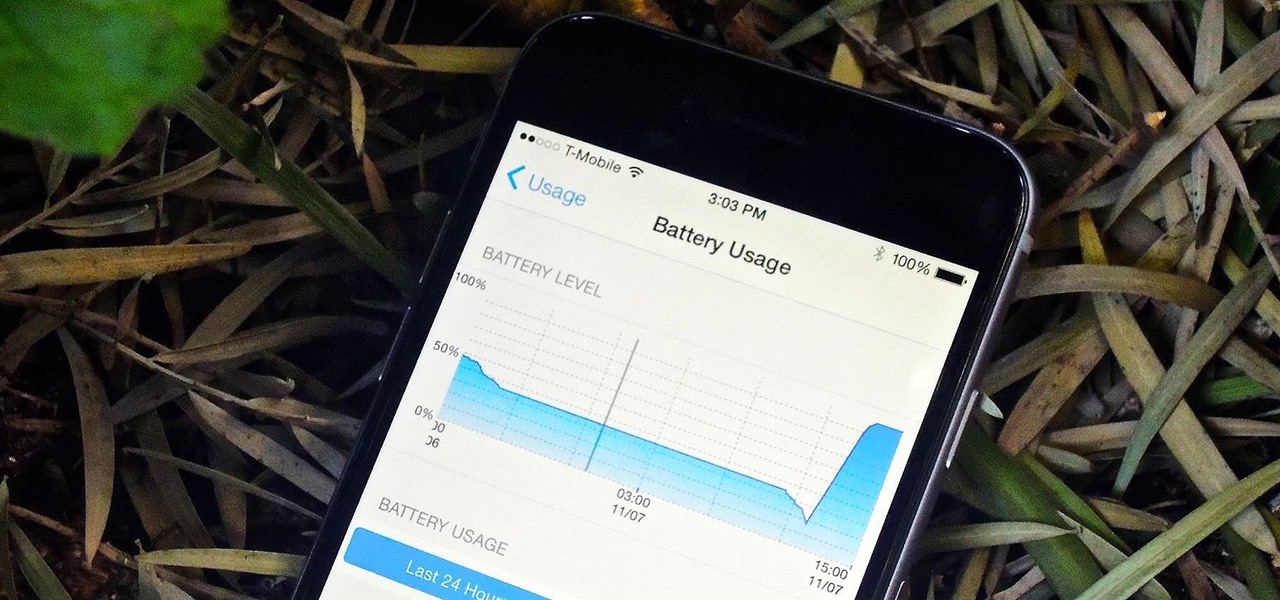
One of my favorite new additions to iOS is the ability to view battery usage stats on a per-app basis, which is helpful in knowing exactly which apps are taking up all of my iPhone's battery life. If you jailbreak iOS 8 on your device, you can take Apple's stock battery stats feature even further to give you details on how those apps are actually using the battery.

Although sleep mode and screen savers contribute to the security and energy preservation of my MacBook, it can become a nuisance when they initiate unwelcomely. Yes, I could just change these settings in System Preferences, but to do this every time I momentarily leave my Mac unattended would be tedious, to say the least.

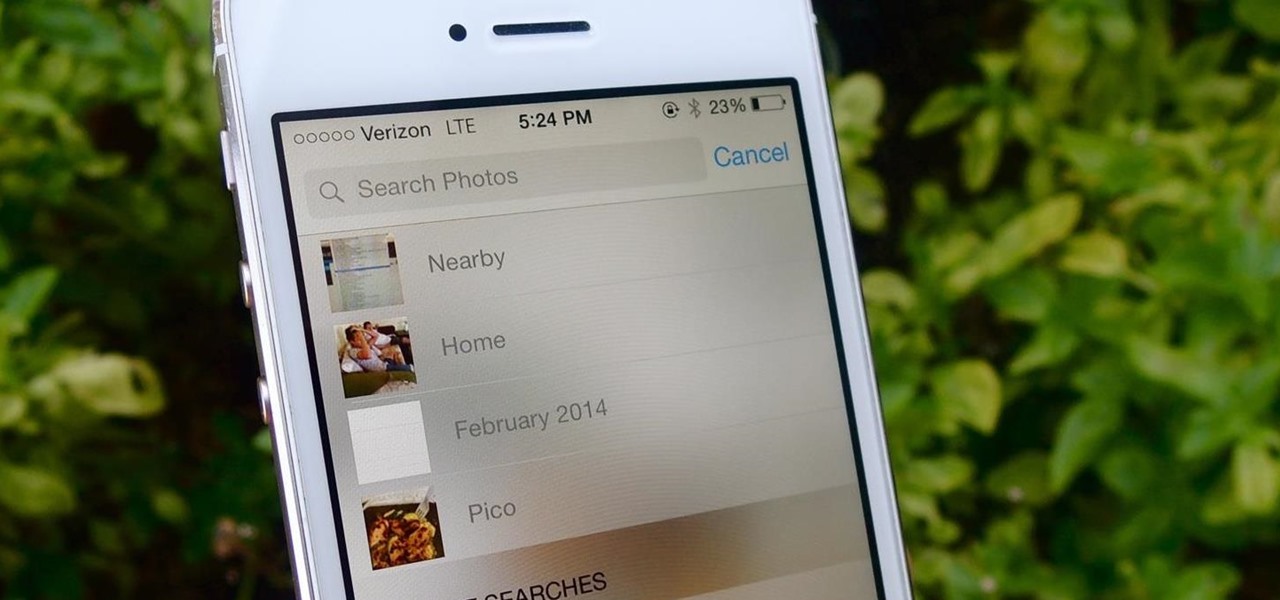
Skimming through the hundreds of photos you may have on your iPhone for that one selfie of you and your friends in Los Angeles can be a tedious task, especially if you were inebriated and snapping pics indiscriminately. Thankfully, as one of the many cool features available in iOS 8, the Photos app now lets you search your images based on date or location.

Even though there are over 1.3 million apps available for Android, we normally confine ourselves to a select few for day-to-day usage. With an average of 41 apps installed per user, most apps on our smartphones lay idle for the majority of the time we spend using them. Instead, we find ourselves constantly coming back to that small set of apps that meet almost all of our needs.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

The Moto X introduced tons of cool features that have slowly been ported over to other phones, like Peek notifications and always listening "OK, Google" detection. Another such feature allows you to twist your wrist to bring up the camera app from any screen—even with the display turned off.

According to a recent survey conducted by Edison Research and Statista, Pandora still has a firm grasp as the most popular music streaming service in the United States. With iHeartRadio, iTunes Radio, and even Spotify trailing behind by a large margin, it doesn't look like Pandora will lose their footing in the near future.

Location-based app shortcuts in iOS 8 work at places like Starbucks, the Apple Store, as well as train stations, banks, hospitals, grocery stores, and more. When you're in the vicinity of these locations, a small notification appears at the bottom left of the lock screen. You you can slide up on these icons (as you would on the camera icon on the lock screen) to access specific apps based on where you're located, making it easy to access your Starbucks account when you're buying coffee or che...

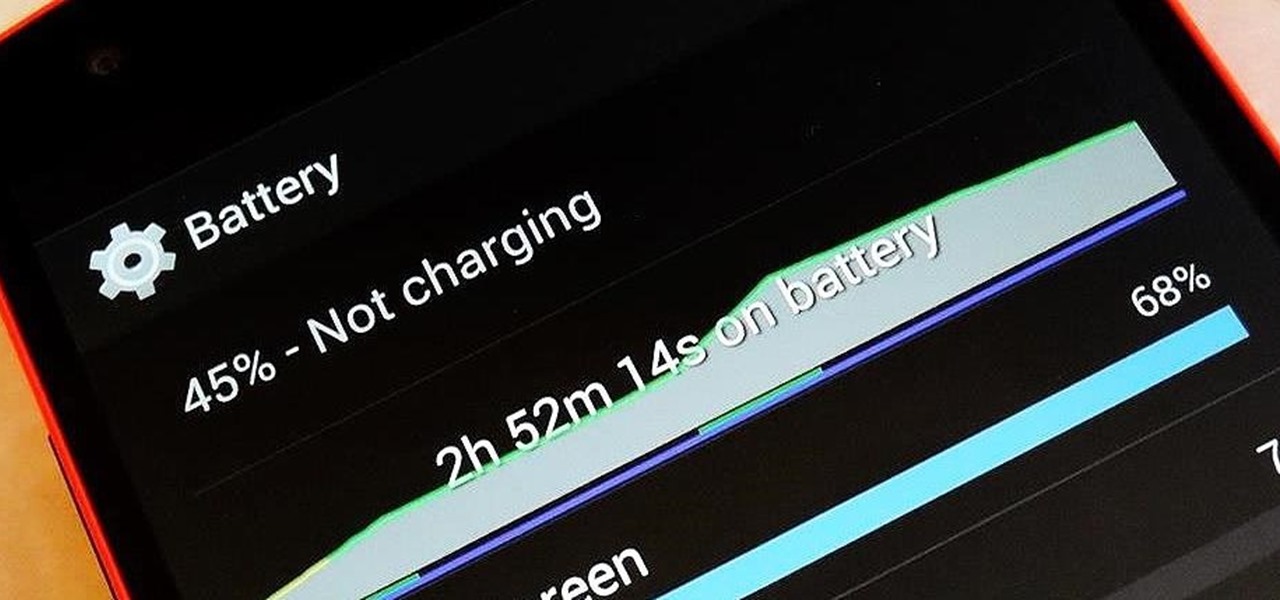
There are so many things to love about the Nexus 5, from timely updates to newer versions of Android to a terrific blend of price and specs. But while mobile phone tech keeps churning along, battery technology isn't quite up to snuff yet, and I find myself wishing that my phone's battery lasted longer on a single charge.

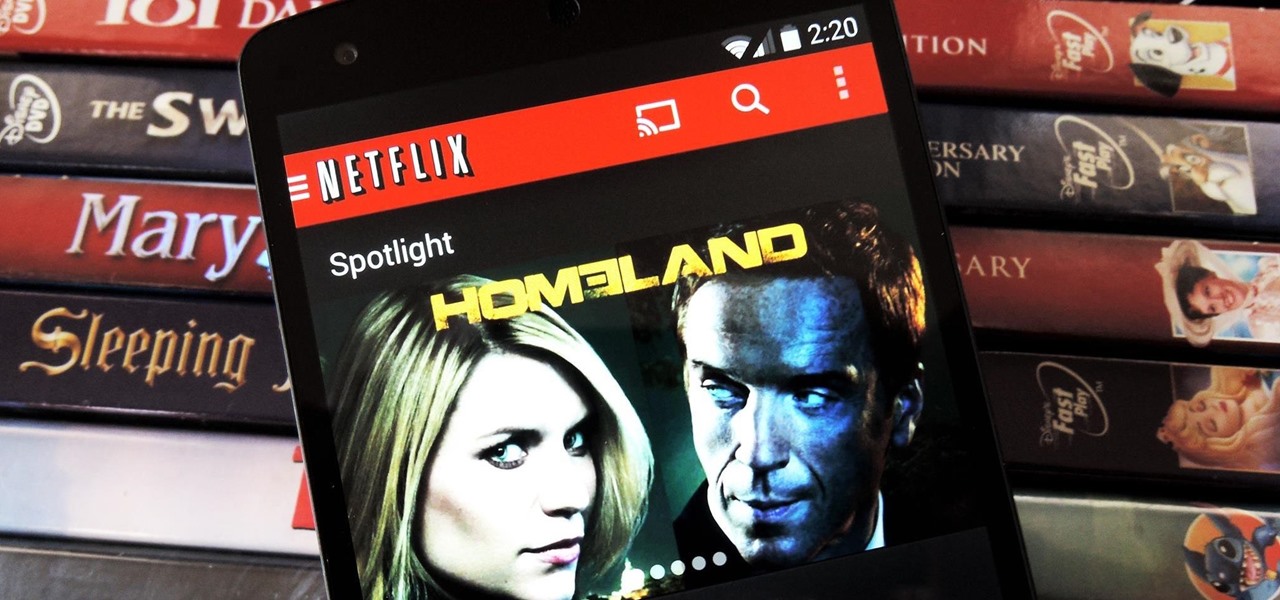
Out amongst the ether of the internet lies a completely different version of the Netflix library you've come to know and love. Because of licensing and rights fees, the streaming media giant maintains separate libraries for each country it services. Ultimately, this means that certain movies and TV shows are only available in certain countries.

Welcome back, my aspiring hackers! Domain Name System (DNS) is one of those things we seldom think about unless it doesn't work. Then, it can be very frustrating when we attempt to navigate to a website and we get that frustrating error message.

Android 4.4 KitKat has begun rolling out for the Galaxy Note 3 in India, Poland, Russia, Switzerland, and several other countries, and an unofficial build for AT&T customers has been leaked for all of us stateside.

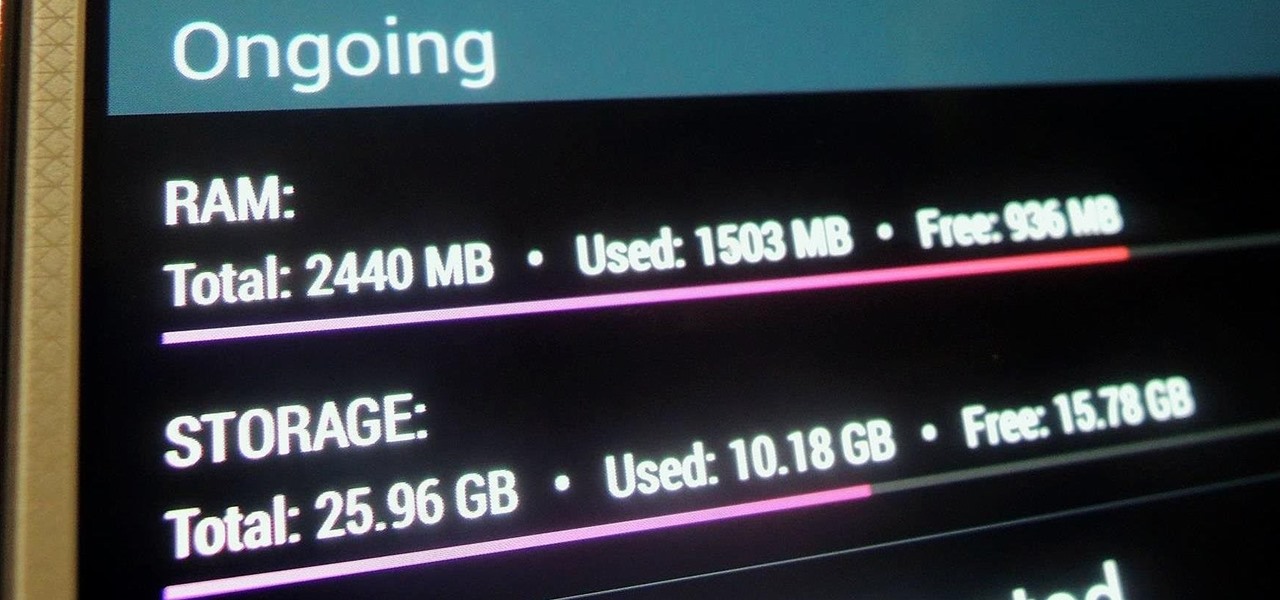
Modern smartphones can easily handle anything you throw at them, but it's always good to keep a tight grasp of what your phone is actually doing and how well it's doing it. System information can be viewed by looking through your Application Manager, but this process makes it difficult to keep an eye on usage in real time.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.