
How To: SQL Injection! -- Detailed Introduction.
Hello NullByte! This will be my first How To series.


Hello NullByte! This will be my first How To series.

If you have no desire to get a separate Mac desktop computer, but want to either supersize your laptop's screen for gaming or need to get additional screen real estate while you work, then connecting your MacBook, MacBook Air, or MacBook Pro to an external display is the right call.

Hanukkah, also known as The Festival of Lights, commemorates the rededication of the temple in Jerusalem in 168 BCE. (Jews and secular publications, such as academic or scientific papers, use BCE—"before common era"—rather than the Jesus-centric BC, or "before Christ.")

Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this.

Welcome back, my budding hackers! In this series, we are trying to understand how AV software works so that we can learn to evade it. To that end, we are working with the open-source AV software, ClamAV. I had previously introduced ClamAV in Part 2 of this series. If you have not installed it yet, go back to that and install it.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

If you haven't come up with a funny, innovative costume yet for Halloween, you're running out of time. While all your friends are busy perfecting their month-long DIY costume project, you're still being lazy about it and have just now started to search online for ideas.

Your brain holds a lot of precious information and is capable of great feats. However, there's one quality that doesn't lie among its strengths—memory security. Yes, that's right, your brain can be hacked, and it doesn't take a psychologist to do it. Anyone with the right know-how can change your memories for their own personal benefit, and you can do so to others, too.

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

In the last iteration of how to train your python, we covered basic string manipulation and how we can use it to better evaluate user input. So, today we'll be covering how to take user input. User input is very important to scripting. How can we do what the user says if we can't tell what the user wants? There are multiple ways to take input, we can give the user a prompt and take input from them directly, or we could use flags/switches, and take their input before the script is even execute...

Android Marshmallow was recently released, and as we've grown to expect, a root method was quickly made available to devices running the brand new operating system. Legendary root developer Chainfire has stated that he's working his way towards retiring from the scene, but he still had enough left in the tank to quickly publish an update to his popular SuperSU root method.

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

If you've been using Windows 10 for a while, you already know that Microsoft incorporated lots of new features into it. So you're probably familiar with Cortana (the new voice assistant), the Edge browser (their replacement for Internet Explorer), the newly resurrected Start menu, and all of the other big changes.

There are over 1.6 million apps on the Google Play Store, which makes it the largest collection of mobile apps on the planet. However, a large portion of this total is occupied by apps with overlapping functions—think social media, news, weather, music players, and various other categories where developers compete against one another to garner the largest user base.
Welcome back Hackers\Newbies!

Last year, the Washington Post's Ashley Halsey wrote an article on what really happens to your luggage at airports. In it, they unwittingly published a photo of the master keys the TSA uses for TSA-approved baggage locks. Now, thanks to that picture and a French lock-picking enthusiast, anyone with a 3D printer can make their own master keys to unlock any TSA-recognized locks.

Newer gaming systems like the PlayStation 4 have a nice, subtle feature that goes a long way towards helping create a more immersive experience. Any time you're on the main menu or home screen, an ambient background music track is playing, which adds an aural appeal to an experience that would otherwise be all about the visuals.

Whether you are sending your phone in for repairs or finally selling it to upgrade to a new flagship, you are going to need to make sure all of your personal data is removed from your device.

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.

Greetings My Fellow Aspiring Hackers,

I like to think of myself as a pretty calm and even-keeled person. I rarely get angry or annoyed, and I don't even get peeved very frequently.

Windows 10 is the most cloud-oriented version of Windows to date—yet, while this means you get some nifty new features, it also means some of your personal data is being shared with Microsoft's servers.

Whether you call them chickpeas, garbanzo beans, or Egyptian peas, these little morsels are one of my favorite snacks—when properly seasoned, that is. Being mild in flavor on their own, they're incredibly versatile and fun to experiment with. (They're also incredibly healthy.)

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.
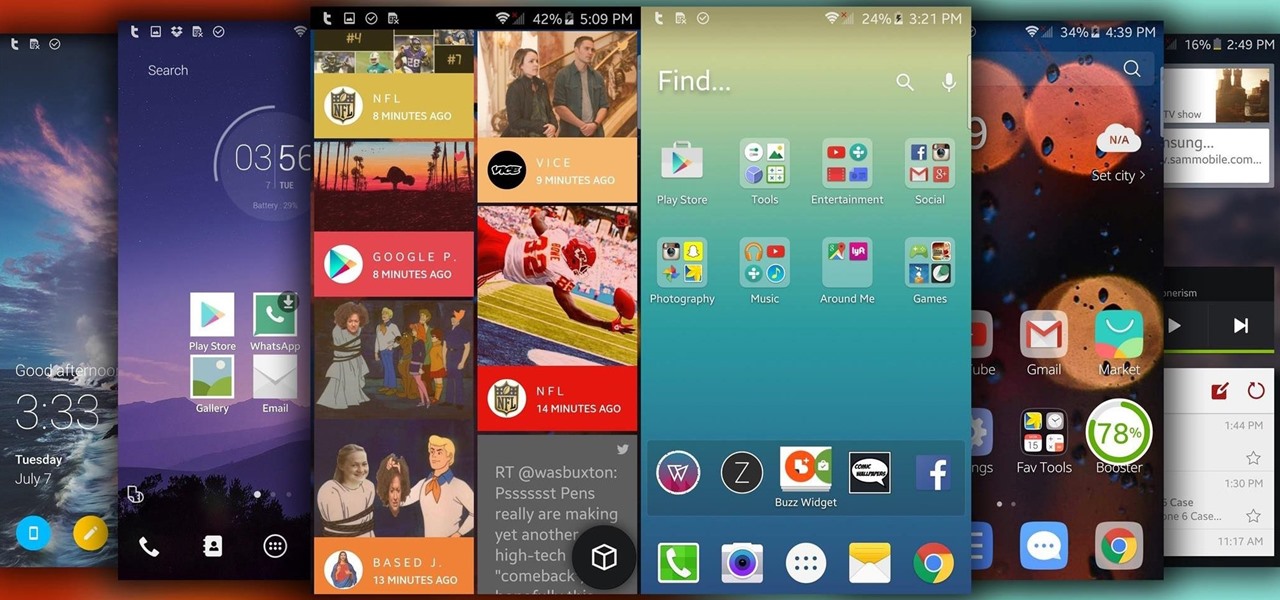
I'm often reluctant to use a home screen launcher other than the stock one on my Android. Once you're well acclimated with something, complacency sets in, welcoming change with much resistance. Well, my friends, I have seen the error of my ways...
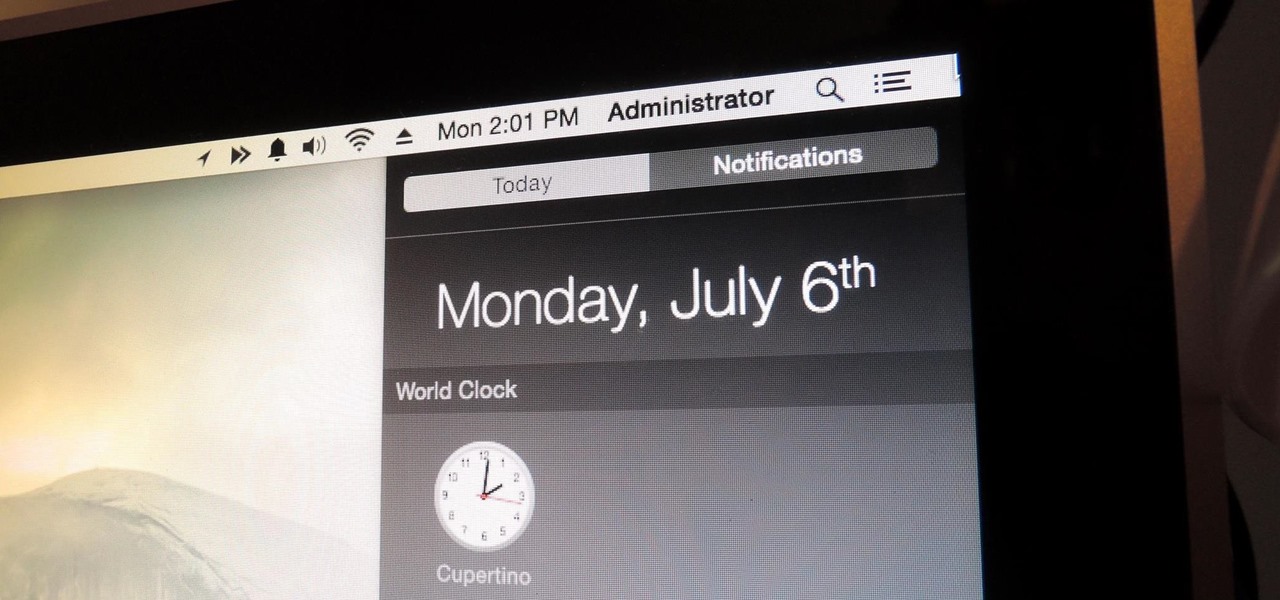
You can check stock quotes, make quick calculations, see the weather forecast, get reminders, and view upcoming calendar events all from the Notification Center on your Mac. But if that's all your using it for, you're just barely scratching the surface.

Few things in life are as exciting and magical as fire. And setting things on fire while cooking? Well, now you're speaking my language. I'm not talking about grilling, though I do love some outdoor cooking. No, I'm talking about the most badass trick in any cook's arsenal: the flambé.

Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just one method.

Windows 10 is due to be released on July 29th, and the majority of existing Windows users should be eligible to upgrade to the newer version for free.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

Protein powder is a fad in the same way that Justin Bieber's music is: you either love it, or you hate it. Everyone I know has a strong opinion about protein powder, ranging from "daily necessity" to "utterly useless."
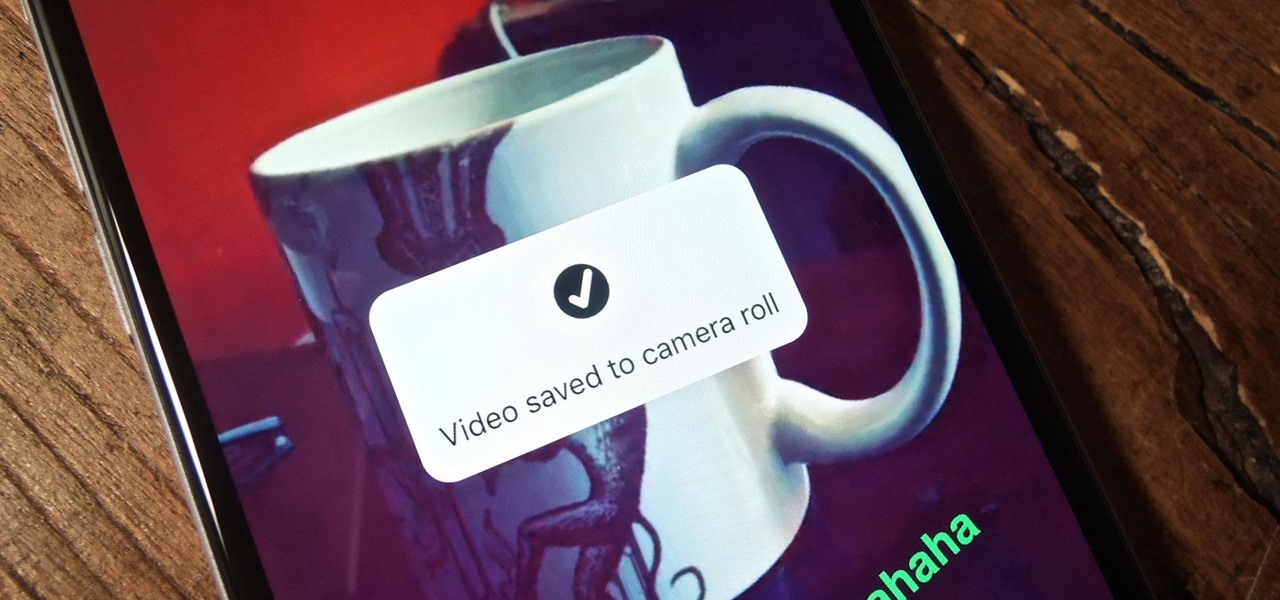
For most of us, the primary reason we capture videos on our iPhones is to post on one of the various social media platforms out there, like Facebook, Instagram, Snapchat, or Twitter, providing instant gratification by receiving a proverbial nod from our followers.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

When it comes to smartphones, the biggest complaint voiced by most users is battery life. Sure, it's unrealistic to expect your Android device to run for weeks without a recharge, but many folks struggle to even make it through the day without having to top off their battery.
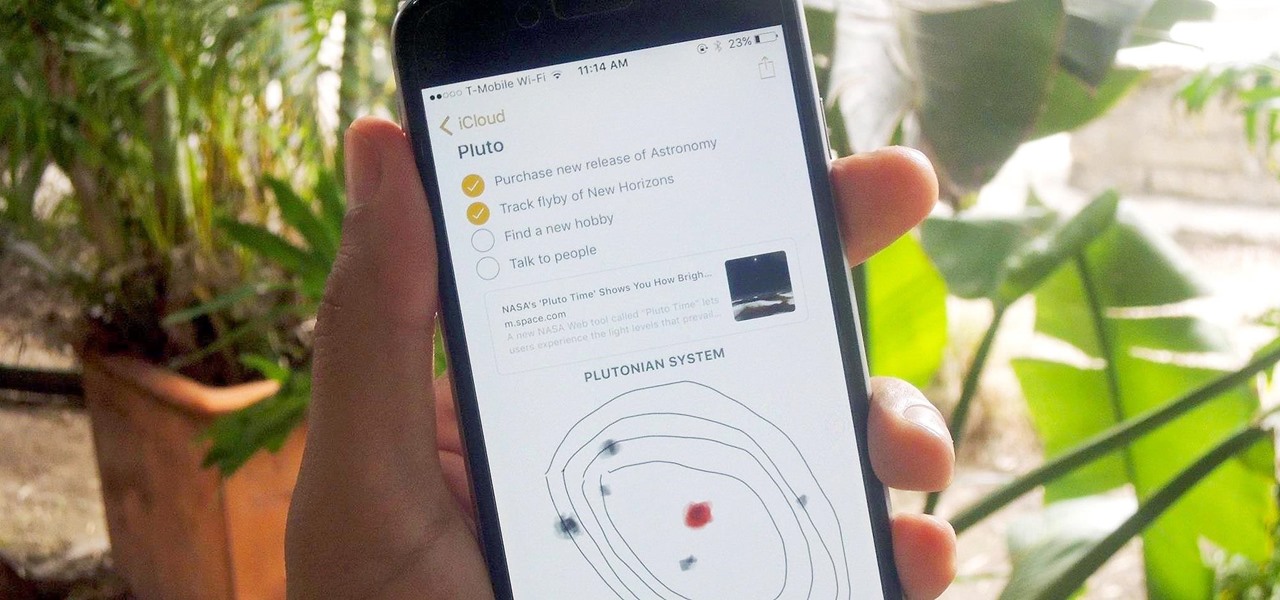
Notes on iOS has never been a particularly great app due to a lack of overall features compared to other note-taking apps like Evernote or Microsoft OneNote.

Unless you're well off, you've probably experienced the hard liquor purchasing conundrum. You know the one: you want to stock your home bar with more than just one spirit, but you don't want to drop $100 or more just so you can have some variety in your alcohol cabinet.

At last, what you all finally waited for! Hi! Fire Crackers,

The fridge is the heart of the kitchen; take it away, and the whole operation falls apart. Yet, despite this, the fridge is also one of the most overlooked appliances in any kitchen. Most people organize their drawers and shelves for maximum efficiency, while many others buy islands simply to make their culinary playground more space efficient. Heck, I know some people who have passed up on otherwise great apartments because the counter space simply wasn't large enough.

Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I suggest doing so unless you are familiar with basic assembly programming and system calls. This is by no means rocket science, so therefore I will simply repeat my TL;DR from last time before we get started, so that the a...