
How To: Workout your abs like Lady Gaga and stay in shape
Lady Gaga is definitely in shape. No one can deny that. But how does she do it? How does pop music's most popular artist stay in perfect shape? How does she get those great looking abs?!?


Lady Gaga is definitely in shape. No one can deny that. But how does she do it? How does pop music's most popular artist stay in perfect shape? How does she get those great looking abs?!?

Shane goes into detail on a specific type of boof in which the paddler comes across the drop with angle and boofs into an eddy.

They are after you from all over the globe. Looking for ways to exploit you. Ways to hurt you. Not political terrorists, but rather "info terrorists." Each month thousands of websites get hacked into and have hidden links inserted into the pages by people wanting their spam sites to rank highly in the search engines.

Suspect that your bovine (bull, cow) is pregnant. Well, there's only one way to be sure. Put on a plastic glove and insert your hand into the rectum, with your fingers together. See how to find out if your cattle is pregnant with help of this video tutorial.

Add speed and power to your computer by adding more memory. You Will Need

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

Apple first included a dual-lens camera onto its iPhone 7 Plus back in late-2016, yet not many developers besides Apple have harnessed the depth data that "Portrait" mode photos provide. A relatively new app is changing that, though, by using that depth information to let you add realistic-looking light sources to your photos.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

Hey there, reader! In this tutorial we are going to explain how values are stored in variables as either signed or unsigned. Try to not get lost!

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

Welcome back, my tenderfoot hackers! In continuing my series on digital forensics using Kali, I want to introduce you to two complementary tools, both built right into Kali Linux. These are Brian Carrier's tools Autopsy and Sleuth Kit.

In this math lesson we will learn how to solve math problems involving sales tax. Remember these two important formulas:

Want massive, Arnold Schwartzenegger-worthy shoulders? Well, you'll have to work for it, but they're achievable with a few strategic exercises. Building muscle, especially big muscles like your biceps, requires heavy resistance.

Kristen Stewart is a well known tomboy who really doesn't care whether she's wearing Chanel or Target when she's out and about. But the sister knows how to glam it up big time on the red carpet and for photo shoots, where she brings out her hidden sultry, feminine side.

Southwest Yard and Garden featuring John White, Dona Ana County Extension Agent, hosts a 6 minute clip with co-host Master Gardener Valois Pearce both of Dona Ana County, New Mexico host a short web show featuring plants that can easily survive on smaller amounts of water over typical plants. They begin by discussing the full sun Ice Plant, which comes in many species and colors as well as their hardiness, but unfortunately are easy targets for wildlife. They then move onto the Gopher Plant, ...

There comes a time in many tattooed individuals when they want to remove their tattoos. There are a lot of different ways to remove tattoo but they all cause scar. Dr. Neal Schultz explains only laser tattoo removal will not leave a scar and give a cosmetically-superior result. Laser energy is specifically targets the colored pigment of the tattoo so it only damages the colored pigment. It does not damage any of the surrounding skin. When people are treated for tattoos, it can take 8-12 treat...

If you're interested in nabbing superhero memory strength, the secret behind training your brain is not necessarily what you might expect. Your standard G-rated brain strengthening exercises range from crossword puzzles to Sudoku to calculating fairly simple math problems to improve short term memory, but the real clincher used by some of the pros is essentially... porn. Yep, you read right.

Bowling is such a fun group activity and is perfect for birthdays and other types of gatherings. However, if you are not a pro bowler the scoring system can be pretty confusing. This tutorial will walk you through the steps of keeping score so you will know a strike from a spare and everything in between.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

The software updates from Canadian smartglasses startup North keep coming, each with a unique new twist.
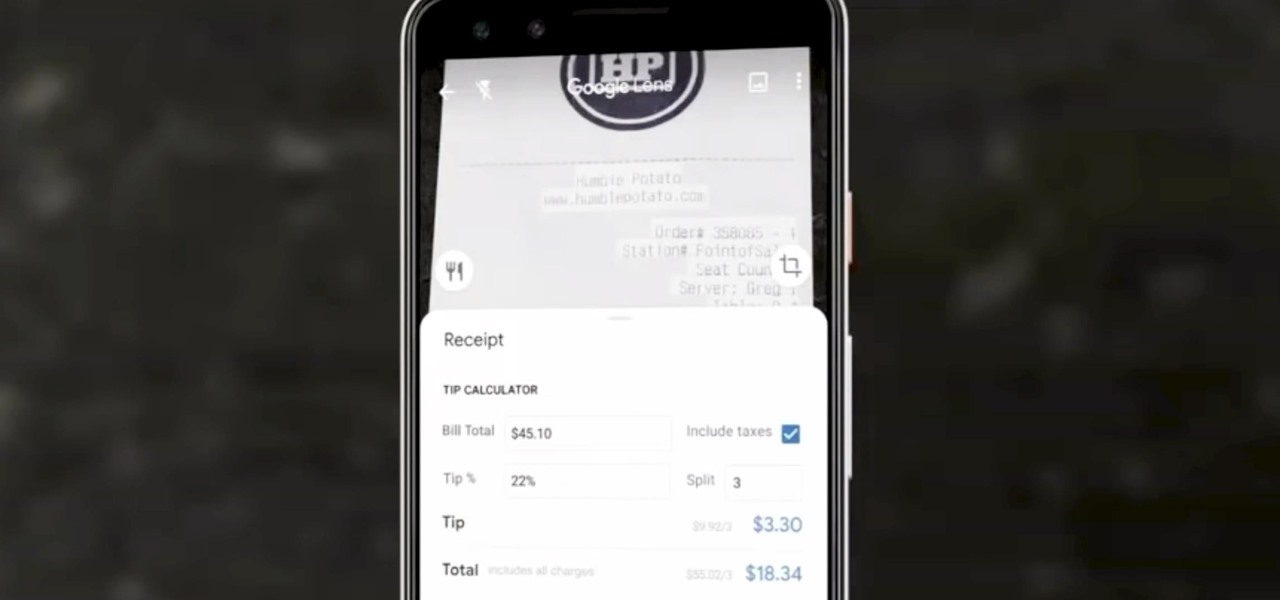
Google Lens can perform many different tasks with your smartphone's camera thanks to advanced machine learning, such as foreign text translations, landmark identification, and business cards to contacts conversion, to name a few. With this year's Google I/O conference, we have another cool Lens feature to look forward to — receipt calculations.
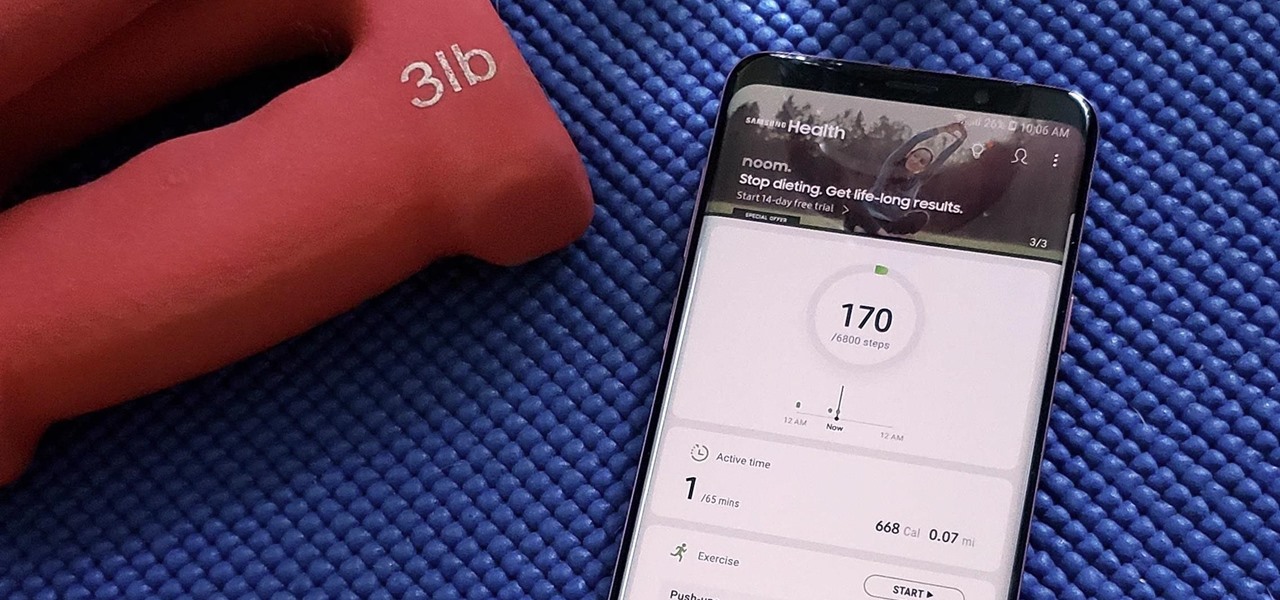
Samsung Health has become one of the most comprehensive wellness apps thanks to features that cover everything from step counting to nutrition logging and symptom diagnosis. But because the app has so much to offer, it can be easy to overlook some smaller, but useful features.
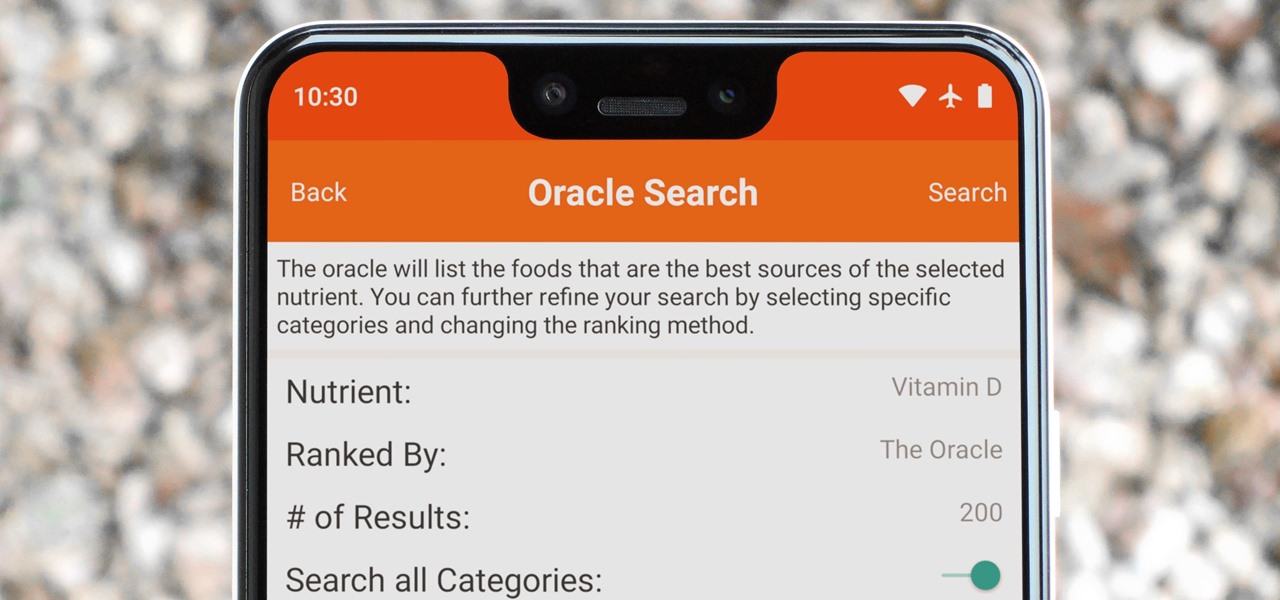
Micronutrients are essential to our health. Unfortunately, many of us aren't getting enough of each nutrient from our diets. It isn't that the food we're eating is bad, but rather we are not eating enough of the right food to get our recommended daily allowance. But with the help of a micronutrient tracker, we can change this.
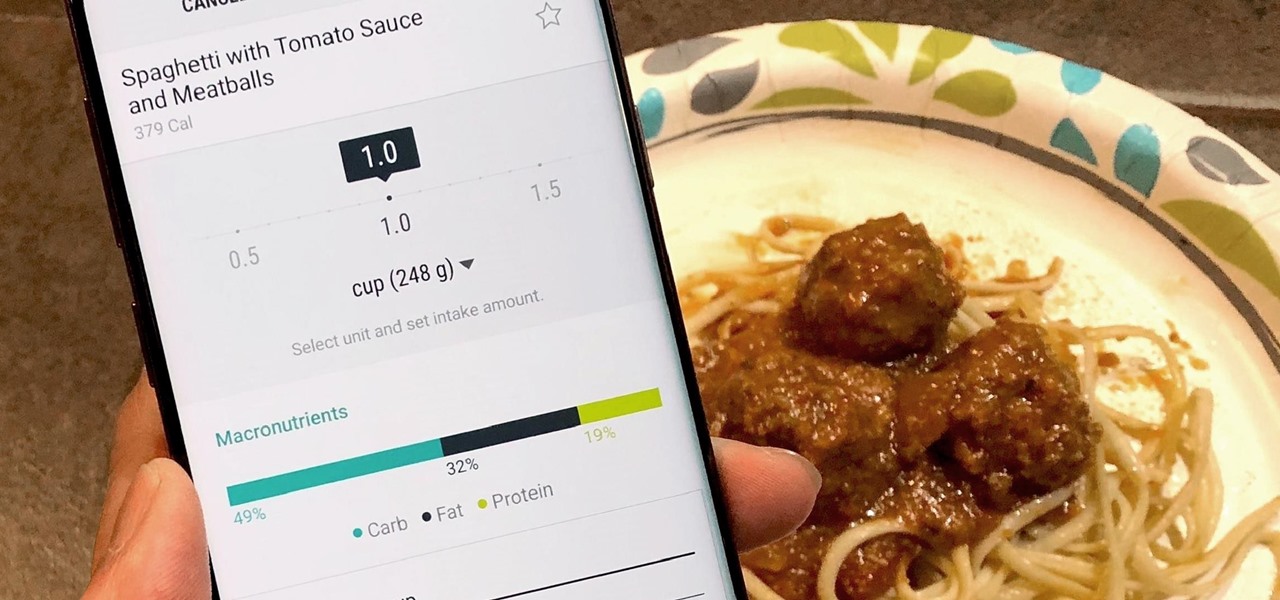
The most essential part of a healthy lifestyle is managing your diet — after all, what would be the point of a daily workout regimen if you were eating junk food? Thankfully, Samsung Health makes it easy to record your calorie and nutrient intake to get a clear picture of your dietary habits and how you can make them better.

Signaling a new direction forward for the company, Magic Leap shook up its executive suite by re-assigning to top leaders to new advisory roles. Meanwhile, a new startup backed by Hollywood executives, tech venture firms, and notable angel investors plans to bring new life to AR for marketing entertainment properties.

If you or someone you're shopping for has a newer iPhone model or an Android smartphone like the Galaxy Note 9 or Pixel 3, they come with wireless charging capabilities. Problem is, they don't come with wireless chargers. But there's no better time to snag one than on Black Friday, and we've found the best deals out there for 2018's holiday season.

Election Day is like the Super Bowl for network and cable TV news, so ABC News is breaking out the big guns with a new augmented reality experience to win over eyeballs of viewers.

In our last ARKit tutorial, we learned how to measure the sizes of horizontal planes. It was a helpful entryway into the arena of determining spatial relationships with real world spaces versus virtual objects and experiences.
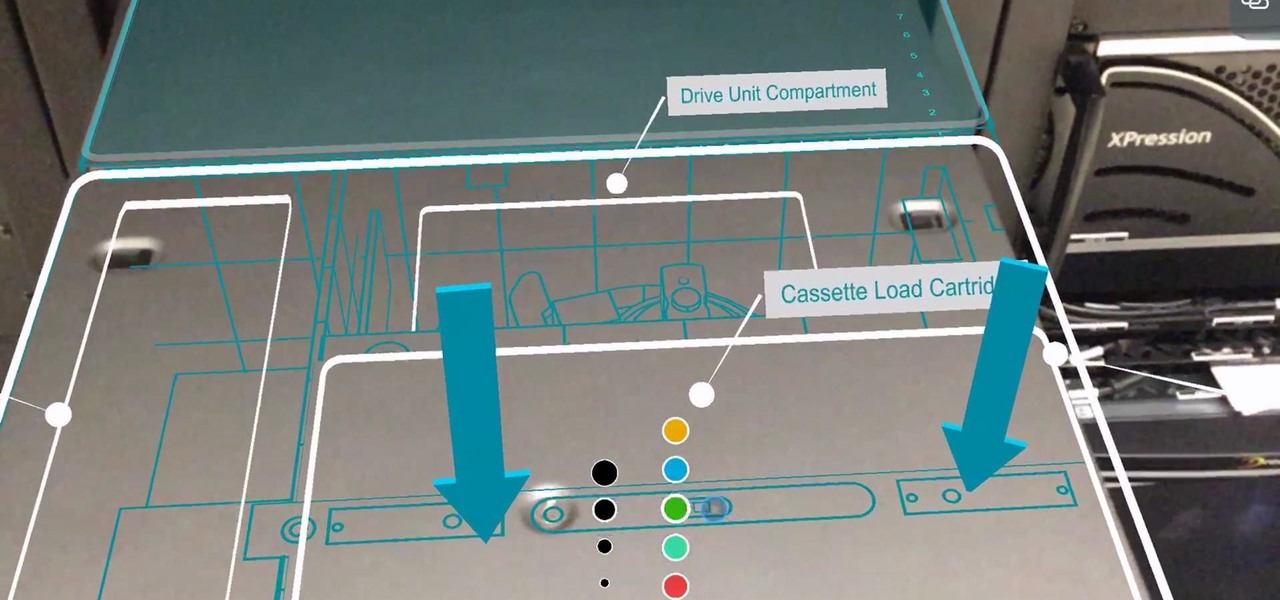
Enterprise augmented reality software maker Scope AR is bringing the powers of its two productivity apps together like the Wonder Twins into the form of a single app.

Your best chance of getting to a destination on time during rush hour is to drive through relatively empty HOV lanes. Thankfully, if you're using Waze to navigate through traffic, you can easily locate HOV or HOT routes to optimize travel times by adding your toll passes in the app's settings.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

PUBG is currently taking the mobile world by storm, and it's easy to see why. The game has breathed much-needed life to the multiplayer shooting genre, primarily by adding an element of sheer terror as you scavenge for weapons in a hostile environment. With new players continually joining in on the fun, many players are looking for ways to gain an edge.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Among the revelations uncovered during the December unveiling of the Magic Leap One: Creator Edition was the fact that the Lightwear augmented reality headset would be tethered to a wearable computer called the Lightpack.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.