If Null Byte had a large Batman-like spotlight calling for help, we would definitely be using it right now. However, we don't, so this is my digital equivalent. Information security is a huge field, far too much for one man to cover adequately, so I need your help!

Lost the product key for your game? If you have to reinstall the game and don't have that key anymore, you're out of luck, especially if you didn't "buy" the game. But never be in fear of losing product keys again with today's Null Byte, where we'll be practicing a little bit of mind-kung fu.

Skype is a great service. It allows a free solution for VoIP to VoIP calls, and cheap VoIP to landline calling. However, a very disturbing, little known fact that might push you away from Skype does exist. If you closely read the terms of service agreement, it clearly says that Skype is allowed to decrypt your messages whenever they please. Here at Null Byte, we tend to enjoy our anonymity, don't we?

Image via Tiger Mom Says.
I’m seeing a flood of posts on youth football forums and even getting a few e-mails from youth football coaches complaining about “player agents” also known as parents. Most of these unhappy coaches are dealing with parents that have non-issues, have an agenda, are misinformed, don’t know much about the game of youth football or are just people that gain great pleasure from complaining. The 80/20 rule is more like 95/5 in youth football, 95 percent of the problems are caused by 5 percent of t...

As hard as you try to protect your valuable information with strong passwords and anti-doxing measures, there's nothing you can really do when someone else gives up your goods. And that is the case with the recent Global Payments breach.

You can make homemade pizza with a minimum of tools, or you can buy the entire yuppie menagerie (and let's face it—if you're a foodie, you probably want the toys). Below is a brief rundown of the different options available. Since I'm a relative beginner to the process, I've also linked out to a few in-depth reviews.

L.A. Noire is the newest Rockstar (GTA4, Red Dead Redemption) game created by Team Bondi ( The Getaway). The game is set in the late 1940’s in Los Angeles. The main character, Phelps, is a war veteran rising through the ranks from police officer to detective. The game is presented in mini episodes (one case per episode) and flashbacks. Once you finish a case, you go straight to the next one. Having played four cases where the character moves from police officer to detective, here are my initi...

Wondering why your inbox is looking a little threadbare? It may be that you've violated a few unwritten rules of email etiquette. Here are a few basic tips that the web-savvy know by heart.

Jersey Shore's pickle-loving, drunken little ball of fun has captured the affection of many, as well as a fair share of haters. According to today's Wall Street Journal, Snooki and other Jersey Shore characters have surpassed Lady Gaga in popularity for Halloween costumes of 2010. Go Snook. (Not too surprising. For lots of ladies out there, the more revealing the costume, the better.)

In Alan Wake, there are hidden messages hidden throughout the levels that are only visible with a flashlight. If you don't flash the light at a particular spot, you will not be able to see the message.

Your iPhone's name matters more than you might think. It shows up when AirDropping files to other Apple devices, when keeping tabs on your devices' locations via Find My, and when syncing with your computer. While "Jake Peterson's iPhone" gets the job done, I'd rather give the phone I spend all my time with a proper name.

If you've got a Samsung Galaxy S3 or Galaxy Note 2, you probably either love or hate the Social Tag feature. Using facial recognition, much like Facebook does, it scans your photos and lets you tag a name to a face. If your device recognizes the face by itself, it will automatically tag it for you. If the person is in your contacts, it will give you the option of calling, texting, or emailing them. While it's a great feature for some, it doesn't always work perfectly. If the flash from the ca...

The announcement of the iPad 4 has made a lot of third-generation iPad owners very angry. After all, it's only been seven months since the third one was released, and it's now "obsolete." If you bought one really recently, though, you could be in luck. Some Apple stores will offer a free upgrade to the iPad 4 for customers who bought a third-generation iPad in the last 30 days. According to CNET, a rep from an Apple store in San Francisco confirmed that her store would be offering an exchange...

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most popular communities. Users can join and participate in any World they're interested in, as well as start their own community.

Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information you want to keep private, private, should be important to you.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Some people are what is labeled a power user. I am one of these people. No matter how fast I get my system, or how quick of programs I have, it is never good enough. There is always at least one program that I could swap out for a more advanced, text-based counterpart that increases performance just a bit. Luckily, you don't have to use text-based programs without graphical user interfaces to get blazing fast speeds on Linux. There are tons of open source alternatives to the mainstream progra...

What happened to please and thank you? When did asking someone to come look at your build degenerate into COME NOW or FOLLOW or sending out teleport requests to any and all currently on the server without asking?

So, you scratched up your $500 Adobe CD and now it's unreadable. You could go buy a new one, but you already purchased it! Searching The Pirate Bay and downloading some Adobe software can usually be easy enough, but what should you watch out for?

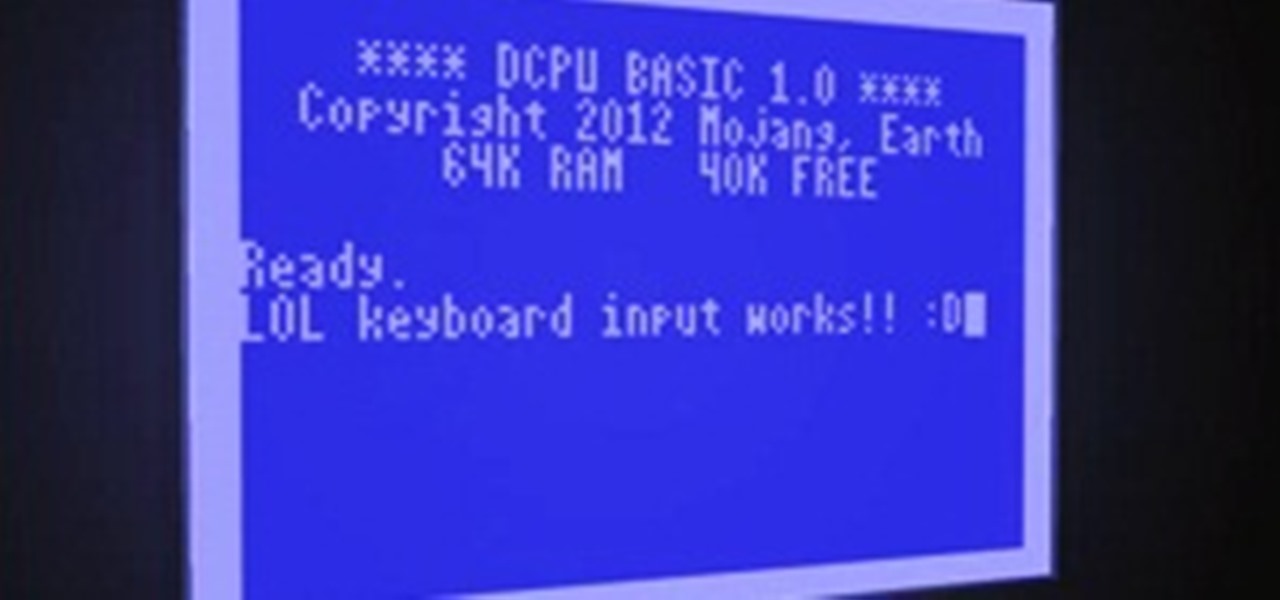
The developer community has already made some incredibly quick progress on implementing assemblers, interpreters, and emulators for the proposed virtual computer in 0x10c, Notch's latest game. But the truth is that the majority of programmers out there couldn't be bothered with spending enormous amounts of time writing anything much more complicated than a "hello world" application in assembly. What's on the top of everybody's mind is creating a compiler for a more widely used language.

Laptops are almost a necessity in today's society. It doesn't help that a laptop that can actually increase your work productivity will put at least a $1,500 dent in your wallet. I'm sure you have searched around to try to find factory direct deals, or (shiver) even looked at used laptops, but that isn't the way to go. You need something that actually has a warranty, and good performance, but at the same time, doesn't require you to sell a kidney. This can cause quite a dilemma, as it can tak...

Remember what life was like before your iPhone? Before there were palm-sized smartphones with seemingly endless features, there were phones like Motorola's RAZR that peaked with its embedded camera. Before that, there were simple flip phones with texting capabilities, bulky two-pound Gordon Gekkos—even briefcase phones.

Moms, don't get stuck in a clothes rut. Shop in your own closet for new looks. Here we show you four outfits that this mom came up with. Casual everyday

In these auto lockout emergency videos, learn what to do when you've locked your keys in the car—aside from calling a locksmith. See how to use special tools, usually readily available to the public, to unlock your car free of charge.

someone dress up as a fake cop and then start arresting people and put like two in the cop car and make it seem like if you were chasing a rober and ten get off the car and some dude gets in and leves with the ar with the people in the car and his calling his buddies saying his leaving los angeles to go to texas and they just say it was a prank.

For this one we get preston or phil. Its really simple. we put a hidden camera in a hotel's bathroom and then phil or preston will dump in the top part of the toilet to the extent to where it wont work anymore. upon calling housekeeping up they come in to find the most foul and disturbing thing in the toilet. or get the entire group to fill a toilet up with fecees and call up housekeeping

Ashton Kutcher said he'll never be Punk'd, but I think we can do it. The show is over, he'll never see it coming. So whats something thats close to Ashton that if something happened to it, he'll freak out? I know, his wife. So, for this one you're gonna have to get Demi Moore invovled with it. So this is the idea I have. Set Ashton up to leave his house for a little while, and when he gets back the whole house is going to be surrounded by cops. Have a bunch of cops and a SWAT team, maybe if e...

For this one you're gonna have to use some good makeup and stuff, but what you would do is make someone look like someone on the FBI's most wanted list and have them hanging outside the white house or outside a police station or something asking cops or agents for directions or something like that. Imagine what they would do if they thought you were that guy.Or, what about prank calling the FBI? Tell them you know where Usamah Bin Laden is, but you want the 25 million dollar reward first or s...