Knowing just one or two programming languages is no longer sufficient if you want to make serious money in the lucrative world of web design and development. But the good news is that you don't need to spend an excessive amount of time or money on a traditional coding education to get the skills you need to thrive.

Whether you're looking to add a substantial coding foundation to your hacking skill set or want to get a job in programming and development, knowing one or two programming languages just isn't going to cut it.

Tequila, raw sugar, simple syrup, and cranberry juice make up the cocktail. Follow along with bartender Jaime as he gives step by step directions for how to mix up this specialty drink that would "send Dorothy Gale back to Kansas." Watch this video beverage making tutorial and learn how to mix the ruby slipper martini cocktail.

Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educated and thoughtful choice on what programming languages you want to learn, and how you want to learn said languages.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.
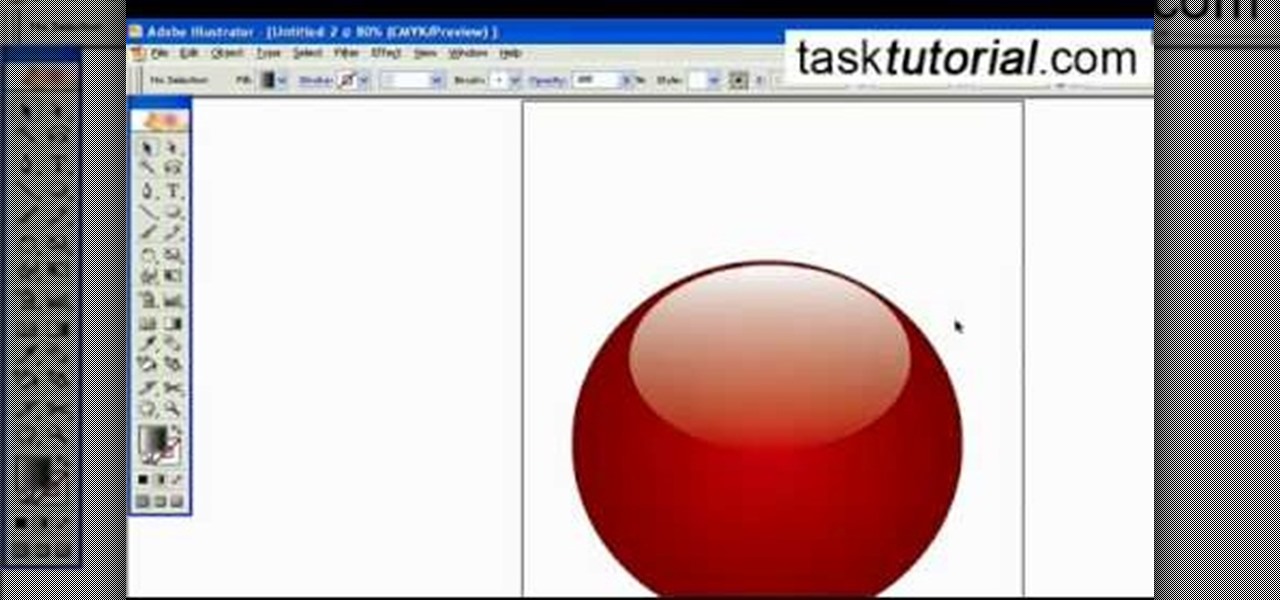
To create a Christmas ornament in Illustrator is very simple if you follow the steps below. Before starting the process one should ensure that all project files used in the tutorial is available. First by holding the shift key draw an oval, then go to gradient and create a new gradient which is at right side of the window. Now select red color and make it darker, then select 'Radiant' from the tool and switch the color positions. Select the ellipse tool once again and create a new shape on to...

In Final Fantasy VII, it's possible to max out vitality without any store-related progress needed if your strength stat has already been maxed. Take a look at this video and learn how to max out vitality simply by targeting an enemy called "spiral".

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

The most used and most washed articles of clothing are undergarments. Underwear, specifically bras and panties, are in desperate need of attention after each and every use. They're not like a pair of jeans, wearing them twice in a row is not a good idea, nor clean. Shabby’s not chic when it comes to lingerie. Use a little extra care to keep your lace and silk bras and panties looking good.

Do not discount the "pretty" rocks found along with gold. The sapphires you see are worth many times more than gold. Sapphire (& Ruby, (corundum), is like garnet, a relatively high specific gravity that will catch in a sluice readily. These gems act as gold, they will drop behind a boulder, in bedrock cracks, and set up in the stratiform layers of a bar on the inside bend of a stream. In a perfect (laboratory world) a river bar sets up from front to back: Gold, Platinum, Lead, Iron Ore (black...

The term "hacker" often has negative associations attached to it, yet the world is in dire need of professionals with hacking skills. White hat hackers are ethical computer hackers that use their hacking skills to pinpoint network vulnerabilities and patch them up before they can be exploited by the bad guys.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.
Before I start a series on remote exploitation, I think we should learn the basics of Perl. Perl, Ruby, C, C++, Cython and more are languages that some penetration testers just need to learn. Perl is a great language for multiple things, sadly, like many other scripting languages, it is limited by the environment in which it is designed to work in.

You can use Twitter to print Instagram photos, track news and weather events, or even remotely shut down your computer, and if you're familiar with IFTTT, there's no shortage of ways your account can help automate your life.

Believe it or not, an ammo box can still be of use to you once its rounds are gone. You can use it for storage, as a toolbox, or possibly even as a Faraday cage. But if you want to use it as more than just a container, why not turn it into a portable set of speakers that you can take with you anywhere? The ammo can speaker pictured above was made by Instructables user Dustin White. He started with an empty .50 cal box, though you could probably even use thinner 5.56 or 7.62 mm cans. He remove...

Controlling your breathing in yoga is one of the ways to bring in more energy, life force, or in yoga it is called "Prana". In this fitness how to video, Pius Ruby and Deborah York will guide you through one yoga breathing method. Yoga help us both obtain physical balance and helps us in keeping balance in our lives. Watch this tutorial and you will learn how to gain strength and flexibility through yoga.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - at my blog, here - https://techkernel.org/2015/12/11/embed-metasploit-payload-in-apk-easily/

if you are looking for a hobby that will pay for itself over time, consider faceting stones. Precious gems like sapphires and rubies are a sound investment that will never lose value, and you can produce them from your home with the right equipment.

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

Greetings, fellow NBers! Welcome to my sixth iteration of my sorting series. Today, we'll be discussing a personal favorite: Quicksort, or Quick Sort.
I see many people posting the same thing on the internet. "How do I become a hacker? Where do I commence?"

Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.

In this makeup tutorial learn how you can create a soft gold and red eyeshadow look. This how to video uses the following products:

Despite the fact that Snap Inc.'s Spectacles weren't the hit some were expecting, the company is nevertheless taking another swing at it by releasing an updated version.

The knee-jerk reactions to Magic Leap's long-awaited augmented reality device, the Magic Leap One: Creator Edition, range from pent-up joy to side-eyed skepticism. That's what happens when you launch the hype train several years before even delivering even a tiny peek at the product.

When it comes to hacking guides, most are written from the perspective of a Linux user. There are a few outliers, but it's mainly Linux, which leads to the idea that Linux is the only OS that's viable for hacking. This couldn't be further from the truth. A properly set up Apple machine can do quite a bit of heavy lifting.

Pitting cherries is really annoying. There's no neat way to do it with a knife and, though they make a tool that does it, not everyone has space in their kitchen for a gadget that does so little. But fresh cherries are so delicious when they're in season... it's almost worth the extra hassle and/or space usage.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

Earlier this week, Spiderlabs' vulnerability researcher Jonathan Claudius discovered a key in Windows 7 and 8 registries that makes it easy for anyone with physical or remote access to a computer get a hold of the user's password hints. When the "UserPasswordHint" key is read, the hints are displayed as a code that looks encrypted, but Claudius noticed a pattern of zeroes that could be easily translated back to plain text with a decoder he made in Ruby. He added this functionality to the Meta...

Traditional makeup is too boring for special occasions, so why not try something a little more fun to ring in the new year? This how-to video goes through the intensive process of applying a vibrantly colorful and ornate harlequin mask, using just makeup. The cosmetic products used to create this look are N.Y.C Yellow Concealer, Clinique Super Powder Double Face Make Up # 10 Matte Medium, N.Y.C Black Pencil Eye Liner, Graftobian Crème Foundation Yellow, Graftobian Crème Foundation #89092 Augu...

Dirty, malformed, and outright mischievous text strings have long been the enemy of interactive website developers. Strings contain any combination of letters, numbers, spaces, and punctuation, and are entered into text boxes on websites by users. These strings in particular can do everything from highlighting XSS vulnerabilities to soliciting 404 error pages.

Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking.

During the summer, fresh strawberries are everywhere: at your neighborhood farmers market and in many desserts like strawberry shortcake and strawberry rhubarb pie, to name just a couple. Bringing home a few baskets of the ruby red fruit always seems like a good idea... until they begin to turn to mush or grow mold only a few days later.

The cool tang and citrusy taste of a margarita in the summer is refreshing, to say the least. But when making margaritas at home, many of us opt for the ease of store-bought mix when it's actually really simple to make it instead.

Unquestionably, one of the best parts of Hanukkah is the prevalence of latkes during the 8-day celebration. But even the most dedicated spud fanatic can get a little "latke'd out" as the week drags on. Here are some alternative preparations for latkes that will give you some variety in your celebratory food choices throughout the Hanukkah season.

When Google Play Music launched a few years ago, I ditched iTunes and began using the service as my one and only source for listening to my personal music library. While All Access is great, I still prefer the radio feature on Spotify, so I still use that to discover new music.

Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can learn to spy, too.

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.