Apple released the eighth iOS 14.5 public beta on Tuesday, April 13. The update (build number 18E5199a) comes three hours after Apple seeded developers 14.5 beta 8, so we know that it contains little-to-no surface-level features or changes. Any changes, at this time, appear to be under the hood.

Apple officially unveiled iOS 14 on June 22 at its first all-virtual WWDC. After months of beta testing, iOS 14 hit iPhones on Sept. 16, but that doesn't mean that Apple is done beta testing iOS 14. There will be new features to try out right up until iOS 15 comes out next year.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

The bacteria in our gut — a community called the gut microbiome — have been in the spotlight a lot lately. What we're learning about how our intestinal bacteria adapt and grow with our bodies could help athletes perform better, according to researchers starting a company focused on creating probiotics that mimic athletes' microbiomes.

If you have encountered bed bugs lately, you are not alone. While the pesticides used to fight these pests are losing effectiveness, a fungus shows promise in knocking the bugs out of beds everywhere.

In the perpetual search for a renewable and convenient energy source, our bacterial friends have once again stolen the limelight.

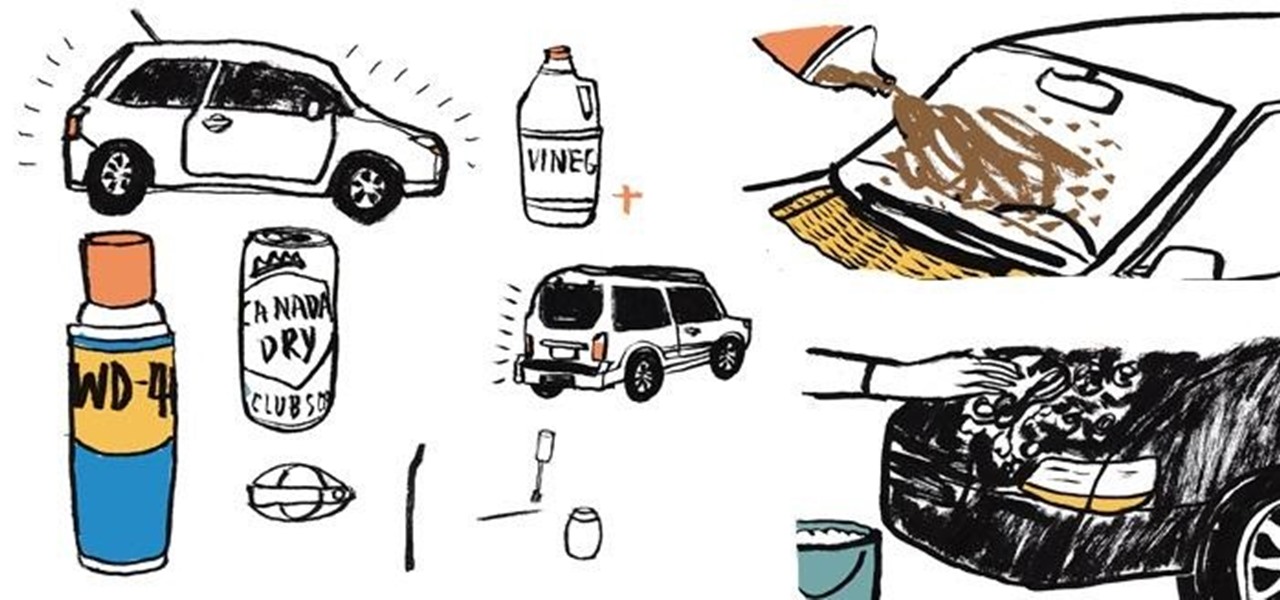
Ever see those cars so covered in dirt, dust, and grime that someone writes "Wash me" on it using their finger? Well, for those cars' sakes, as well as cases less extreme, a word of advice: procrastination is not a solution — it can only compound the problem. Self-cleaning cars are the stuff of the future, not the present, and your car needs attention now.

Have you ever heard a sound when you shut down, boot up, or restart your iPhone? Probably not, but it doesn't have to stay that way.

Apple released the first beta for iOS 14.7 today, Wednesday, May 19. The update (build number 18G5023c) comes two days after Apple seeded testers the RC (release candidate) for iOS 14.6. The new update adds the ability to set timers for HomePod on your iPhone via the Home app.

It's a bit surprising that Apple hasn't seeded beta testers the release candidate for iOS 14.5. The next big iPhone update is rumored to be out soon, so it stands to reason that we'd see a "final" version of that software hit our test devices rather than another beta. But that simply isn't the case here, as Apple decided to release a seventh 14.5 beta.

Mobile augmented reality gaming pioneer Niantic is chomping at the bit to get games like Pokémon GO out of smartphones and onto smartglasses, and it appears to be taking matters into its own hands.

Earlier this month, the rumor mill suggested that Apple was gearing up for a Mar. 23 event, with a possible release of iOS 14.5 to boot. That event, as we can now see, never came to be. It seems Apple is also not quite ready to unveil iOS 14.5, either, as we now have a fifth beta to test on our iPhones.

In response to Apple's implementation of LiDAR sensors in iPad Pro and iPhone 12 Pro models, Google is looking to leverage the dual-camera setups in recent flagship devices as depth-sensing components.

Apple released the second public beta for iOS 14.4 today, Wednesday, Jan. 13. The most notable addition to this beta isn't user-facing — baked into 14.4 beta 2's code is evidence that Apple will start issuing warnings on iPhones using unapproved cameras. Of course, those warnings will only apply to phones that have had their cameras replaced.

While iOS 14.3 is available to everyone right now, Apple is currently working on iOS 14.4 in its beta programs, and the second iOS 14.4 beta just came out for developers. The public beta version of iOS 14.4 beta 2 was released soon after. But what's in these new betas?

Google's 2020 Pixel Buds are one of the hottest true wireless earbuds of the year. With their unique, circular design, they stand out from the long-stemmed AirPods look you get from other wireless earbuds. The design is also sleek and minimal, making them the perfect candidate to use as a personal hearing aid.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

With the best selling phone on Amazon in 2018, Lenovo had big shoes to fill when making the successor of the Moto G6. Fortunately, Lenovo was up to the task. The Moto G7 continues to provide a high performance-to-price ratio, offering a worthwhile upgrade for G6 users while remaining budget friendly.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

Take a close look at the image above. These bugs spread a deadly parasite that infects thousands of people each year. They also live in the US, and it's important to know where they are and whether you need to worry that they're carrying a dangerous infection.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

For the novice cook, fungi can be weird because, well, they're fungi. However, if you've been afraid to get acquainted with mushrooms, you've been missing out. Vegetarians love mushrooms and with good reason.

Apple released the iOS 14.7 RC (release candidate) today, Tuesday, July 13. The new update — and likely official 14.7 release — includes support for Apple's new MagSafe Battery Pack, adds two Apple Card Family options to combine credit limits and share one co-owned account, among other new features and changes.

Apple's iOS 14.5 is the biggest update since iOS 14.0 came out, with over 50 confirmed features and more being discovered every day. There are new emoji, support for AirTags, more privacy controls, and exciting upgrades to Siri, Maps, Reminders, Podcasts, Music, and even Shortcuts. So it wouldn't surprise us if you want to get this on your iPhone ASAP.

Apple just seeded developers the sixth iOS 14.5 beta today, Wednesday, Mar. 31. The update includes a calibration for battery health measurements for the iPhone 11 line, as well as two new Siri voices.

The world of politics can sometimes get a little toxic, but with the new administration, there's already a bit of whimsy creeping back into the online meme space.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

The music you listen to is often a reflection of your personality, which is why people tend to use the artwork from their favorite albums as device wallpapers. But one lonely album cover may not look right on your iPhone's lock screen, and it's not indicative of your broader music interests. To combine cover art into one lock screen background, there's a shortcut that makes it easy to do for any playlist.

Apple just released iOS 14.2 for iPhone, which introduces multiple fun new features and changes. There are 117 new emoji, such as a seal, ninja, bubble tea, and smiling face with tear. Eight new wallpapers can also be found, each containing a light and dark mode variant. HomePod's new Intercom feature appears too. And those are just a few of the things to look out for.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

Buckle up, iPhone users, because it's update time! Apple just released its latest iPhone OS to the public, iOS 14.4. This new edition isn't the company's most ground-breaking, but it doesn't come up short, either — you'll find support for smaller QR codes in Camera, a new "Device Type" setting in Bluetooth, support for a new Apple Watch face, and a major privacy feature, among other new changes.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

While autonomous vehicles are almost assuredly the future of personal transportation, we are likely many years from seeing self-driving cars become as ubiquitous as manually-driven ones, as the auto industry has a myriad of government regulations and other constraints to contend with. Until then, augmented reality is looking like the next big thing in automotive technology.

Apple's latest update, iOS 14.2, is finally here. As the name implies, it's the second major update to hit iPhones since Apple released iOS 14 in the fall. The update brings at least 13 new features and changes to all compatible iPhones, including over 100 new emoji and eight new wallpapers.

Apple's "Spring Loaded" event introduced us to many new and exciting products, including iMac and iPad Pro models with the M1 chip, an upgraded Apple TV 4K, a purple iPhone, and the long-awaited AirTag. However, one of the most anticipated announcements came in the form of a software update — the biggest update since iOS 14.0 and iPadOS 14.0 came out — and that's iOS 14.5 and iPadOS 14.5.

Bash scripting is a convenient way to automate things on any Linux system, and we're going to use it here to automate certain tasks we use all the time.

There are countless tutorials online that show how to use Netstat and Tasklist to find an intruder on your computer. But with a few PowerShell functions, it's possible for a hacker to evade detection from the almighty command line.