
How To: Give Your iPhone Mac-Like Shutdown and Startup Chimes So You Know When It Powers Off and On
Have you ever heard a sound when you shut down, boot up, or restart your iPhone? Probably not, but it doesn't have to stay that way.


Have you ever heard a sound when you shut down, boot up, or restart your iPhone? Probably not, but it doesn't have to stay that way.

Apple released the first beta for iOS 14.7 today, Wednesday, May 19. The update (build number 18G5023c) comes two days after Apple seeded testers the RC (release candidate) for iOS 14.6. The new update adds the ability to set timers for HomePod on your iPhone via the Home app.

It's a bit surprising that Apple hasn't seeded beta testers the release candidate for iOS 14.5. The next big iPhone update is rumored to be out soon, so it stands to reason that we'd see a "final" version of that software hit our test devices rather than another beta. But that simply isn't the case here, as Apple decided to release a seventh 14.5 beta.

Mobile augmented reality gaming pioneer Niantic is chomping at the bit to get games like Pokémon GO out of smartphones and onto smartglasses, and it appears to be taking matters into its own hands.

Earlier this month, the rumor mill suggested that Apple was gearing up for a Mar. 23 event, with a possible release of iOS 14.5 to boot. That event, as we can now see, never came to be. It seems Apple is also not quite ready to unveil iOS 14.5, either, as we now have a fifth beta to test on our iPhones.
In response to Apple's implementation of LiDAR sensors in iPad Pro and iPhone 12 Pro models, Google is looking to leverage the dual-camera setups in recent flagship devices as depth-sensing components.
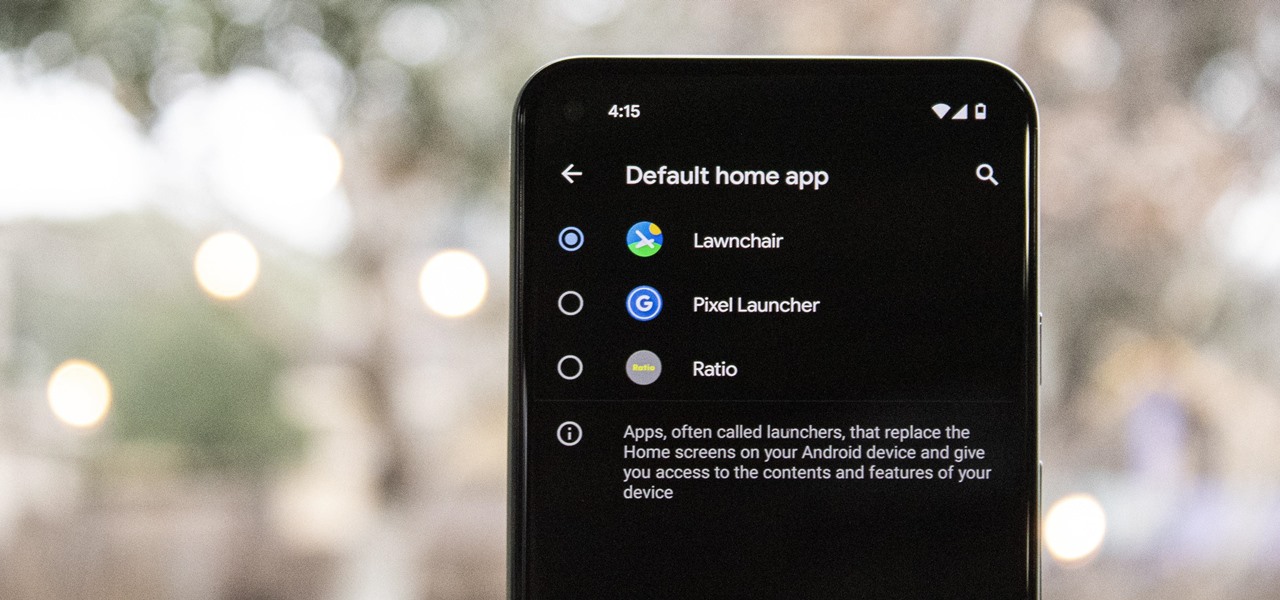
One of the easiest ways to change up your Android experience is by swapping out the stock launcher with a new one. The word "launcher" is Android lingo for "home screen app," and it's a common term because of how easy it is to switch to a new one. So if you're looking to revamp your home screen, this guide's for you.

Apple released the second public beta for iOS 14.4 today, Wednesday, Jan. 13. The most notable addition to this beta isn't user-facing — baked into 14.4 beta 2's code is evidence that Apple will start issuing warnings on iPhones using unapproved cameras. Of course, those warnings will only apply to phones that have had their cameras replaced.

While iOS 14.3 is available to everyone right now, Apple is currently working on iOS 14.4 in its beta programs, and the second iOS 14.4 beta just came out for developers. The public beta version of iOS 14.4 beta 2 was released soon after. But what's in these new betas?

Apple released the "release candidate" for iOS 14.2 today, Friday, Oct. 30. The update is available for both developers and public beta testers, and notably fixes a pressing bug in beta 4 — users would encounter a message telling them to update from their iOS 14 beta, despite no update being available.
Google's 2020 Pixel Buds are one of the hottest true wireless earbuds of the year. With their unique, circular design, they stand out from the long-stemmed AirPods look you get from other wireless earbuds. The design is also sleek and minimal, making them the perfect candidate to use as a personal hearing aid.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

With the best selling phone on Amazon in 2018, Lenovo had big shoes to fill when making the successor of the Moto G6. Fortunately, Lenovo was up to the task. The Moto G7 continues to provide a high performance-to-price ratio, offering a worthwhile upgrade for G6 users while remaining budget friendly.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

Andre was enjoying the carefree life of a 12-year-old with his friends, riding his bike and playing sports, like all kids that age. Schoolwork wasn't hard for him, and his grades showed that.

Take a close look at the image above. These bugs spread a deadly parasite that infects thousands of people each year. They also live in the US, and it's important to know where they are and whether you need to worry that they're carrying a dangerous infection.

Architects are natural candidates to be early adopters of mixed reality. Their trade consists of not only designing buildings and spaces, but also presenting those designs to clients, who then decide that their vision is worth spending thousands (if not millions or billions) of dollars to build in reality.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

For the novice cook, fungi can be weird because, well, they're fungi. However, if you've been afraid to get acquainted with mushrooms, you've been missing out. Vegetarians love mushrooms and with good reason.

Brining is magic. All you have to do is make a mild saline solution, toss in your protein of choice, let it soak, and cook. You end up with incredibly tender, flavorful meat or tofu for very little effort. So why aren't more of us doing it?

Apple pushed out its iPadOS 16.6 update for iPad on July 24, with iPadOS 16.7 following on September 21. While the company is currently working on improving iPadOS 17, we may still see an iPadOS 16.8 update. If that happens, you can try out all the upcoming new features as long as you're OK with running beta software on your iPad.
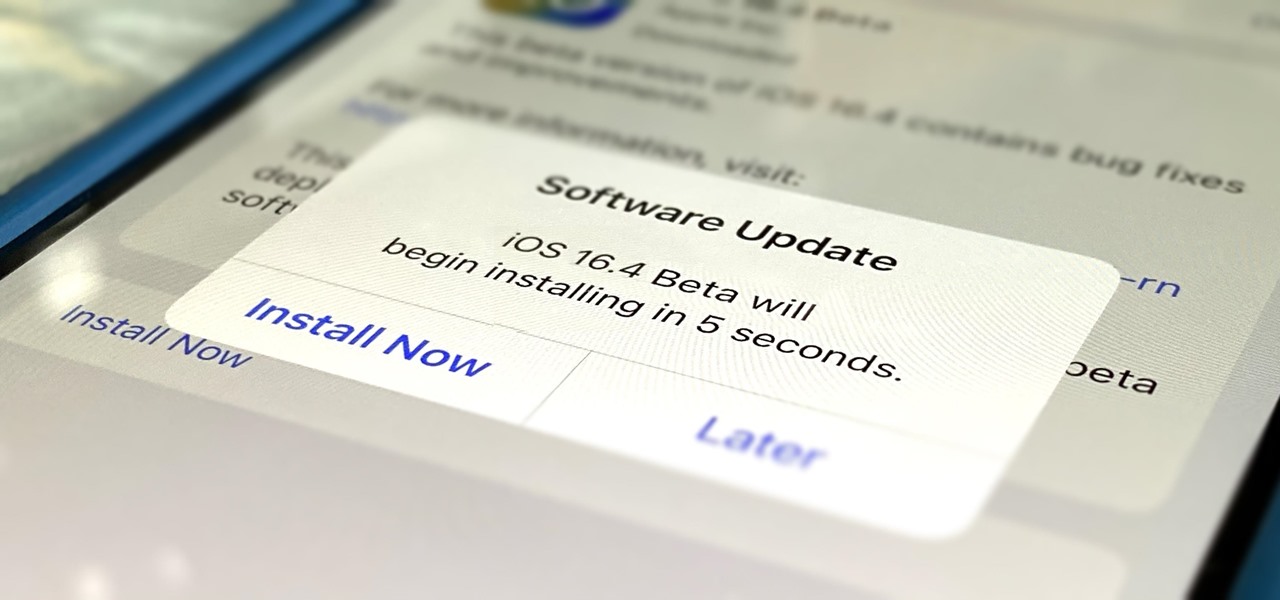
Apple's iOS 16.6 software update for iPhone was released on July 24, with iOS 16.7 following on September 21. While Apple is currently focused on improving iOS 17, we may see iOS 16.8 pop up. When it does, you can try out all the upcoming new features as long as you're OK with running beta software on your iPhone.

Apple released the iOS 14.7 RC (release candidate) today, Tuesday, July 13. The new update — and likely official 14.7 release — includes support for Apple's new MagSafe Battery Pack, adds two Apple Card Family options to combine credit limits and share one co-owned account, among other new features and changes.

Apple's iOS 14.5 is the biggest update since iOS 14.0 came out, with over 50 confirmed features and more being discovered every day. There are new emoji, support for AirTags, more privacy controls, and exciting upgrades to Siri, Maps, Reminders, Podcasts, Music, and even Shortcuts. So it wouldn't surprise us if you want to get this on your iPhone ASAP.

Apple just seeded developers the sixth iOS 14.5 beta today, Wednesday, Mar. 31. The update includes a calibration for battery health measurements for the iPhone 11 line, as well as two new Siri voices.

The world of politics can sometimes get a little toxic, but with the new administration, there's already a bit of whimsy creeping back into the online meme space.

Apple's first release candidate for the iOS 14.3 beta came out on Dec. 8, but there must have been a serious bug in the system because iOS 14.3 RC 2 followed it just two days later on Dec. 10. These builds highlight everything that you should expect to see on the stable version very soon.

The COVID-19 pandemic has practically shut down all sports except for World Wrestling Entertainment, which has continued staging matches without an audience, leaving us sports fans with nothing much to cheer for. While they can't replace live games, smartphone games provide an alternate reality to live out our competitive entertainment in the absence of the real thing.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

If you're on the hunt for a profitable side-gig, or even a completely new way to to make money, you'll want to take a look at Upwork, a leading freelancing platform that connects skilled freelancers with clients from all over the world.

The music you listen to is often a reflection of your personality, which is why people tend to use the artwork from their favorite albums as device wallpapers. But one lonely album cover may not look right on your iPhone's lock screen, and it's not indicative of your broader music interests. To combine cover art into one lock screen background, there's a shortcut that makes it easy to do for any playlist.

Apple just released iOS 14.2 for iPhone, which introduces multiple fun new features and changes. There are 117 new emoji, such as a seal, ninja, bubble tea, and smiling face with tear. Eight new wallpapers can also be found, each containing a light and dark mode variant. HomePod's new Intercom feature appears too. And those are just a few of the things to look out for.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

From Farmville to selling a company to Google, Amitt Mahajan has been through the startup ringer. Now, as managing partner with Presence Capital, he's funding the future of augmented and mixed reality.

Apple's iOS 18 and iPadOS 18 have been out since September, but more features are coming, and you can test them after installing a beta build for iOS 18.3 or iPadOS 18.3.

Apple's new iOS 14.5 will be coming out very soon, and that's even more evident now with the release of the iOS 14.5 Release Candidate (RC) on Tuesday, April 20. Anyone can install this update and get all of the same features iOS 14.5 will give everyone for iPhone; only you'll have a head start to using all of the updates in Maps, Music, Podcasts, Reminders, Shortcuts, Siri, and more.

Buckle up, iPhone users, because it's update time! Apple just released its latest iPhone OS to the public, iOS 14.4. This new edition isn't the company's most ground-breaking, but it doesn't come up short, either — you'll find support for smaller QR codes in Camera, a new "Device Type" setting in Bluetooth, support for a new Apple Watch face, and a major privacy feature, among other new changes.

Automation has been a buzz word for quite some time now, but the principles behind it are as strong as ever. For a hacker or pentester, Bash scripting is one form of automation that cannot be ignored. Virtually any command that can be run from the terminal can be scripted — and should be, in many cases — to save valuable time and effort. And a Bash script just happens to be great for recon.