Now that we've officially seen the HoloLens 2 and Microsoft has shown off the improvements and new superpowers of the augmented reality headset, what about the specs?
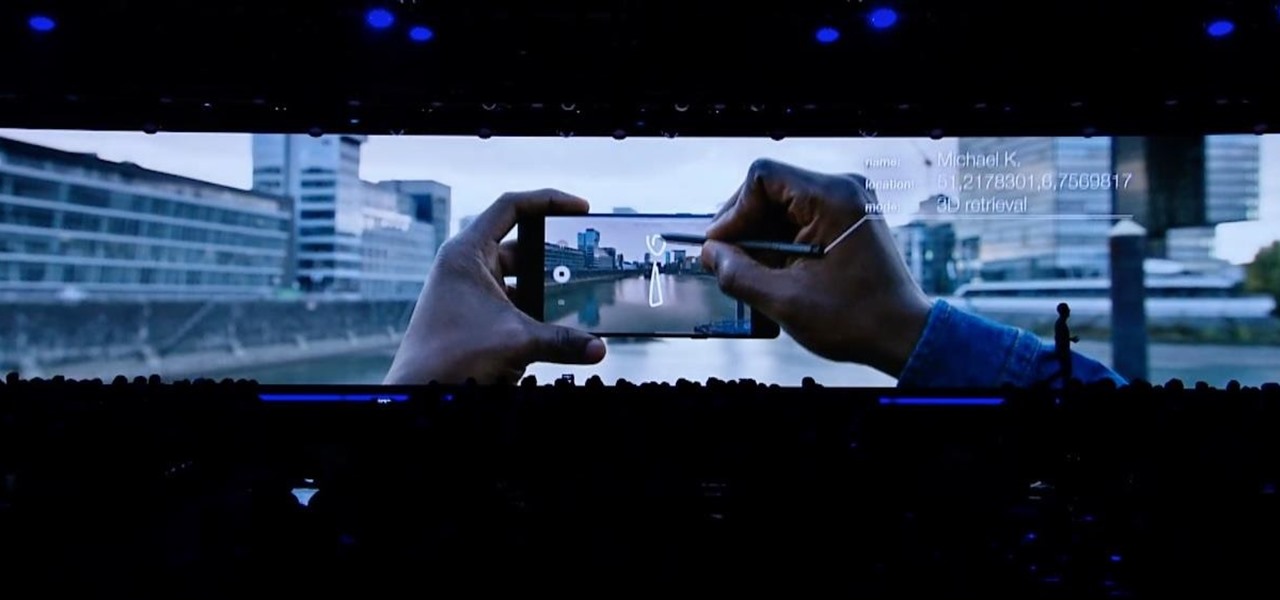
This week, at its developer's conference, Samsung took the wraps off a new tool from Wacom that bestows the S-Pen with AR powers, as well as its own entry to the AR cloud market called Project Whare.

Despite the launch of ARKit a year ago, and ARCore this year, a true killer app has not arrived for either platform, that's according to the head honcho for one of the leading development environments for 3D applications.

The rumors are still hot that Apple might include an 18-watt USB Type-C power adapter with the upcoming iPhone lineup so that there's fast-charging capability right out of the box. Leaked photos have surfaced that substantiate this rumor, though, they could also be fake. But how would ditching the old-style 5-watt USB Type-A power cube affect you if it's true?

While numerous startups are competing to convert the AR Cloud from a pie-in-the-sky to a reality, Wikitude is thinking smaller with the latest edition of its augmented reality SDK.

Some of the big guns developing augmented reality technology fired shots at their competitors with announcements and leaked plans this week.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

Kali Linux is known as being the de facto penetration-testing Linux distribution but can be a pain to use as an everyday OS — even more of a pain if that means carrying around a second laptop or the constant frustration of using the finicky Wi-Fi on virtual machines. But there's another option: installing a Kali subsystem on your Windows computer as a convenient compromise.

Earlier this year, Nokia released the Nokia 8 Sirrocco overseas. The new device served as an upgrade to the 2017 model with a minor specs bump and a more modern design. However, HMD isn't done with the 8 series. A rumored Pro version is coming later this year that brings innovations the iconic brand is known for.

MoviePass may be popular with filmgoers on a budget, but it might not be with those of you who are concerned about your privacy, since MoviePass may be logging your location data even when you don't expect the app to do so.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

Despite longer live spans, almost half a million people die of healthcare-associated infections (HAIs) each year, many of them preventable.

Forget Waymo, Uber, Tesla, and other other heavily mediatized driverless contenders — German premium carmaker Audi AG has become the first OEM to introduce a Level 3 car sold in retail channels.

Look no further than Flint, Michigan, to discover the serious consequences of contaminated drinking water. Around the world, water polluted by pathogens and toxins sickens people or cuts them off from safe drinking water. Looking for a solution, researchers created tiny, swimming robots that pack a powerful punch against waterborne pathogens.

Could your fever, body aches, cough, and sore throat be the flu? Soon, finding out may not involve a trip to the doctor.

Long admired for their active and cooperative community behavior, some types of ants also wear a gardening hat. Nurturing underground fungus gardens, these ants have a win-win relationship that provides food for both ants and fungi. If we humans understand it better, it may just help us out, too.

The ability of one microbe to adapt is giving it a whole new career as a sexually transmitted disease. Usually content with the back of the throat and nose of those who carry it, the dangerous pathogen Neisseria meningitidis has adapted to cause an illness that looks a lot like gonorrhea.

To keep fungal pathogens at bay in their crowded homes, wood ants mix potions to create powerful protection for their nest and their young.

The Great Barrier Reef in Australia is the largest living system on the planet. Yet more than 90% of the reef is bleaching because of the loss of a tiny algae that lives within the coral.

For regions that experienced a boom in mouse populations last year, scientists say 2017 could see a surge in cases of Lyme disease.

Maternal infection with genital herpes, or other pathogens, during early pregnancy could increase risk of autism, or other neurodevelopmental disorders, says a new study.

Avian flu is making the news again with new human cases in China reported in January. What does "avian flu" mean to you—and how dangerous is it?

Although their effectiveness is waning, antibiotics remain a front-line defense against many infections. However, new science reveals using the wrong antibiotic for an infection could makes things much worse.

Disengagement report numbers for self-driving car testing in 2016 on public roads in California were just released, and the biggest point we can make about them is that Waymo is very far ahead of their competitors in almost every metric.

New weapons are needed to combat antibiotic-resistant bacteria. Instead of drugs, scientists have discovered in an animal study that they may be able to harness vampire bacteria to vanquish pneumonia.

When the time comes to replace your car, you most likely have a checklist of criteria that you would like on the new one. Your car is possibly the most expensive possession you have—or the second-most expensive, after your home—so you want to make sure that you are not only getting what you want, but that you are getting the best deal possible.

Last week it was announced that Waymo, the former Google Self-Driving Car project, had graduated from Alphabet's X innovation center. This graduation had been in the cards for many months with senior members of the project team and X hinting that it would be soon.

While visiting the Made by Google pop-up shop in New York City this morning, I had a chance to try out the new Daydream View virtual reality headset. First impressions are important, and Google's new mobile VR product makes a good one. The headset is made of a soft fabric that most evokes a beloved old college sweater that's well worn but properly cared for. The demo only featured the Slate (darker gray) model, though customers will ultimately be able to choose from either Slate, Snow, and Cr...

Welcome back, my greenhorn hackers! In many cases when a computer, phone, or mobile device is seized for evidence, the system will have graphic images that might be used as evidence. Obviously, in some cases these graphic images may be the evidence such as in child pornography cases. In other situations, the graphic images may tell us something about where and when the suspect was somewhere specific.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

Many people deal with motion sickness on a daily basis, and if you're reading this, chances are you're one of them. Kinetosis can make your stomach roll, your entire body sweat, and make you feel fatigued and dizzy at even the slightest movement, whether it's related to carsickness, seasickness, or airsickness. And let's not forget the worst part—vomiting.

Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.

Doxing is the act of finding one's personal information through research and discovery, with little to no information to start with. You may have seen doxing in the news, for instance when not so long ago, hacker team Anonymous doxed and reported thousands of twitter accounts related to ISIS. Doxing can be useful for finding the address of a coworker, or simply investigating people on the internet. The tutorial I will provide to you now will teach you the basics of doxing and how you can prot...

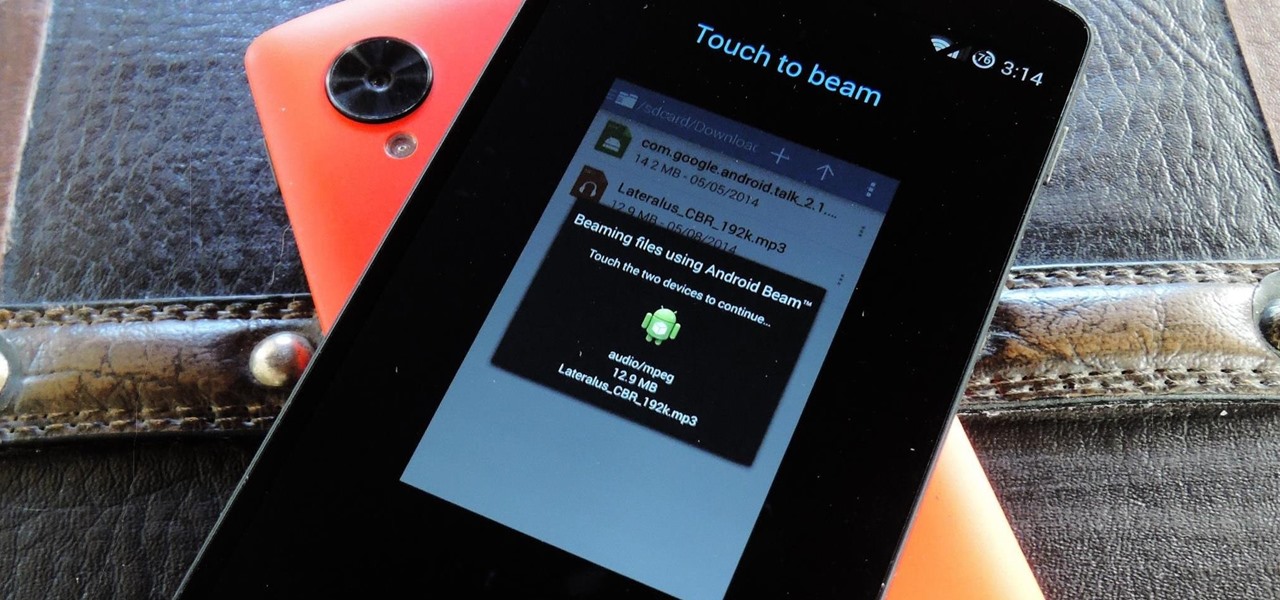
Your Nexus 5 comes with a pretty cool feature baked in called Android Beam. Using NFC, or Near Field Communication, this functionality allows you to send information to another compatible device by simply touching the two together. Most flagship devices have NFC built into them these days, so there is a broad range of devices that your Nexus 5 is capable of sharing information with wirelessly.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.

Welcome back, my budding hackers! In my continuing series on Linux basics for aspiring hackers, I now want to address Loadable kernel modules (LKMs), which are key to the Linux administrator because they provide us the capability to add functionality to the kernel without having to recompile the kernel. Things like video and other device drivers can now be added to the kernel without shutting down the system, recompiling, and rebooting.

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).