Robert Templeman from the Naval Surface Warfare Center in Crane, Indiana and several of his friends from Indiana University recently developed an Android application that is capable of gathering pictures and videos from mobile devices in order to reconstruct a user's environment in 3D. The malware would come coded inside of a camera application that the user would download. The malware, called PlaceRaider, would then randomly take pictures throughout the day and carefully piece them together ...

In the following video, I demonstrate how to create a device capable of charging the body of anyone who wears it with static electricity, allowing a powerful shock to be discharged into anything that is touched. This grants the wearer the ability to do some pretty amazing things, some of which are shown in the first segment of the video.
Saw is no longer just a movie, it's a video game, and you can play it on the Xbox 360, PlayStation 3, and Windows. With this video walkthrough series from Committed Gamers, you can BEAT IT (for the Xbox 360).

All you science and astronomy nuts out there, pay attention, this detailed video tutorial series will tell you everything you need to know about using the Meade EXT Backpack Telescope to ogle the universe.

YouTube user diabeticHOWIE instructs you on how to enable MMS (Multimedia Messaging) for your iPhone 3G or 3GS. He claims that this may not work for the first generation iPhone. Using his step-by-step tutorial, you will be able to send multimedia messages to your friends and family.

This truck repair video shows you how to remove the bed from a Chevrolet C1500 W/T truck. This needs to be done to fix certain problems, in this case the fuel lines. Whatever reason you need to remove the bed from your Chevy, this video shows you how to do it properly.

Don't buy those $100+ laser pointers. Watch this video, and for under $50 you can make your own that is capable of burning, popping balloons, and cutting things!

The biggest win in the race for consumer augmented reality smartglasses to date belongs not to Apple, Facebook, or Google, but Snapchat's parent company, Snap.

After piloting the Nreal Light in South Korea and Japan via carrier partnerships and securing another round of funding, Nreal is now ready to begin selling the consumer edition of the smartglasses to the western world as well as introduce a version for enterprise customers.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

You might think you need to buy a thousand dollar phone to get a great experience while streaming movies and TV shows from services like Netflix, Hulu, and YouTube, but that's just not true anymore. While phone prices keep rising and the midrange segment now ranges from $300–$500, there are still cost-effective options that come with top-notch displays and media features.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

Augmented reality is beginning to leak out into the mainstream world. This is thanks, in part, to ARKit and ARCore. These releases turned the current smartphones owned by millions of Apple and Android users into AR-capable machines. And while there are definitely some awesome use cases for mobile AR, the real future in AR is headworn.

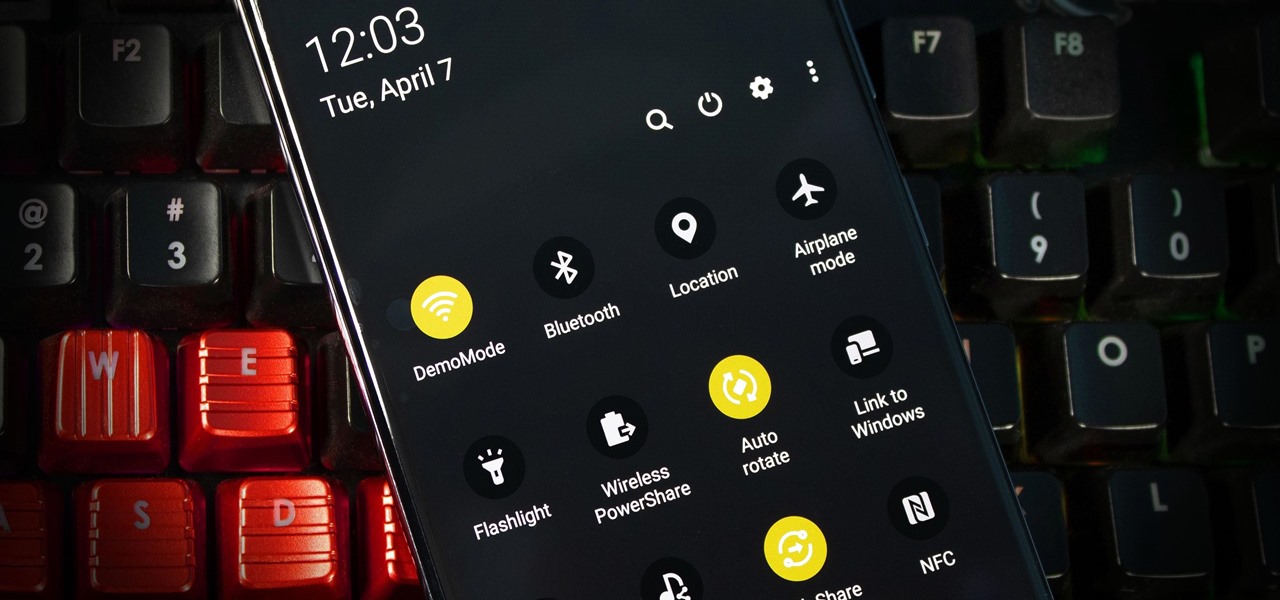
These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

HP has you covered with Mobile printing. With printers like the Officejet H470wbt and the PS A820 you can print on the go.

There is plenty of evidence to suggest that learning to program is becoming a highly lucrative and useful skill. Monster.com called coding "the skill you need today" if you want a job in some of the highest-paying fields out there. If the last year has proven anything, working online requires a strong digital infrastructure that someone has to help build. That someone can, and should, be you.

Every Galaxy S20 sold in the US — even the S20+ and S20 Ultra — simply can't be rooted. With the bootloader permanently locked, you miss out on the world of rooting and the customization it opens up, but modifications are still possible.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

If you just got a new iPhone, chances are you picked up the iPhone 11, successor to the iPhone XR, the most popular device in Apple's 2018 series. Since the XR did so well, it was predicted that the iPhone 11 would too, and so far, it has lived up to that prediction, beating the 11 Pro and 11 Pro Max in sales in 2019.

As excitement looms for Apple's annual parade of pomp and circumstance for its latest lineup of iPhones, some hidden hints in an internal build of iOS 13 has Apple enthusiasts salivating for what Cupertino is testing in the AR wearables realm.

Just when we thought the AT&T partnership with Magic Leap wouldn't really take off until the latter launched a true consumer edition of the Magic Leap One, the dynamic duo jumped into action this week to offer the current generation headset to customers.

Current-generation mobile augmented reality apps offer users numerous opportunities to punch up photos and videos with 3D content, but there's surprisingly few options for users to express themselves using virtual characters.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

Ever since the announcement of the Razer Phone, a wave of gaming smartphones started to hit the market. With ASUS being such a big name in gaming, it made sense for them to throw their hat in the ring. The result is the ROG Phone. And with this first try, ASUS has topped the rest, creating a gaming phone others should try to emulate.

This week, Next Reality published profiles on the leaders in augmented reality hardware industry, with Magic Leap CEO Rony Abovitz topping the list. So, it should be no surprise that two app makers want to align themselves with Magic Leap's flagship product.

If you haven't heard, another big OEM has decided to drop the headphone jack. OnePlus, the hero of the people, has just announced that the OnePlus 6T will not have the popular port. With this decision, audiophiles and others are limited to just three big-name options.

When rumors first emerged of Sony's Xperia XZ3, many of us wondered why. With the Xperia XZ2 just releasing in April of this year, why is Sony already releasing its successor? But now that it is officially announced, it makes a bit more sense, as what Sony is calling the XZ3 is actually more like the XZ2S.

Although the Magic Leap One: Creators Edition is currently officially available in only six US cities, those living outside of Magic Leap's designed US cities now have a roundabout way to order the device.

One of the latest trends in Instgram is breaking up larger videos into more digestible clips to use in stories. Stories max out at 15 seconds, making it a pain to show anything meaningful in that short time frame. Fortunately, you can virtually extend the duration of your Stories on both your iPhone and Android phone.

While numerous startups are competing to convert the AR Cloud from a pie-in-the-sky to a reality, Wikitude is thinking smaller with the latest edition of its augmented reality SDK.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

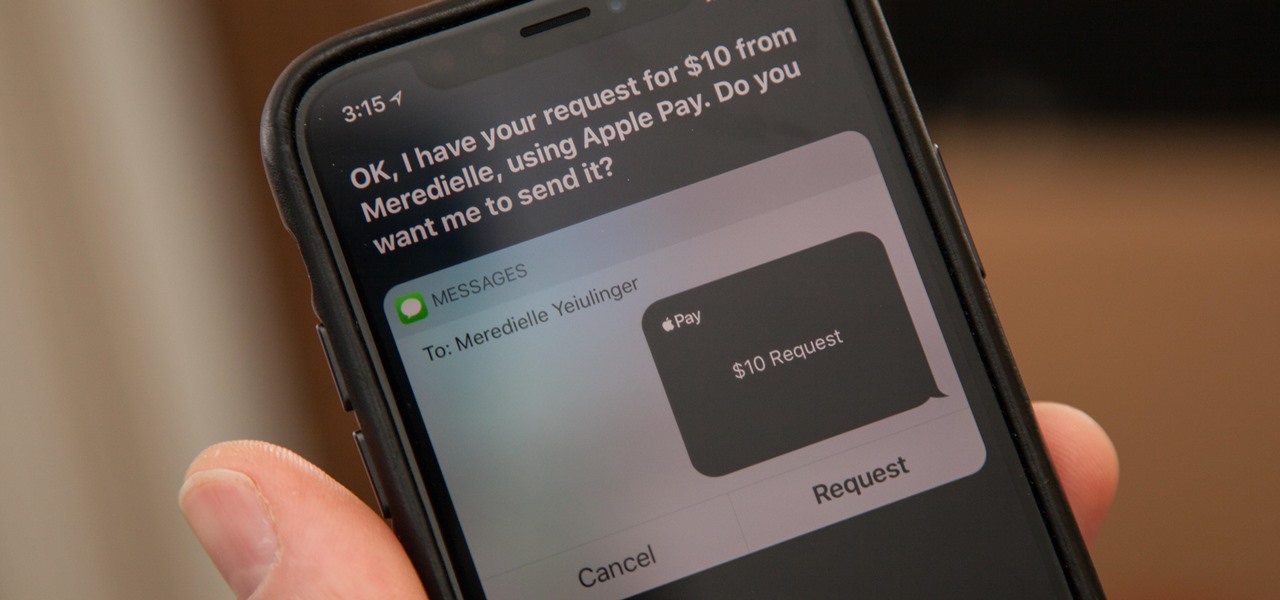
You might be proficient at sending your family and friends money using Apple Pay Cash on your iPhone, but what about when you need some digital currency in your wallet to buy in-app purchases or to get back the money you spent on someone's lunch? Requesting some Apple Pay Cash can be done a few different ways, none of which are hard.

With four major carriers, buying an iPhone X or iPhone 8 can be more complicated than you'd think. While Apple has its own iPhone upgrade program, AT&T, Sprint, Verizon, and T-Mobile all have versions of their own. Which plan you choose depends on your needs and, of course, your carrier. However, getting around to upgrading can be challenging to say the least.

As a self-proclaimed chocoholic, any day with chocolate mousse in it is a good day in my book. And thanks to prominent chemist Hervé This, one of the founding fathers of molecular gastronomy, chocolate mousse is not only easy to make every single day—but only requires two ingredients.

Chris' Outrageous Cheesecake, a decedent combination of chocolate cake, brownies, cheesecake, and coconut-pecan frosting, is easily one of The Cheesecake Factory's most popular desserts. But, the price of fulfilling your cravings for this addictive treat can get up there (at about $8 a slice), and when you eat it at the restaurant you likely are limited to only one small piece.

While a hot dog with all the typical American condiments (ketchup, mustard, relish) is heavenly for kids, as an adult, I realize there is nothing wrong with switching things up a bit and getting creative. In fact, a plain hot dog can be a fantastic blank canvas for chefs to work with—a great, edible example of going from drab to fab.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.