While photography usually gets all the love, our phones have gotten really good at capturing video. Think about it — when was the last time you needed a camcorder for a vacation? With mobile cameras getting better each year, we're now at a point where smartphones can be used for pro-level videography.

If you haven't heard, another big OEM has decided to drop the headphone jack. OnePlus, the hero of the people, has just announced that the OnePlus 6T will not have the popular port. With this decision, audiophiles and others are limited to just three big-name options.

When rumors first emerged of Sony's Xperia XZ3, many of us wondered why. With the Xperia XZ2 just releasing in April of this year, why is Sony already releasing its successor? But now that it is officially announced, it makes a bit more sense, as what Sony is calling the XZ3 is actually more like the XZ2S.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

In the recent hit movie Furious 7, the storyline revolves around the acquisition of a hacking system known as "God's Eye" that is capable of finding and tracking anyone in real time. Both the U.S. spy agencies and an adversarial spy agency (it's not clear who the adversary is, but the location is "beyond the Caucasus mountains," which could imply Russia?) desperately want their hands on this system.

Both the Galaxy S6 and S6 Edge have had root methods available to them before the phones were even released, but the problem with these existing root methods is that they would trip the KNOX counter on your device.

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

No one wants to appear stupid. Whether you rely on lengthy, complicated vocabulary to show your smarts, or enjoy highlighting your speedy mental math skills, everyone prefers emphasizing intelligence over hiding it.

When the Chromecast first came out about a year ago, developers were quick to find a way to root the streaming device. Google was almost as fast, however, in updating the Chromecast's firmware to close the loophole that this method used.

Since the day of the Xbox 360 release, storage space for the device has been overpriced beyond belief. OEM 250GB HDD models still cost $110 USD! A 250GB hard drive should not destroy my wallet, Microsoft. Storage space, especially on HDDs, is cheap. You can buy a removable 2TB external for only $100 USD, so it's a little beyond my comprehension to see how they calculate their MSRP to yield such a large profit. On the other hand, Xbox 360 had very impressive hardware specs back in the day, equ...

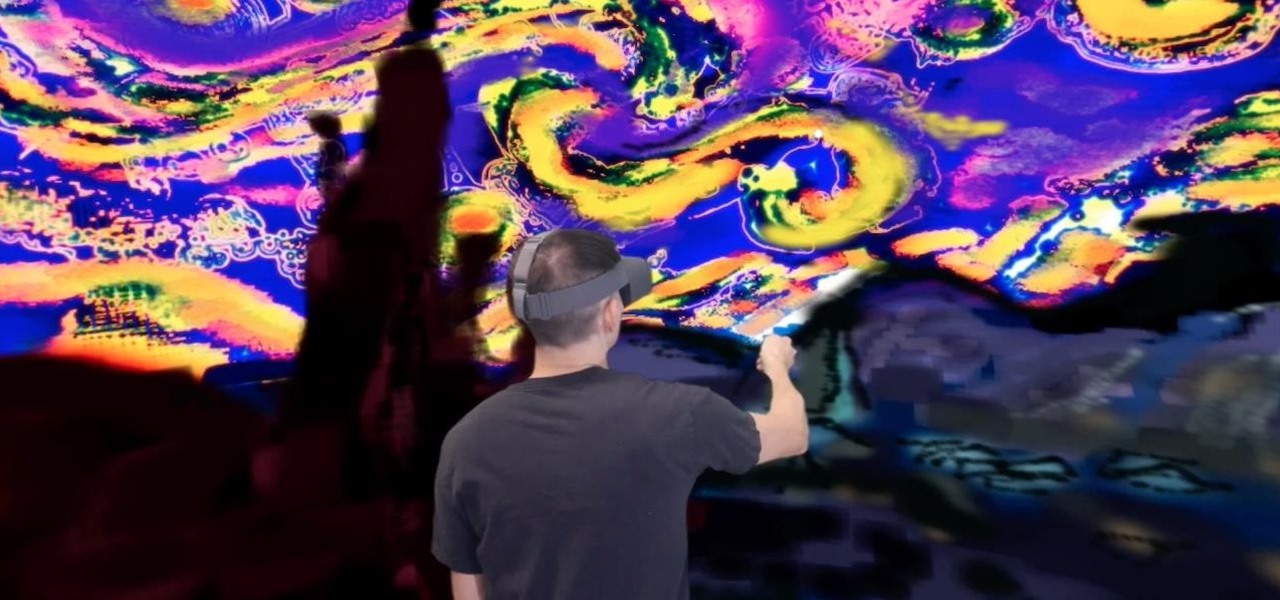
High-end augmented reality devices like the HoloLens and the Magic Leap 1, as well as the Ultraleap motion tracking modules, have demonstrated robust hand-tracking capabilities. However, many AR wearables (including Magic Leap) still rely on handheld controllers for interactions in AR space.

The iPhone 12, 12 mini, 12 Pro, and 12 Pro Max are capable of shooting 4K video using HDR with Dolby Vision, producing content unthinkable in an Apple smartphone just years ago. That said, it's quite easy to miss the full potential of your iPhone's camera, iPhone 12 or not. If you want the best quality video possible on the iPhone XS and newer models, make sure you don't make this one mistake.

For over three decades, Microsoft's landmark program, Excel, has helped businesses accomplish tasks and problem solve quickly and efficiently. Whether you're a budding entrepreneur or navigating a remote career, Excel can help you apply your business skills at a higher level.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

When Samsung announced its new Super Fast Charging 2.0 system was based on USB PD, the industry rejoiced. By using an open standard, Galaxy users could pick from hundreds of third-party chargers in addition to first-party options from Samsung. Trouble is, this never came to fruition.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

The cosmetics brands are among the earliest adopters of augmented reality, using virtual try-on tools to preview shades of makeup before buying.

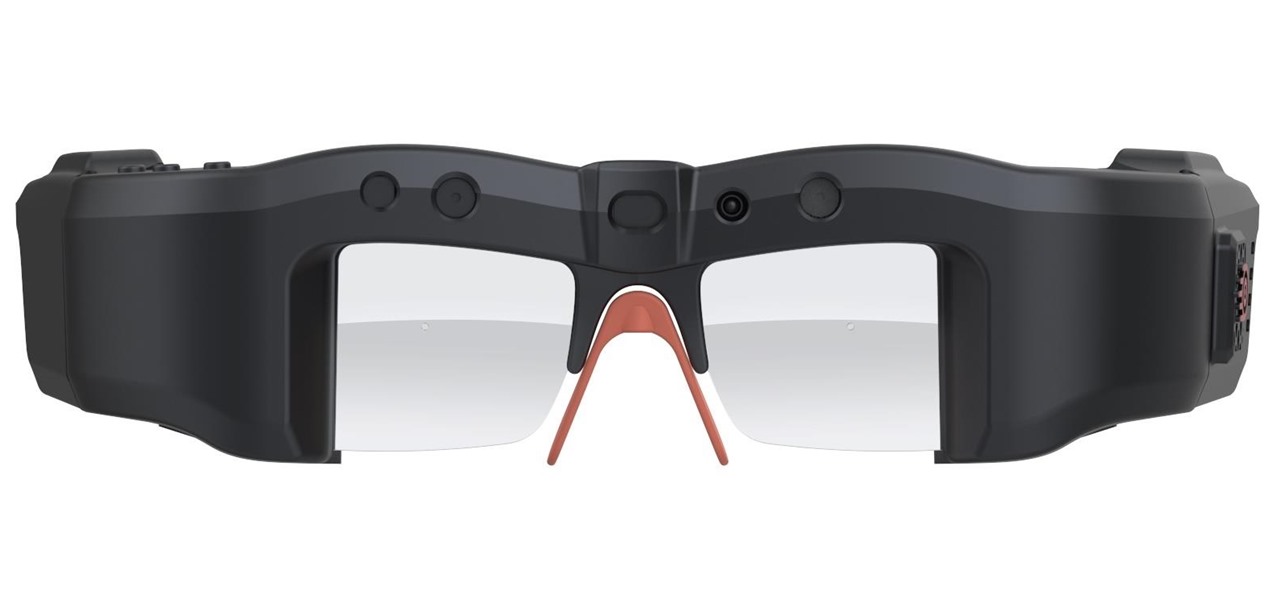
With big-name tech companies like Apple and Facebook gearing up to push out their own smartglasses in the coming years, engineering conglomerate Bosch has been working on the optical components that could help the competition catch up.

Sorry, Galaxys S11–19, Samsung's jumping straight to Galaxy S20 this year. They're also going with essentially three base models before accounting for niche variants. Of these three models, it's clear which one's the best: the Galaxy S20 Ultra.

Now that iOS 13 is in the wild, developers are starting to show off the magical augmented reality powers ARKit 3 can deliver.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

We last saw China-based augmented and virtual reality headset maker Shadow Technologies at last year's Augmented World Expo, where they had the Action One, one of the wildest augmented reality headsets we've seen, on display.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

With the best selling phone on Amazon in 2018, Lenovo had big shoes to fill when making the successor of the Moto G6. Fortunately, Lenovo was up to the task. The Moto G7 continues to provide a high performance-to-price ratio, offering a worthwhile upgrade for G6 users while remaining budget friendly.

Augmented reality wearables maker ThirdEye Gen, Inc. has officially released what it claims are the "smallest mixed reality glasses" in the X2, which will be available for hands-on demonstrations at the company's CES 2019 booth this week.

Google's next-gen cellular carrier, Google Fi, which replaces Project Fi, is making waves across the mobile industry. With super-cheap plans starting at only $20 and the ability to connect to millions of Wi-Fi hotspots across the globe, it's tempting many users to make the switch from AT&T, Sprint, T-Mobile, and Verizon Wireless.

While the next-generation HoloLens does not have a launch date yet, we now have a better idea of how big a leap the device will take in terms of depth sensor performance.

If you find yourself on the run from the Empire, you no longer need a droid to send a holographic distress message, you just need an iPhone X and the HoloBack app.

Apple continues to build its augmented reality hardware and software team in stealth mode. The latest addition comes via the hiring of a former DAQRI user experience designer and VR app developer.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

Google's Pixel smartphone had a decent head start as one of the first devices to offer ARCore, but that early exclusivity has been frustrating for some Android device owners. Some of that frustration was relieved when Google added more Android devices to the ARCore list in February.

While Apple has generally been more bullish on augmented reality as opposed to virtual reality, the latest whispers about its purported AR headset suggests that it may be giving VR another look.

Do you see a red door and wonder if it might be a good idea to paint it black? You could "ask Ask Sherwin-Williams," or, better yet, you could just ask the new augmented reality features in the retailer's mobile app.

Augmented reality hardware maker Avegant has reportedly laid off between 20 and 30 employees, with founder Edward Tang returning to the CEO role at the company.

The research team at Google has found yet another way for machine learning to simplify time-intensive tasks, and this one could eventually facilitate Star Wars-like holographic video.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

When it comes to finding lost things, the joke goes that it's always in the last place you look. With an assist from ARKit, Pixie can make your iPhone the first and last place you look for that missing item.

Over the weekend at IFA 2017 in Berlin, Huawei introduced the Kirin 970 processor, the first of its kind to include artificial intelligence baked into the chip.