It's truly amazing how far smartphone camera hardware has come in such a short period of time. It took roughly 5 years to advance the image processing capabilities from a pixelated mess to the crisp and clear photos we can take today. This reaches well beyond the megapixel spec race, since camera modules these days sport vastly improved optics, wider aperture, and even larger pixel sensors that capture more light.

Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

When it comes to added features, no manufacturer out there can hold a candle to Samsung. Whether it's a remote control for all of your electronics, a heart rate and stress level monitor, or a seemingly-magical stylus, Galaxy devices always have as much functionality as possible packed in.

Sometimes, we need to record outdoors for our film making. Perhaps we need an audio clip of a babbling brook, or perhaps just ambient noise. This instructional filmmaking video covers some tips for capturing good sound when shooting outdoors.

This is a discussion of a tricky line against the Stonewall, the Horowitz Defense (2...Nf6 3.Bd3 Nc6). White allows Black to spend three moves capturing the light squared Bishop and bringing White's pawn from c2 to d3, preventing a ...Ne4 invasion. This makes for very dynamic play.

Slow motion recording is an incredibly handy feature that works by capturing moments at a higher frame rate than they're played back at. Timing is everything when recording in this setting, so if you want a user-friendly app that keeps device interactions to a minimum and leaves you to focus on capturing your subject, Google Camera will surely fit the bill.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

Hi, dear co-apprentices and wise masters. I've been recently trying to learn the basics to hacking here, and I've read all guides on Wi-Fi hacking and noticed no word is dedicated to this awesome script that comes bundled with Kali!

I've been using the Photo Sphere Camera from Google on all of my Android devices ever since it came out on Jelly Bean 4.2, which lets me create riveting 360° panoramic images.

As part of its ARCore release announcement, Google also revealed a forthcoming app that's sure to excite those who celebrate '80s pop culture.

As interest in augmented and virtual reality continues to grow, so does the need to bring objects from the real world into virtual space. With that, there's also now an increased need for solutions that bypass the time-consuming process of producing handmade 3D models.

Believe it or not, capturing a beautiful shot of a vehicle is more difficult than you think. Sure, you can just snap a photo, but capturing the design, detail, and essence of the car is a whole other story. Lighting, location, settings, and angles are play into how well the photographic representation turns out.

With the ever-evolving technology that imbues photography, we are never short of fantastic awe-inspiring shots. Digital cameras can capture things that the naked eye only wishes it could see, like streaking lights, rapid movements, and faraway objects, and it's fairly easy to capture these things if you know the basics.

This seven part tutorial shows you the basics of using Sony Vegas video editing software. If you haven't used this software, or any other video editing software, this series will go over the basics you need to know. Part one covers the interface, two covers importing files, three covers adding sound, four covers adding effects, five and six cover rendering, seven covers capturing video.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

UPDATED 5/4/17: SI has stated that they won't be augmenting its Swimsuit Edition. Although, this could be a sign that the company may do so in the future. If they already have all the tech set up for the latest feature, then they are already half way ready to augment other SI editions. So get ready SI fans and download the designated Life VR app, because you are going to need it to point it at these specially marked SI pages.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Long-exposure photography gives us the ability the capture some pretty amazing shots by delicately capturing moving elements in an image while keeping the shutter open at a slow speed. While that's great for things like traffic, scenery, and carnival rides, it can come in especially handy for 4th of July fireworks.

While many of the features in the iPhone 16 and 16 Pro series build on what we've seen in previous iPhone models, Apple has packed the 2024 lineup with iOS 18 and plenty of fresh upgrades worth considering.

The Snapdragon 820 and 821 were met with praise last year, receiving almost no complaints compared to their overheating predecessor, the Snapdragon 810. But now, all eyes are on Qualcomm to see what goodies they have in store for us this year, as their new SoC, the Snapdragon 835, will be revealed this week at CES 2017.

Being in your twenties is tough. You're not a child anymore, but also not quite a full-fledged "adult" yet. Sure, you do adult things like cook asparagus sometimes, but you're also sweating about securing enough likes on your social media posts.

Video: . Steel wool fire Photography

Chance are, you or someone you know is that person in the gym: flexing in front of a mirror, posing for the perfect photos to show off your workout results. But finding the right picture is hard. The thing is, it doesn't need to be.

Because timing is everything, the latest entry in the location-based augmented reality gaming sweepstakes, Ghostbusters World, has arrived just in time for Halloween.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

Thanks to its advanced cameras, the Galaxy S9 can capture videos at an astonishing 960 frames per second (fps). To put it in perspective, you now have you the ability to record the world around you in ways that previously required expensive professional camera equipment. And that's just the tip of the iceberg.

It seems like each day new rumors and leaks come out for Huawei's upcoming P series devices. Everything from its name change to its specs has been leaked, sometimes with contradicting rumors. One of the biggest leaks is the inclusion of triple rear cameras, a first for smartphones.

With the release of Object Capture this fall, Apple is giving everyone with a Mac and a camera the means to create their own 3D objects.

While Snapchat augmented reality often embraces pop stars like Drake and Ariana Grande, a couple of bands from the louder side of the music industry have found a home with Facebook.

While a new museum to house the original torch of the Statue of Liberty is under construction on Liberty Island and scheduled to open in May 2019, New York Times readers can now view the sculpture in their own space through augmented reality.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

The latest augmented reality feature from The New York Times gives readers a close-up view of the damage left behind by the eruption of Volcán de Fuego in Guatemala earlier this month.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

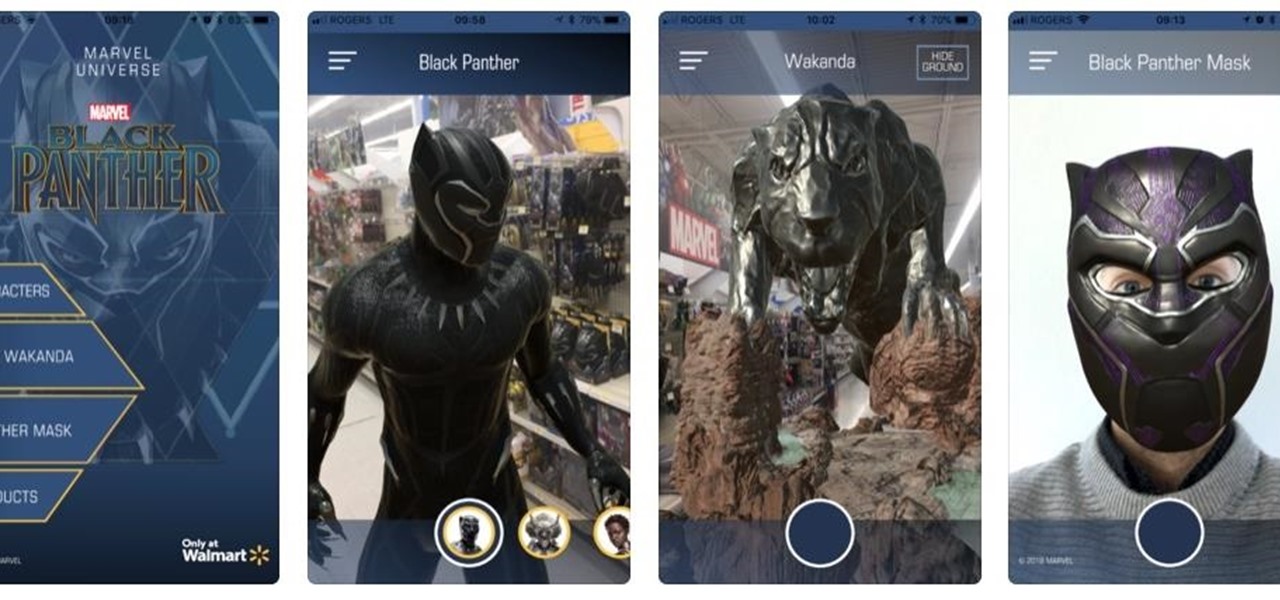
Marvel and Walmart are looking to capitalize on the uber-successful Black Panther film with a mobile augmented reality app designed to push the franchise's merchandise.

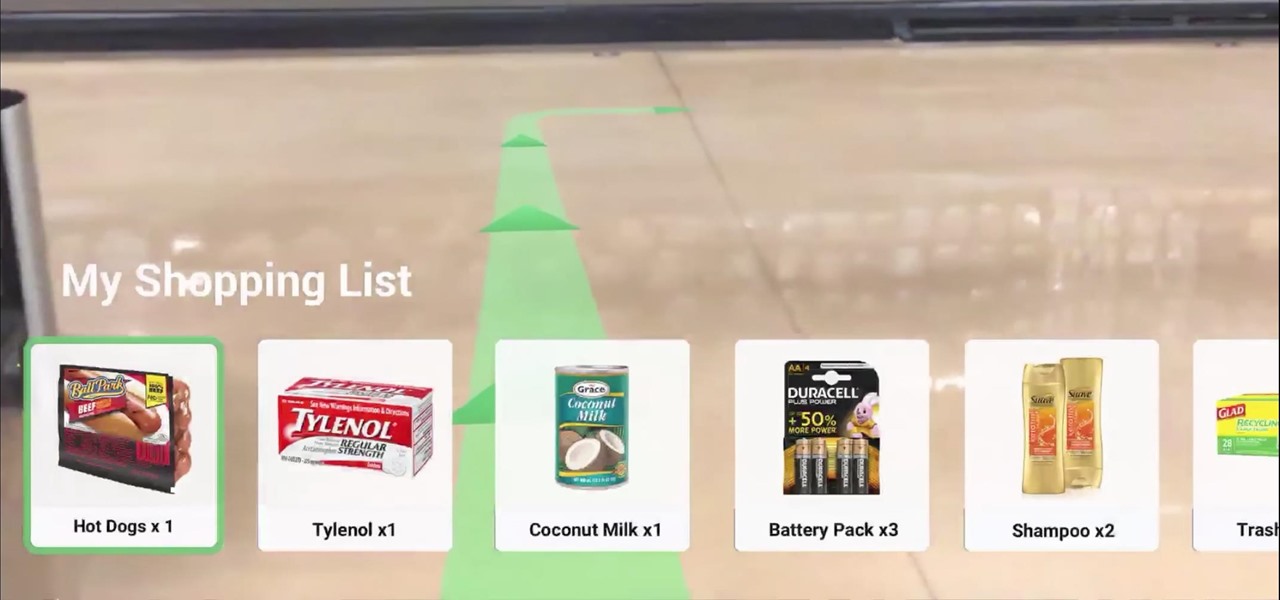
We've all been there. Lost in the supermarket for what feels like hours trying to figure out where the hell the macaroni and cheese is and why it isn't with the rest of the pasta items. The labels at the top of the aisles aren't always helpful or accurate, and items often get misplaced or lost in the masses of food on each shelf. Thankfully, the augmented reality gods have answered our prayers as a new demo shows the future of finding the items you need using Apple's ARKit.