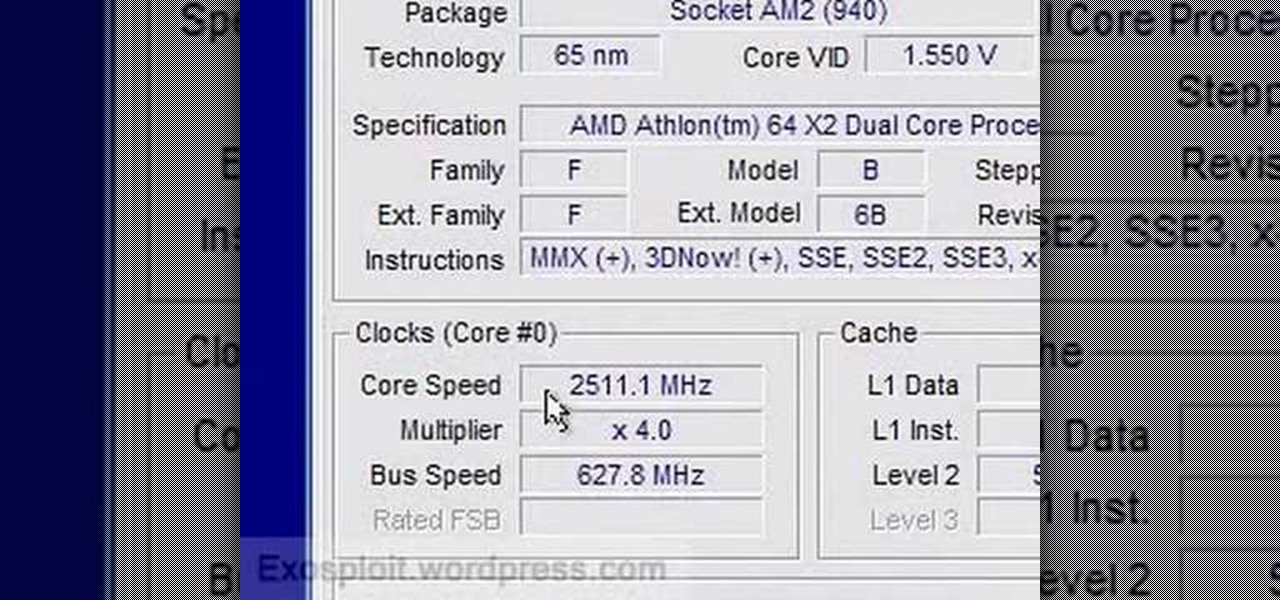
In this video from exosploit we learn how to find your system specs in Windows XP. If someone is trying to help your computer, you might need this information. Right click My Computer, and click Properties. Here you'll see your operating system, service pack, and how much RAM you have. Also google cpuz. Go to the first link and download it. Extract it and click the main file. Here it will tell you your processor, mother board, what bios version you have, how much RAM you have, and it will tel...
ReadyBoost in Windows 7 can give your PC a boost. How? This feature takes advantage of unused space and can quickly free up room and make your computer faster. Watch this Microsoft video for more details.
If you're curious about how powerful your PC is, the Windows Experience Index can give you a snapshot of its capabilities and help you decide if it's good enough for you. This video will help you understand the basics of what the Windows Experience Index can do in Windows 7.
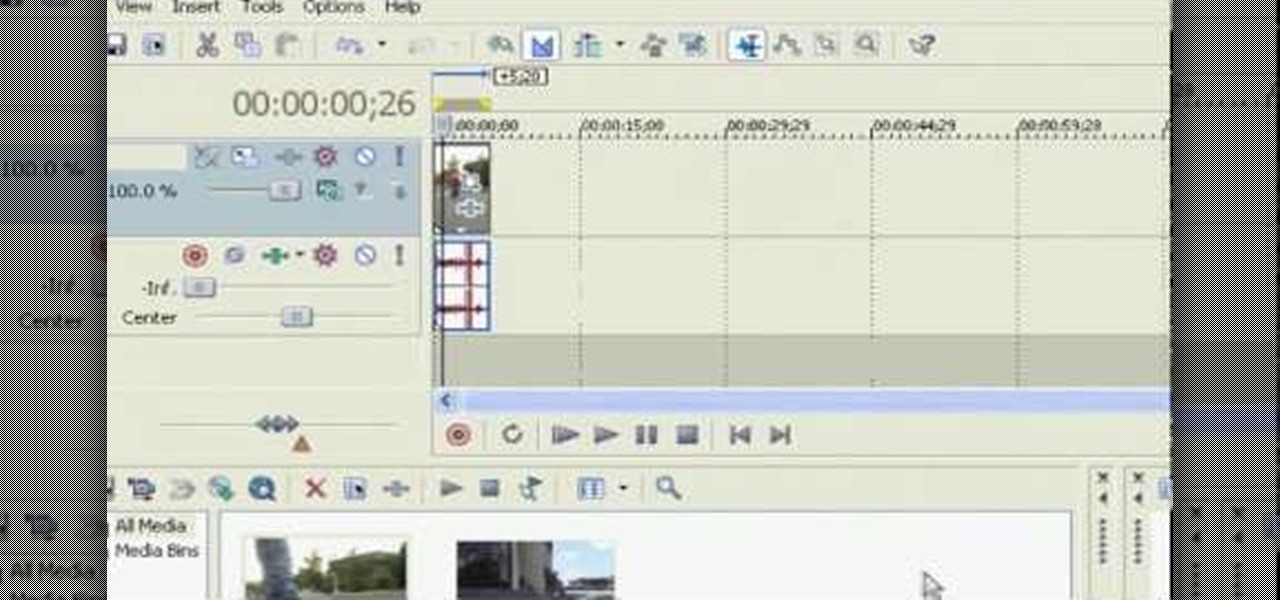
One of the most common problems with any video editing software is the preview lag- a result of high quality video slamming your CPU. There is a great fix in Sony's Vegas editing software to allow previews to run full-frame with a slight tweak called the dynamic RAM preview feature. This is especially useful if you don't have a brand new computer with maxed-out RAM and video card. Double-click the clip (or drag for a series of clips) that you would like to preview and select which quality you...

This is how you would use your PC to be a DJ if you are disabled. First you'll need a second sound card option for the headphones. Cheaper headphones can be used also until you're able to get the proper ones. The software you will be using supports microphone input which is called Virtual DJ. It's a fantastic kit made especially someone with a disability with all the same things that you would find in other decks and a mixers. Then you would want to just experiment with the controls until you...
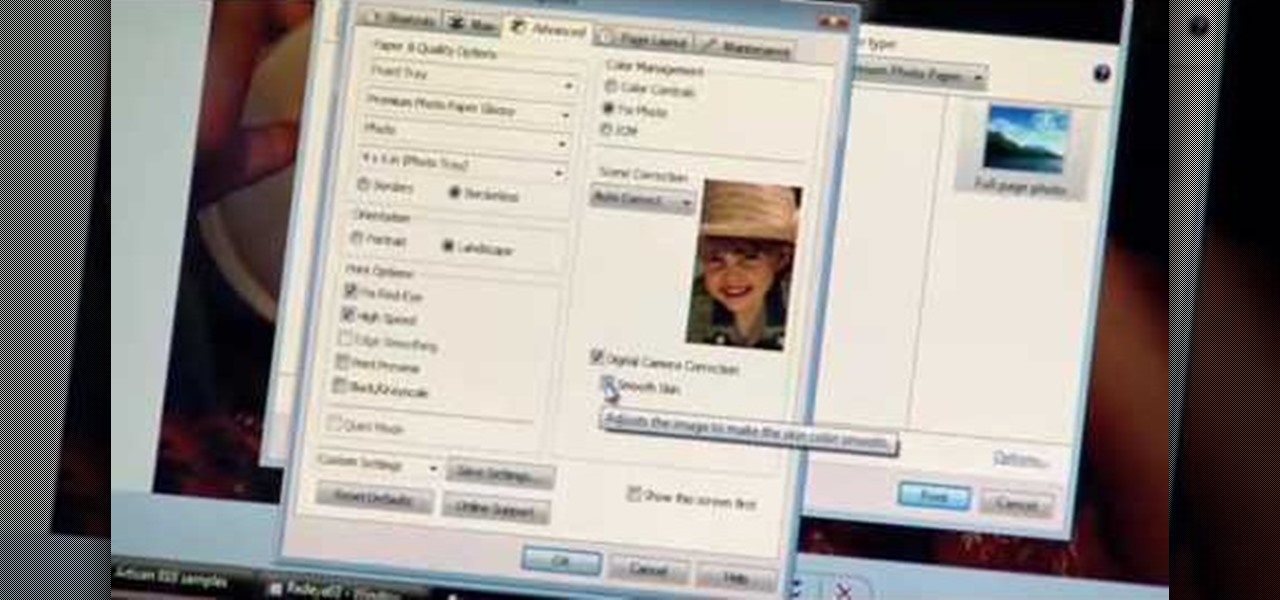
Watch this Epson video tutorial to learn how to automatically enhance digital pics with the Epson Artisan 810 All-in-One Printer.

Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to hack Wizard101 with Cheat Engine (09/25/09).

Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to get money on Wizard101 (09/23/09).

Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to get to find a walk through walls glitch in Wizard101 (09/20/09).

Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to download Wizard101.

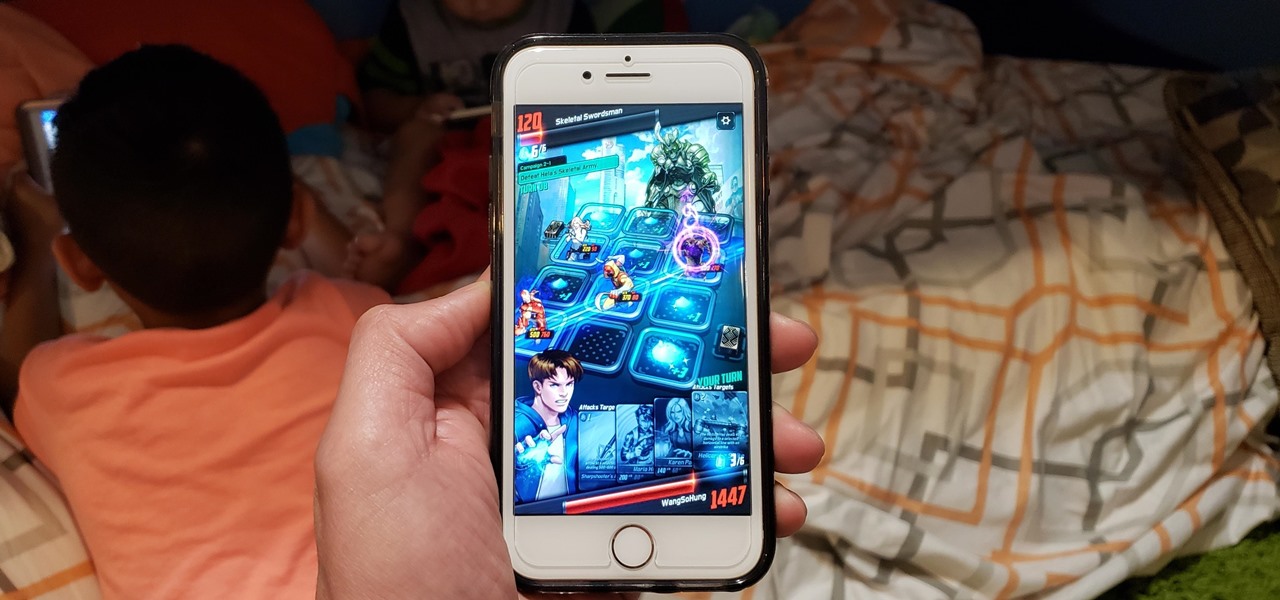
Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial from Wizard101Tutorials1 to learn how to walkthrough "Skeletal Pirates" in Wizard101.

Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to find the Smiths locations in Wizard101.

Want to learn how to broadcast live & record from your game console while viewing game-play in HD - using the BlitzBox B1-HD (for under $100). THis is an easy way to record your PS3, PS2, XBOX 360 or Wii games.

This innovative handset makes user convenience its priority. Created with the aim of overcoming the limitations of existing mobile phones, every function is available through a flexible layout of navigation keys. Fixed keypads are a thing of the past with the LG KF600 Venus cell phone.

Are you looking for a new card game to play that you can play by yourself? Learn how to play Tripeaks solitaire in this free gaming video series.

Susie Henderson, owner of Auntie's Beads, explains how to be successful in the bead industry. Learn how to make up business cards, get the business name out there, display the product, have the product ready, and how to present the product nicely. Watch this instructional video series and follow along to pick up these great business tips.

Do you have some footage from the Sony XDCAM EX digital camera memory card that you need to get into Final Cut Pro? Well, check out this brief tutorial on ingesting that XDCAM EX footage into Final Cut Pro with ease by downloading some software, like upgrades. You'll need the Sony camera and a USB cable, then just watch the video to see how it's all done in Final Cut Pro. This will work with Sony EX1 or EX3.

If you have no intention of getting personalized engravings on your AirTags, you don't need to shop on the Apple Store unless you have an Apple Card you want to earn Daily Cash with. Best Buy. Target. Adorama. B&H Photo. All of those places will let you preorder AirTags now but so does Amazon, America's second-biggest retailer, a good choice whether you have Amazon Prime or not.

In the event of an emergency where you can't answer for yourself, trained professionals can view your Medical ID on your iPhone to learn about your medical situation, granted that you have created one. But that's not all your Medical ID can do. With a new feature, iOS can share your Medical ID data automatically with first responders when you place an emergency call.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

A long-standing request for the iPhone has been a way to quickly browse and connect to available Wi-Fi networks and Bluetooth devices without having to dig through the Settings app. With iOS 13, Apple has finally built this essential feature into Control Center, giving you quick access to wireless settings from anywhere, including the lock screen.

Seven days ago, Apple released the first public beta for iOS 12.2. Now, public testers have access to the latest beta update since Apple released 12.2 public beta 2 on Tuesday, Feb. 5. The company released the developer beta one day earlier, which includes bug fixes, new Animoji, and more.

On Monday, Feb. 4, Apple released the second developer beta for iOS 12.2. The update features bug fixes to users running iOS 12.2 beta 1, as well as four new Animoji for Face ID devices. Developers are strongly encouraged to update their iPhones. It's unclear at this time whether the update includes a fix for the Group FaceTime bug discovered last week.

Public beta testers are no longer stuck on iOS 12.1.3. Apple just released the first public beta for iOS 12.2 today, Jan. 28. The company released the first developer beta for the software Thursday, Jan. 24, which includes new features for HealthKit and News, as well as a slew of hints for upcoming developments.

One day after the official release of iOS 12.1.3, Apple released the first beta for iOS 12.2 to developers. The software appears to be the first in some time to be a major update. Apple's last beta cycles included 12.1.2 and 12.1.3, incremental updates to iOS 12.1. Now, we've entered a new version of iOS 12 entirely, hopeful for new features.

Shopping wasn't always this easy. Now, in a matter of minutes, you can order your groceries for the week, send your cracked phone in for repairs, get your holiday shopping done, and have everything delivered to your front door in just a few days — without ever having to leave your home. Online shopping is convenient, comfortable, and a blessing ... right? Well, it can also be a headache.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Marvel has solidified itself as the dominant superhero franchise with the release of Avengers: Infinity War, and it's now dipping its toes into the world of mobile card-based strategy games with the soft launch of Marvel Battle Lines in select countries ahead of a worldwide release. If you'd like to install this game right now and get a head start on your fellow gamers stateside, there's a workaround.

Thanks to its intuitive interface that makes sending and receiving money a breeze, Venmo has become the go-to app for millions in the US. In fact, you've probably heard the term "Venmo you" being tossed around between friends. But before you take the plunge and sign up, it's always a good idea to read the fine print and know what you're getting into. Money is involved, after all.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

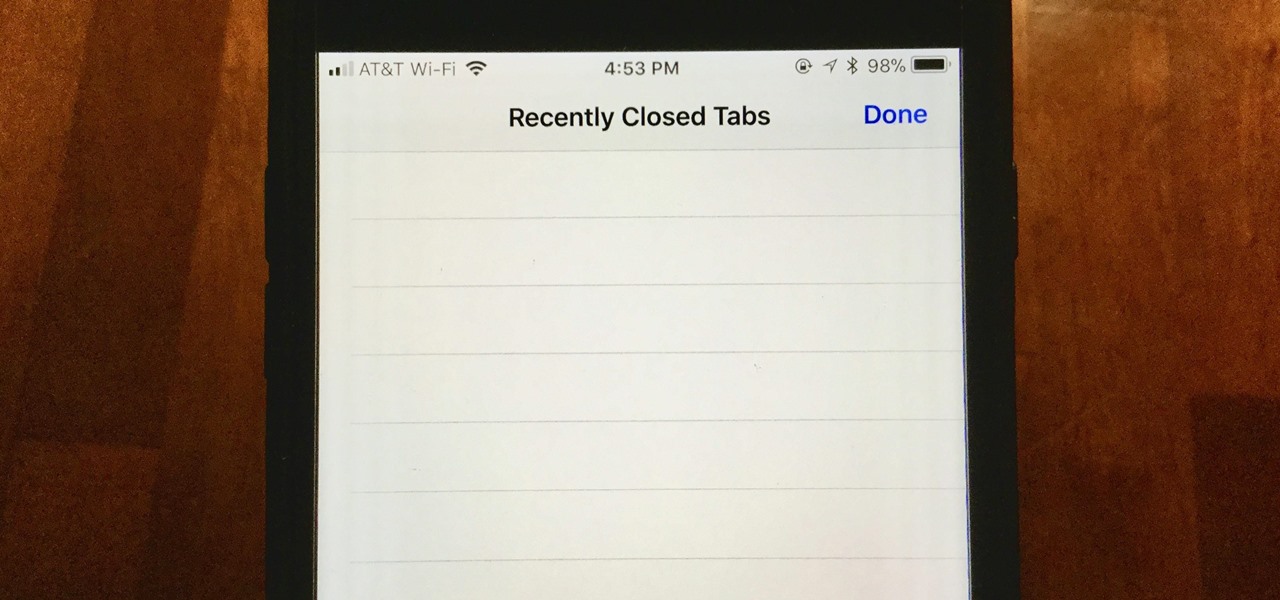
When you accidentally close out of an important tab on your iPhone, Safari's "Recently Closed Tabs" list really comes in handy. However, when it comes time to clear the list, things get a bit complicated. There's no "Delete" or "Erase" button on this page, but don't let that fool you — there are three easy ways to clear your recently closed tabs list.

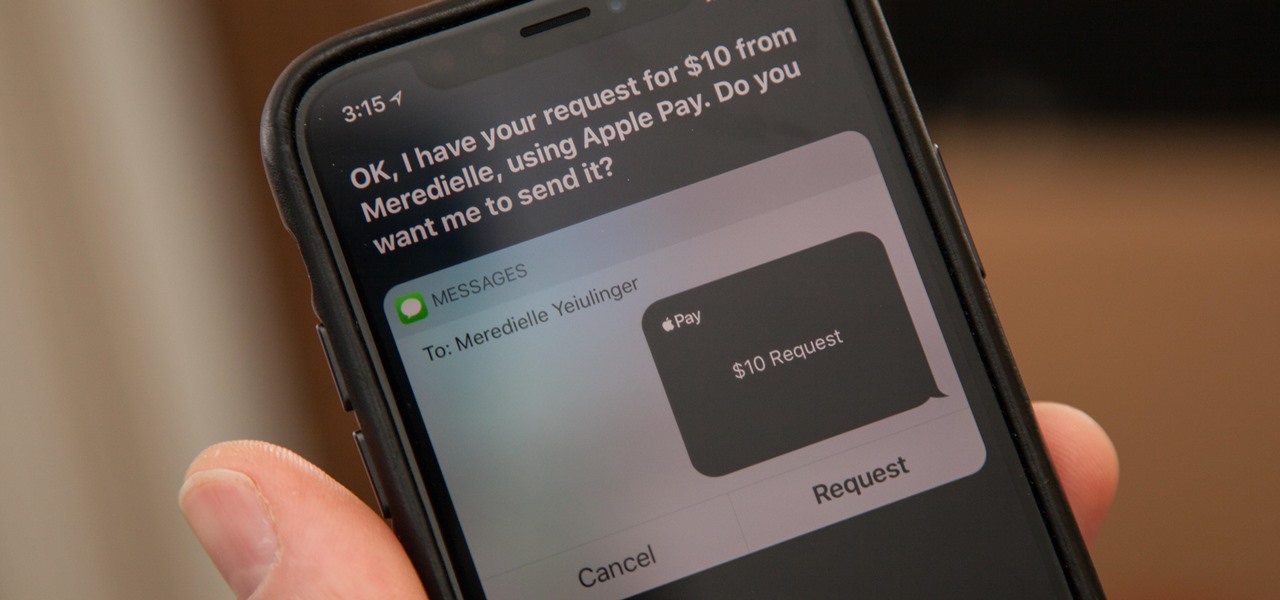
You might be proficient at sending your family and friends money using Apple Pay Cash on your iPhone, but what about when you need some digital currency in your wallet to buy in-app purchases or to get back the money you spent on someone's lunch? Requesting some Apple Pay Cash can be done a few different ways, none of which are hard.

While Black Friday shoppers found countless deals on all kinds of smartphones, one device was overtly left out of the price cuts — the iPhone X. Walmart was the only store to offer a promotion on the newest Apple device, and even then, it was difficult to find. Cyber Week appears to have repeated recent history, with only one store offering a special on the iPhone X, but it's not Walmart this time.

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

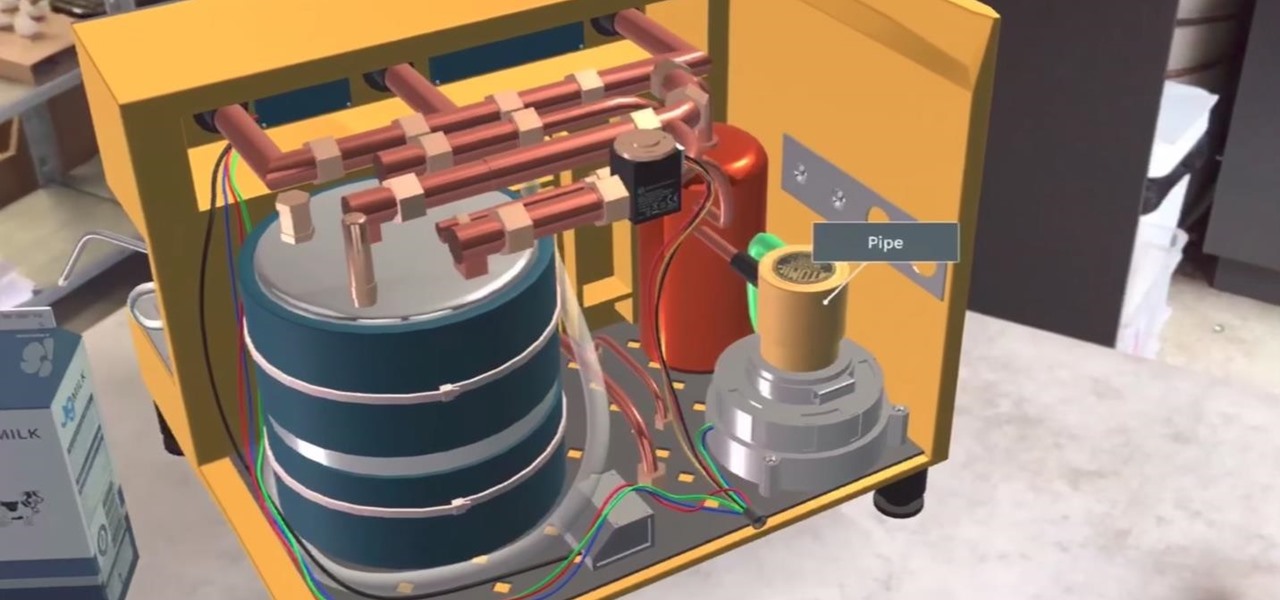
JigSpace, a company that uses 3D renderings to give instructions, showed off a fun new way to learn how things work using Apple's ARKit. The video released shows the anatomy of a range of things, including an espresso machine, an Archer Hb Plus chair, and the manual transmission of a car. Not to mention, they also used ARKit to show a 3D how-to of removing an iPhone's SIM card.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Buying a smartphone used is an excellent way to save money, but those savings come with a risk that your seller isn't as forthcoming as they claim. You don't want to end up buying a stolen smartphone because it might not work correctly ... and, you know, it's wrong. Luckily, there's an easy way to check if the phone you're about to buy is legit.