A long-standing request for the iPhone has been a way to quickly browse and connect to available Wi-Fi networks and Bluetooth devices without having to dig through the Settings app. With iOS 13, Apple has finally built this essential feature into Control Center, giving you quick access to wireless settings from anywhere, including the lock screen.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

Seven days ago, Apple released the first public beta for iOS 12.2. Now, public testers have access to the latest beta update since Apple released 12.2 public beta 2 on Tuesday, Feb. 5. The company released the developer beta one day earlier, which includes bug fixes, new Animoji, and more.
On Monday, Feb. 4, Apple released the second developer beta for iOS 12.2. The update features bug fixes to users running iOS 12.2 beta 1, as well as four new Animoji for Face ID devices. Developers are strongly encouraged to update their iPhones. It's unclear at this time whether the update includes a fix for the Group FaceTime bug discovered last week.

Public beta testers are no longer stuck on iOS 12.1.3. Apple just released the first public beta for iOS 12.2 today, Jan. 28. The company released the first developer beta for the software Thursday, Jan. 24, which includes new features for HealthKit and News, as well as a slew of hints for upcoming developments.

One day after the official release of iOS 12.1.3, Apple released the first beta for iOS 12.2 to developers. The software appears to be the first in some time to be a major update. Apple's last beta cycles included 12.1.2 and 12.1.3, incremental updates to iOS 12.1. Now, we've entered a new version of iOS 12 entirely, hopeful for new features.

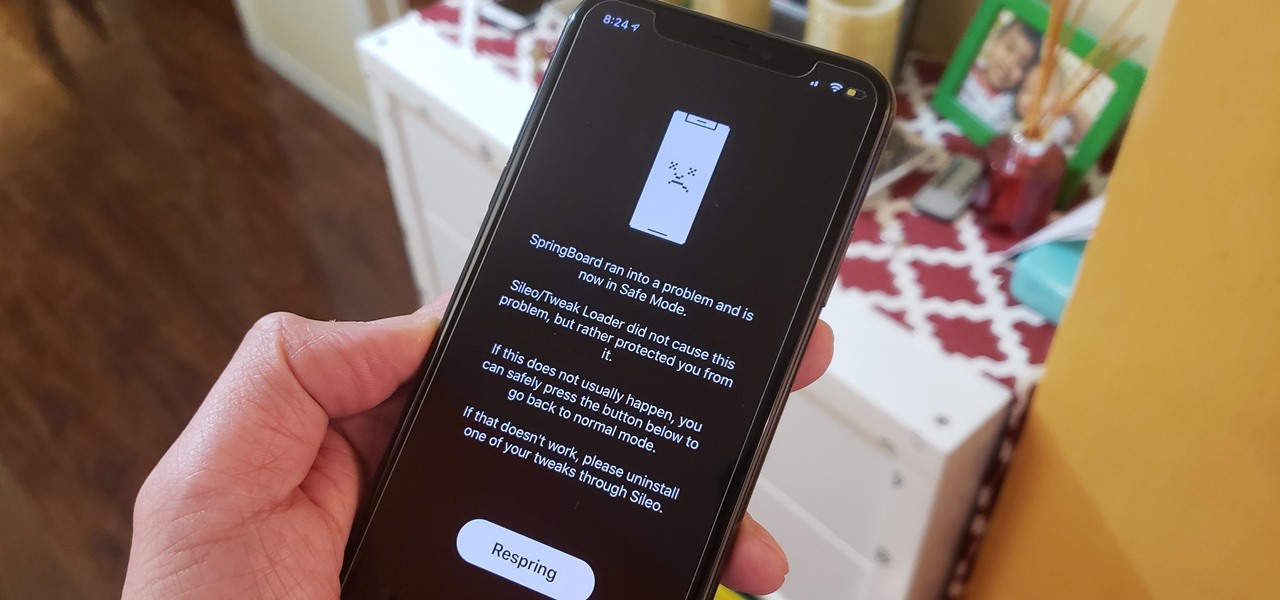
Removing unwanted apps from your iPhone is a straightforward affair — long-press an app's icon, then hit the delete button once it appears. Unfortunately, the same can't be said when it comes to uninstalling tweaks from a jailbroken iPhone.

Shopping wasn't always this easy. Now, in a matter of minutes, you can order your groceries for the week, send your cracked phone in for repairs, get your holiday shopping done, and have everything delivered to your front door in just a few days — without ever having to leave your home. Online shopping is convenient, comfortable, and a blessing ... right? Well, it can also be a headache.

Apple's stock Podcasts app in iOS remains my go-to for all of my podcast-listening needs, but skipping around during an episode can be frustrating. Scrubbing audio along the timeline is often an imprecise maneuver, which is why the skip buttons can be so useful and efficient. Without customizing skip lengths, however, you may find yourself tapping far more than you need to.

Amazon Web Services is calling up an age-old tactic of the tech industry — the hackathon — to drum up excitement and encourage the development of apps built on the Amazon Sumerian AR/VR platform.

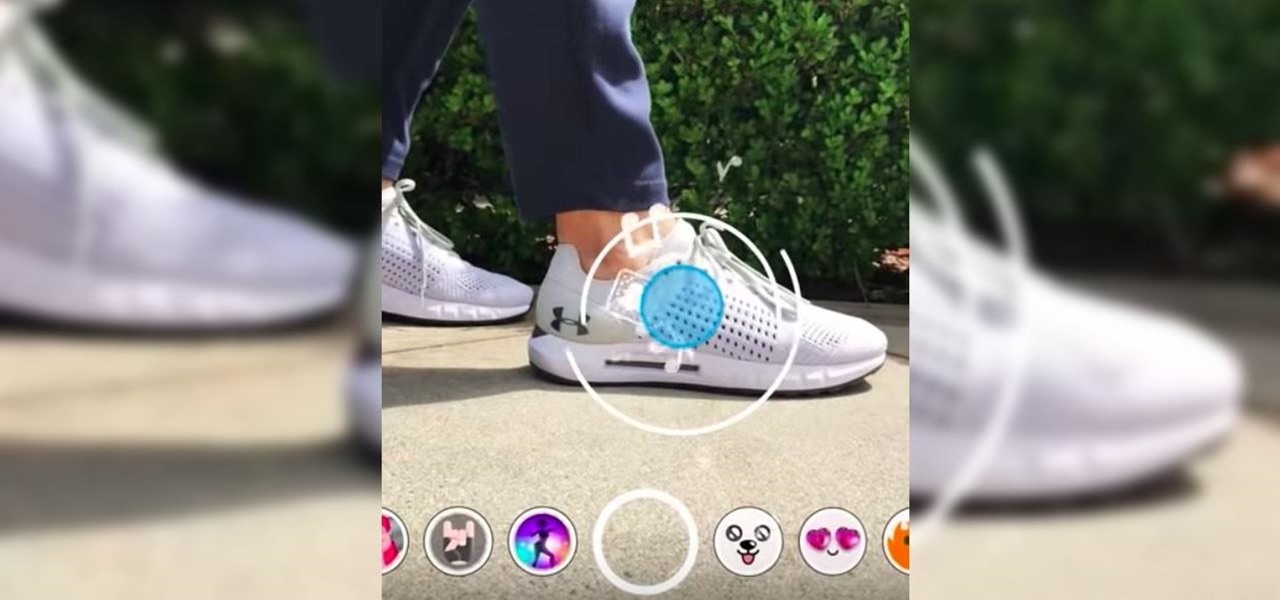
Snapchat has officially unveiled its Visual Search service for Amazon (teased a month ago), a tool the company began testing on Monday.

Fans attending the US Open Tennis Championships in Queens, New York, which kicks off on Monday, will have the opportunity to meet tennis star Venus Williams in an augmented reality game sponsored by American Express.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

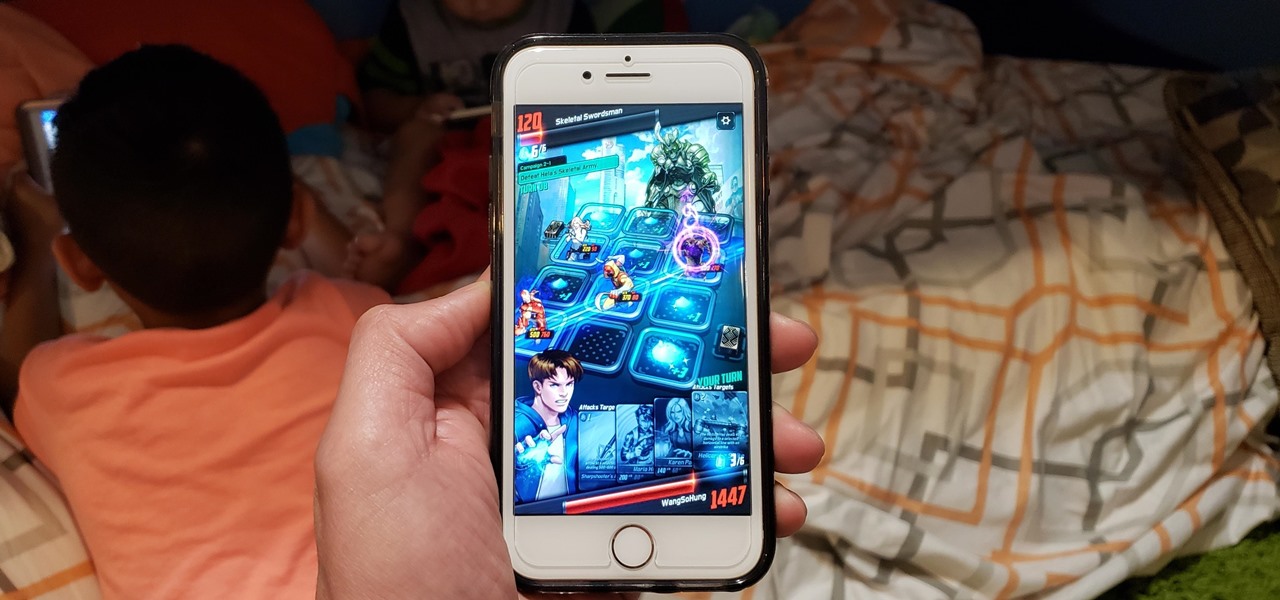
Marvel has solidified itself as the dominant superhero franchise with the release of Avengers: Infinity War, and it's now dipping its toes into the world of mobile card-based strategy games with the soft launch of Marvel Battle Lines in select countries ahead of a worldwide release. If you'd like to install this game right now and get a head start on your fellow gamers stateside, there's a workaround.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

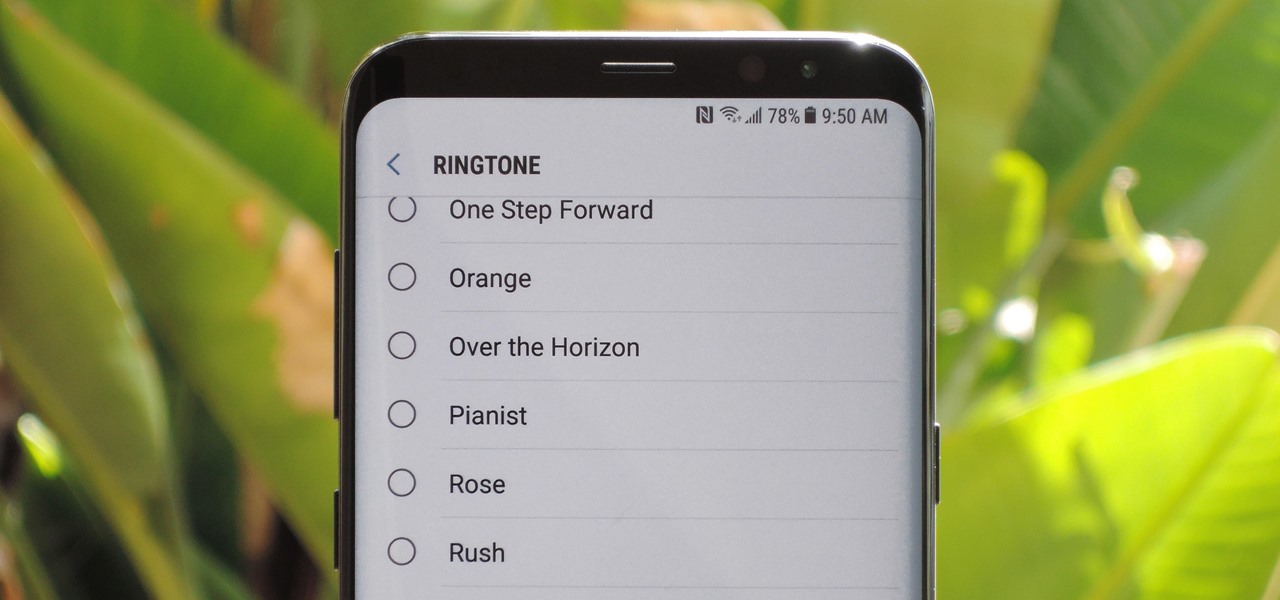
The Galaxy S9 was announced February 25, and it's jam-packed with features like AR Emojis and and a Dual Aperture camera. You really love the cut of its jib, but maybe you don't have the means to get your hands on one. Well now, you can get the Galaxy S9's notification sounds and ringtones, to help you feel like you own one.

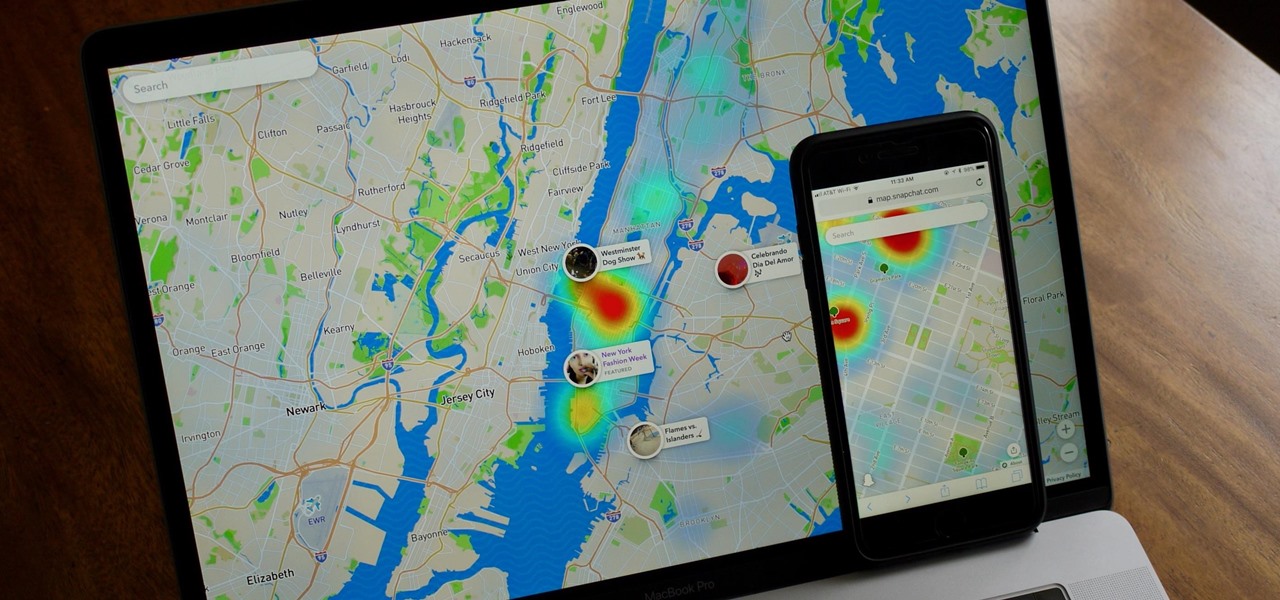
When first released, Snap Map made a lot of users uneasy. Beaming their location to the world at all times isn't necessarily the definition of privacy, but Snapchat's map is nonetheless intriguing, offering users a view into the lives of people across the globe. Now, you don't even need to have an account to access Snap Map — you can view it right from your web browser.

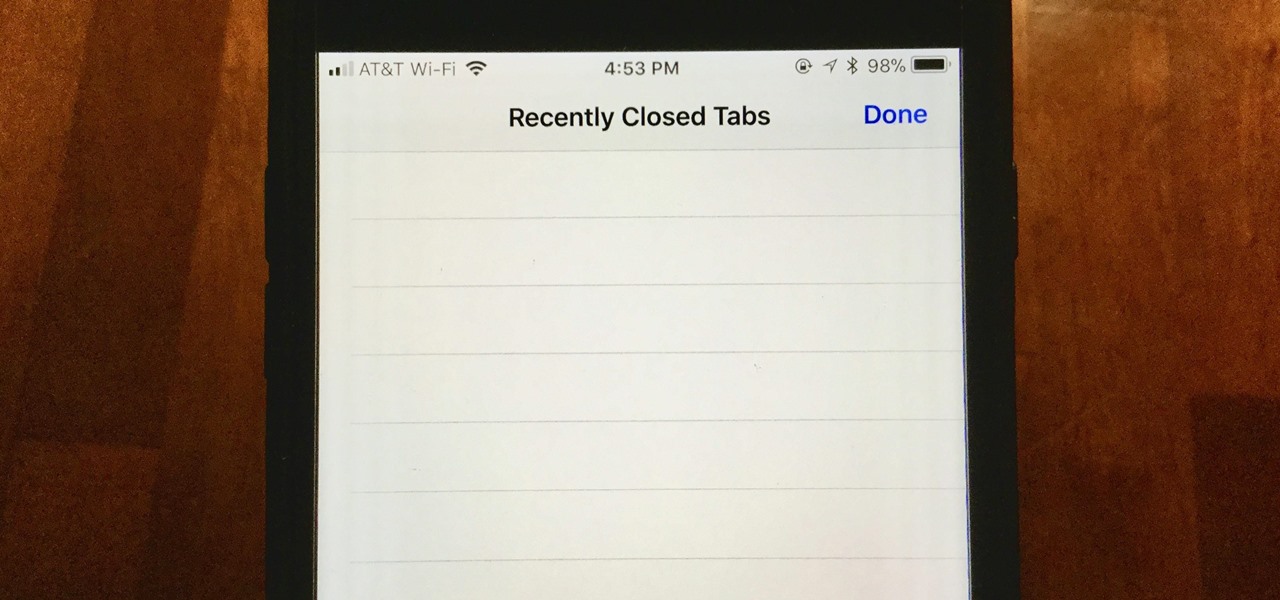
When you accidentally close out of an important tab on your iPhone, Safari's "Recently Closed Tabs" list really comes in handy. However, when it comes time to clear the list, things get a bit complicated. There's no "Delete" or "Erase" button on this page, but don't let that fool you — there are three easy ways to clear your recently closed tabs list.

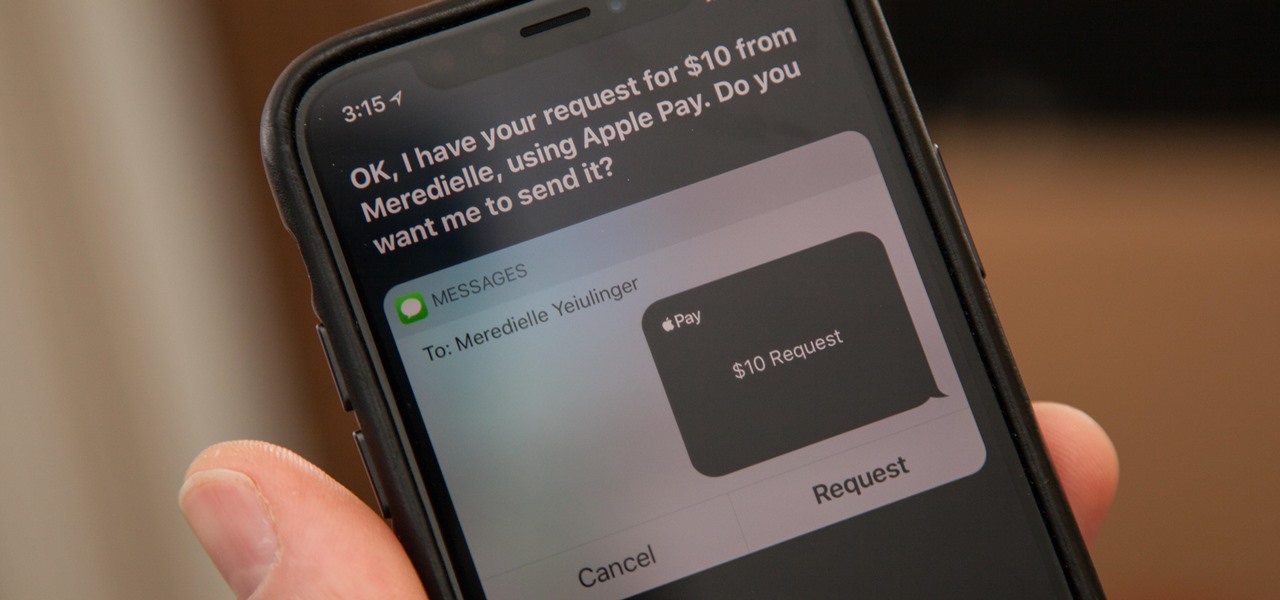
You might be proficient at sending your family and friends money using Apple Pay Cash on your iPhone, but what about when you need some digital currency in your wallet to buy in-app purchases or to get back the money you spent on someone's lunch? Requesting some Apple Pay Cash can be done a few different ways, none of which are hard.

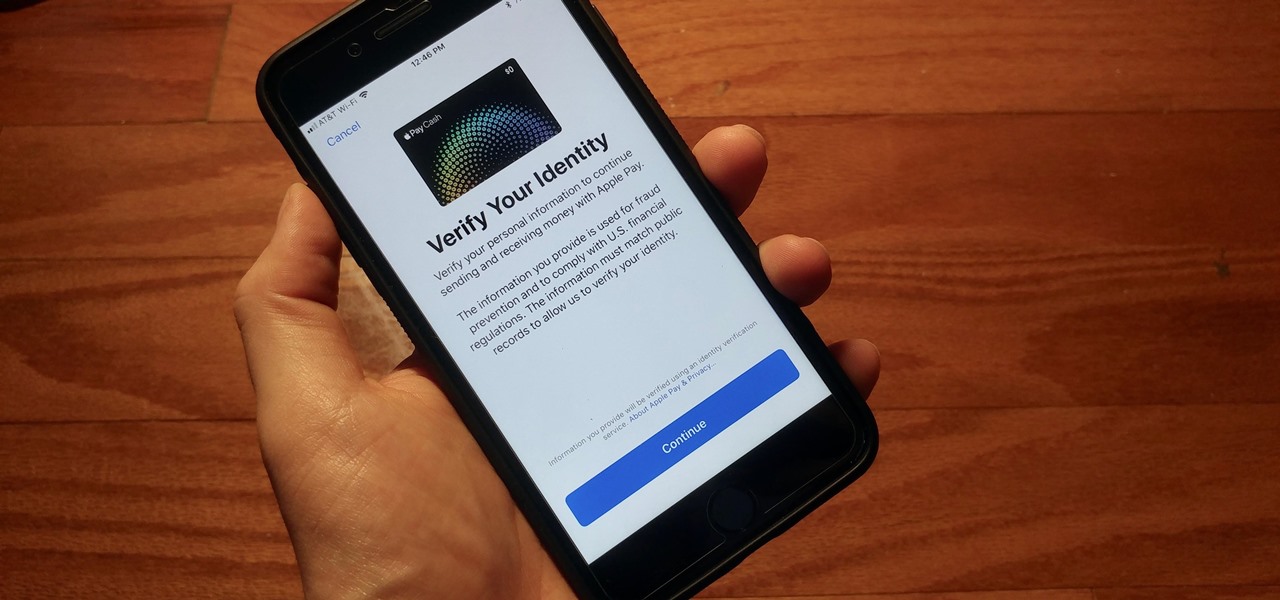
With iOS 11.2's introduction of Apple Pay Cash, you can send and receive money to others directly through iMessage, using the convenience and security Apple Pay is known for. However, if you want to make sure your efforts go uninterrupted, you'll want to make sure you verify your identity with Apple.

While Black Friday shoppers found countless deals on all kinds of smartphones, one device was overtly left out of the price cuts — the iPhone X. Walmart was the only store to offer a promotion on the newest Apple device, and even then, it was difficult to find. Cyber Week appears to have repeated recent history, with only one store offering a special on the iPhone X, but it's not Walmart this time.

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Baseball fans can now leave their wallets behind at specific stadiums throughout the country. A new upgrade by Appetize to the foodservice and retail technology used at ballparks means you can now use Apple Pay to make purchases at 5 Major League Baseball stadiums.

M — Facebook's AI-powered assistant unveiled to the public in April — is now better than ever. The latest update to M now allows it to provide three more suggestions: a function to save content to view later, birthday wishes, and call initiation.

Buying a smartphone used is an excellent way to save money, but those savings come with a risk that your seller isn't as forthcoming as they claim. You don't want to end up buying a stolen smartphone because it might not work correctly ... and, you know, it's wrong. Luckily, there's an easy way to check if the phone you're about to buy is legit.

Google's working on a new mobile operating system called Fuchsia, and while we don't know much about how they intend to use it, we're now getting a glimpse at what the main interface will look like.

Stop me if you've heard this one before. You plop a marshmallow down in front of a kid and propose the following: You can eat this marshmallow now, or you can wait twenty minutes and eat two marshmallows. What do you think the kid is going to do? Better still, what do you think you would do? Personally, I'd eat the first marshmallow without hesitation. But now we're getting off track ...

Samsung's new personal assistant, Bixby, is making its debut on the Galaxy S8 and S8+. In addition to taking voice commands and performing visual searches, a new Hello Bixby feature predicts what you might want to do next with an integrated home screen feed. All of these features look nice, but if you're not ready to shell out at least $750 for a new phone, you'll be glad to know that Hello Bixby just leaked.

As the first phones to be made by Google, the new Pixel and Pixel XL have several slick customizations that you won't find on any other Android device. There's tons of functional stuff like the new Google Assistant and a much-improved camera app, but also a few aesthetic tweaks to help class up the joint.

Like previous installments in the Pokémon series, as you progress through Pokémon GO you'll be able to evolve your Pokémon into more-powerful monsters with new and more-damaging attacks. However, unlike older entries in the series, your Pokémon won't simply evolve when they reach a certain level. Instead, you'll have to "feed" them a certain amount of character-specific candy to induce the transformation.

Knives are among the most important utensils in any kitchen; it's hard to even conceive of cooking a decent meal without them. However, many different foods can be prepped without a knife, and some are actually better off without one. If you don't believe me, then check out these 10 creative methods for chopping, peeling, mincing, and slicing knifeless.

With the FBI getting access to iPhones, and apps like Waze being used to track people's locations, you've got to wonder just how safe and secure your smartphone is... or isn't. When you consider everything you do on your phone, from taking and sharing pictures to mobile banking, keeping your information safe is a crucial step that may seem out of your hands.

Android's flexible operating system allows for lots of customization, and one of the most common ways to add personal flair to your smartphone is to set your own ringtones and notification sounds.

Most of you probably heard about Rasberry Pi and if you haven't; what is wrong with you? But nothing less a Rasberry Pi is a computer a very small computer. Despite these size limitations, the Rasberry Pi is to not be underestimated. Not only can it do anything like a normal laptop or desktop, but, in my opinion on of the coolest features is that it boots off a Micro SD card. It can do anything that you want, but it's built to be played with. A hacker heaven.

Android has a brand new mobile payments system, and it's rolling out to most devices as we speak. Android Pay, as it's called, will replace the existing Google Wallet app as an update, and it brings some awesome new functionality such as tokenization and the ability to tap-and-pay by simply unlocking your phone.

Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"

When you search for a specific location or business with the Google app, a Knowledge Graph card is usually the top result. This card displays a handy mini-map and offers a quick link for directions to the location of your query, but it has one irksome flaw—these links can only be opened by the Google Maps app.