Months before London-based Jonathan Moon would turn 30, he started musing over how to celebrate. While he had rung in past birthdays at home, he wanted to do something out of the ordinary as a farewell kiss to his twenties. A short ski vacation with friends felt like the perfect idea.

A scary piece of malware just got a lot more terrifying this week. Security firm Comodo reports that "Tordow," a banking Trojan first uncovered in September 2016, received a massive update this December.

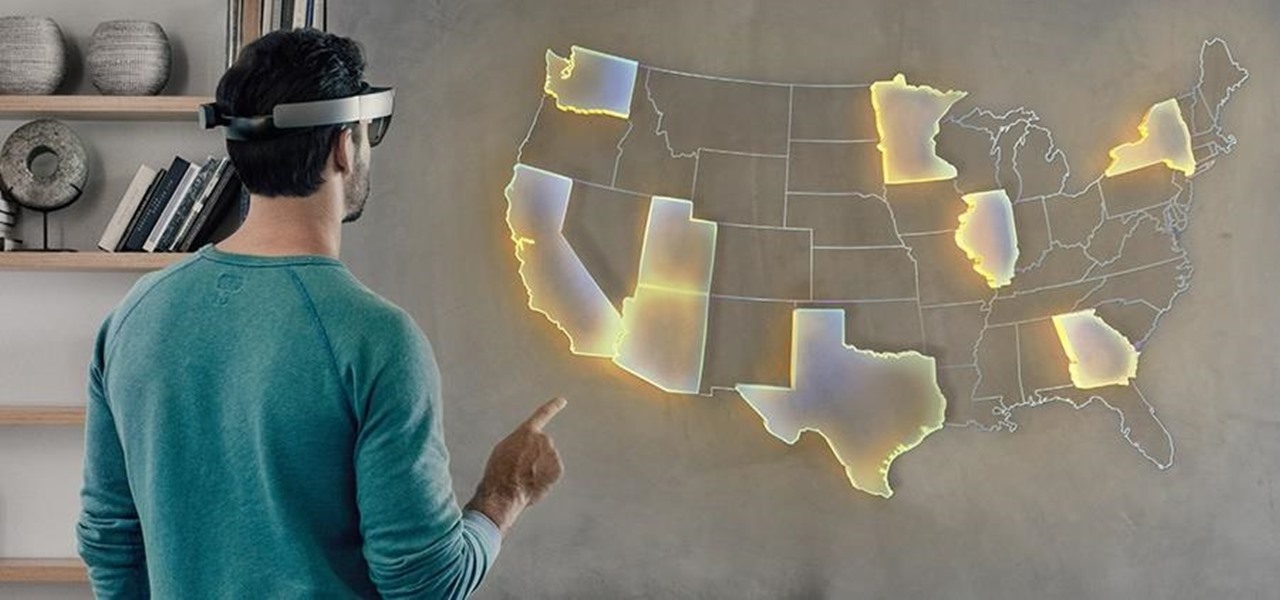
When the HoloStudy Demo app for HoloLens came out in September, it was a pretty impressive start to what could be a very valuable science tool for education. Now, Moscow-based HoloGroup, makers of HoloStudy, started an Indiegogo campaign to improve their modular teaching app.

As Alfred monologued in The Dark Knight, "Some men aren't looking for anything logical, like money. They can't be bought, bullied, reasoned, or negotiated with. Some men just want to watch the world burn."
Hear me out. No, really. Before you sharpen your pitchforks and give me anecdotal evidence of your Chinese restaurant syndrome, I think you need to know a few things about monosodium glutamate. First of all, it's a naturally-occurring chemical compound that can be found in anything from tomatoes to cheese, and is used in all kinds of foods from KFC to breakfast sandwiches. So spare me the comments on MSG and Chinese food—you probably eat MSG on a daily basis without even knowing it. (And also...
If you follow tech, you're probably familiar with Siri, Apple's personal voice assistant, which has been integrated heavily into iOS ever since iOS 5. But you might not have known that Siri is capable of performing some tasks when the iPhone is in a locked state. The default state of iOS is to allow access to Siri from the lock screen, most likely for the convenience of hands-free access to the phone.

Video game emulation has saved arcade and console classics from obsolescence, and that wonderful hobby has found its way onto the Microsoft HoloLens—with some three dimensional upgrades, of course.

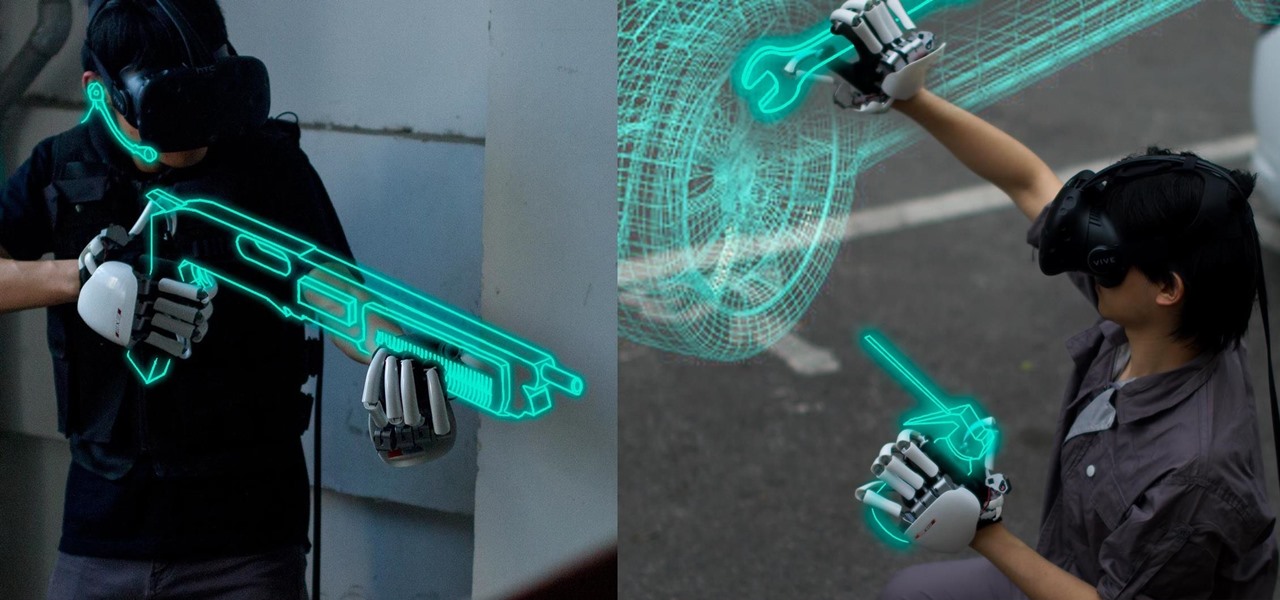
One of the disadvantages of the digital world is that you can't pick it up and touch it. While that can feel like less of a problem in virtual reality, where you're already holding controllers, mixed reality environments—like the one you'd experience in Microsoft's HoloLens—suffer from a lack of physical connection with the digital objects that appear in your real world. Dexmo aims to solve that problem with a relatively intimidating new controller that encompasses your hands.

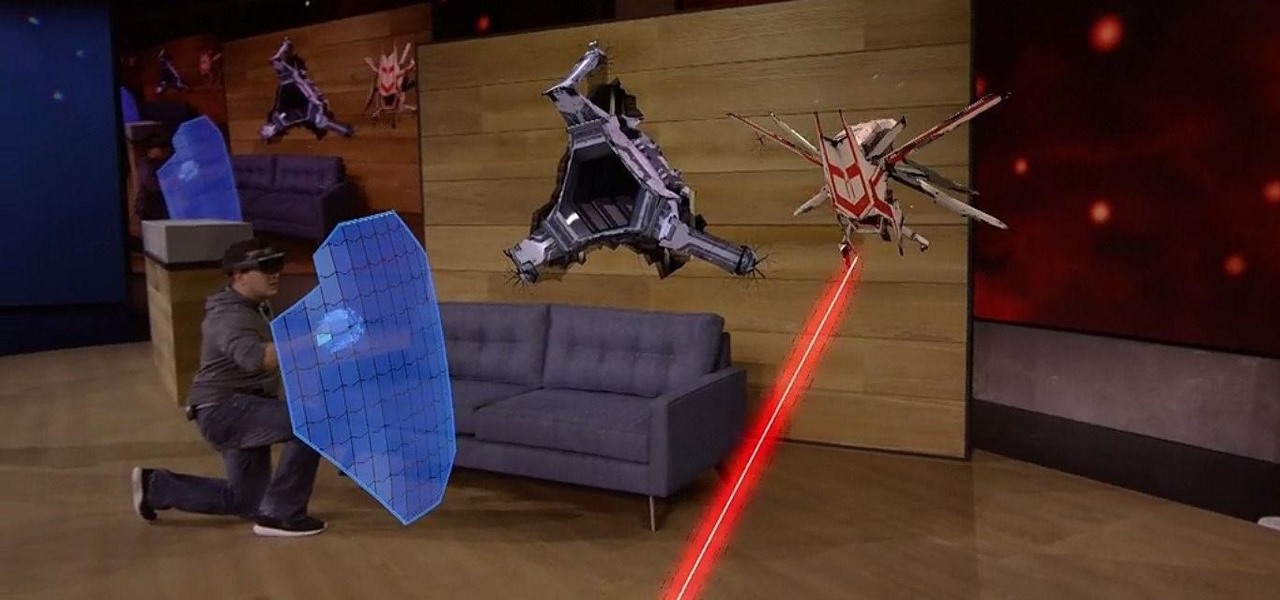
Microsoft's HoloLens has many applications in the business world, both large and small, but what about gaming? Initial demos gave the impression that we could expect amazing first person shooters, platformers, and even Minecraft. Yet, as Newsweek noticed, the HoloLens was nowhere to be found at E3 this year.

Before you figure out how to strip the paint on your car to bare metal, you should should first ask the question, should I strip all of the paint off. Depending on the type of job you're doing, it may actually be better not to strip all of the paint off.

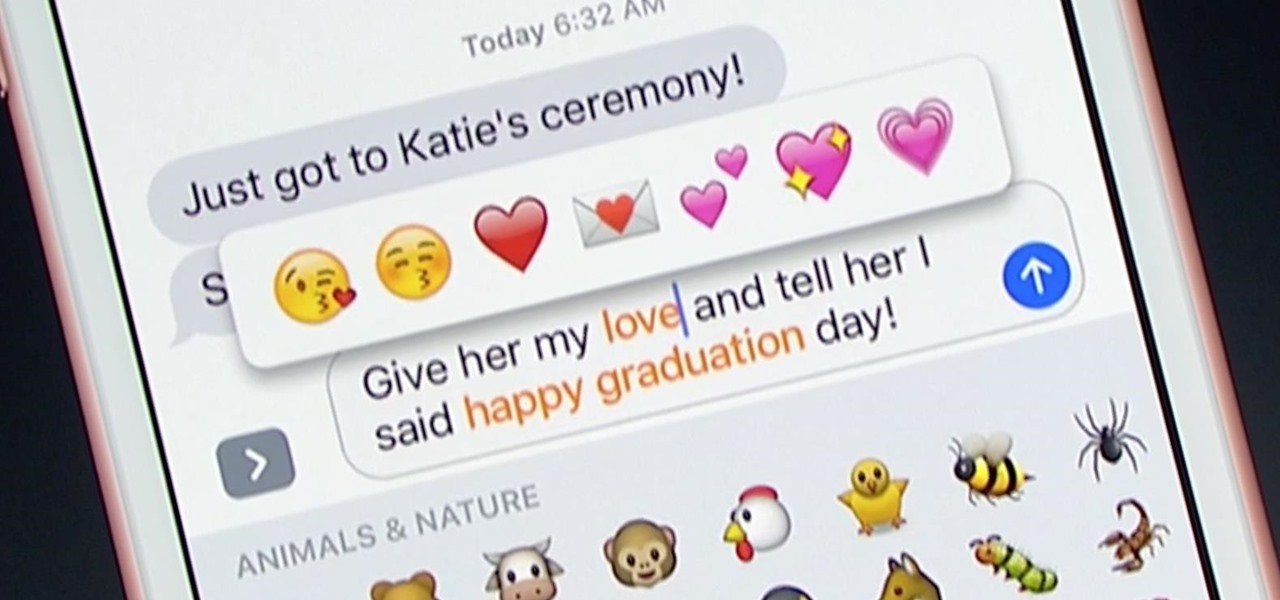
Apple unveiled huge improvements for Messages in iOS 10 at WWDC '16, and my favorite new feature is that searching for emojis will be much, much easier. But there's a lot more to this update besides emojis.

Mixed reality (MR) feels like an amazing, almost mind-blowing futuristic technology—but only once you've experienced it for yourself. Words, images, and even videos simply cannot describe the experience in full. If you want to really peer into the future and experience MR for yourself, you can sign up and just go in many cities.

Summertime means lots of parties, picnics, and barbecues—and wherever a group of fun-loving adults can be found basking in the sun's rays, delicious cocktails are sure to flow freely.

With the FBI getting access to iPhones, and apps like Waze being used to track people's locations, you've got to wonder just how safe and secure your smartphone is... or isn't. When you consider everything you do on your phone, from taking and sharing pictures to mobile banking, keeping your information safe is a crucial step that may seem out of your hands.

Researchers at MIT's Computer Science and Artificial Intelligence Laboratory have created Wi-Fi technology that identifies where you are, which may eliminate the need for passwords.

Logan's Run is one of my favorite movies of all time. The dialog is cheesy, the set design and special effects are wonky, and the main villain looks like he was conceived and built by an eighth grader in shop class—oh, and his name is Box.

Up until the last 15 years or so, watching the commercials during the Super Bowl was arguably more exciting than the game itself. Super Bowl XXIV featured the San Francisco 49ers blowing out the Broncos, 55-10, in the worst Super Bowl beatdown of all time. The game might not have been that exciting, but the commercials sure were.
I've recently been on holiday in Europe, staying in a hotel that was part of a big chain that included many in the local area. A quick review of the wi-fi within range of my room showed that there was another in the chain that was in range of my Yagi Turbotenna, which naturally got me thinking. If I wanted an anonymous internet connection, this could be quite handy.

Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of those accounts have just been leaked.

Flashing people in an oversized trench coat is both old-fashioned and exhausting (and also very illegal). But like the evolution from school-yard bullying to cyber-bullying, it seems as if the new trend is "cyber-flashing" (it's even has an official hashtag). In the U.K., police are now investigating what they are calling the first cyber-flashing case.

When you go to the grocery store, chances are you're confronted with the usual piles of apples, berries, bananas, and melons. All well and good, right?

If a tree falls in the woods and nobody is there to hear it, does it make a sound? If a person makes calls but doesn't have a Facebook account, are they even really a person? Yes, of course they are, but it just makes life easier when you're part of the world's biggest social network, as proven with Facebook's latest application, Hello - Caller ID & Blocking.

Mother Nature is one creative entity, especially when it comes to fruit. Let's face it: most major supermarkets stock only the most common fruits like apples, pears, and grapes, but they're so basic. Why not explore other options, from the stinky-yet delicious durian to the captivating citrus caviar that is finger limes?

Collaborating with other people can be a pain, especially if you have to share one device between the entire group. Usually when you're creating a new design or trying to edit a mockup, you end up hunched around a single screen or end up emailing revisions back and forth, which can be difficult when you're short on time.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

If you're one of the many that likes to upload collages to Instagram, the Facebook company has a new tool for you. Instagram released a brand new app in March called Layout to help facilitate the process of creating photo layouts to post onto social media or just share with friends.

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

When going out to eat with friends, it's inevitable that one person takes charge at the end of the meal to split the bill. They whip out a pen and begin asking everyone what they ordered, carefully dividing, adding, and subtracting on the back of the receipt for everyone to use. Unfortunately, that never seems to work as intended. One person will end up paying a little more, while another will pay less.

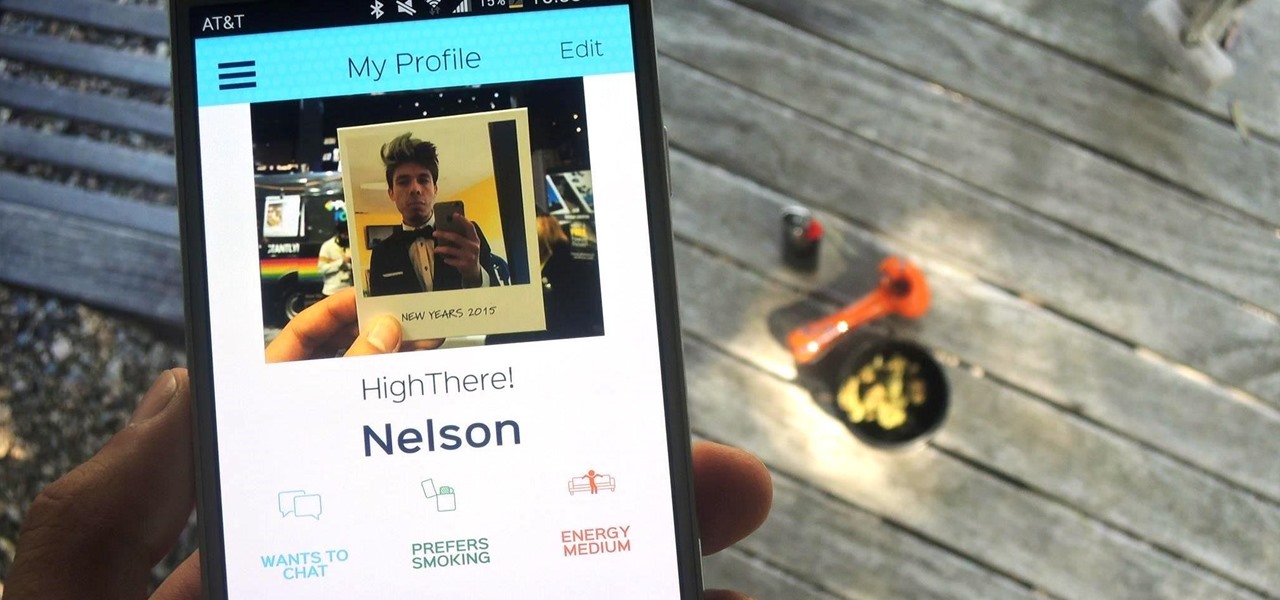
Dating can sometimes be a cruel and embarrassing game. You could be having a great time with someone, only for the situation to turn awkward and uncomfortable when a little bit of information is released, especially when that information is your use of medicinal or recreational marijuana.

Chicken wings, pizza, beer, and chips are among the top five most popular Super Bowl foods, and we eat them in staggering quantities. According to the stats, Domino's and Pizza Hut sell over 25 million slices of pizza during the Super Bowl, and Americans snack on over 1 billion chicken wings, over 11 million pounds of potato chips, and drink over 49 million cases of beer.

Android 5.0 has a cool new feature called Priority Mode that allows you to silence your phone's ringer except for when certain people call you. It's something you'd enable right before bedtime, for instance, if you don't want to be disturbed unless it's someone important trying to reach you.

This past Halloween, 26-year-old Gabrielle Wathen learned the hard way about Uber's ridiculously expensive surge prices. After a night out and an Uber ride home, she learned that the 20-minute drive cost her more than $360.

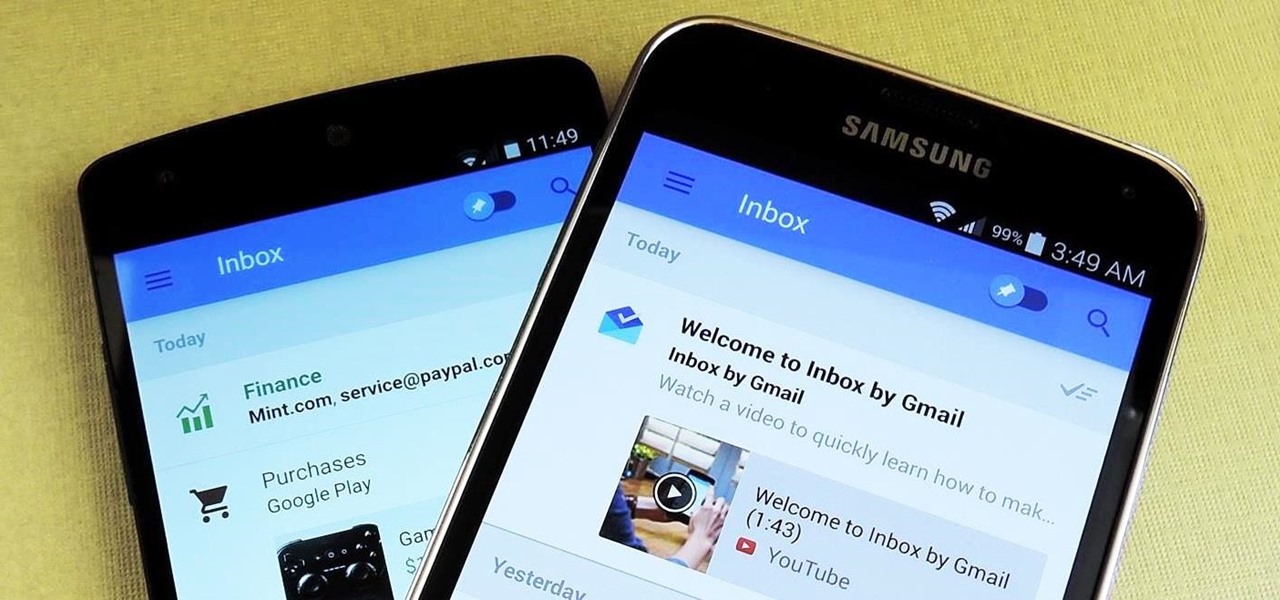
Google's new Inbox by Gmail service offers a new take on email with a particular emphasis on productivity. But, as an invite-only service at this stage, not many people can access Inbox just yet.
Hello everyone. The red ring of death of Xbox 360 has been a huge problem since the beginning of Xbox 360. Many gamers like me have faced this problem and the red ring of death (RROD) is one of the biggest reason behind all the rant on Xbox 360 gaming console.

With over 2 million uploaded videos and over 28 million people who had talked about it online by the end of August, the ALS Ice Bucket Challenge was the most viral social media event of 2014. Its popularity provided the ALS Association with $115 million in donations to date, with everyone from students to veterans to celebrities contributing.

Coffee mugs: nothing proliferates more quickly in my kitchen cabinets. People are always handing them out as gifts or as swag, plus I always seem to find a vintage model or two at a garage sale that I'm compelled to buy. I used to do a yearly purge of my excess muggage, but it turns out it's a good idea to hold on to one or two extras.

Who said you need a smartphone to use Snapchat? A new application in the Mac App Store, appropriately dubbed Snappy, allows you to send and receive Snapchats directly on your computer. Check out the guide below to learn how to go through all of your Snapchat stories, take and send photos with filters, and text just like you would on your mobile device.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

Unlike the suave 007 that Daniel Craig portrayed, I am not a spy, nor am I that charming, but I do occasionally enjoy taking a stealthy video. Maybe I'm a jerk, but I often catch people doing ridiculous things and just think, "Aren't you embarrassed?"

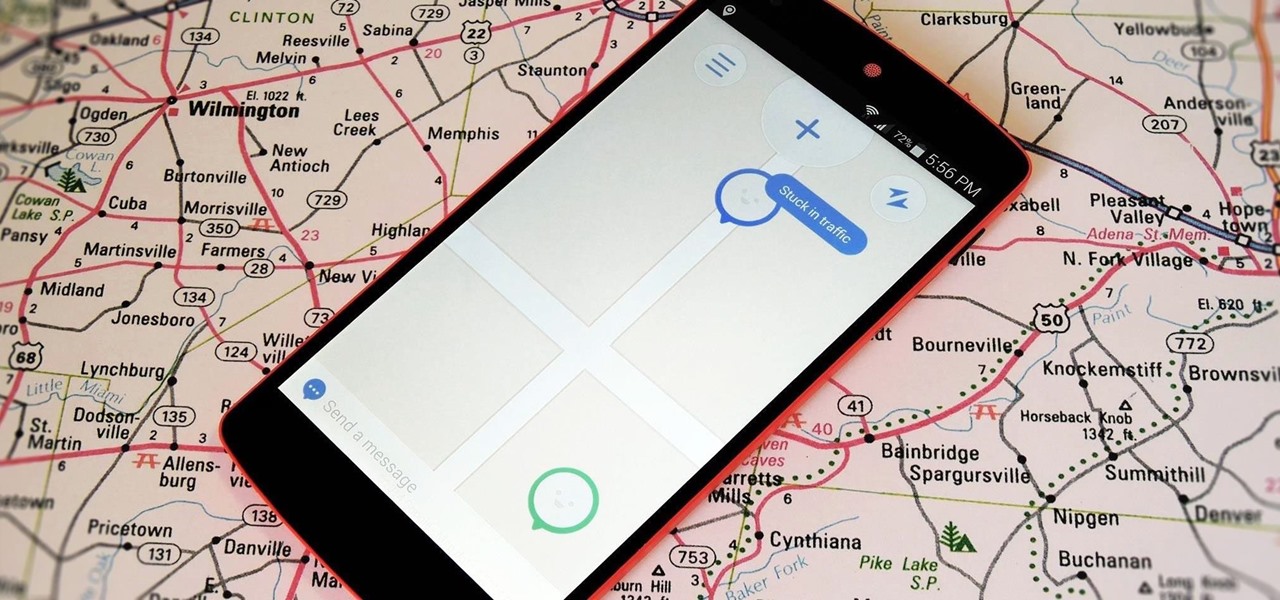
With GPS chips and Wi-Fi positioning systems, a modern smartphone is capable of tracking its user's location with pinpoint accuracy. This being the case, it's strange that the most common text message sent today is still "Where are you?"