
News: These Beautiful Chairs Are Grown, Not Made
For anyone who has spent an entire afternoon attempting to assemble a set of IKEA chairs, these wooden masterpieces probably seem pretty appealing.


For anyone who has spent an entire afternoon attempting to assemble a set of IKEA chairs, these wooden masterpieces probably seem pretty appealing.

These days, if you walk through Best Buy, you will see an entire area designated to smart home technology. Thanks to the interest and growth of the Internet of Things (IoT), this exciting new technology has finally entered the mainstream. Appliances, thermostats, and even the lighting throughout your house can be controlled from your computer or smartphone. You could also use artificial intelligence; Simply tell Amazon's Alexa what you want your house to do, and she will do it.

If print is a dying media, you might as well destroy books in the most beautiful way possible. Guy Laramée is a Montreal-based interdisciplinary artist who turns old books, such as the Encyclopedia Brittanica, into intricately-carved works of art using mostly a sand blaster and some paint.

Months before London-based Jonathan Moon would turn 30, he started musing over how to celebrate. While he had rung in past birthdays at home, he wanted to do something out of the ordinary as a farewell kiss to his twenties. A short ski vacation with friends felt like the perfect idea.
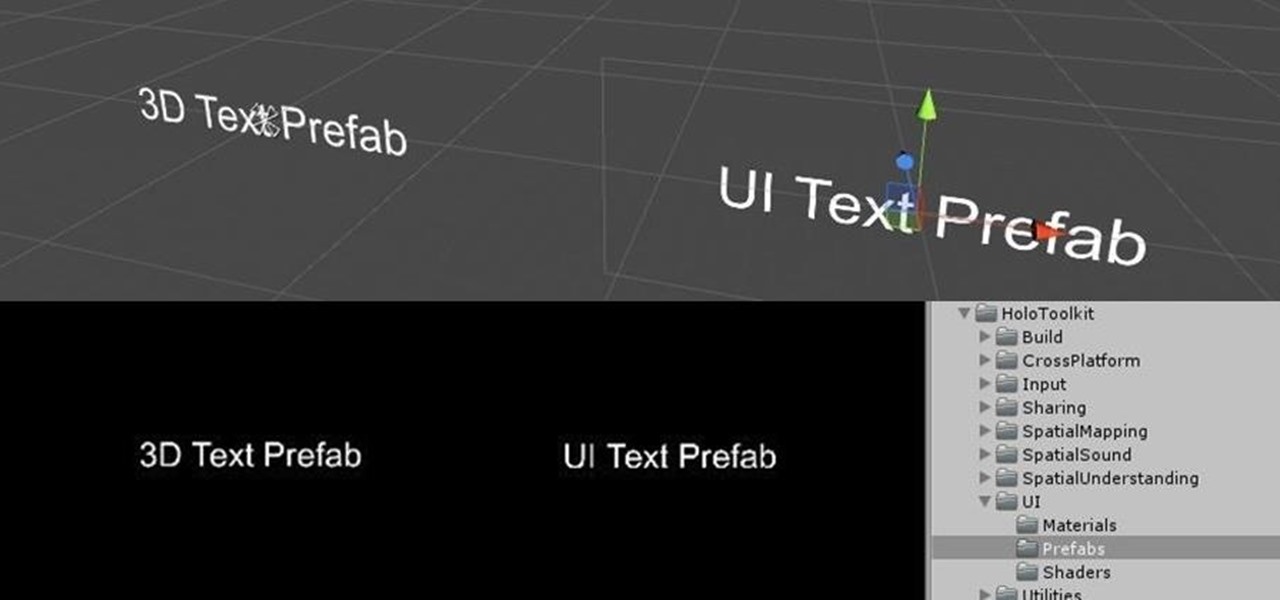
You may remember my post from a couple weeks ago here on NextReality about the magical scaling ratios for typography from Dong Yoon Park, a Principal UX Designer at Microsoft, as well as developer of the Typography Insight app for Hololens. Well, his ideas have been incorporated into the latest version of HoloToolkit, and I'm going to show you how they work.

Well, we have some potentially good news for those wanting to experience Magic Leap. The ultra-secretive company seems to be planning a big year in 2017.

Each generation of smartphones ushers in a new set of top-of-the-line specs, with processing power, battery size, and display resolution growing by the year. These headlining features get the most press, but there's one unsung hero that has the potential to make the biggest difference when it comes to real-world performance: RAM, or random-access memory.

When the "Just another day in the office at Magic Leap" video was released last year, it was called a mind-blowing, stunning, and breathtaking take on mixed reality gaming. It was a great presentation of what the technology could be, but not for a second did I think it was anything other than a concept video, and I'm not the only one who thought that. This was a goal to reach for mixed reality, not the reality.

The new Samsung Galaxy S8 and Galaxy S8+ phones were announced on March 29 at the Samsung UNPACKED 2017 event. Preorders start on March 30 for the Korean tech giant's latest flagships, and sales officially begin in the US on April 21. Samsung will need a smooth release to win back consumer trust after the Note7 mess, and it's already looking like the S8 won't disappoint.

Oh no... your precious iPhone is in shambles. Maybe you shattered your screen after a crazy night of celebrating, or maybe your two-year-old jabbed a toy into your iPhone's charging port, completely destroying it in the process. Now what? Do you take it to a repair shop, or go to an Apple Store to have it fixed? This brief article will help you weigh your options.

Designing for mixed reality, especially for the HoloLens, can present unique challenges. Dong Yoon Park, a Principal UX Designer at Microsoft with a passion for typography, recently gave a talk to the Windows Holographic Users Group Redmond (WinHUGR) about the pitfalls he ran into trying to convert what started out as a 2D iOS app 5 years ago to the newer 3D Holographic frontier with Unity.

I don't know about you, but visions of pumpkin pie and cornbread stuffing and big, juicy turkeys are constantly dancing through my head right now. I'm sorry, healthy eating habits, but it's Thanksgiving week, and all I can do is think about food.

Robots are always really cool, if you ask me. Sometimes they're made out of Legos, and that's even cooler.
Heads up: the following videos and GIFs will definitely cause you to zone out and lose focus on whatever it is you're doing.

Kryptowire, a company specializing in mobile security solutions, released a report on Tuesday, November 15 that exposed firmware in a number of Android devices that was collecting personally identifying information (PII) and uploading it to third-party servers without users' knowledge.

A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists right now, and it can have some serious real-world repercussions, so this is something all iPhone users need to be aware of.

If you've ever wondered why the pictures and videos you share with Snapchat on your Android device seem to look grainy with low resolution, you're not alone. We all know it, and we've come to accept it as a plain fact: Snapchat image quality sucks on Android.

We all got a little jealous of the iPhone 7 Plus's dual-lens camera during the Apple Keynote in September. It's okay, you can admit it. But just because your Android doesn't have two lenses doesn't mean you can't recreate the fun bokeh effect of the iPhone's now wildly popular Portrait Mode.
Google's new Pixel phones are shaking things up in the world of Android, as the Nexus line is no more, and the Mountain View tech giant has now become a smartphone OEM. The long-term impact of these moves remains to be seen, but we already know that Google, the manufacturer, will be adding extra software and UI features to the version of Android that ships with its Pixels.

Guys, this has got to stop. It's not funny anymore. I'll defer to one of my all-time favorite people when it comes to my feelings on this unsavory subject:

Google's Tilt Brush has proven to be one of the most compelling VR experiences for the HTC Vive, letting you paint with crazy materials like electricity and duct tape. It is clearly an experiment in bringing the joy of imagination to life—or creating some form of virtual LSD—and the app's latest update brings a variety of features that only continue to support that theme. There are few to no rules in virtual reality app development, and that can both be freeing or absolutely paralyzing when t...

Okay, so that headline definitely got your attention, but what the hell do cats have to do with Android Nougat? Well, apparently, Google's on a far-out trip reminiscent of the post-India Beatles era, because this is actually a thing.
When was the last time you restarted or shutdown your Mac? In the post-iPhone era, most devices are now powered on almost constantly. For better or for worse, the computing landscape has accommodated this "always on" trend, but you still need to periodically restart your devices—especially your Mac.

Pokémon GO, the biggest augmented reality sensation ever, broke app store records this opening weekend. But it also did something even more important: it gamified physical activity.
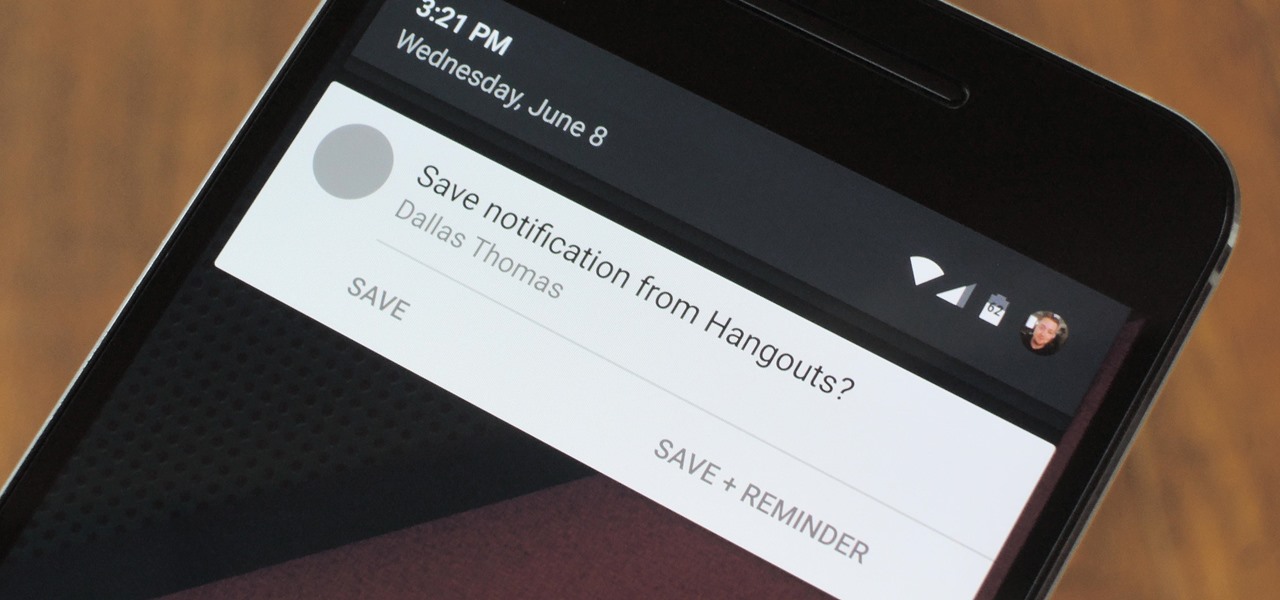
These days, there's almost an expectation that you have to deal with messages as soon as you get them. But that's not always the best way to handle things—sometimes, you're preoccupied with something, and it would be better if you could deal with a new message when you have a chance to give it your full attention.

Bread doesn't have a long shelf life, as most of you probably know quite well from firsthand. You get it home from the store and before you know it, the loaf has turned from soft and perfectly pliable to hard and crumbly—and maybe even moldy! So what's the best way to keep your bread from going bad before you've finished off every delicious slice? Put it in your freezer. It's a simple solution that you've probably heard many times before, but one you probably don't use very often because you ...

Greetings comrades! Great leader has ordered that we gain intel on a website owned by the opposition. For all general purposes we will be scanning nmap.org because they really don't care if Big Brother decides to perform a whois on their IP. We will be using Dmitry for the scanning.

Soda bottle jello went viral when the popular YouTube channel AwesomeDisneyToys posted video directions for this revolutionary gelatin confection. I just had to try it out to see what the hype is all about.

One of the common complaints about dry pasta is that it lacks depth of flavor. This is why, once cooked, it often pairs best with bold and complexly flavored sauces.
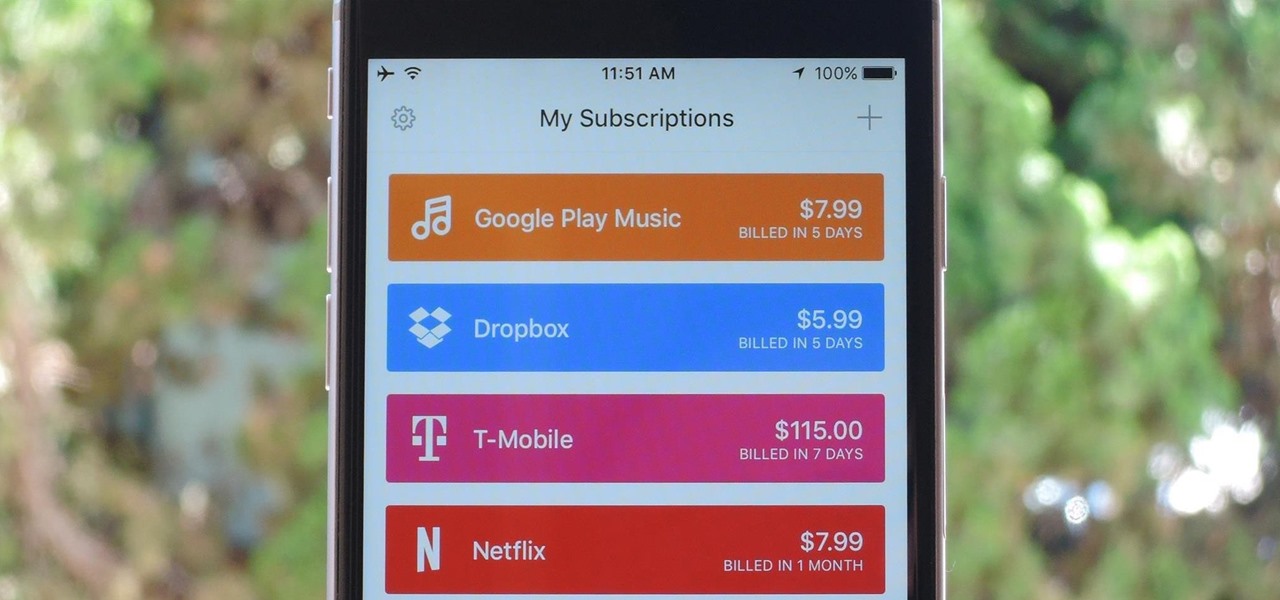
As the internet continues to become a bigger part of our day-to-day lives, we slowly but surely start to rack up a bunch of web-based subscriptions. These internet subscription services—Netflix, Hulu, and Amazon Prime, just to name a few—may seem innocuously cheap individually, but when combined, they actually comprise a significant portion of our monthly bills.

You're only as smart as your communication skills allow you to be, as other people will simply never know your inner genius if you can't effectively express yourself. Regardless of the medium—be it a Facebook post or even a simple text message—this fact remains true.


This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

Hello everyone! How's subnetting going? Did you practice a lot? I hope you did, but even if you didn't we will go through some more examples so you can be feeling confident after reading this article. It's all about that bad boy binary!
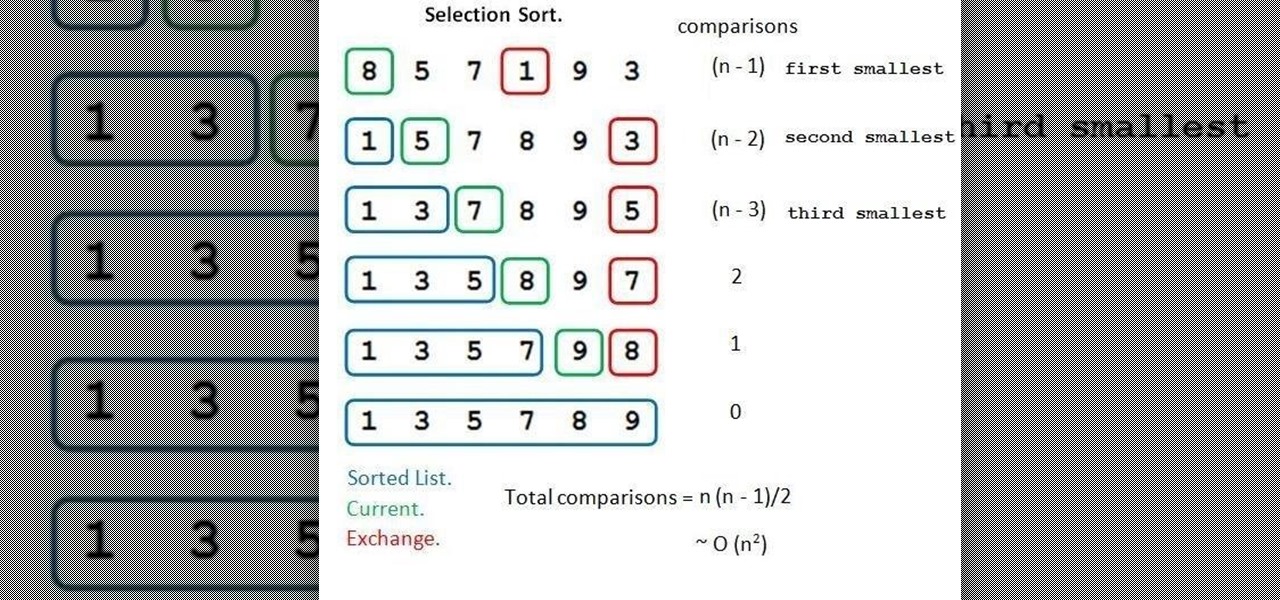
First and foremost, let me once again apologize for that bug, which I failed to notice in time. Alright, alright... Enough sulking, oaktree. Get to it!

The Android Nougat preview build for Nexus devices comes packed to the brim with new functionality: multi-window mode, a dark theme, and a data-saver toggle, just to name a few. However, unless you have a Nexus device, it will be a while before you get these exciting new features by default.

Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

Hello NullByte, it's mkilic! This time I'm here with the C.H.I.P from NTC. Although it is not too popular, the C.H.I.P is a brand new micro computer. It is very similar to the Raspberry Pi or Beaglebone Black. The key difference with this particular board is its cost and size. The C.H.I.P only costs $9 and measures 2.5 x 1.5 inches. In addition to this, the C.H.I.P has built in 802.11 b/g/n Wifi and Bluetooth 4.0. Considering these great specs, what could a Hacker use this for? Step 1: The In...

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.