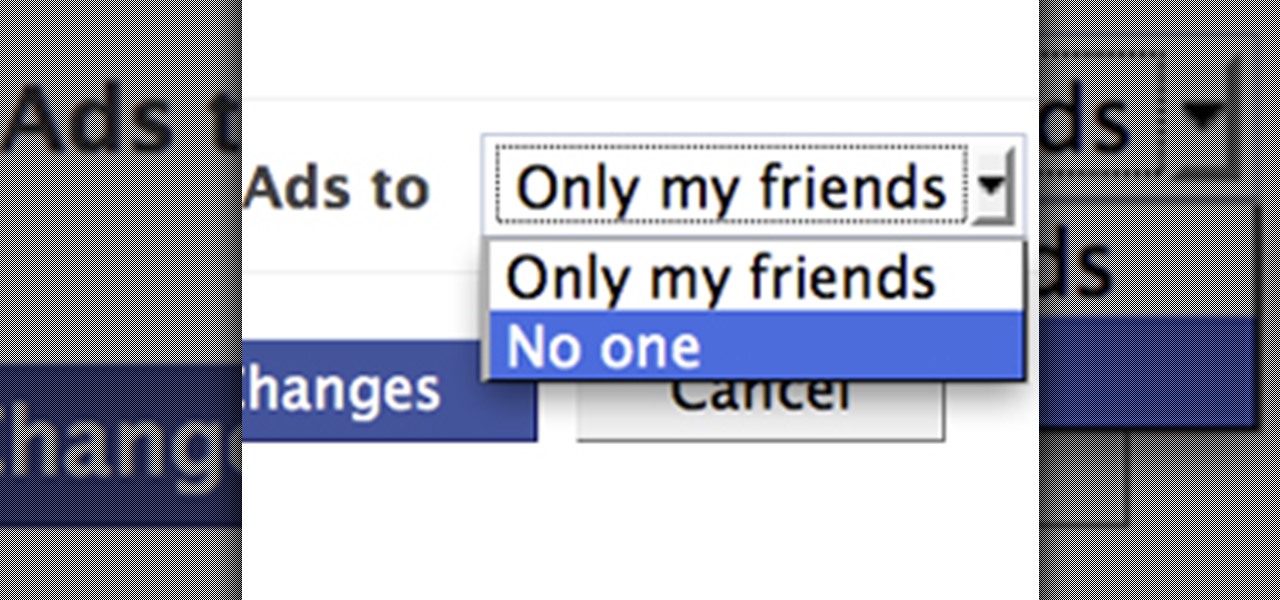
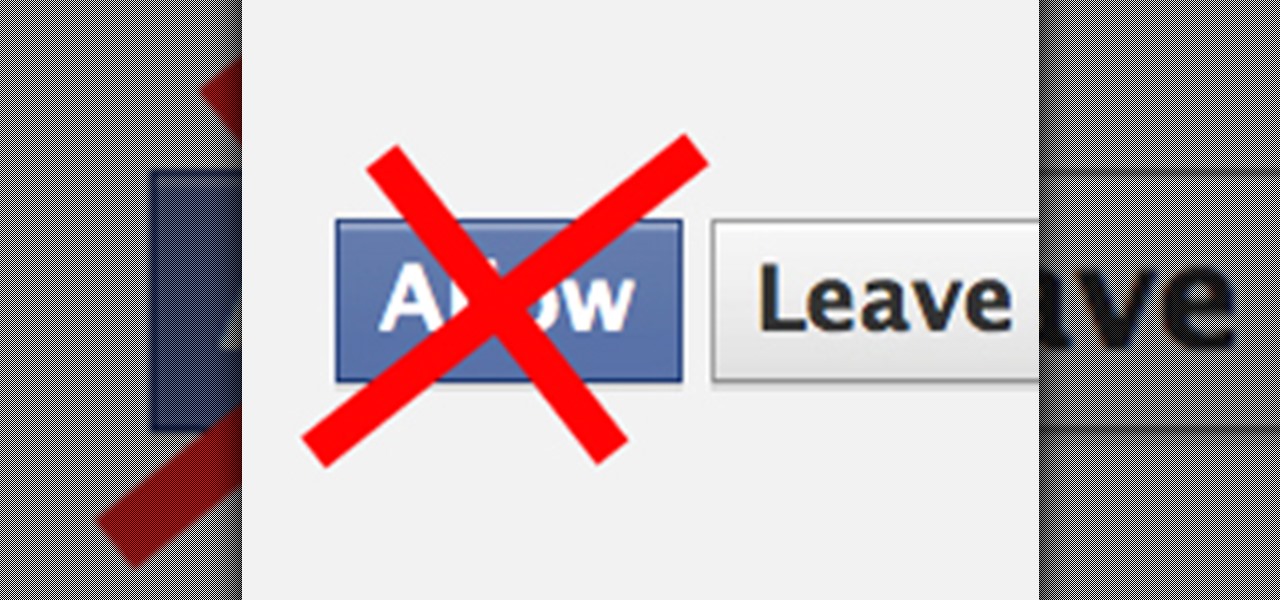
Facebook is constantly evolving, and lately it seems like a bad thing, at least for its users. First, you had to opt out of Instant Personalization, which shared your personal information with Facebook's partner sites. Then, you had to take drastic measures to secure your home address and mobile number from third-party apps and websites. And now?—Now you need to opt out of Facebook Ads.

Nothing on the web is ever private. If you thought you can control your privacy, you were wrong. Websites may give you security options to better hide your information from the world, but ultimately your privacy resides in the hands of the website itself. We've seen how websites let ad companies track our private usage. We've seen how Facebook mucked up their privacy controls. We even saw how websites like Gawker are prone to hackers stealing user information. And now, Etsy has made what was ...
Facebook is at it again. First they invaded your privacy with Instant Personalization, now they plan to take it a step further with their controversial plans to share users' home addresses and mobile phone numbers with third-party developers and websites.
You know it's crazy out there when governments start blocking social websites like Facebook, Twitter and even YouTube. But that's what happened in Egypt, when tens of thousands of anti-government protesters took to the streets on Tuesday (January 25th) in hopes of ending President Hosni Mubarak's 30 years of authoritarian power.
Sputnik, Apollo and the Space Race. If you watched the State of the Union address last night, you probably heard President Barack Obama mention those three things.

The Google Nexus S smartphone is finally here! Well… almost.

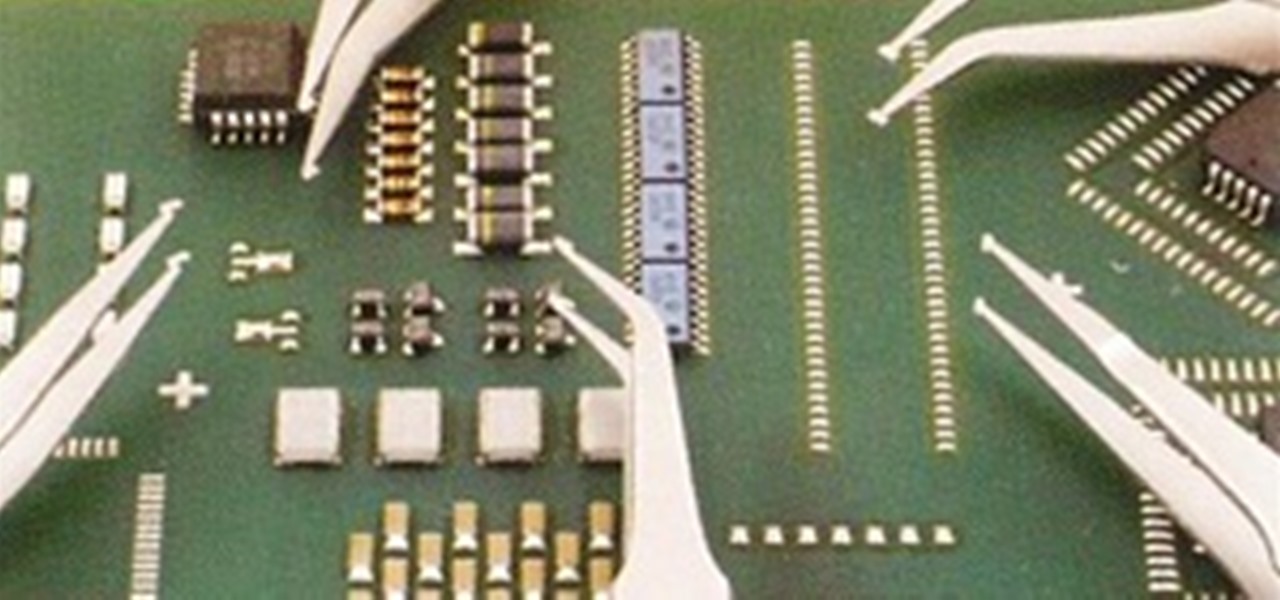
Whenever we make a homemade circuit, we use what are called through-hole components. Any components with long metal leads is a through-hole component. They are great for soldering to, but it's tough to fit enough through-hole resistors and capacitors into a smartphone. To get those last microns, we have surface-mount components for SMDs (surface-mount devices). These are all of those teeny, tiny things you see when you crack open your digital camera or laptop case.
Collapse At Hand Ever since the beginning of the financial crisis and quantitative easing, the question has been before us: How can the Federal Reserve maintain zero interest rates for banks and negative real interest rates for savers and bond holders when the US government is adding $1.5 trillion to the national debt every year via its budget deficits? Not long ago the Fed announced that it was going to continue this policy for another 2 or 3 years. Indeed, the Fed is locked into the policy.
Some interesting news this week, from Obama's new political ad, to the $20,000 payments by Cardinal Dolan. Take a look:

Smartphones are crazy awesome. You can do your banking, track your children, find directions, and even pretend to have a mustache. The only thing that these personal supercomputers are missing is physical interaction with the environment.

There is a secret world hidden just beneath the surface of every pond, lake, and stream. Those waters are filled with wails of hideous creates murdering other hideous creatures for food and sport. Beautiful animals like dragonflies and damselflies that you see in the light of day start their lives in this sparse spartan hellscape. Luckily, being giant mammals, we can pluck these creatures from the depths and look at all of their cool behaviors! All you need is a pond, net, and curiosity.

Today, we are going to combine what we learned from the Introduction to Cryptography article with our Java programming skills. If you are new to Java, check out Matthew's Learn Java: Part One for a quick beginner's lesson, or check out some of the Java tutorials directly on Oracle.

Microcontrollers are great. You can do anything from water your garden to catch wildlife trash diggers in the act—and on the cheap. I prefer to use the Arduino microcontroller because of the large and helpful community built around the website. Though it is my favorite, there are some drawbacks to using an Arduino board in every project. It gets expensive, the board can take up too much space, and the rat's nest of breadboard wires are a pain to repair.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Today's digital cameras record not only the images themselves, but also the metadata behind the scenes, like camera settings, location, date, time, etc. But there's a lot more to say about a photograph. What's the subject? Is it night or day? Outside or inside? Person, place or thing?

If you are a pet owner, going on vacation can be stressful. Usually, you need a friend or neighbor to come over everyday and feed your pets. However, by enslaving robots you can keep your pet happy and enjoy a stress-free holiday.

As some of you Mad Science readers will remember, we recently covered the separation of water into hydrogen and oxygen using electrolysis. Passing a current through water can rend it apart, but we can also recombine that oxygen and hydrogen to make electricity! This is the principle behind those vehicles run by hydrogen fuel cell engines.

Oh Data, You so Awesome! We are going to use Node.JS to gather us some data. Given nodes plethora of well abstracted network abilities and it's deep evened nature, it will make quick work of plugging into various data sources and gathering / making good use of said data.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Today isn't actually Pi Day, but I was unable to get this article out in time. Pi Day was actually yesterday, March 14th (3.14), so let's call this a post-Pi Day treat!

Balloons are fun, but the helium ones are always more entertaining. So today, we're going to learn how to make hydrogen gas by combining toilet bowl cleaner with aluminum foil. With hydrogen, you get the same lighter-than-air properties of helium, plus it will explode! Historically, this has proven disastrous, but for our tiny-scale experiments, it will be safe and fun!

In many ways, we center a large portion of our lives around festivals. They provide us days off from work, allow us time to be content with our families and loved ones, and a give us a chance to eat as much as we want without Aunt Carol saying something about our necks (it's thyroidal, Carol). However, some festivals are determined to push the needle to crazy. Here, for your consideration, are those offenders.

Ivy League schools aren't just places for people to row and sip their drinks out of glasses normal people would never use (i.e. snifters). They also the place for trolling on a grand scale. Just take a look at these Trolls de la Resistance!

US can legally kill Americans in terror groups You read it right. The US can now target Americans who are supposedly part of terrorist groups. Here's my analysis of Attorney General Eric Holder points (keep in mind though, these are point's brought up by MSNBC, original article here):

Search engine optimization (SEO) is now one of the most important topics for website owners to understand. Anyone that depends on their website to bring them business needs to know the ins and outs of SEO in order to maximize their website’s potential. And if you want your website to have a high Google rank then SEO is essential.

I write this post as an afterthought on the recent mass burnings of the Quran by U.S troops. Let me lay down the facts first to clear any misunderstandings:

This article will be about setting up a static IP (Internet Protocol) address in Windows Seven. To see whether you should set one up, ask yourself the following: Do I have many computers in the house hold? Do I get connection issues often? Did you answer yes to both? Then you should set one up.

As my in game name (TehGeekFather) would suggest I tend to like things on the Geekier side of things. Games being one of them. (duh I'm on a Forum dedicated to Minecraft) That being said I am a huge Fallout fan. (NO! not the band. <Sigh>) I'm referring to the post apocalyptic series first developed by Black Isle Studios, the roll playing game division of Interplay, back in 1997. Fallout 1 and 2 were pretty big back then open game play, being able to complete tasks in different ways depending ...

In this article, I'll be showing you how to make a simple yet effective static electricity generator. Basically, this device allows you to carry a constant static charge on your body and discharge it on anything grounded or of opposite polarity. The electricity generated is around 8-10 kV, at a very low current. The shock is enough to startle your friends, just like a static shock from a trampoline or carpeted room. You'll need a little experience in soldering and circuit design to build the ...

Let's face it, the world we live in is far from the fairy-tale land we want it to be, where violence doesn't exist and weapons are not needed. Our foremost goal in life out there in the scary world is simply to survive. And if we need a few tools to accomplish this, we should use them, right?

Sometimes, paying for the whole Xbox LIVE service might seem like a waste of money. You're constantly experiencing lag, you've got people modding and cheating, kids are being loud and obnoxious over the mic, and your kill-to-death ratio is getting dumped on. Basically, the whole multiplayer experience just isn't cutting it anymore—you want to go back to the classic world of single player. Well, there's always downloadable content—simply known as DLC.

It's no secret that water and electronics don't mix well, but somehow, people always manage to combine the two. I've had my fair share of water-damaged electronics, everything from cheap headphones to a desktop computer. My devices are getting dunked in water so much, it's like doughnuts in coffee. And I know I'm not the only one. That jam session with your favorite song will end really quick when your iTouch is chilling in the toilet bowl.

Originally made as portable convenience locks, padlocks are known for their cheap, simplistic and relatively secure design. Their construction is made up of a body, shackle and locking mechanism, with the shackle typically assuming a "U" shape to be easily linked to things like fences and chains.

Here's a delicious Byte of information for you. A proof of concept program on Linux was coded to exploit a known bug in how the Linux Kernel (versions 2.6.39+) handles permissions for the

Last Friday's mission was to accomplish solving HackThisSite, realistic 2. This second mission in a series of realistic simulation missions was designed to be exactly like situations you may encounter in the real world, requesting we help a friend take down a racist hate-group website.

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials on any skill level, and about anything you feel like sharing that...

Here's another delicious Byte. Ucha Gobejishvili, a Georgian Security Researcher under the handle of longrifle0x, discovered two cross site scripting (XSS) vulnerabilities on the official website of Forbes. He discovered the hole in two different locations on the site, and has already informed the website of the vulnerability.

Google is great. They provide us with tons of free services and open source APIs that we can code fun tools for, one of which I don't think gets enough credit: Google Voice.

Last Friday's mission was to accomplish solving HackThisSite, realistic 1. This is the first in a series of realistic simulation missions designed to be exactly like situations you may encounter in the real world. This first mission, we are asked to help a friend manipulate the website voting system for a Battle of the Bands vote count in his favor.