Who doesn't love the world of Game of Thrones? Whether you're a fan of the hit HBO show, or can't wait for George R. R. Martin's next novel installment, it's a story loved by nearly everyone. It's an excellent source of inspiration for Halloween costumes too, ranging from the disturbed to the beautiful. Lady Stoneheart, Catelyn Stark risen from the dead, is the perfect scary choice—bloodied, battered, and carrying a desire for vengeance.

We've all been there: slipping on a pair of perfect yet slightly uncomfortable shoes, hoping they'll stretch to fit perfectly. After about 30 minutes of wear, suddenly those fantastic shoes aren't feeling very great. By the end of the day, your poor feet are covered in throbbing blisters.

We've all been there: you're staring at a fantastic-looking salad or sandwich full of your favorite ingredients. You take a bite, and you taste only one thing—raw onion. A glass of water, a toothbrush, and an hour later, and your breath still tastes like only one thing—raw onion.

Bringing lunch to work or school is a win-win situation. You save money, you eat better, and you create less waste. But while the virtues of brown-bagging it are undeniable, it also gets kind of boring after a while. How many times can you shove a container of salad or noodles into an insulated sack before you say screw it and buy a $12 burrito for lunch instead?

When it comes to theming your Android device, it's the little things that matter most. Whether you're tweaking your navigation buttons or changing the color of system menus, no theme is complete until even the smallest element matches the rest of your color palette.

Whether you live in foggy California or icy Massachusetts, you've more than likely struggled with a cloudy, vision-impairing window that makes even the shortest commute impossible.

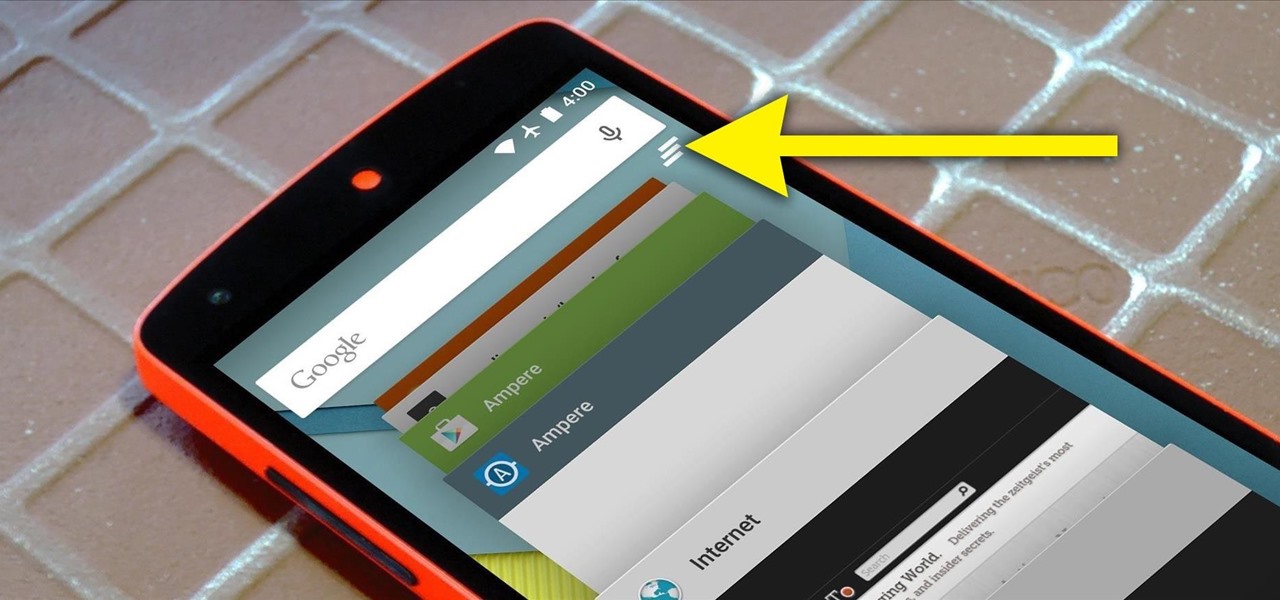
Android 5.0 brought a lot of changes to the world's most popular mobile OS, but few were more central to the user experience than tweaks made to the "Overview" menu (more commonly known as the "Recent Apps" menu). Aside from a visual overhaul, Chrome tabs now exist as separate entries in this list, as do Google searches and a few other activities.

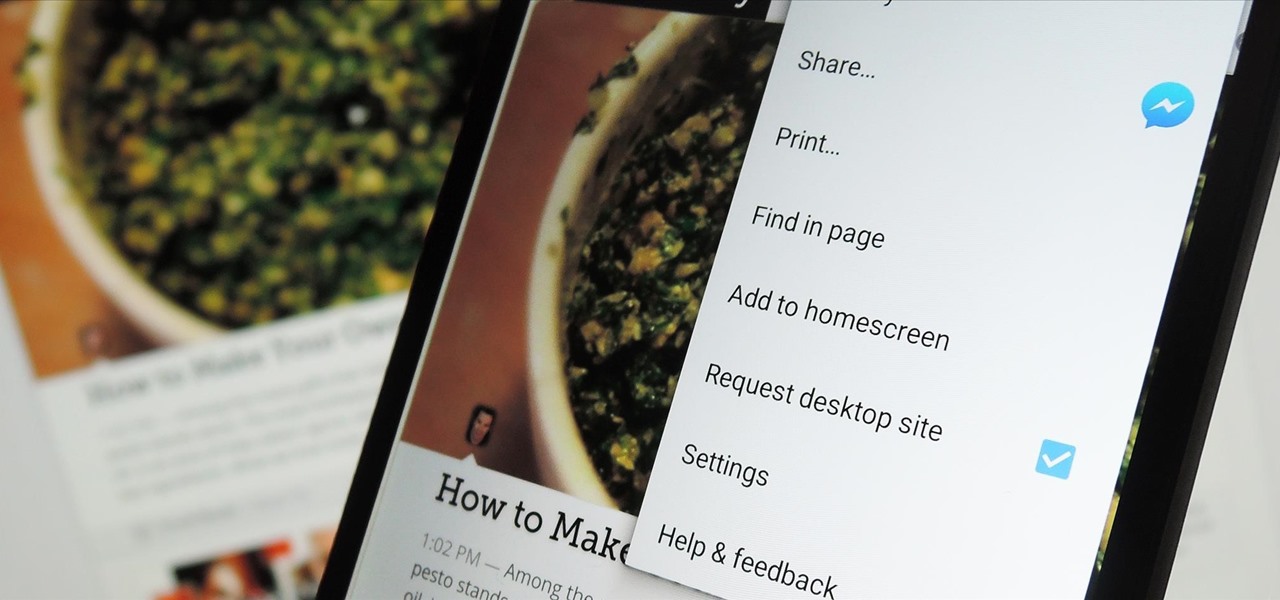
The majority of Android web browsers carry a "desktop mode" feature that makes mobile websites look like normal computer versions. Mobile versions are designed to work faster and more efficiently on smartphones, but sometimes the desktop version looks better on large displays or has additional features not included in the mobile one.

I've known eaters who will fearlessly bite into the hottest peppers, but even they have quailed before durian, the fruit that hails from Southeast Asia and whose smell has been compared to garbage, rotting flesh, and the bathroom post-use. However, this hefty globe with its spiny, prickly outer covering isn't called "the king of fruits" for nothing. According to its many fans, its stench does not correlate to its taste, which has been described in extremely flattering terms. Monica Tan of The...

With developments from tech giants Apple and Samsung being shared throughout the interwebs, the term smartwatch has become increasingly popular over the last year. That being said, smartwatches have been around for a while.

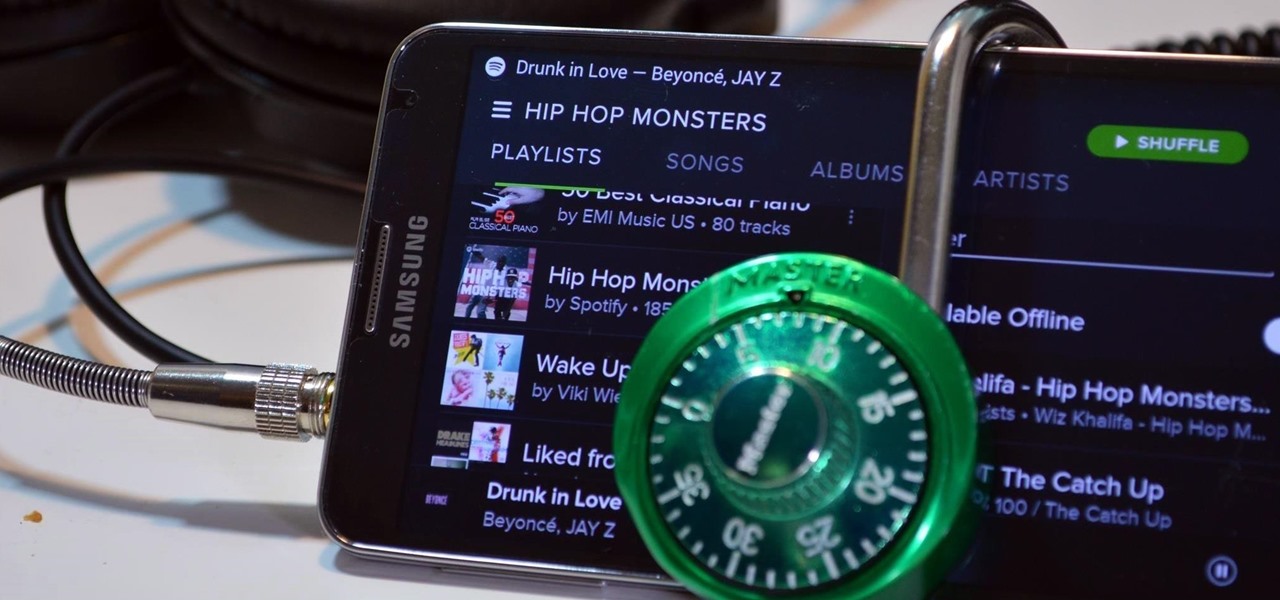
With over 20 million songs, Spotify has become my go-to source for music. I can stream tunes to my desktop or phone, without ever having to worry about storage space being eaten up.

Video: . Dent Repair - Using a Stud Welder Gun

These days, our smartphones carry some very sensitive data. From banking app passwords to personal photos, there are many things on your Nexus 5 that you might not want other people to have access to.

When it comes to smartphones, we can sometimes get a little carried away with the "smart" aspect of it all. Things like apps, games, and softMods take center stage, and we can almost forget that the device also functions as a phone.

Battery life is precious to all mobile device users, and nothing is worse than running out of it. The only thing that can save a device from the dreaded low battery warning is the charger, but who carries those around?

There's one reason why most of us have a Samsung Galaxy S3—because we don't want an iPhone. Yes, there are some pretty cool things about the iPhone aesthetically, but looks aren't everything. Anyway, with the nearly unlimited customizations options we have available for Android, cloning the iPhone-look is no problem—even the lock screen.

Like insurance, it's always better to have a computer mouse and not need it than to need it and not have it. Honestly, I don't want to carry around a clunky mouse with my laptop, so I don't. I do something else, something more convenient. I use my Nexus 7. If you want to give it a try, I'll show you how it's done right now. All you need to is a Wi-Fi network and a specific Android app to control your computer with your Android tablet.

This last weekend, Apple released the second beta of iOS 7.1 for iPad, iPhone, and iPod touch, and I've got a firsthand look of what's to come in iOS 7.1—the first major update since iOS 7 was released.

There are so many kitchen gadgets that only do one thing. You can buy a special tool to strip the kernels off an ear of corn, de-stem your strawberries, or cut bananas into perfectly uniform slices, but that's all it'll do. It's easy to get carried away, and before you know it you find yourself designating an "everything" or "miscellaneous" drawer. Then there are the tools that have multiple functions, but you know you'd never use them often enough to justify spending the money. Unless you co...

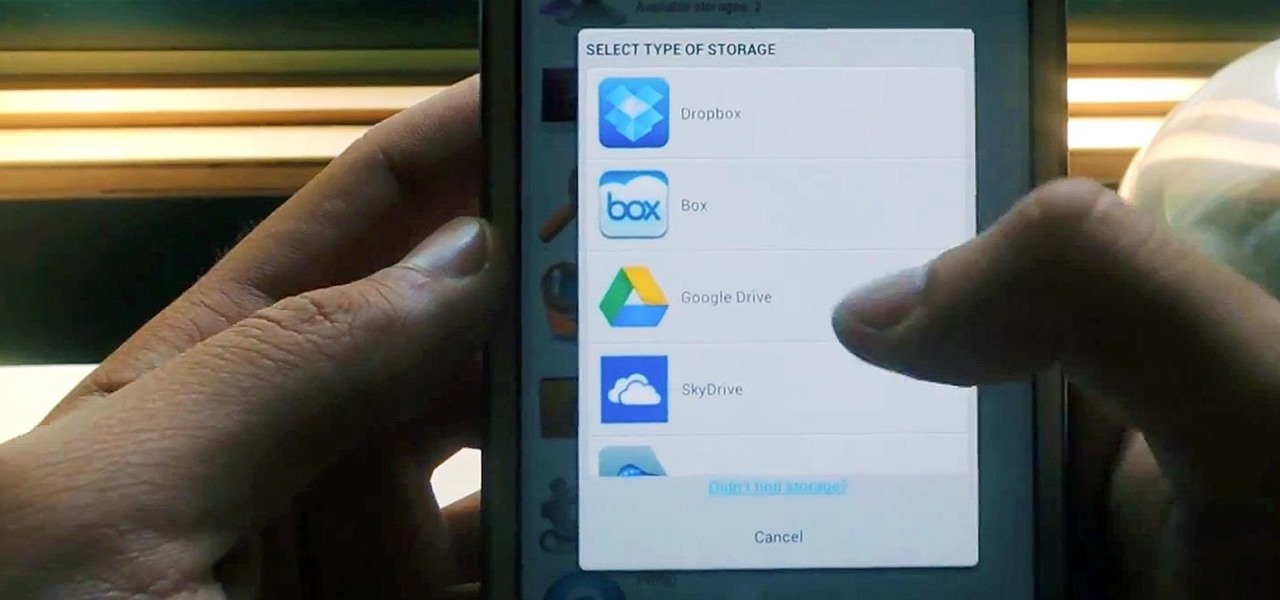
Cloud storage looks pretty good compared to the heavy restrictions that hard drives and other types of external memory carry. The cloud is not only limitless in what it can hold, but it can also easily be accessed from any device that has Internet—your smartphone, work computer, personal laptop, tablet, and more. While accessing a specific cloud storage system like Dropbox or Google Drive may be easy on your Samsung Galaxy Note 2, managing all of them individually can not only get confusing, ...

How can you tell if the pair of Ray-Ban Wayfarer sunglasses that you are about to buy online are not a fake? Follow these 9 simple steps to verify the authenticity of your purchase. Always ask the seller to use the youVerify app prior to purchase. It's Smarter Selling & Safer Shopping.

Cats. Whether you love 'em or hate 'em, you've got to admit—they've got minds of their own. While this makes them incredibly entertaining at times, it can also cause tons of issues for their owners. Trying to "train" a cat is usually an exercise in futility.

In most states, it's completely legal to record a telephone conversation that you're a part of without the other parties knowing. You can even record a conversation that you're not a part of, as long as you have consent from at least one person involved in the call.

There are very, very few things better than a solid Hobbit songI mean, I was almost brought to tears when Pippin busted out this one in The Lord of the Rings: Return of the King.

I don't know how many of you had this experience in your youth, but when I was a kid, I used to actively think about what would happen if I suddenly woke up in a fantasy land, or were to pass through a portal into another space and time. I knew it wouldn't really happen, but when you're a kid, these can be important issues to you. So I slept with my glasses on every night, just in case. Photo from George Pal's The Time Machine.

The Samsung Galaxy Tab 2 (7.0) 4G LTE on Verizon has only been released for a couple months now with good reviews. It comes with dual cameras, memory expansion, and very quick 4G LTE speeds, without needing a contract. While most users are satisfied with the tablet as is, there are others that prefer rooting the tablet in order to install their own custom ROM. Now you can do it with the Samsung Galaxy Tab 2.

In college, I enjoyed eating, sleeping and making my roommate's life a living hell. My most satisfying prank involved 500 red cups stapled together, filled with water, and strewn across his bedroom floor. He was not happy. To clean up, he had to unstaple each cup, carry it to the bathroom, and dump the water. He was furious, but I was okay with sacrificing our friendship in exchange for a fantastic story that I'll probably tell my grandkids one day. If you're not as cruel as me, there are oth...

If you have a smartphone with a good camera, chances are you don't think it's good enough. There's always something that can better with your mobile pics, and for me, that something is closeup shots.

Get more money and experience in Fish World with this simple Facebook Fish World cheat using Cheat Engine 5.5. Easy to perform.

Cheat your way up the ladder, higher and higher, with more levels than anyone on Fish World. Using Cheat Engine, this Facebook Fish World cheat will outperform your expectations on leveling up.

You not only want more money, but you want to level up fast, too. What do you do? Hack with Cheat Engine, that's what. This Facebook Fish World cheat will give you all the money and levels you want.

Need a little more money for your aquarium? How about a little more experience to help your fish along their way? Easy… use Cheat Engine to hack Fish World for whatever you need.

The mother's body can be the source of delivery complications like placenta previa or uterine rupture. If delivery problems do occur, your doctor can usually help you manage these childbirth complications with medication or an emergency cesarean section.

You won't have to ask Santa for holiday-themed augmented reality experiences, because practically any social and shopping app that offers AR effects has them available now.

With smartphone cameras and software getting better and better every year, more and more users are getting passionate about photography. So when you're shopping for a gift to get someone, if they have a smartphone, chances are they'll more than appreciate some tools and accessories for taking better photos with their pocket friend — and we've got some gear ideas they'll love.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

It finally happened! In a world of "go big or go home," Magic Leap has finally done something other than tease us with vague promises and rendered video concepts. Although, other than actually showing us what the developer's kit will look like, it seems little more than a slightly different kind of a tease. To demystify this new product, we here at Next Reality decided to put together what we know about the hardware.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.