There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

The default Camera app got a few more tricks up its sleeves when iOS 11 was released, and the best addition by far was the inclusion of a built-in QR code reader since that meant no more third-party apps just for QR code scanning. However, Apple's built-in QR code scanner did have a vulnerability at one point that would let hackers direct you to a compromised website without you even noticing it.
Another year, another Oscars. This year's red carpet coverage kicks off Sunday, March 4, at 6:30 p.m. EST, while the ceremony itself starts at 8:00 p.m. EST. Finding a stream online isn't always the most straightforward endeavor, especially if you want it to be free. To avoid any delays on the night itself, make sure to run through your viewing options here.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

For all those times when an app either isn't available or simply won't cut it, your phone's internet browser provides access to your favorite websites and services. But some browsers are flat-out better than others, and chances are, the browser that came pre-installed on your phone isn't the best option out there.

Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.

In order for software developers to do their jobs as new hardware reaches the market, they will need the right tools to get their projects off the ground and into augmented and mixed reality devices. There have been completely new approaches to development when it comes to AR and MR, and these are some of the faces behind them.

It's safe to say most of us know the dangers of online security. We know there are people trying to steal our most sensitive information, and we try our best to prevent that theft. But new research is showing what we're doing might not be enough, as the sensors in our phones may be telling hackers everything they want to know.

In this first part of our tutorial series on making physical objects come to life on HoloLens, we are going to set up Vuforia in Unity.

A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists right now, and it can have some serious real-world repercussions, so this is something all iPhone users need to be aware of.

Welcome back, my novice hackers! You have probably heard of the Panama Papers hack by now. This was a hack of the servers at Mossack Fonseca, a major law firm in Panama. This law firm specializes in assisting the rich and powerful to hide their wealth from taxes and scrutiny by creating tax havens overseas.

This is My Review of the Electric Hair Brush Straightener LCD Iron Brush. I have had a Bad Experience please Watch this Video for more info!

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

This Video will Show you how to Prepare Yarn before you do your Yarn Wraps, Braids, Faux Locs....etc

This Video will Show you how to make a Semi-Southern Meal Quick and Easy! I will be Having Fried Chicken, Greens, Sweet Potato Soufflé

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

Video: . Hi, this is a quick demo about how to backdoor executables (software) sent over HTTP using MITMF, backdoor factory

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

Hi there, Elites Welcome to my 6th post, This tutorial will explain how to hack windows, using a program (No-IP)

Now that we have our vulnerable server, it's time to start up BeEF. Getting Started

Hello, hackers and engineers! Today we are going to dive a tiny bit deeper into the secrets of psychology, and how we can use them with hacking and social engineering attacks.

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"

Doxing is the act of finding one's personal information through research and discovery, with little to no information to start with. You may have seen doxing in the news, for instance when not so long ago, hacker team Anonymous doxed and reported thousands of twitter accounts related to ISIS. Doxing can be useful for finding the address of a coworker, or simply investigating people on the internet. The tutorial I will provide to you now will teach you the basics of doxing and how you can prot...

With over a billion monthly active users, it seems that Facebook is nowhere close to being dethroned as the most popular social media service in the world (sorry, Ello). While their stats may be impressive, it doesn't mean that Facebook is as good as it can be.

This tutorial is for everyone who has been waiting for a solution to stream web videos to a Chromecast by using an iPhone or iPad. It is easy as a cakewalk.

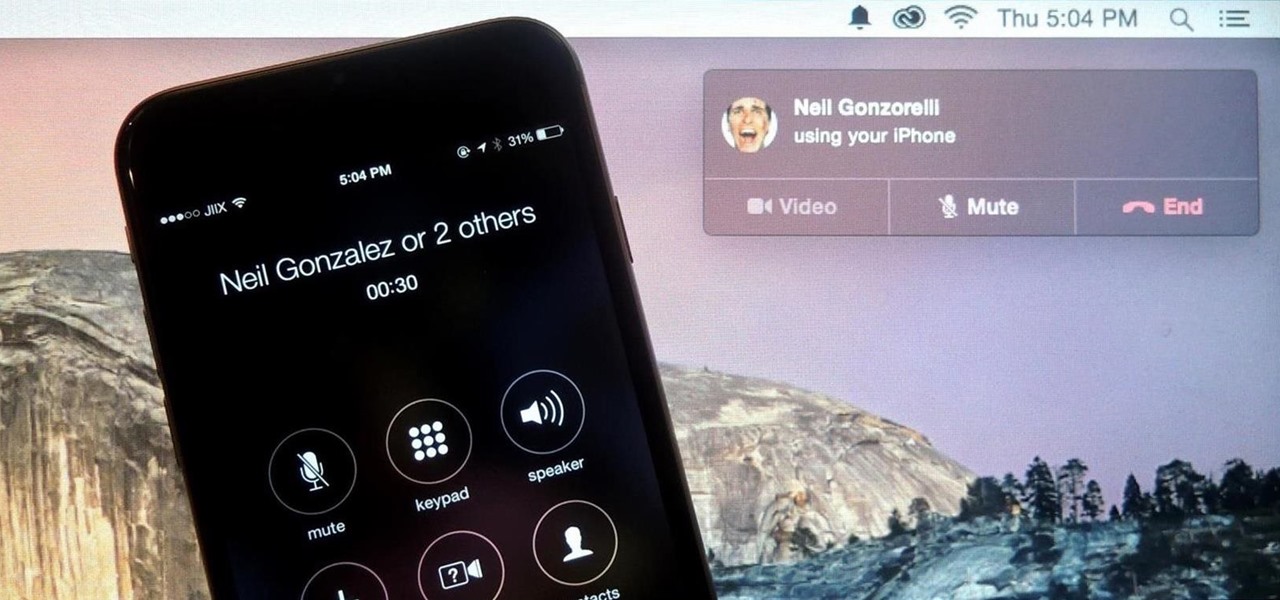
Earlier this year, Apple announced Continuity, a feature for Yosemite and iOS 8 that lets you connect your iOS devices to your Mac in order to access apps, receive phone calls, send text messages, and more while seamlessly switching between the two.

After about 3 weeks of working on it, I finally finished my Cookie Clicker! It's a concept that has been done before by sethbling and others, but I wanted to try and make something closer to the original since one of my subscribers asked me to. I think I delivered! Check my website for a download link (linked)

One day I was contemplating about a canard paper airplane design. After several attempts, here is what I got - the Eurofighter Paper Airplane.

While FIFA may be one of the most corrupt organizations in the world (depending on who you talk to), that won't stop millions of us from tuning in this Thursday, June 12th, to watch the first game of what's going to be a month-long World Cup affair.

Welcome back, my greenhorn hackers!

Video: . How to Dye Weave Extensions Easy!!

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

Being in your twenties is tough. You're not a child anymore, but also not quite a full-fledged "adult" yet. Sure, you do adult things like cook asparagus sometimes, but you're also sweating about securing enough likes on your social media posts.

Website Design Tutorial for Xara Web Designer - graphics folder in designs gallery. In this web design tutorial learn how to add various graphics, modify colors and remix images to create your own custom icons or logos. The web design tutorial will put some of the concepts you learned in previous web design tutorials to practical real world use. If you need assistance using Xara Web Designer let us know and we will do our best to create web design tutorials to help you.

In this web design tutorial learn to create and delete layers. This web design tutorial for Xara Web Designer also covers deleting pages, deleting objects on different layers and re-arranging layers that have objects on them. A brief discussion about MouseOff Layer and MouseOver layer is also introduced in this Xara Tutorial. I would say this is one of the single most important Xara Web Designer Tutorials because layers allow you to do so many unique things with your website within Xara Web D...

First of all I am glad that I was able to find this website and become part of it. So far I love it. Recently Playstation created a competition where a person has to show how online gaming is good. Pretty simple right? You can enter with an image or a video, however I do not think that an image can really show the fun of online gaming. I have created a video which does show some of the good parts of online gaming and I also tried to keep it fun. I would really appreciate if you would have a l...

In this web design tutorial learn how to use the shape tool. In This Web Design tutorial for Xara Web Designer you will learn how to create straight and curved lines and smooth and cusp joins. Also this Xara Tutorial covers deleting and breaking nodes apart on a given line. The shape tool will allow you to make custom shapes and objects to give your website a creative boost.

Use the Xara Web Designer 7 Premium Mould tool to mould, re-shape and change perspectives of objects. The Xara Web Designer Mould tool will allow you to create some very interesting effects to make your website stand-out and have depth. Even the thumbnail shown for this web design video tutorial was created with the envelope tool. If you have ever seen the software boxes shown on various those are usually created with an envelope tool to give the box its perspective.

The upcoming web series "Crypto-Historians" does for cryptohistory what Indiana Jones did for archaeology. For those who don't know, cryptohistory is the study of supernatural or alien elements throughout history, and yes—it's a "real" field.