This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this.

T-Mobile's "Binge On" service for streaming videos has received mixed reactions so far. On one hand, it gives any T-Mobile subscriber unlimited access to popular streaming video services like Netflix and Hulu without having to worry about going over their monthly data cap. On the other hand, it reduces video quality to 480p, which is 6 times lower than full HD.

OS X is built upon a UNIX foundation, which grants you access to the benefits that UNIX offers, including the standard toolkit (make, gcc, clang, git, perl, svn, size, strings, id, and a lot more) via the command line developer tools, which are an essential if you're a developer. Aside from developers, the command line tools can offer benefits to normal users as well, like the ability to purge RAM for better performance.

Before you sell or give away an old iPhone, Find My iPhone, which works in conjunction with Activation Lock (Apple's anti-theft system) needs to be deactivated from your iCloud account. This also applies if you've lost your passcode and are locked out of the device, if you're restoring to a previous iTunes backup, or just want to remove it from your list of iCloud devices.

There's a feature in Google's Photos app for Android, iOS, and the web that lets you create shared albums with your friends and family. It's really a useful feature that makes it fun and easy to collaborate on an album with a person or persons of your choosing.

3D Touch on the iPhone 6S and 6S Plus is a pretty cool feature, and will only get better as more developers begin to roll its functionality into their apps.

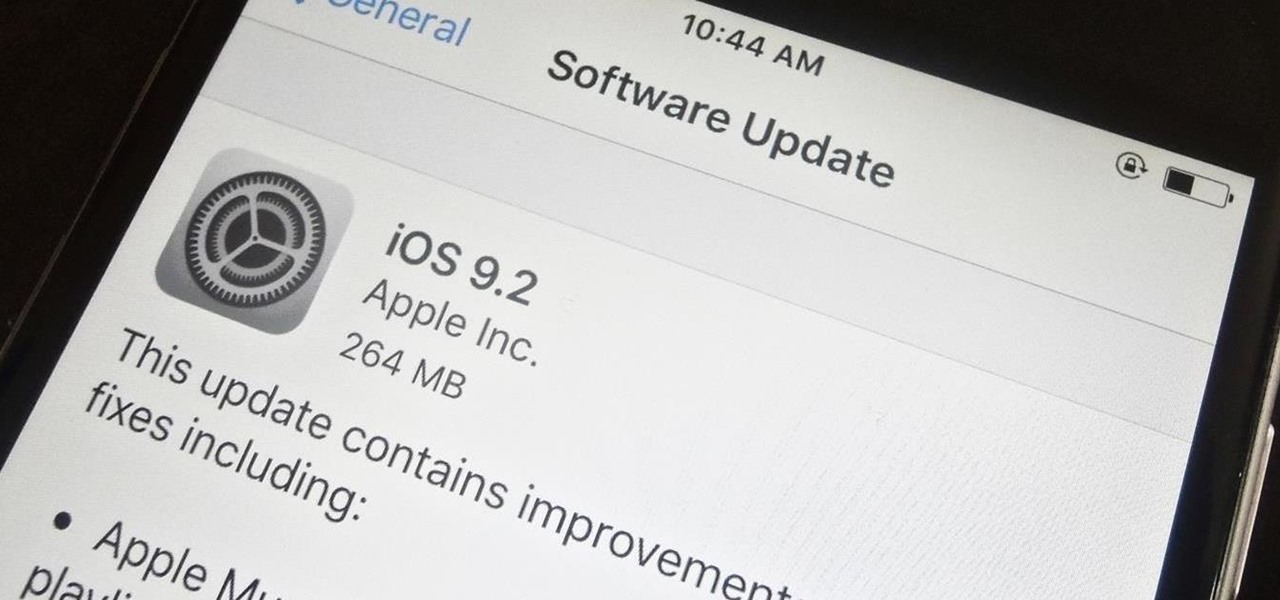
We're near the end of a productive year for Apple, one that introduced a new Apple TV, the iPad Mini 4 (in conjunction with the Apple Pen), the iPad Pro, and the iPhone 6S and 6S Plus, as well as iOS 9. Now, the second major update to iOS 9—version 9.2—has just been released to the public.

Hello! This is my first post on this awesome website! I know that Windows exploits are less common than the more advanced hacks, but I found something I deem pretty cool and figured why not share it with you all. Alright, enough about me, lets begin.

Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

This is my first tutorial on this website. So, if you think anything to be wrong, just place it in the comments.

Microsoft's "Fall Update" to Windows 10, code named Threshold 2, has a lot of new tricks up its sleeve. It's the biggest update we've seen since Windows 10 was released this summer, and it's rolling out to all users right now.

Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

Roughly four years ago, Adobe decided to abandon development of the mobile version of their popular Flash Player browser plugin. Their excuse at the time was that this move would enable them to focus more on HTML5 development for mobile devices and allow them to put more effort into maintaining the fluidity and security of their desktop Flash plugin.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

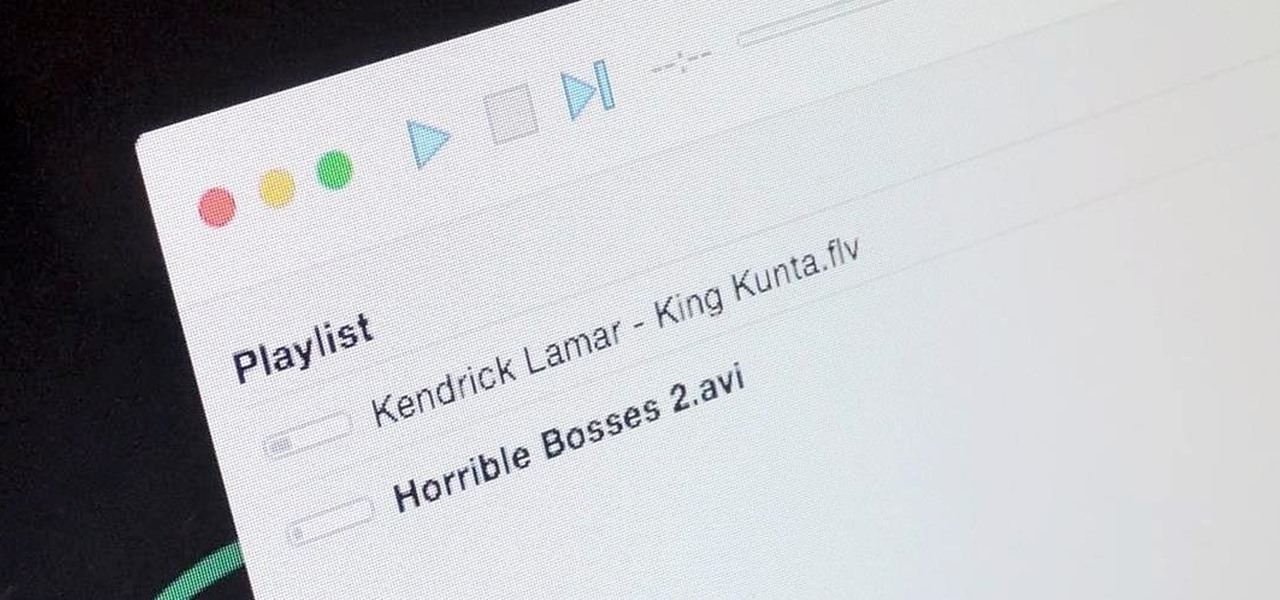
It's a breeze to send videos and music from your phone straight to your TV with an Apple TV or Chromecast, but these devices don't support all file types. While MP4 videos and MP3 music files are the norm these days, I still have a ton of AVI and FLV files that I'd like to watch on a big screen.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

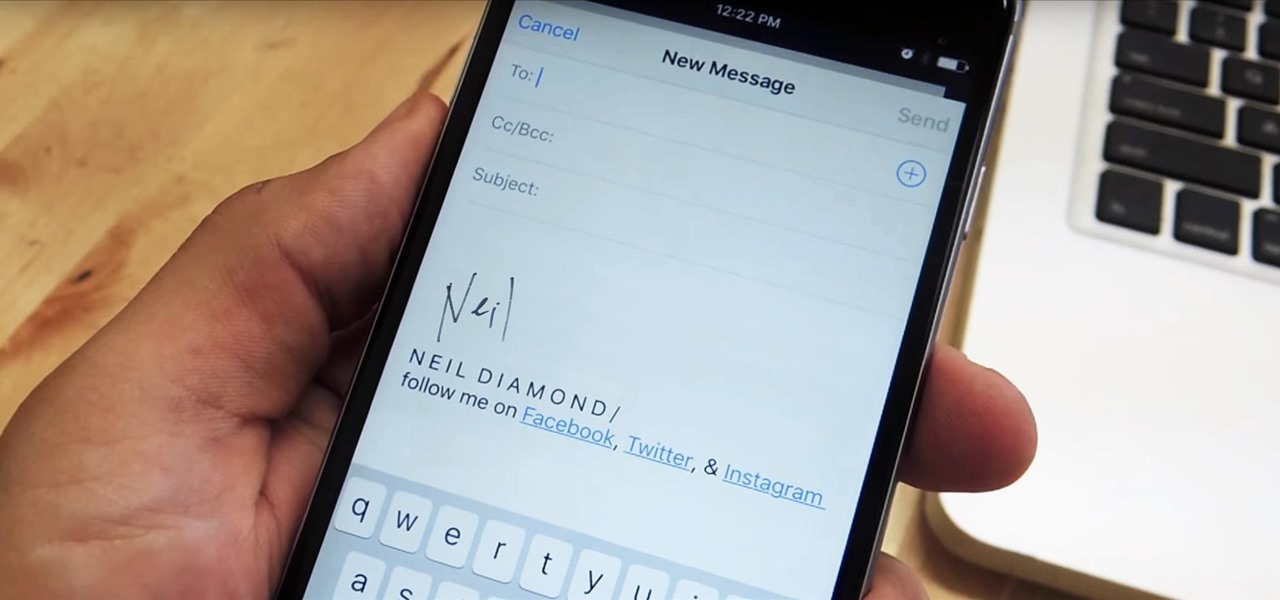
Emails sent from an iPhone, by default, are signed "Sent from my iPhone," which almost seems like a disclaimer in case the email has spelling or formatting errors. If your goal is to look professional while corresponding with coworkers or potential employers, then you're better off removing the signature completely and just typing your name out.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Sushirrito offers burrito-sized sushi rolls that are on the cusp of becoming the trendiest handheld snack to hit the foodie world. According to its website, Peter Yen created the Sushirrito brand, trademarked it in 2008, and opened his first restaurant in 2011 in the Bay Area with Ty Mahler, executive chef.

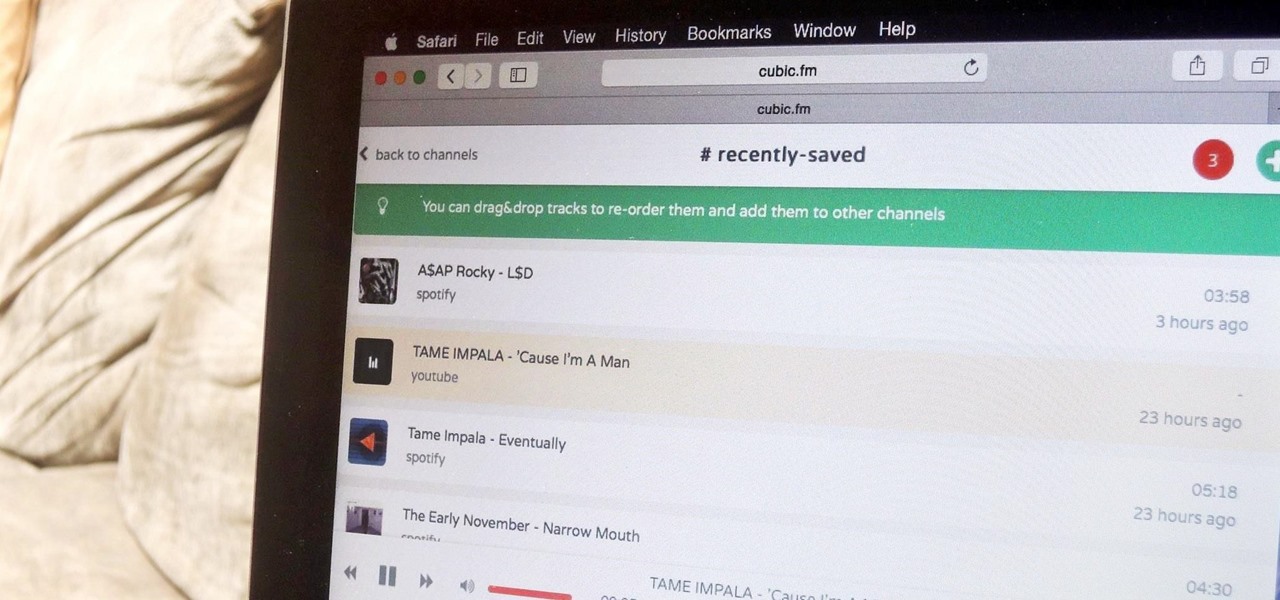
Piracy, it can be argued, is the scourge of the internet. But when it comes to music, sometimes it's best to give a listen to a track or album before deciding to spend your hard-earned money on fully supporting it.

Apple's unveiling of the iPhone 6S, iPhone 6S Plus, Apple TV, and iPad Pro dominated the news today, but at the end of their special September 9th event, they quietly released the final version of iOS 9 to developers, called the Gold Master (GM) build.

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.

Hello you sexy, savage, surreptitiously tech-savvy penetrators (Pun intended)!

All of those keys on your keyboard can do much more than just help to update your Facebook status or fire off a scathing tweet. By learning all of the keyboard shortcuts for apps on your Mac, you can cut back on mouse or trackpad usage to perform actions faster and more efficiently.

Remembering keyboards shortcuts can prove difficult, especially when there are so many to remember, not to mention that they differ from app to app. While tools like CheatSheet can make them easier to use, today I'm going to show you how to enter them without using your keyboard at all.

Managing files can be time consuming on your Mac, for the simple reason that keyboard shortcuts and right-clicks sometimes lack the effectiveness we need. But with a simple third-part app, you can expedite the process of sharing, moving, deleting, and overall managing files on your computer.

Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options;

The options for finding random or specific music to listen to are vast. Spotify is excellent for streaming popular music and new releases, while SoundCloud provides a healthy dose of user-generated remixes and originals. And then there's YouTube for everything else.

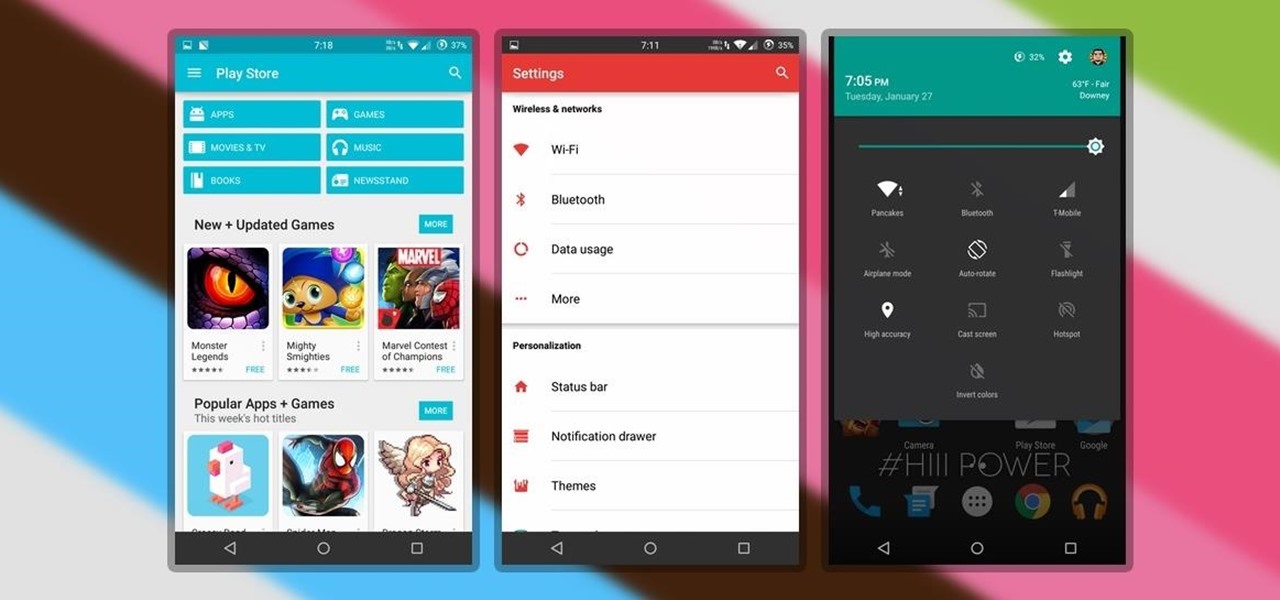
Ad blocking on Android usually requires root access, but a pair of new browsers based on the open source Chromium and Firefox builds are looking to change this.

Let's say that we want to see what someone is doing on their computer? In this tutorial, we'll be hijacking cookie sessions to do just that!

My morning just doesn't start without a cup of coffee and an incredibly hot shower. There's nothing better than sloughing off sleep with a dose of warm, cleansing water. Except, as scientists are pointing out, our habit of showering daily isn't exactly the healthiest choice. Though it feels great, if you have a shower-a-day habit like I do, you're showering all wrong.

Easter may have come and gone, but my love of hard-boiled eggs sure hasn't. Yet as much as I love hard-boiled eggs, I hate making them; I have to work in small batches to have consistent results, and they're always a little overdone, crumbly, and sometimes even green.

Apple's Touch ID, introduced on the iPhone 5S, has definitely made my life a little easier. Not only can I unlock my device, I can use the tech to log in to websites, make purchases through iTunes, and buy groceries at Walgreens using just my fingerprint. Still, as awesome as Touch ID is, it's pretty limited as to what it can do on native apps.

Today marked the official unveiling of the HTC One M9 at Mobile World Congress in Barcelona. The newest HTC flagship will be released by the middle of March globally, and come in gold, gunmetal, pink, and silver. And if you were wondering, yes all of the leaks were pretty much spot on.

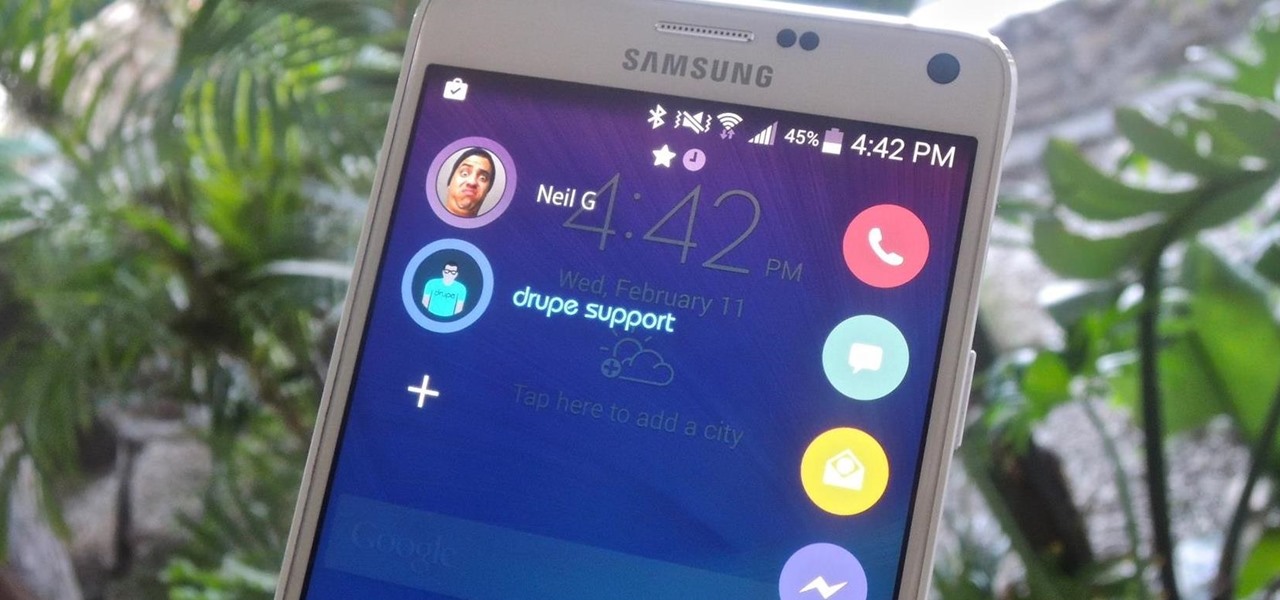
Contacts on your phone can be messy. Keeping all of those numbers, emails, and addresses organized takes time and, even then, they still may not be be as accessible as you want them to be.

Finding the right theme can be a pain. Some are too gaudy or simple, while others look like they were thrown together as a joke. So why not try your hand at making your own?

2015 is quickly shaping up to be the year of the cord cutter, with various media companies finally warming up to the concept of offering live streaming content. In the wake of Dish Network announcing a streaming cable service called Sling TV and Sony unveiling a similar platform in PlayStation Vue, NBC has decided to stream the Super Bowl and all of its festivities online. Before we get to all of the many ways you can stream Super Bowl 49 between the New England Patriots and Seattle Seahawks ...