It seems like each day new rumors and leaks come out for Huawei's upcoming P series devices. Everything from its name change to its specs has been leaked, sometimes with contradicting rumors. One of the biggest leaks is the inclusion of triple rear cameras, a first for smartphones.

When you don't want somebody you're calling to know the real phone number associated with your iPhone, whether it's for privacy reasons, to avoid being called back, or to prevent being ignored, there are multiple things you can do to block it on their caller ID.

No matter your reasons, you might need a second phone number that's a little more disposable than your primary number — a "burner" number, so to speak. If you create this burner number using Google Voice, you'll get new functionality like call forwarding and voicemail transcripts, and best of all, it's completely free.

Despite their sometimes fluffy reputations and occasionally ethically compromised viewpoints, tech evangelists are important, don't let anyone tell you otherwise. The right passionate voice behind the right technology platform or piece of hardware can sometimes spell the difference between fostering a community of potential users and watching a product die on the vine.
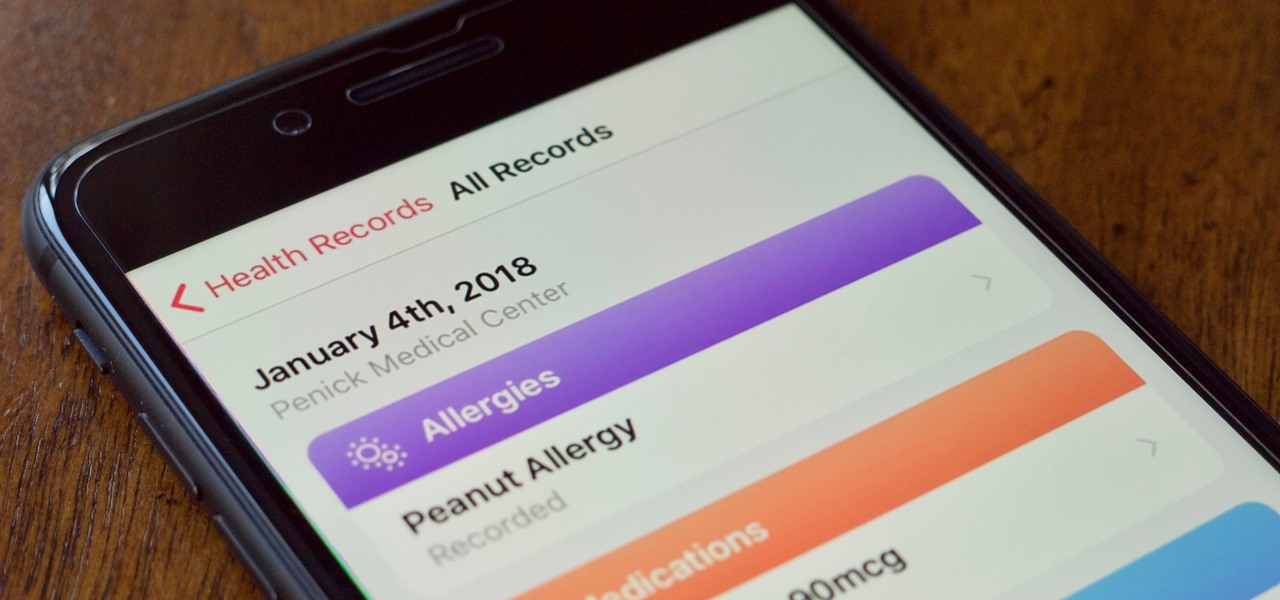
Mobile phones are not only essential for work and communication, they're quickly becoming an integral asset to our health. Your iPhone can store valuable data about fitness, nutrition, heart health, and so much more. And since iOS 11.3, your iPhone can even import a list of allergies, medications, immunizations, hospital visits, and other health information from your doctor or hospital.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

While iOS 11.3 doesn't have as many new features as iOS 11.2, there's still a lot to love about Apple's latest update for iPad, iPhone, and iPod touch, even if some of the best features we were expecting didn't make the cut.

Apple has tools built into iOS to help parents monitor the iPhone habits of their children. However, those same tools can be used by everyday iPhone owners to both hide apps they don't care about, as well as restrict features they don't need or that infringe on privacy. Whether you fit into one category or the other, all iPhone users can benefit from the "Restrictions" feature.

Recently, iPhone users have been bragging that they can set Live Photos as their lock screen wallpaper. While this is a great way to spice up a boring lock screen, Android users shouldn't feel left out in the cold. The highly customizable and feature-rich OS has a few tricks up its sleeve too, and it's really easy to set any GIF as your Android's home screen and/or lock screen background.

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

Just in time for the holiday season, Lenovo has released its Mirage AR head-mounted display with the Star Wars: Jedi Challenges game and accessories. Unfortunately, while its price point is a fraction of most other AR headsets, at the moment, it does have a few issues with the setup process.

Speakers today are a marvel for their portability and sound quality. No longer do we need giant boxes to bring down the house — a speaker that can fit in your hand can fill a room with your favorite music. This is even more important when you pair it with your smartphone, and there are lots of smartphone-friendly speakers on sale this Black Friday.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

Hak5's products get a lot of attention. Popping up in popular shows like Mr. Robot, their hacking tools are bold proof of concepts with space built into the design for the community to add their own tweaks and modifications. On Friday, Oct. 27, Null Byte attended the Hak5 release event in San Francisco to check out their latest devices, including the new Packet Squirrel.

OnePlus surprised the mobile industry last year when it revealed the OnePlus 3T in November, an improved version of the OnePlus 3 that came out just months earlier in June. While many thought this was a fluke, history has repeated itself with the arrival of the OnePlus 5T.

Apple's iOS 11 is finally here, and while they showed off several of the new features it brings to your iPhone, iPad, and iPod touch back at WWDC 2017, they've only just touched the surface of what iOS 11 has to offer. There are a lot of cool new (and sometimes secret) features to explore, so we've collected them all here for you.

At Build 2017, the annual developer's conference, Microsoft featured a Windows Mixed Reality Academy. This class was designed to get a developer started creating Mixed Reality experiences quickly. For those of us already developing for the Microsoft HoloLens, while the class — which is now available on the Microsoft website — did offer our first real chance to work with the new Acer HMD, there was not much depth.

Nintendo's Super NES Classic system, a pint-sized version of the iconic Super NES from the '90s, is highly anticipated in the gaming world. The retro system has already met its fair share of controversies and it's been a long journey to preorder. Finally, the Super NES Classic is officially available for preorder, but it's selling out fast.

Our smartphones are full of personally-identifiable information. So much of what we do with these devices is tracked and recorded to make our experience more streamlined and personalized. For many users, that's a fair trade — but for privacy-minded folks, it's a raw deal.

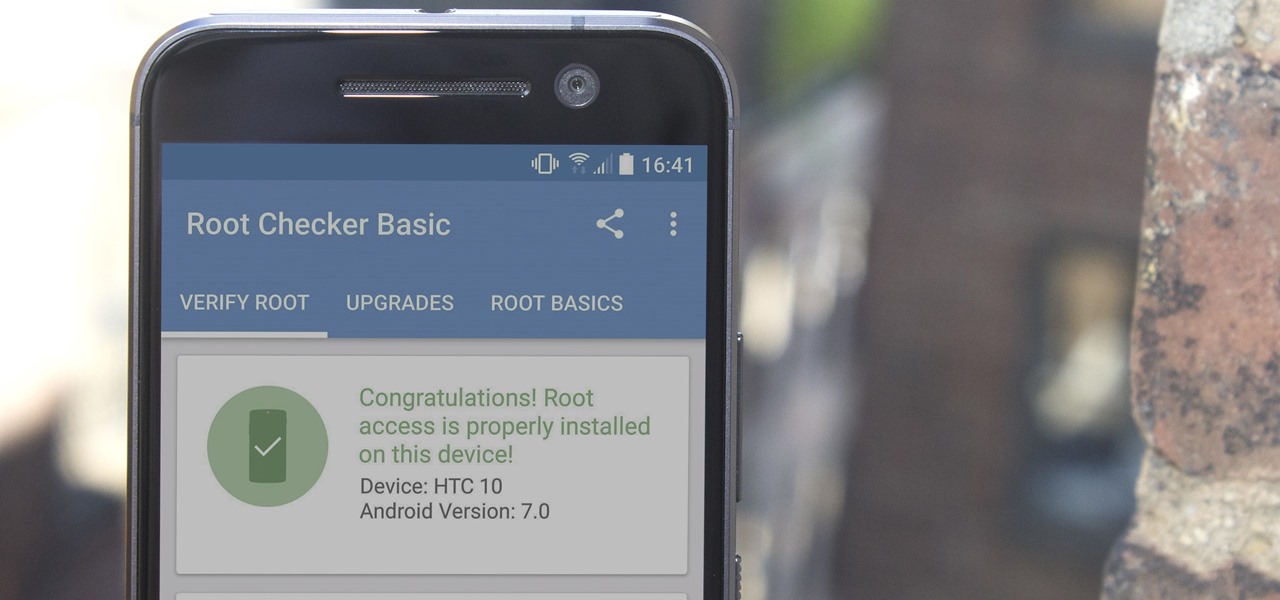
There are many great reasons to root your phone, but if you're not experienced with tools like ADB and Fastboot, it can seem like a daunting task. Fret not, because if you want to root your HTC 10, we're here to walk you through the process.

Apple's been hard at work adding new features and finishing touches to iOS 11, and there's evidence of it everywhere. But there's one place where these changes are more noticeable than perhaps anywhere else — Safari.

Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID attacks. The USB Rubber Ducky can be used to attack any unlocked computer in seconds or to automate processes and save time.

User interfaces for computers have evolved over the years, from the introduction of the keyboard and mouse on the personal computer, to touchscreens on mobile devices, to natural voice recognition. However, the same cannot be said for robots or drones—until now.

For some of us, winter puts the brakes on apps like Pokémon GO since smartphone screens usually only respond to bare fingers. Nobody wants to be that guy who caught frostbite chasing a Sneasel. When you use normal gloves, the display's sensor simple doesn't activate, so that doesn't help any. Fortunately, several options for touchscreen-friendly capacitive gloves are on the market to help you through this last blast of winter.

The coming year promises to be a good one for those of us watching the augmented and mixed reality world. And the Consumer Electronics Show (CES), starting Jan. 5 in Las Vegas, Nevada, for its 50th year, is bringing 2017 in with a bang—we're expecting a ton of great announcements on the horizon.

As a former repair tech, I've heard the same reasons over and over as to why people opt not to purchase phone insurance. Some cite the cost—why pay extra every month for insurance when you're careful with your phone? Deductibles are expensive, so why not just spend that money on a repair instead of getting a refurbished phone as a replacement?

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

Ah, butter—the (literally) heart-stopping star of the dairy world. Everything tastes better with it, from pie crusts and cookies to veggies and steaks. Hell, you can even fry things in butter if you want the best-tasting fried foods of your (short) life.

Smartphone manufacturers do their best to keep you tied down to their ecosystem, but the reality is that there's not much keeping you from switching. Transfer some files, install a few apps here and there, and all of a sudden, you're knee-deep in a new operating system.

Google has already issued a few updates to Android 7.0 Nougat. There aren't many headlining features, as these minor updates are mostly bug fixes and performance improvements. But there's a few security enhancements as well, so staying up-to-date with the latest patches is important for a number of reasons.
Most of you lot would be aware what WPA/WPA2 is so I won't bang on about the encryption or protocols a great deal. In short WPA and WPA2 both have a maximum of 256bit encrypted with a maximum of 64 characters in the password. The encryption is really only 64bit but x 4 because of the way the authentication functions as a 4 way handshake.

Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities appear to exist. If they do, it is your job to test whether they are real and can be exploited.

Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT security professionals to prevent intrusions. So a basic understanding of this ubiquitous IDS is crucial.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

Coverage for the 88th Academy Awards, aka the Oscars, will air live this Sunday, February 28th at 4 p.m. PT (7 p.m. ET). The ceremony itself, hosted by Chris Rock, is set to begin at 5:30 p.m. PT (8:30 p.m. ET).

So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.

Welcome aboard my inquisitive comrades. I am starting a new series that nobody expected coming. It may not seem very exciting at first, but await the last few parts as many startling discoveries will be made. This is a series which I plan to continue after the completion of Nmap, unless you have major objections.