Nothing makes my stomach growl and my mouth water quite like the smell of roasting chicken. It's a pretty universal reaction, too—there's a reason every grocery store places its rotisserie grills and delis near the entrance, after all.

Microsoft decided to give users a free upgrade to Windows 10 if they were previously running Windows 7 or 8—but it came with a catch. Their main motivation for knocking off over $100 from the normal going rate was to get more people using new Microsoft services like Cortana and the Windows Store. To bolster these services, Microsoft implemented a host of new tracking "features" in Windows 10.
I've recently been on holiday in Europe, staying in a hotel that was part of a big chain that included many in the local area. A quick review of the wi-fi within range of my room showed that there was another in the chain that was in range of my Yagi Turbotenna, which naturally got me thinking. If I wanted an anonymous internet connection, this could be quite handy.

A simply frosted or glazed cupcake is like a blank canvas for creative decorations. Intricate cupcakes are works of art, but piping frosting or rolling fondant can be tricky. Luckily, even the most craft-challenged person can use pre-made decorations to create party-worthy cupcakes. Use chocolates or candies to make designs or other decorations and you can have endless fun (and very little stress) creating eye-catching treats.

Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have not been made public yet, but hackers now know the general framework for this type of attack, so you can be certain that they'll hammer out the details in no time.

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

Why did I write this when they're tons of scanning tools available.

Mother Nature is one creative entity, especially when it comes to fruit. Let's face it: most major supermarkets stock only the most common fruits like apples, pears, and grapes, but they're so basic. Why not explore other options, from the stinky-yet delicious durian to the captivating citrus caviar that is finger limes?

Every smartphone manufacturer is susceptible to defects, but after dropping a good chunk of change on a shiny new device, we as consumers have little tolerance for such issues. We want our gadgets to be perfect in every regard, so even the tiniest flaw is irksome.

Thanks to its longevity and familiarity among web designers, Flash is still alive and thriving, but HTML5 is catching up since it can render faster in web browsers, can be customized by developers on a per platform basis, doesn't need a plugin to run, and is less vulnerable than Adobe Flash Player to attacks (for the moment).

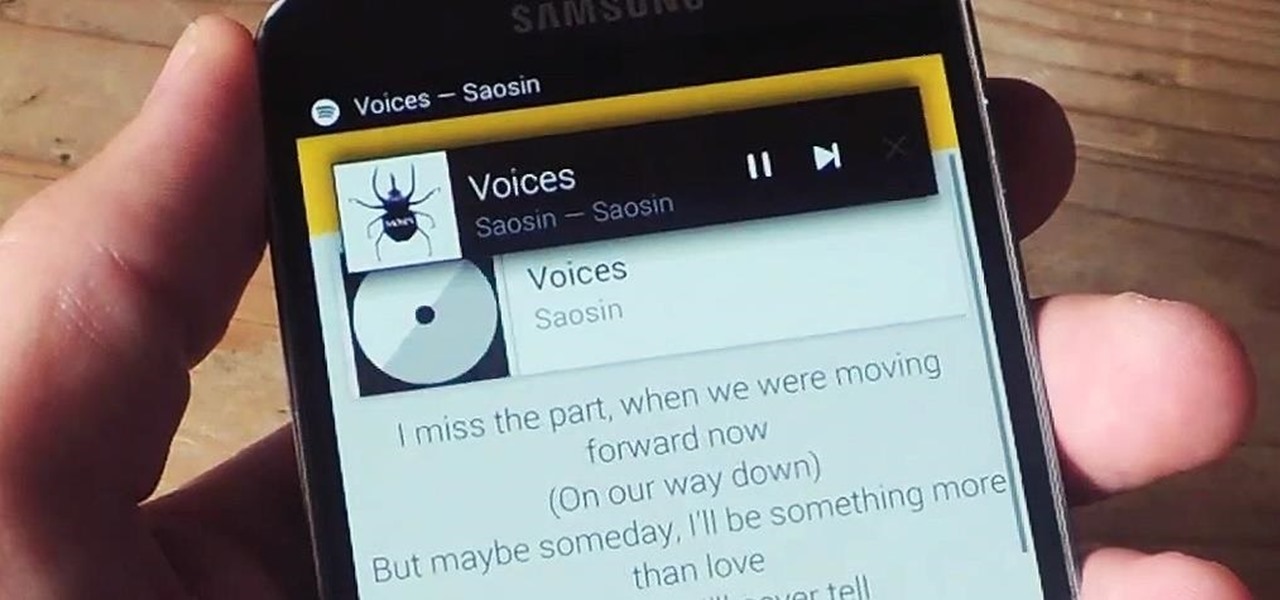
With floating song lyrics displayed over the screen, apps like musiXmatch and Floating Lyrics are perfect for people who want to go beyond just the tunes and delve into a song's message and meaning. And while these floating windows can be convenient, they're not always necessary.

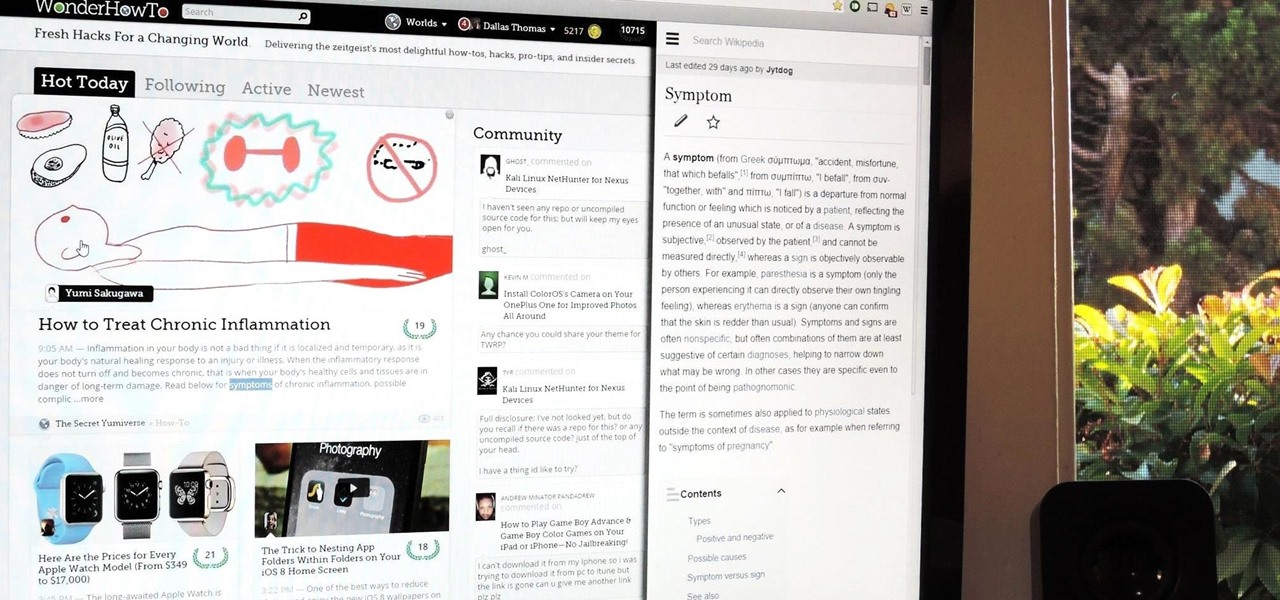
For all of the flak that it catches, Wikipedia is still a great source of information. Contributors take their work very seriously, so the vast majority of information is cited, and the site serves very well as a starting point to learn about a new topic.

If Detective Alonzo Harris from Training Day taught me anything, it's that "It's not what you know, it's what you can prove." So when items mysteriously go missing from my room or my section of the fridge, it's up to me to figure out and prove which roommate took them.

When you hear a song you like but can't quite catch enough of its lyrics, it can be nearly impossible to search for it online. That's where Shazam comes in. For the past decade, they've been making music easier for us to identify by analyzing a track's acoustic footprint, requiring only a few seconds of audio for accurate identification.

Looking back at my childhood in the '90s, I can't help but feel like I was deceived. Movies that took place in the "future," like in the year 2015, would showcase awesome technology. You know, self-driving or flying cars, hoverboards, and virtual displays controlled with hand gestures—so where are they?!

Even if you've put aside your percolator and have gone the way of the pod coffeemaker, there are still dozens of ways to use your leftover coffee filters. Incredibly cheap, absorbent, and shaped with a ruffle, coffee filters are useful in the kitchen, garden, and around the house.

We use our smart devices for pretty much everything these days, from getting directions to playing games just to kill time. They're extremely important to our daily routine, and as we use our devices more and more, things get a little bit messy.

There are certain foods and beverages that can actually brighten your smile or improve your dental health when you chew or sip them. Once you understand their chemical properties or textures, you can look to items you already have in your cupboards or refrigerator to help keep your teeth looking and feeling their best.

While it's currently impossible to go back in time, there is something wonderful about being able to undo the stupid stuff that you just did. While this is only really possible in the digital world, it does save you from real-life repercussions. If you've ever sent an email to the wrong person or sent some not-so-genius text messages, you know exactly what I'm talking about.

Getting a good night's sleep is critical to maintain good health, a better mood, and clear your mind for whatever the day has planned for you. But in practice, whether you're tired or not, the world has a way of preventing it, either through your partner's snoring, your neighbor's music, or the road construction going on right by your bedroom window. It can get rough.

When you're on a limited data plan, bumping up against your monthly cap is a major concern. Overage fees are incredibly high these days, and being throttled down to 2G coverage almost renders a smartphone completely useless.

One of the more talked-about features of Android Lollipop is a new Priority Mode that allows you to mute all notifications except for those coming from starred contacts. As simple as that sounds, this can still be a bit confusing—or at least lead to some unwanted interruptions.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

Social media is constantly evolving, and as a result, we're now capable of sharing much more than we were even just a few years ago. Television, on the other hand, continues to hold strong as one of America's favorite pastimes.

If you've ever tried to record a Snapchat video of a song playing in your car, you know that it's impossible to do if the song is playing on the same device that you're Snapchatting with.

Being the bearer of bad news is unpleasant; there's nothing more uncomfortable than offering up a spoonful of negativity. Whether you're a supervisor who spends a lot of time interviewing and rejecting candidates, or simply someone who has to say "no" to a friend, it's never fun to break bad news. But sharing unpleasant words or feedback with another person can become less of a burden with a few simple steps.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

Admit it: you've been caught muttering to yourself under your breath in very public places. Maybe you've gotten stares while wandering the grocery store talking to yourself out loud. If you're like me, you might even talk yourself through various tasks, giving the atmosphere a little background noise.

Sony's latest flagship, the Xperia Z3, comes with some pretty high-end hardware, but what really draws me to it are the aesthetics of its ROM, Xperia UI. Even though my HTC One M8 can still go toe-to-toe with the Z3 in a performance matchup, there is something about Sony's UI that is simply missing from my HTC.

Earlier this month, John Oliver spent a segment on Last Week Tonight explaining native advertising, a practice followed by many online media outlets such as BuzzFeed, The New York Times, and VICE, which combines editorial content along with sponsored advertisements.

Unlike the suave 007 that Daniel Craig portrayed, I am not a spy, nor am I that charming, but I do occasionally enjoy taking a stealthy video. Maybe I'm a jerk, but I often catch people doing ridiculous things and just think, "Aren't you embarrassed?"

The Spanish and Portuguese introduced many things (some desirable, some not, depending on your POV) to Mexico in the sixteenth century: Christianity, language, and lots of flora and fauna.

It's been over three months since iOS 7.1 came out, but your wait for jailbreak is now over. If you're still running iOS 7.0 iterations to maintain your jailbreak, you can now finally update to the latest and greatest thanks to a Chinese team of developers, who recently released their untethered jailbreak for Apple devices running iOS 7.1, 7.1.1, and even 7.1.2.

Shopping online can be as easy as buying cigars in Mexico. You find what you like, ask for the price, and walk away. "My friend! Come back! I give you 10% off. Just for you."

Videos are great for catching fleeting moments, and photos are insanely easy to share with anyone, but how can you get the best of both worlds?

While Snapchat's latest update brought messaging and video chatting, it also ruined something for us softModders—KeepChat. With KeepChat, we were able to save pictures and videos sent to us without the other person being notified. It was pretty slick, and I was beginning to miss it.

I passed a cool looking bar the other day that I wanted to check out. When the weekend came around, I was ready to go, but for the life of me couldn't remember where it was. Not wanting to retrace my steps or drive around aimlessly, I gave up.

You've seen the Samsung Fingers and the Emoji Translator, and I know you spent a good part of the day catching Pokémon, but now that April Fool's Day is officially upon us, the flood of gags has reached a tipping point. Here's the best of what we've seen today.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

The mother of all games is almost here. Super Bowl XLVIII pits the Seattle Seahawks (or Seachickens, if you're from the Bay Area) against the Denver Broncos and regent exemplar of neck surgeries, Peyton Manning.