"Ahoy-hoy." If telephone titan Alexander Graham Bell had his way, we'd all be answering phones like Mr. Burns. Thankfully, frienemy Thomas Edison had enough sense to realize we weren't always on the briny. He preferred "hello" as our standard telephone greeting, which he is credited with coining in 1877. Fellow American pioneer Davy Crockett actually used it as a greeting first in 1833 (as compared to an exclamation)—but in print, not over the phone.
For those needing to replace old controller hardware on cutting mills, those into native retro gaming, or for those who want to see what all the fuss was about in the 1980's, or for those who just want a play with old but great technology, this tutorial shows you step-by-step processing getting the breakthrough desktop operating system running on the latest greatest hardware.

How to cut Drywall, Sheetrock, Plasterboard. THE EASY WAY! G'day Knuckleheads, Uncle Knackers here and welcome to Video Two of my ten part series titled 'My Top Ten DIY Tips' as nominated by you..

Food can smell great before, during, and after cooking. A pot of stew simmering away on the stove will tantalize you all afternoon, and there's nothing better than the smell of fresh-baked cookies lingering in the house for hours.

The art of persuasion is a very crucial characteristic that anyone can learn, and it has countless benefits. Whether it's at work, home, or in social situations, the ability to be veritably persuasive can have an unheralded impact on your daily life.

We frequently associate plastics with the modern era, starting at around the 1950s with the prevalence of bakelite. However, for all of you "you can't use plastic in Steampunk" purists out there, I have bad news for you:

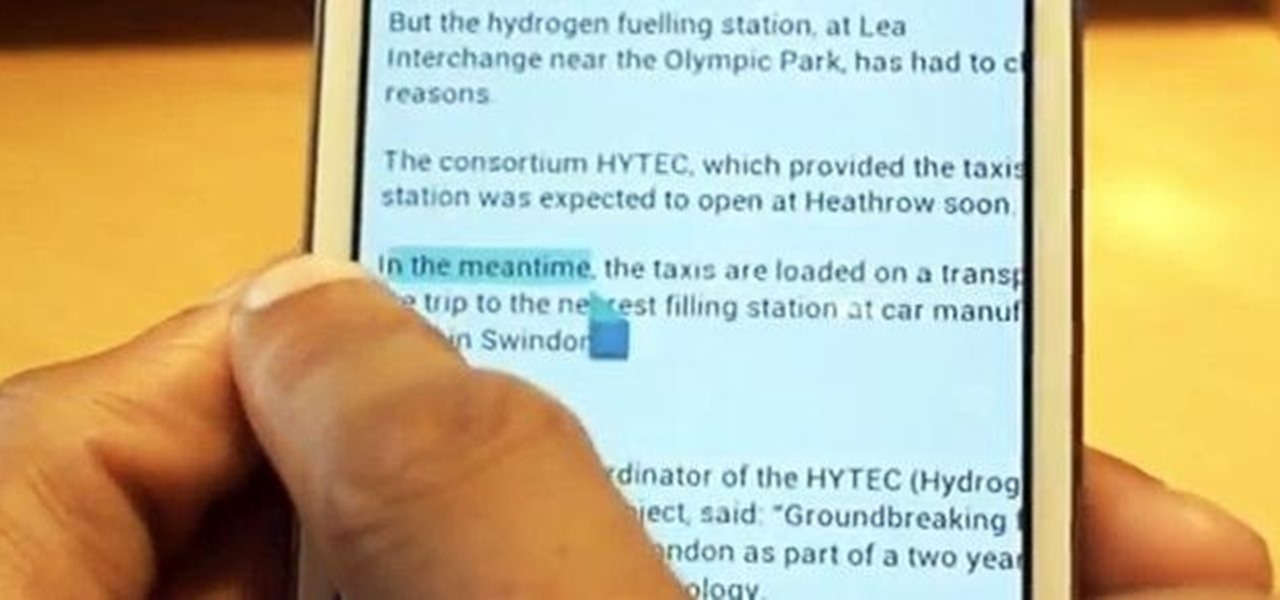
If you have a Samsung Galaxy S3 or Galaxy Note 2, you might not have noticed it yet, but there's an annoying little bug that centers around your clipboard. If you tend to do a lot of copy/pasting on your device, you've probably seen it happen—your phone crashes.

We go to such great lengths to secure our smartphones. We put passwords on our lock screens, encrypt our data, and install anti-theft programs, but it's never enough—someone, somewhere, will find a way around any protective measure you use, no matter how sophisticated.

Earlier today, a meteorite flew over the Chelyabinsk region of Russia, triggering a shock wave that injured hundreds of people and caused damage to buildings and vehicles in the area. Witnesses describe seeing a bright ball of light streak through the sky followed by a loud boom as the 10-ton meteorite entered the Earth's atmosphere and exploded.

A common problem on bumper covers is that the tabs that attach the bumper to the car get broken. This is critical, as this is what secures and aligns the bumper cover. Many times, a broken tab is all that is wrong with the bumper cover. With the cost of these plastic parts $200 to $700, the replacement cost can break the bank.

I love my Mac just the way it is. Well, minus the fact that I accidentally deleted iPhoto and would now have to pay $14.99 to get it back. Other than that, my Mac is pretty sweet.

The problem of system freezes is not new to the world of Windows and this has come to light even in the latest Windows 8 release. In the event that your system freezes, you cannot open your desktop files, some controls stop functioning, or you are unable to launch the start screen applications either. You may experience this unusual behavior after updating Apps in the store or due to a driver issue. Sometimes, freezes occur because of video card problems too. In order to do away with these Wi...

The Geminid meteor shower happens every December and has been observed for over 500 years. It's is also known as Winter's Fireworks because when viewed from the right location, there are enough meteors to light up the whole night sky, and some of them can even be different colors. The shower appears to come from the Gemini constellation, but is actually caused by Earth passing through the tail of dust and debris left behind by the comet 3200 Phaethon.

With Sprint already rolling out their Jelly Bean updates to Samsung Galaxy S III owners here in the United States, international users have already had a chance to check out Android's newest OS on their S3, but all is not gravy.

It can be incredibly frustrating to take closeup shots with an iPhone camera—or any smartphone camera for that matter. Even if your phone's camera is top of the line, you'll still get a fuzzy picture if you get to close to your subject.

Hello and welcome to my post. I would like to share a few things I have picked up along the way - while feeding my two dwarf rabbits. In this tutorial I would like to answer the question - How to choose the best food for your rabbit?

With how quickly technology evolves in this day and age, it's only natural that people replace their computers every couple years—even sooner. It seems that right when you get a new desktop, there's always a faster model with more features released the following week.

3D printing has been around for a while, but until recently it was used mostly for prototyping and research. Now, with technological advancements, it seems like everyone is using 3D printers, from crime scene investigators to garage hobbyists and hackers. Below are some of the most innovative uses people have come up with so far.

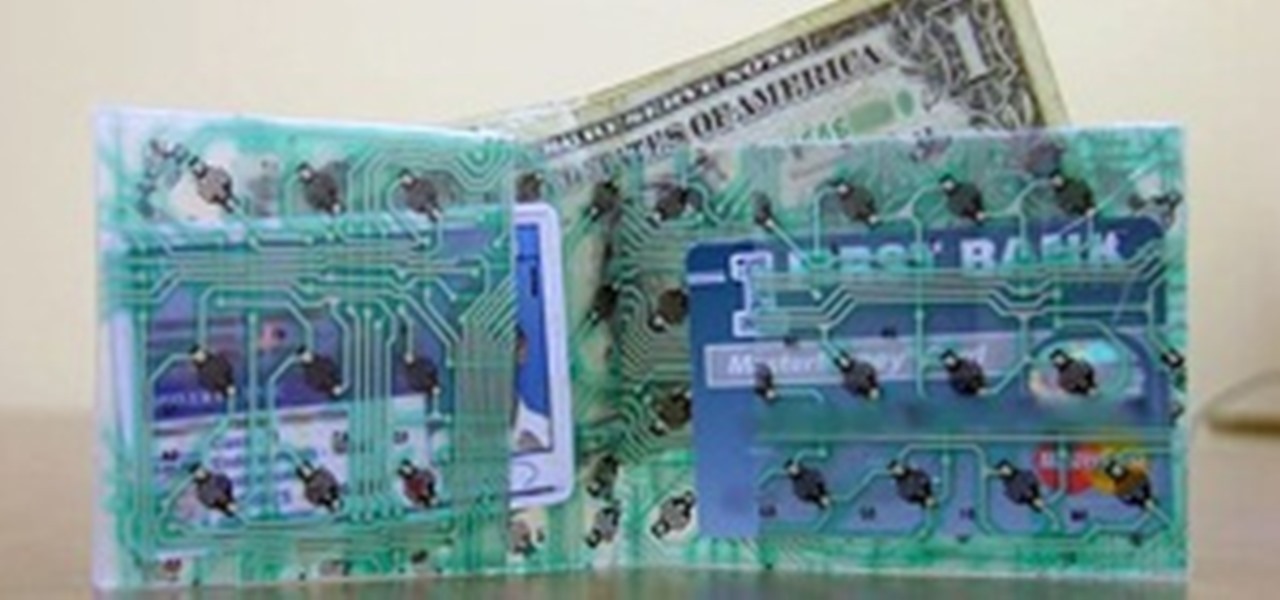
What's a penny worth these days? Not much. But could there be some free energy hidden inside your spare pennies? You'd be surprised! See how I hack together stacks of pennies into makeshift batteries that can drive small-current devices like LEDs and calculators.

Okay, you can't really become the king of the world by stacking three pistons. For that, you have to stack four pistons.

For those of us with small children, bath time can be very fun. Kids usually love splashing about and playing with their toys in the water! One thing they don't love however, is getting water in their eyes or on their face.

Hello! This tutorial is made for all who like to sunbath, but also do not want to get those tiny first wrinkles too soon. Or even skin cancer.

Firstly, let me say a few quick things: Once built, this is a lazy (one button) way to harvest melons, but this is going to be a complex and lengthy build.

We've all been there. You wake up early, hungry for breakfast, but not just any breakfast will do. You want bacon and eggs. So, you blindly stumble into your kitchen, underwear-clad, and begin fumbling about with pots and pans. After a few minutes, you fill your pan with delicious and smokey rashers and turn the heat on. Everything seems okay... until the bacon actually starts to cook. With a splat, burning hot grease flies out of the pan and bombards your skin, causing intense pain and great...

If you're always taking blurry and underexposed pics with your mobile device, try using some of the tips below to turn your phone into a valuable photography asset. It doesn't matter if you have an iPhone, Android smartphone, or even a first-gen camera phone... you can still take some beautiful, winning photographs.
(Series designed to help explore whether your ideal employment ideas should be formalized into a business venture or as an employee or volunteer value added problem solver).

We've gathered some of our favorite pranks with the seasonally appropriate for all you college kids out there. You're more than likely cohabitating with a complete stranger, and what better way to make a good first impression and develop a strong personal relationship than subject them to a hilarious prank?

There are always certain situations that unnerve people. One of the biggest unnerving situations you may encounter is a job interview. The nervousness breaks out and you look like a total fool, but it's just the nerves. It happens. And why can't you control it? It's hard for some to keep their cool, but Chantilliscious offers up some advice on what she does to prepare for an anxiety-causing situation.

Lauren Dickerson and Ed Barnett demonstrates how to properly use a cane. Using a cane is appropriate when you have impaired mobility of any kind such as an injury caused by a knee or a hip. First, measure the cane. Hold the cane about four inches away from you and it should come to hip height. When the cane is the right length, your arm should come at a 30 degree angle. Hold the cane on the stronger side of your body. When you walk, bring the cane and your weaker leg out together. Then bring ...

In this video the instructor shows how to repair the volume on your iPhone. This video advices caution and is not responsible for any damage caused to your property. While using iPhone people often face different kinds of problems with volume like low volume or no volume at all. If the warranty expires then throwing away the iPhone and getting a new one because of this is not a good idea. To get around this follow the given procedure given in the video. Now open your iPhone and use a safety p...

There's no shortage of ice cream recipes out there, but one ice cream shop in London has found a unique recipe to sell to its customers, and of course it's controversial—breast milk ice cream.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

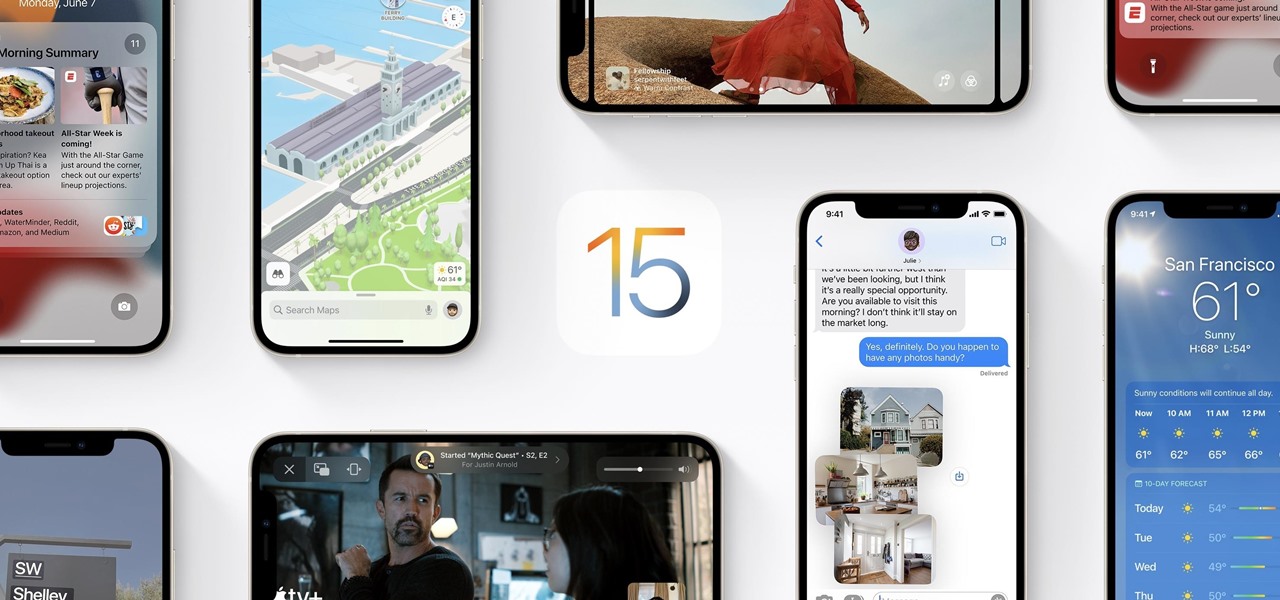
Apple released the second beta for iOS 15 on Thursday, June 24. The update includes FaceTime's "SharePlay" feature for the first time, a new Maps icon, updates to Focus mode, in addition to many other changes and bug fixes.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

It's finally out. After months of testing, iOS 13 is available to install on your iPhone, which means over 200+ new features you can use right now. The update, released on Sept. 19, can be installed over the air or from a restore image using iTunes in macOS Mojave and older or Finder in macOS Catalina. Ditto for the 13.1 update issued on Sept. 24.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.