
How To: Keep the Government Out of Your Smartphone
We use smartphones for just about everything, and while that may be beneficial to us in our day-to-day lives, it can also be used against us in the court of law.


We use smartphones for just about everything, and while that may be beneficial to us in our day-to-day lives, it can also be used against us in the court of law.

Store-bought fake blood isn't too expensive, but the consistency and color are always the same. Real blood varies, from bright red when oxygenated (arterial blood) to deep, dark red when deoxygenated (venous blood), and it can be either thick or thin. So to achieve the best special effect, you're better off making a batch of DIY fake blood yourself to get the look and texture you're going for. And it's very simple to do.

This video shows you how easy it is to install the J&T water temperature gauge on your snowmobile. This is a "Must Have" for any snowmobile rider in order to keep an eye on your water temperature so you don't melt a piston.

In this video series learn from Mark Williams a 6th year Registered Plumbers Apprentice with over 11,000 hours of experience as he discloses tips and techniques such as what chemicals to use to clean your bathroom; how mineral deposits build up; what causes certain stains to form; how to get rid of stains and deposits; how to prevent stains, deposits, and decreased functionality of your sink, toilet, and bathtub.

Unlike typical waxing, which strips your skin of vital moisture, causing inflamed, dry, and itchy skin as well as ingrown hairs, sugaring is a slightly gentler way of removing hair. Because it's all-natural, made generally of sugar, water, and lemon juice, it irritates the skin less because there are no artificial ingredients or harsh chemicals.

Unless you're a high-schooler building a nuclear fusion reactor, the hardest part of a science investigatory project often is coming up with a good idea. You want it to be cool yet feasible, novel but still useful.

Butter cream frosting isn’t only delicious but allows for great decorating possibilities. It can be a little difficult to create smooth surface to of the frosting if bubbles have created pock marks when laid, but as the video demonstrates you can use a smoothing tool to get that perfect service with a little work. Using a delivery bag and more colored butter cream you can create tropical flowers for a paradise cake.

After nearly two months of beta testing, Apple is finally pushing the iOS 15.6 software update to all iPhone users. While it's not as feature-rich as the iOS 15.5 or iOS 15.4 that came before it, there are still a few things you'll want to know about it.
The first Android update of the year is here. On Monday, Jan. 4, 2021, Google started pushing out the January security patch for the Pixel 3 and all newer Pixels, after having ended support for the Pixel 2 last month.

Good time-lapse videos capture cities, nature, and other long-running events in a way normal photos and videos simply can't. Your iPhone 12, 12 mini, 12 Pro, or 12 Pro Max can make time-lapses look even better, thanks to Night mode. But it isn't exactly intuitive or even clear on how to enable the feature since, unlike with Video mode, you won't find a Night mode icon to use.

Apple just released iOS 14.0.1 for iPhone today, Thursday, Sept. 24. The update features bug fixes for the News widget, default browser and mail apps, and more. In iOS 14, default apps suffer from a bug where iOS reverts back to Safari or Apple Mail when rebooting your iPhone, which defeats the purpose of the feature entirely.

Even if you're new to Android phones, chances are you've heard of the power of Android's customization, and that applies to the Samsung Galaxy Note 20 series as well. Your brand new Galaxy Note 20 or Note 20 Ultra's operating system is capable of modification beyond what's available in the basic Settings app — and it all starts with the hidden "Developer options" menu.

Wherever life takes you, knowing how to successfully manage both large-scale projects and teams will undoubtedly serve you well. Whether you're eyeing a promotion at work or looking to switch to an entirely different field, having the skills to innovate products, inspire people, and solve problems will make you stand out to your current and future employers.
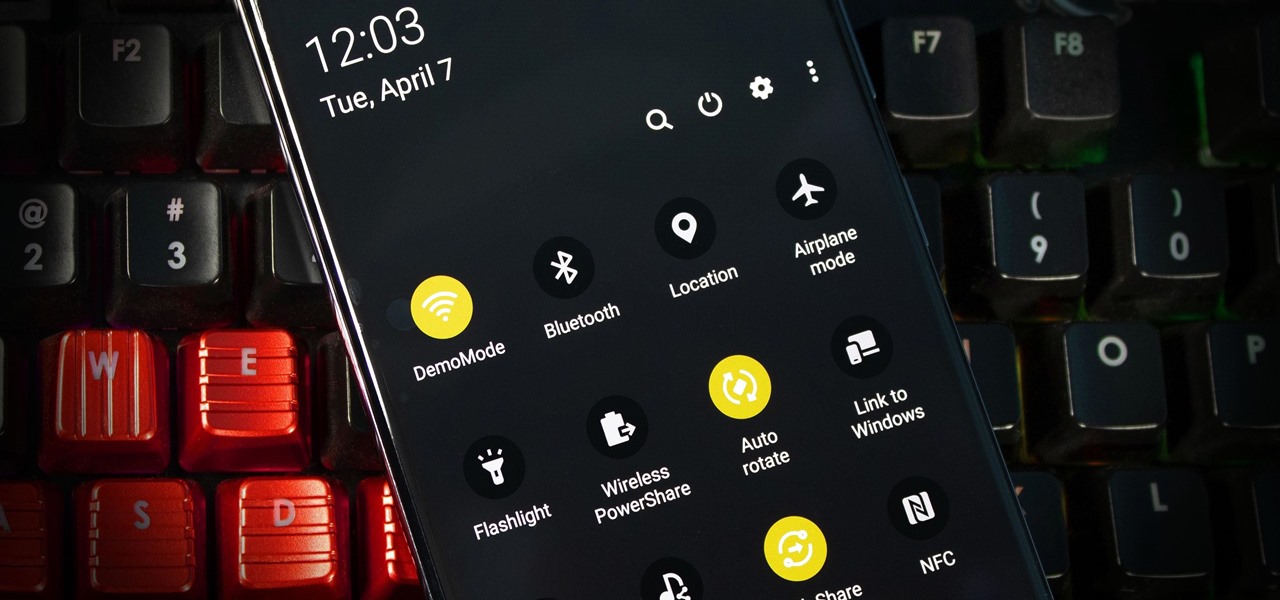
Every Galaxy S20 sold in the US — even the S20+ and S20 Ultra — simply can't be rooted. With the bootloader permanently locked, you miss out on the world of rooting and the customization it opens up, but modifications are still possible.

The response to the COVID-19 pandemic means that social distancing has become the new normal. It also means that more Americans are using video conferencing to connect with colleagues working from home or friends and family in quarantine because of the new coronavirus.

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

It seems like each day our phones become more integrated into our lives. School, work, shopping — so many tasks either require a phone or heavily benefit from one. But our phones are a double-edged sword that can easily distract us and harm our mental health as well.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.
TWRP won't be ready for the Pixel 4 and 4 XL until months after release. But since you can already root with Magisk and tinker with the OS, you might find yourself in a situation where your phone won't boot, yet you don't have a custom recovery installed to fix it. Luckily, there's still a way around this.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

Indian startup Dimension NXG is launching augmented reality headsets into India's consumer market with a bold idea: focusing on immersive computing in education on the high-end. The plan is to give a new kind of AR headset to schoolchildren in remote Indian villages, starting from class 5 (age 10) until graduation.
The Galaxy Note 10+ is the pinnacle of Android hardware. You won't find many phones with a better combination of specs and design. But you may not love the software. Even with One UI on board, some users still want a more "stock" feel.

Action games encompass a wide array of categories, ranging from racing games that pit you against players the world over for track domination, to endless runners that push you to set ever higher scores, and RPGs that let you embark on adventures in fantasy worlds. With such a huge selection of titles to look through, it's all too easy to overlook a game you might otherwise like.
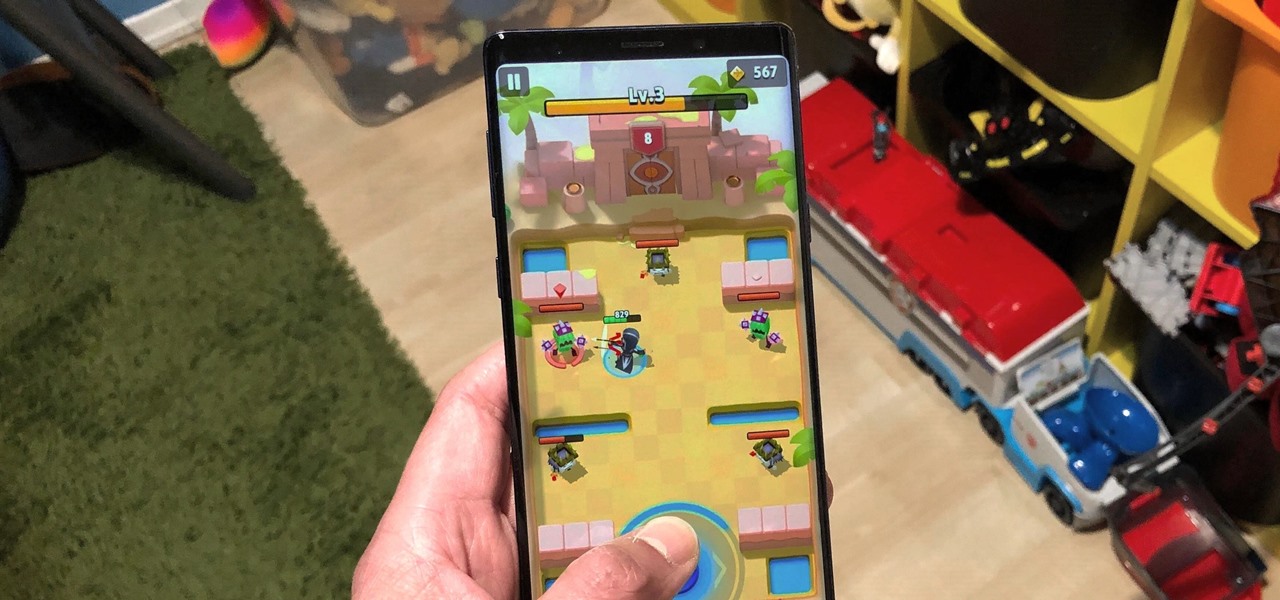
When it comes to shooting games, battle royale titles like PUBG and Fortnite have come to dominate the scene, leaving other sub-genres like top-down and third-person shooters living in the shadows. They're far from irrelevant, though, as evidenced by all the great games released just in 2019 alone.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.
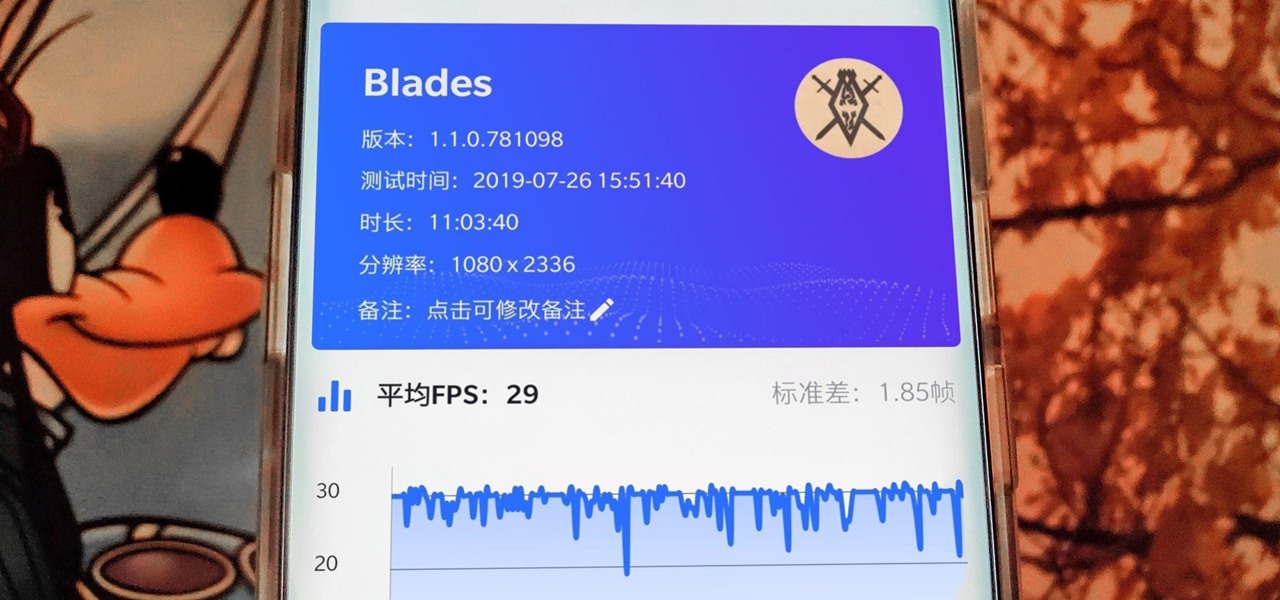
When you're gaming on your Android phone, does it sometimes feel "slow" and you can't figure out why? That means a drop in performance, which is when the frame rate dips, causing some noticeable stutters and lag. There's not really a way to know what's wrong unless you made the game yourself. But on the bright side, you can check any game's FPS with a simple tool.

Well before Magisk was in our lives, the Xposed framework was where all the mods and magic happened. Magisk was built on a similar concept with the ability to customize your system via modules. We can thank Xposed for where we are today in terms of root-related mods, but it's not done just yet — it's still very much alive and kicking after all these years.
The idea of squeezing your phone might have sounded a bit out there when it was new, but it's now a hallmark feature on Pixel devices. As useful as it is for summoning the Google Assistant, however, it certainly would be nice to be able pick and choose what action is triggered by squeezing the phone. Well, now you can.

Fireworks are the best part about the Fourth of July and other celebrations, but they can easily cause accidental injuries. It's both safer and more fun to set them off remotely, so we'll hack some standard fireworks with nichrome wire, a relay, and an Arduino to ignite remotely over Wi-Fi using any smartphone or computer.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

The first developer beta for iOS 13 is available to install on iPhone models, but the process for doing so may be a bumpy ride. Apple has not included configuration profiles for the developer beta yet, and many developers are having issues installing iOS 13 even with macOS 10.15 Catalina installed. Plus, since this is the first beta, there are a lot of problems with old and new features to work the kinks out of.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.
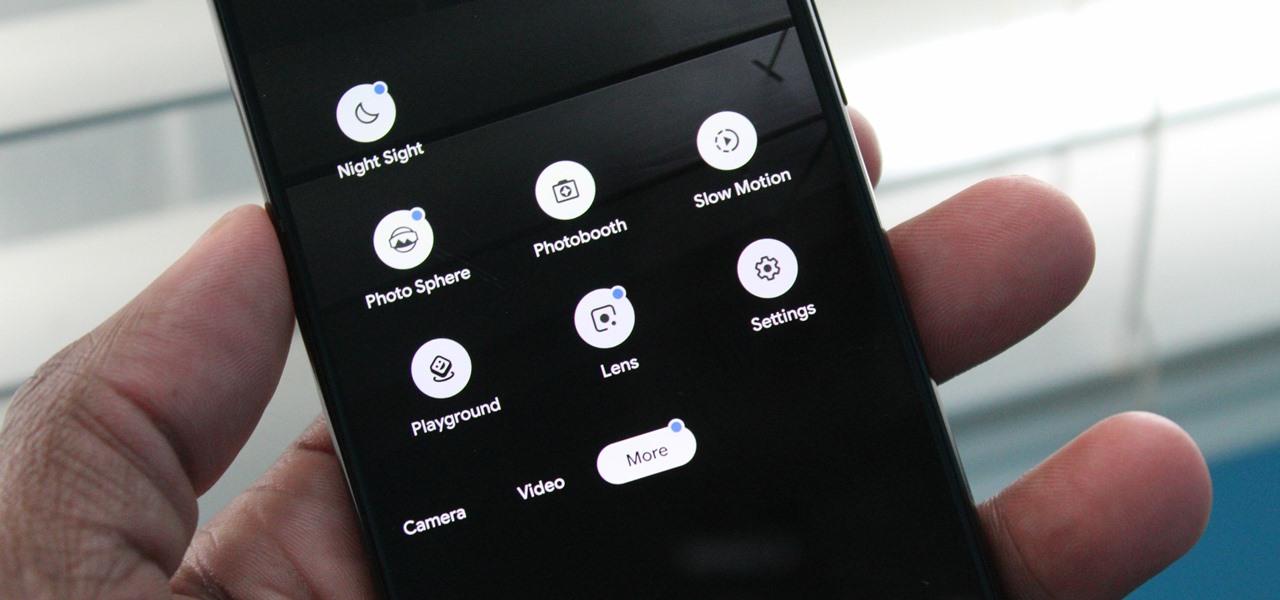
Nowadays, our phones are capable of just more than 30 fps video. Phones like the Galaxy S10 can shoot 4K at 60 fps, even on the front camera. Slow motion functionality has recently started to appear on more and more devices — but as you may have noticed, the quality of the feature differs from phone to phone.

After years of rumors and waiting, Samsung's first foldable smartphone is finally a reality. The phone itself is a bit wild, but with Samsung going so far out of their comfort zone with this one, there were some bumps in the road that caused a delayed release. The launch has been pushed back yet again, but when it does hit stores, it could end up being one of the most influential devices in years.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.