
News: Daring Man Carves Thrifty Engagement Ring Out of Meteorite
When most people say, "Damn, look at that rock," regarding an engagement ring, they're usually not referencing an actual rock—let alone a space rock.


When most people say, "Damn, look at that rock," regarding an engagement ring, they're usually not referencing an actual rock—let alone a space rock.

Switching your favorite facial cleanser isn't an easy choice. Since everyone's skin type can range from dry, to oily, to some complicated combination of both... well, let's just say that the conventional wisdom is to stick to what you know works.

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

You can beef up the security on your Mac all you want, but all the firewalls and antivirus apps in the world mean nothing when that can of soda tips over on your Macbook, destroying your laptop and all its data forever.

Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.

You're in the middle of cooking and a car alarm, cute kitten, or neighborhood brawl made you step away from the stove for a few minutes longer that you should have. It happens to almost every home cook. Most of the time, nothing dramatic happens, but every now and then, you end up with something like this:

I love my cast-iron skillet, but I never seasoned it properly. Instead, I took that sucker out of its packaging, wiped it down with a damp cloth to remove any factory dust, and started cooking with it ASAP. And you know what? It works just fine.

Fresh salsa is so tasty. Who can resist the robust mix of spices, the mouth-watering heat of jalapeños, and the juiciness of fresh tomatoes? Alas, I don't always make my own and have to get the pre-made stuff.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

Like humans, cats can suffer infections caused by ticks, and too often, the disease is fatal. Learn about tickborne diseases that affect cats and what you can do to protect Fluffy from an untimely demise.

Bitcoin continues to make chaotic waves in the finance industry, with one bitcoin currently worth about $1,250 as of this writing. What's great about bitcoin is that you don't need to shell out rent money to get in the game, because bitcoins can be bought in increments—basically, whatever you can afford.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

People tend to skip toasting nuts in recipes or before adding them to salads because it seems time-consuming and the margin for error is high. However, skipping this step is a big mistake. Why? Because when you skip toasting your nuts (go ahead, you can laugh, we're all doing it), you sacrifice flavor and texture. And not just a little flavor, but a lot. Alton Brown recommends wok-frying peanuts before making your own nut butter for this very reason.

Welcome back, my tenderfoot hackers! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers because you need to know that even when you delete files on your computer or on the victim's computer, a forensic investigator can usually recover them.

The iPod changed the music and electronics industries when it was first introduced way back in 2001. It is credited with ushering in the age of "connected devices," and has held a huge market share of around 70% for years. At the height of its popularity, the iPod made up almost 50% of Apple's revenue. Now that the smartphones and tablets we use every day have the ability to store and play music, the iPod's glory days are over. Nevertheless, there are millions of people who still use them, an...

These days, you can find a digital version of almost any form of entertainment. Being able to download or stream content is convenient for a lot of reasons—you can avoid going to the store and you never have to worry about late fees on rentals.

Caller ID is great to have, but there are certain situations where you don't want the person you're calling to have your number. People who sometimes use their personal phones for work may not want clients knowing where to reach them outside of work, and anytime you're dealing with Craigslist, it's better to be safe than sorry.

Apple officially released iOS 12 to everyone on Sept. 17, and while the new iPhone XR, XS, and XS Max will come with the software by default, you have a choice on whether or not to update your current iPhone model from iOS 11. There are a lot of tempting features to want to update right away, but there are also some compelling reasons to wait it out and install at a later time.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

If you live with pets, you know where their tongue has been, yet you let them kiss and lick you all they want without even thinking twice about it. I've heard people say that a dog's mouth is very clean, and that their saliva, delivered by licking, can help heal wounds, but is that really true?

Hello readers, and welcome to Null Byte. Before we start, for those of you who may not know me, my name is ghost_; I'm a relatively active member of our community and have been around for a while.

You can find chili peppers in practically every cuisine. From the sweet Italian variety to the spicy Thai bird's chili and the smoky Mexican chipotle, peppers are ubiquitous and universally loved. But if you find the range and scope of these little fireballs overwhelming, you're not alone.

Pumpkin carving and decorating is a favorite October pastime. After you've carved an amazing design or face into a pumpkin or two, you want to show it off through your window or set it out on your porch for the neighbors to see.

Brining is magic. All you have to do is make a mild saline solution, toss in your protein of choice, let it soak, and cook. You end up with incredibly tender, flavorful meat or tofu for very little effort. So why aren't more of us doing it?

Chances are that you've been using your microwave just to nuke leftovers, but they can do so much more than heat up last night's dinner—microwaves can help you peel garlic more quickly, get more juice out of lemons, disinfect your kitchen, dry out herbs, give beauty products new life, cause exciting explosions, and even arc weld.

All kinds of people pretend to be someone they're not on the internet, including scammers, people attempting to wind others up, hackers and web predators. Almost all of these people will leave bases uncovered and they're all easy to expose when you understand how to. Here are my favorite ways of finding out when somebody is lying quickly. Image Search
After poor sales of the Pixel 3 and Pixel 3 XL, Google needs to reinvigorate its Pixel lineup, devices it's been pushing heavily over the last couple years. On May 7, Google had the eyes and ears of the technology industry at its Google I/O keynote, making it the perfect time to announce new devices that would attract a different crowd of users. Meet the Pixel 3a and 3a XL.

A spare key is one of those things that never seems like a huge deal until you need it. If you've ever lost your keys, had them stolen, or locked yourself out of your house or car, you know how difficult and embarrassing it can be trying to get your door open.

Generative AI, or GenAI, is the hottest thing in tech at the moment, particularly for its ability to create content,p including essays, images, and videos. After Microsoft added its own GenAI tool to its Bing web search engine, Google is eager to follow suit, and you can be one of the first to try out Google's new GenAI search tool.
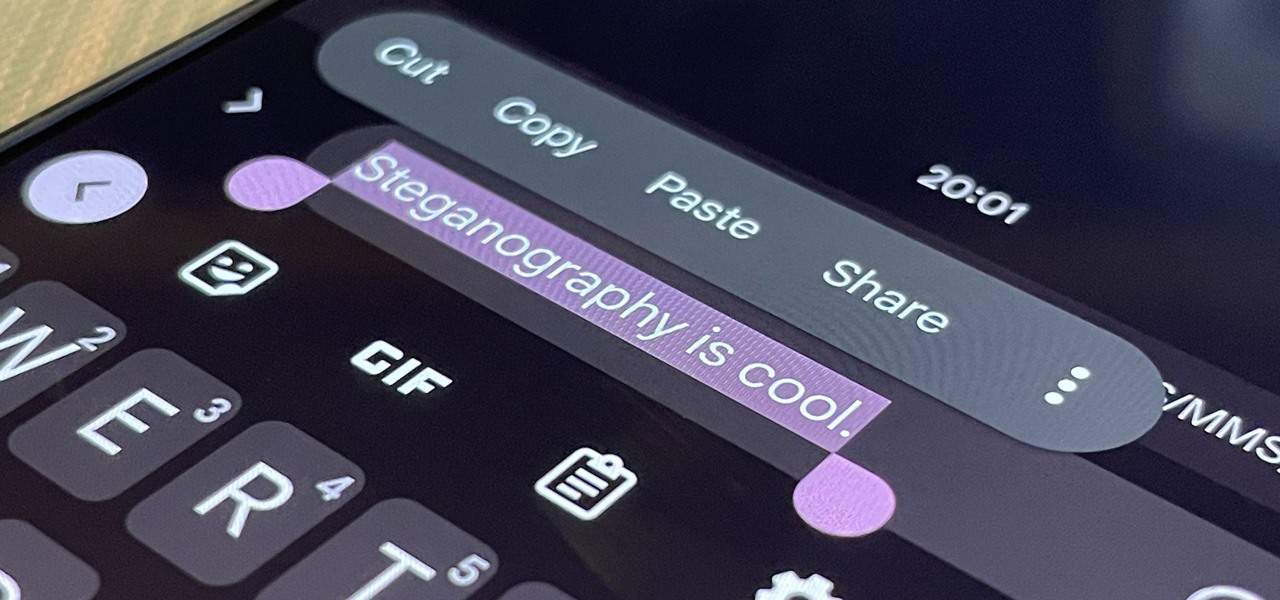
With a simple web-based tool, you can hide secret messages for family, friends, and fellow spies inside of plain text communications, and anyone that intercepts the messages will be none the wiser.
If you're in the market for a new smartphone, there are some pretty fantastic options for $400 or less. Both Apple and Google have unveiled budget smartphones with high-end specs in 2020, so you no longer have to suffer from subpar quality to save a few bucks. Low prices no longer mean cheap phones.
Android's settings menu is actually pretty daunting. There are options for nearly everything, so in the sea of various menus and submenus, it's easy to overlook important privacy and security settings. On Google's Pixel phones in particular, there are 20 such settings that you should double check.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

Nearly ten years since the first Galaxy Note and yet the Galaxy Note 20 still hasn't solved one of its biggest problems: bloatware. There are still over 20 redundant or unnecessary apps that are on this $1,000+ phone. But while it does require some advanced tools, it's still possible to remove them.

Apple Watch owners know there's a built-in way to remove water from the device's speaker. However, even though modern iPhones are IP67 and IP68 water resistant, there's no official way to deal with water-clogged speakers that can muffle audio and cause prolonged damage if not ejected. Older iPhone models have it even worse, but there are some easy things you can do to get that water out.