
How To: Find Out If Facebook Owes You Ten Bucks
For the most part, nobody makes money off of Facebook. Sure, some people make a living by updating pages for businesses and celebrities, but hardly anyone gets a dime from the site itself.


For the most part, nobody makes money off of Facebook. Sure, some people make a living by updating pages for businesses and celebrities, but hardly anyone gets a dime from the site itself.

With the ever-evolving technology that imbues photography, we are never short of fantastic awe-inspiring shots. Digital cameras can capture things that the naked eye only wishes it could see, like streaking lights, rapid movements, and faraway objects, and it's fairly easy to capture these things if you know the basics.
Fingers are very useful for many things in life—but fingers get dirty. With most smartphone and tablets using touchscreen technology, our fingers have become our greatest technological asset. But if you want to keep your phone or tablet from looking like this: Then you can try some of these awesome and easy DIY styluses.

Considering how often many of us fly on commercial airlines, the idea that a hacker could somehow interfere with the plane is a very scary thought. It doesn't help to learn that at Defcon, a researcher found that the Automatic Dependent Surveillance Broadcast (ADS-B), transmissions that planes use to communicate with airport towers are both unencrypted and unauthenticated.

Do you own an HP printer? If so, it may be vulnerable to malware attacks. Researchers at Columbia University discovered that 25% of Hewlett-Packard printers have significant vulnerabilities that put your printer in danger from hackers—even your home. With a budget of just $2,000, researchers Salvatore Stolfo and Ang Cui were able to hack into the printers using remote firmware to install malware, and in some cases even cause the printer to catch on fire. The main issue is with the printer's c...

There's a strange grey area for "guerrilla filmmaking" on YouTube. Generally, someone shooting a video needs to get permission from the people in it to show their faces. But on YouTube, that "rule" is more of a suggestion (and sometimes not even that).

A PA system, or public address system, is an electronic amplification system with a mixer, amplifier, loudspeakers, cables, mikes and cords. Learn how to properly set up a PA system with tips from a multimedia technology expert in this free technology video series.

Google Chrome is finally here, and everyone can benefit from a faster, streamlined web browser. This video will cover all the basic functions and features of the new Chrome we browser, so if you're thinking about switching, this is a must-see.

Everybody's hacking these days. Everybody wants to be a hacker, but that's what happens as technology becomes more and more accessible. Hacks are due to a lot of things. The main point is that you allow your user to access your WordPress Admin section or any section. So, may a problem could come with your user or writer. So, you must know about your login details and failed login details. Then only do you know about your user and what they are doing in your WordPress Admin section.

This is a video good for people who have problems with their Apple iPod. It uses simple steps in order to tell you how to successfully reset the iPod to its default state. Though it works primarily on the older models, viewers will learn which buttons on the machine allow you to completely reset the system in case of a system freeze or other problems. These easy to follow instructions will allow even people who have problems with technology to clean their system and get the iPod back to full ...
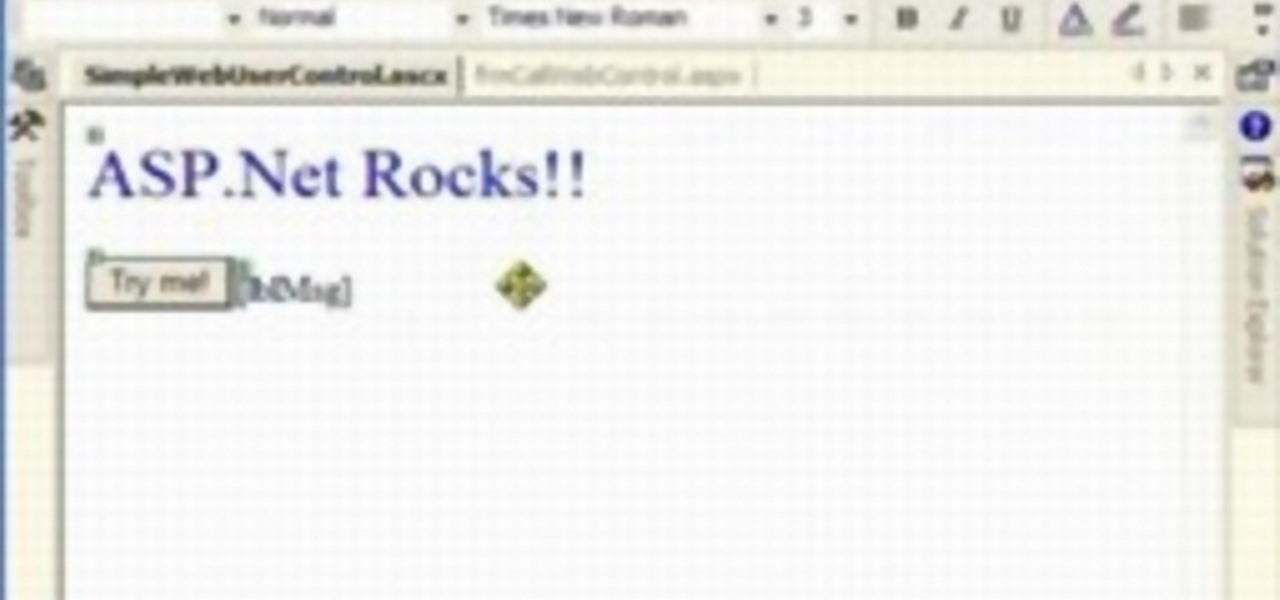
Microsoft ASP.NET is a free technology that allows programmers to create dynamic web applications. ASP.NET can be used to create anything from small, personal websites through to large, enterprise-class web applications. All you need to get started with ASP.NET is the free .NET Framework and the free Visual Web Developer. In this tutorial, you'll learn how to call your first web service in .NET. In just few minutes you'll be up and running with your own web service in .NET framework in ASP. F...
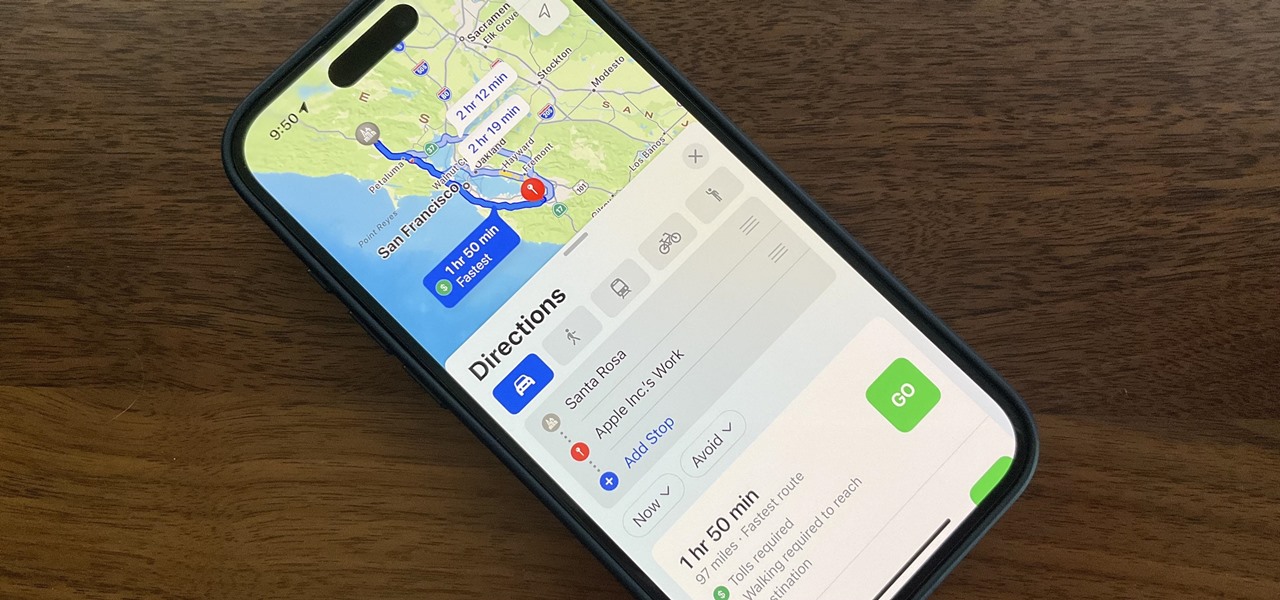
While Apple Maps didn't receive as huge of an update on iOS 17 as other apps such as Safari, Camera, Photos, Notes, Weather, and Messages, there are still some very important new features and changes you need to know about.

Your iPhone has a safety feature that makes it easier to call 911 in the U.S. and other emergency services abroad. Instead of fumbling with your iPhone's dialer, you can call someone for help in various ways — with or without your hands.

You see the status bar nearly everywhere on your iPhone, and it almost always looks the same. But you can use a few tricks to spice things up a bit — without jailbreaking your iPhone.

The US Department of Treasury isn't generally known for being on the very edge of technology innovations (see the current hubbub around crypto), instead usually waiting until certain tools have been battle-tested in the mainstream or enterprise sector.

Digital artist Beeple's $69 million NFT art auction at Christie's has a second act called Wenew, and includes attempting to open the digital art floodgates to mainstream collectors and artists alike by using physical goods.
Over the past decade, China tech giant Tencent has invested in several companies with varying roles in the augmented reality industry.

The Apple rumor mill never stops churning and when it comes to augmented reality smartglasses, the chatter has been particularly hot in recent months.

Web applications are ubiquitous in the modern online world, and knowing how to attack them is an increasingly valuable skill. But the key to a successful attack is good recon since it's easier to be focused and efficient with the more information you have. There are many fingerprinting tools available, such as httprint and WebTech, but there are even more that can aid us in reconnaissance.

The signal bars in your iPhone's status bar are great visual indicators for knowing how good your cellular reception is, but they're not very accurate. Instead of showing the actual amount of signal you're receiving, they just give you a general range, and you'll have no idea if three out of four bars is actually a good connection or not. But there is a trick to see the real numbers.

The average business person likely recognizes Epson for its printers or even its projectors, not the futuristic AR wearables.

Help me, George Clooney. You're my only hope. If that mash-up of cultural references doesn't make sense, it will momentarily.

When Treasury Wine Estates released 19 Crimes Snoop Cali Red this summer, named for its new partner in wine, rapper Snoop Dogg, it already came with the brand's signature AR-enhanced label.

No doubt, you've heard a lot about 5G lately. This might have you looking at your current 4G phone and lamenting your inability to connect to the faster network. But is 5G worth buying a new phone over, and should you buy one right now?

There's a serious issue with Google Fi's service for iPhone that prevents sending any MMS pictures via the Messages app. The problem doesn't affect all iPhone users on Google Fi, but if you're like me and keep getting that frustrating "Not Delivered" alert, there's a fix.

Samsung decided to jump into the foldable category early, announcing the Galaxy Fold in February 2019. After a major hiccup, Samsung released the phone four months later to praise. But Samsung's not finished with foldables, as the new Galaxy Z Flip is just on the horizon.

In a bold move, Samsung has decided to forgo the Galaxy S11 moniker and jump straight to the S20. Perhaps it's marketing for the new 20:9 aspect ratio and 120 Hz display, or maybe it's just the fact that it's releasing in 2020.
It's always a big deal when the company that makes Android releases a new phone. Google's Pixel series has made a name for itself in three short years behind its camera prowess, but now it's time to start competing with the major players. That said, Google should like how their Pixel 4 and 4 XL stack up against the iPhones and Galaxies of the world.

Apple has seemingly always made it a priority to show how much it cares about user security and privacy — enough that it has a page dedicated to it, proclaiming that "privacy is a fundamental human right." It's true that there are few issues more important than user privacy when it comes to technology, and Apple only makes things better in iOS 13.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

Motorola is a shell of its former self. In 2010, it had just released the Motorola Droid, a phone so popular it led to all Android phones being called "Droids" by non-techies. But there have been some rough years between then and now, and Motorola's latest "flagship" doesn't look like it will help get them off this path.

Apple's scheduled to show off the first look of iOS 13 at WWDC 2019 on June 3, but what will the new operating system hold for iPhone? Rumors suggest that many features initially planned for iOS 12 will show up in iOS 13, codenamed "Yukon," and dark mode will be the big ticket item this year.

You can almost detect the collective breath-holding of the augmented reality industry as it waits for Apple's inevitable entry. A new Apple wearable built with augmented reality technology is likely the device that will finally make the smartphone take a backseat.

You don't have to be a frequent flyer to know how indispensable navigation apps have become. Many of us rely on these apps for traveling from state to state and getting around in foreign cities, but even more of us count on these apps to beat rush hour traffic and find the quickest routes to school or work. So naturally, we all have our favorite mapping apps, but which one is truly the best?

You might think you need to buy a thousand dollar phone to get a great experience while streaming movies and TV shows from services like Netflix, Hulu, and YouTube, but that's just not true anymore. While phone prices keep rising and the midrange segment now ranges from $300–$500, there are still cost-effective options that come with top-notch displays and media features.

Over the years, Magic Leap's long-cultivated shroud of mystery led some onlookers to buy into the company's dream before even trying the device, while for others, the secrecy seems to have stoked the kind of resentment and overcorrecting critique usually reserved for the mighty Apple.

The hype train that left the station years ago has reached its first stop, and now we finally have access to the Magic Leap One, the device many have claimed would revolutionize the augmented reality space at launch. But is that really true?

There's actually more to the dialer screen on your OnePlus than meets the eye. Besides its obvious purpose of calling people, there's a vast array of secret codes that you can input to troubleshoot your device, in addition to revealing important information, making anonymous phone calls, and so much more.

After delaying its launch by four months, LG revealed its 2018 entry to the flagship market on Wednesday, May 2. After years of an underperforming mobile division, the LG G7 ThinQ is the first product since a shakeup within the division to get things back on track, and it brings a number of upgrades over its G6 predecessor.

As we aim for a wireless world, technology's reliance on cloud computing services is becoming more apparent every day. As 5G begins rolling out later this year and network communications become even faster and more reliable, so grows our dependency on the services offered in the cloud.