Okay, so that headline definitely got your attention, but what the hell do cats have to do with Android Nougat? Well, apparently, Google's on a far-out trip reminiscent of the post-India Beatles era, because this is actually a thing.
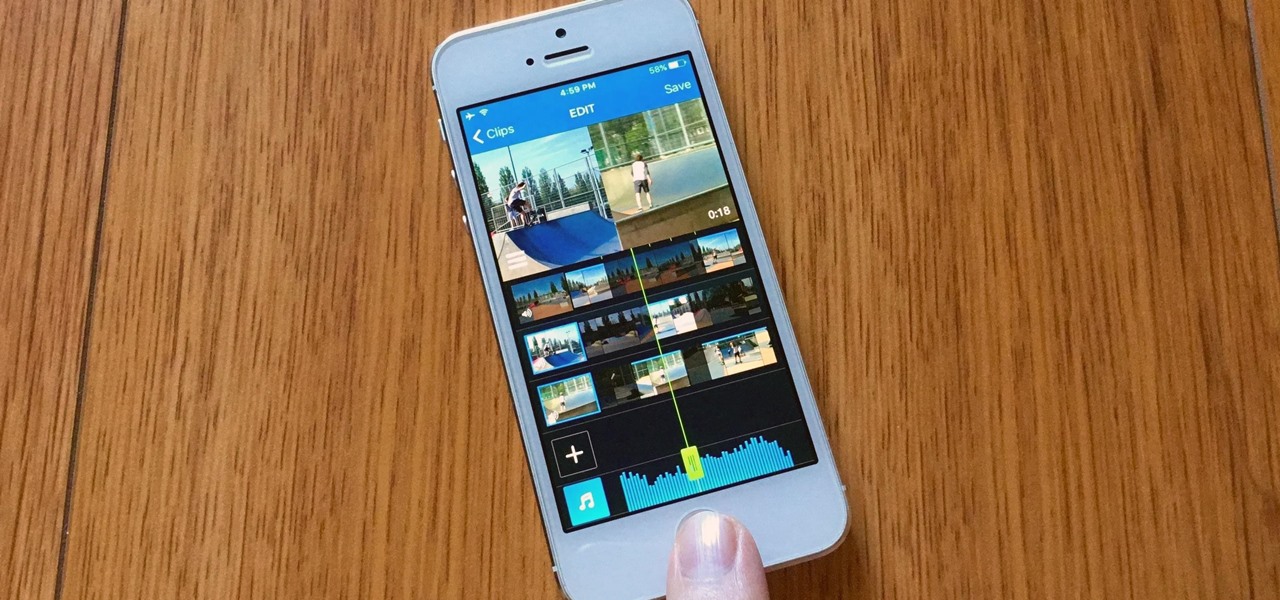
Let's say you're with friends at a sporting event, music festival, lounge, or some other fun venue, and you want to create a fun split-screen compilation from all the videos you took independently. It's not an easy task, because someone has to get all the video footage and then use a video-editing program that supports split screens. It's a daunting task most people will just skip.

We've seen these bean-filled blondies trending on social media for a while and, with some inspiration from The Kitchn, we finally decided to grab some chickpeas and give them a go.
With the next iPhone release around the corner, Apple is hard at work getting iOS 10 squared away. On Monday, July 18, they issued the third beta of iOS 10 to developers, which should be released within a few days to those using the iOS 10 public beta.

There are two kinds of people standing in the international section of the grocery store: the kind who love Pocky and the kind who don't yet know that they love Pocky because they've never had it.

Are there any benefits to watching a movie in a holographic mixed reality headset, or should you just stick with your TV? It's not as cut and dried as you might think. While TVs have some advantages, so does the virtual screen of a Microsoft HoloLens.

Soda bottle jello went viral when the popular YouTube channel AwesomeDisneyToys posted video directions for this revolutionary gelatin confection. I just had to try it out to see what the hype is all about.

It seems like Microsoft has finally come to the realization that their Windows Phone mobile operating system is probably never going to compete in today's smartphone market. Why do I say that, you ask? Because they've recently started to embrace the more popular platforms by releasing some quality iOS and Android apps.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

Near Field Communication, or NFC for short, is a feature that allows our smartphones to wirelessly communicate with other devices over a short distance while using almost no power at all. Think of it like a slimmed-down version of Wi-Fi or Bluetooth that can send a small burst of data two inches away without having any measurable impact on your battery life.

Whenever I go to Jamba Juice, I usually gravitate towards either the Matcha Green Tea or Caribbean Passion smoothies. But when I learned about their secret menu a few years ago, I felt like a little kid all over again—especially with flavors like Pink Gummy Bear and Orange Dream Machine.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

Some of the best images I've seen were shared via Snapchat, but once they're expired, they're gone forever, with no way to view them again unless I want to take a screenshot. But that will, of course, alert the sender.

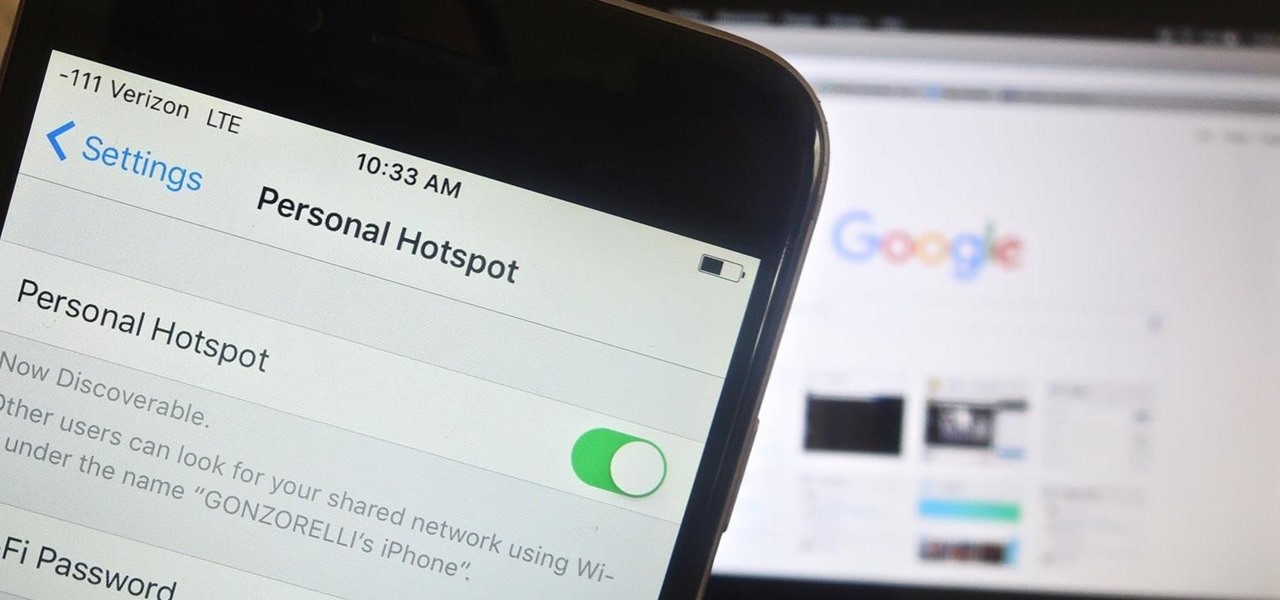
When you're in a bind and need an internet connection for your laptop, look no further than your iPhone. Using the Personal Hotspot feature in iOS, you can share your iPhone's internet connection with other devices by way of Wi-Fi, Bluetooth, or even USB.

The morning started out like most of them do: I was hungry, and it was time to chow down on some breakfast. However, this particular morning had me craving something besides the usual milk and cereal.

In this article, we will build a parallel password cracker using the techniques explained in the previous part. As SHA-512 is the digest function that Kali (and most modern Linux distributions) use to store our passwords, we will make a SHA-512 password cracker.

This is my first how-to for this site so feel free to let me know if I can somehow improve! Inspired by the great Jailbroken iDevice and Rooted Android PenTesting tutorials I decided to share how I use my Toshiba Chromebook 2 with Kali Sana.

This is my first tutorial and it is about accessing deep web for total beginner,sorry in advance if I make any mistake plz forgive me.

There's only one day that can top the aftermath of Easter and its copious amounts of leftover candy, and that is November — the day after Halloween. As you come down from your sugar rush and realize you now own more chocolate than your stomach can physically hold in one sitting ... fear not! Here are several ways to turn your Halloween chocolate into delicious snacks and desserts that you can enjoy at your leisure.

Your brain holds a lot of precious information and is capable of great feats. However, there's one quality that doesn't lie among its strengths—memory security. Yes, that's right, your brain can be hacked, and it doesn't take a psychologist to do it. Anyone with the right know-how can change your memories for their own personal benefit, and you can do so to others, too.

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.

Practically every smartphone comes with a built-in camera app, but these apps are generally created by the device's manufacturer. And let's face it, manufacturers are hardware companies first and foremost, so they don't always produce the best software.

Windows 10 marks a new era for Microsoft with the return of the Start menu, the demise of Internet Explorer, and the introduction of the remodeled Windows Store.

Apple's latest mobile operating system, iOS 9, may not be the huge overhaul that iOS 8 was, but that doesn't mean there aren't plenty of new features. In fact, there are a ton of subtle changes that you may not notice right away. Here's a rundown of all the coolest new features you need to know about on the new iOS 9 for iPad, iPhone, and iPod touch.

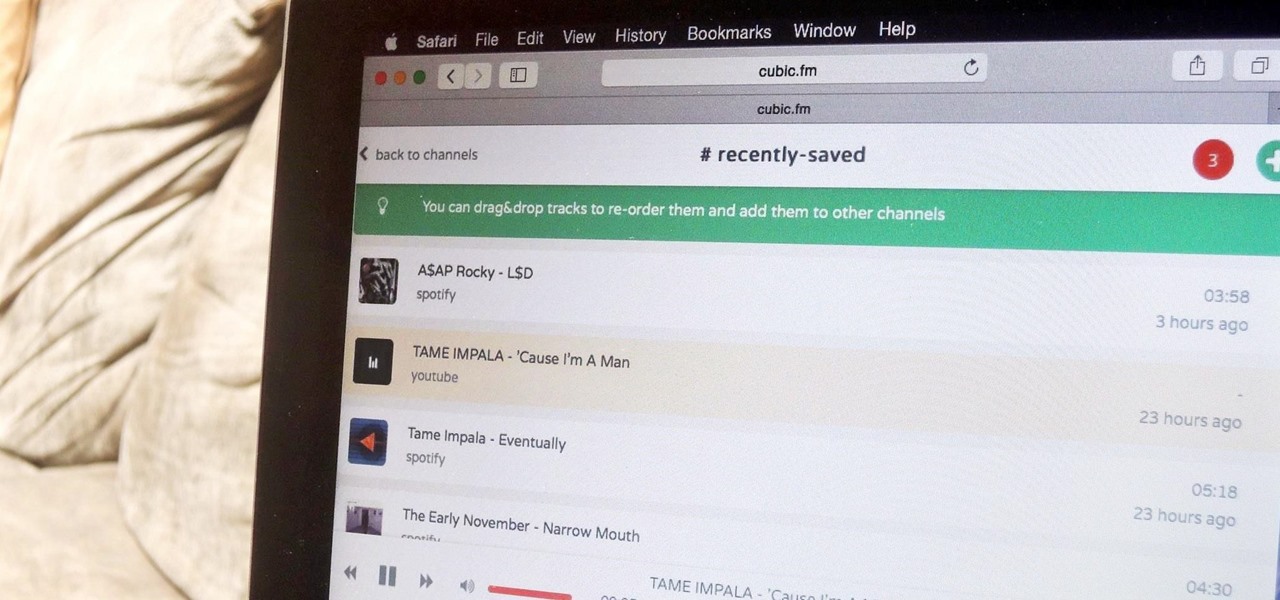
The options for finding random or specific music to listen to are vast. Spotify is excellent for streaming popular music and new releases, while SoundCloud provides a healthy dose of user-generated remixes and originals. And then there's YouTube for everything else.

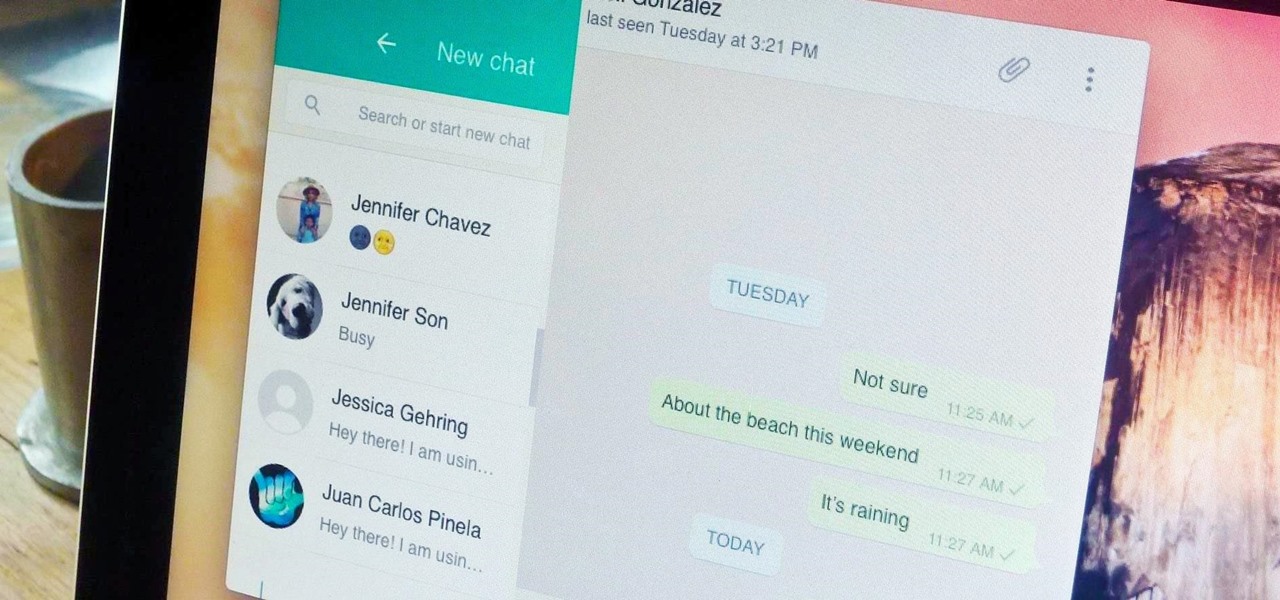
Boasting over 800 million users a month, WhatsApp has quickly become one of the most popular messaging services available today. Thanks to its low price, ease of use, lack of ads, cross-platform functionality, and great features, its popularity is well-deserved.

Google made a huge splash this year in their annual Google I/O with an awesome announcement regarding their Photos app. Although I was primarily interested in the details surrounding Android M, my ears instantly perked up when Google announced that their Photos app will now offer free, unlimited, high-quality storage.

Smartphones don't generally play nice with tripods, so videos taken with our handheld devices make terrible source material for time-lapse photography.

On the internet, everything is possible, even if it's not grounded in reality (check no further than anything The Onion publishes). Witty headlines combined with clever photo edits make even the most absurd topic seem like a serious news story. Some of these stories are so convincing that they even fool news organizations, such as the New York Times and even the official newspaper of the Chinese Communist Party. While some of us can tell when something sounds a bit off, others (like our paren...

Some people are of extremely secretive nature. They do not like sharing their personal events in their lives with anyone. Thus people around that person wont be able to figure out details on their life's personal matters. It is not like they want to hide some mysterious secrets from the world, but it is just their nature that they do not want others to know much about them or are too shy to share their feelings with others. Being secretive is neither good nor bad, it is just how they are.

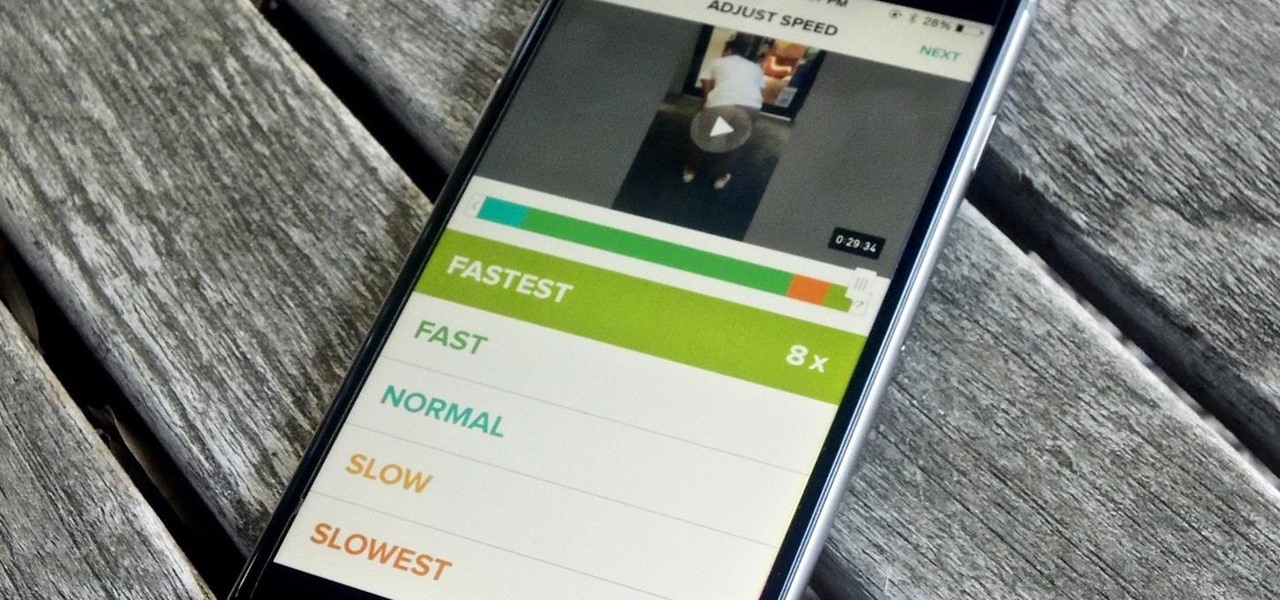
You can capture some pretty amazing videos using the slo-mo and time-lapse capabilities in the stock Camera app for iPhone 5s, 6, 6 Plus, or iPad Air 2, but there's no way to really combine them unless you shoot different videos and splice them together with a separate video editing app.

At any moment, you can open up Meerkat and start live-streaming a video from your smartphone, available for anyone to watch. Thanks to its popularity at SXSW and the backing of several big Hollywood players, the app just announced that it's receiving $14 million in funding.

When it comes to added features, no manufacturer out there can hold a candle to Samsung. Whether it's a remote control for all of your electronics, a heart rate and stress level monitor, or a seemingly-magical stylus, Galaxy devices always have as much functionality as possible packed in.

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

If you're an Android fan, you probably made your choice in mobile operating systems based on the insane level of customization options that Google's software offers. Don't like your home screen app? Simply replace it. Not a fan of a particular app's sharing system? No big deal, just share through a third-party app.

What type of person are you in group settings? Are you the social butterfly, eager to get to know everyone and interested in the people more than the setting? Or are you a wallflower, afraid to catch anyone's eye out of fear?

In the weeks before Apple officially released iOS 8, consumers were abuzz over rumors that a new feature would password-protect your photos and text messages from prying eyes. Unfortunately, this ended up being untrue, though we did cover some alternatives to protecting your important information using some built-in features and a third-party app. Now, there's a new iOS app that can do it all.

If you have ever attempted to mix and shape your own meatballs or burger patties, you may have endured bits of meat continuously and stubbornly sticking to your hands. This can make shaping more challenging than it should be.