In recent years, unwanted calls have become a top priority for the FCC. In 2016, analysts estimated that US customers received over 2.4 billion robocalls per month. As a result, the FCC has provided carriers new tools to combat this problem.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

I love cryptography. It is like a great gigantic puzzle for me to solve. However, it is more important than that. It is also how we keep secrets safe. Not just sorta safe either, but really safe.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

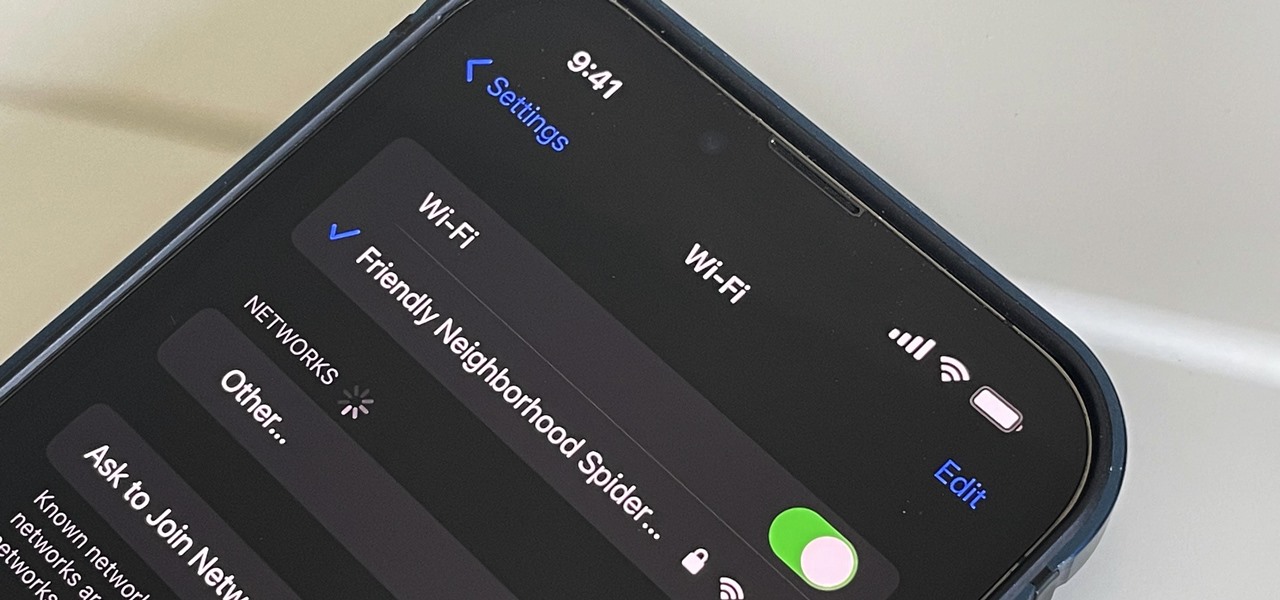
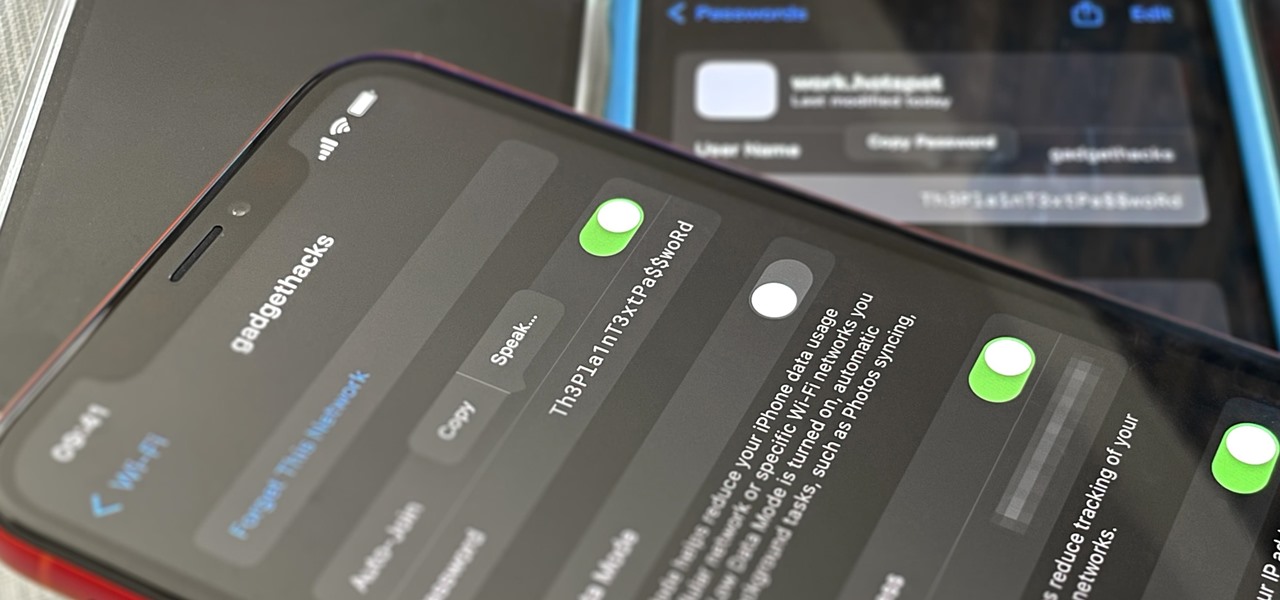
For years, Android has provided easy ways to view all the Wi-Fi networks you connected to in the past, and you can even see the saved passwords in plain text. With iOS 16, Apple finally gave us a similar way to view saved Wi-Fi hotspots, copy their passwords, and remove old ones without being near their access points.

If you have an iPhone running iOS 15 that's connected to Google Fi or another mobile virtual network operator, you may not be getting any photos or videos in Messages. That may be because you recently installed a software update, and you'll have to restore your cellular data network settings to get MMS working again.

Your iPhone goes with you pretty much everywhere you go, and unless you have unlimited data on your cellular plan, you've probably connected to dozens of Wi-Fi hotspots over the years. Wi-Fi passwords are saved to your iPhone so you can auto-connect to the router or personal hotspot again, but finding the plain text password for a network hasn't always been easy.

The wait wasn't so long this time. Apple released public beta 3 for iOS 13 on Thursday, July 18, just one day after the release of developer beta 4. For context, Apple took five days to seed public beta 2 after releasing dev beta 3, so it's a pleasant surprise that the latest public beta dropped so soon.

We're pumped for iOS 13 and all of the fresh features and changes that come with it. Developer beta 3 came with new features in the double digits, including AR eye contact in FaceTime and mouse cursor size customization. Developer beta 4, released today, has a few more additions and changes as well.

The third developer beta for iOS 13 has been out since July 3, and while devs have had fun exploring all the new features, those of us on the public beta have sat on the sidelines running the public version of dev beta 2. But we don't need to wait any longer, as Apple just released iOS 13 public beta 2 and all the goodies that come with it.

On July 3, Apple pushed out iOS 13 developer beta 3 for iPhone, and there's a lot found hidden within. A new FaceTime setting, more Arcade details, full-page scrolling screenshots everywhere, a noise cancellation option in the Control Center, and a new markup tool — and that's just a few of the new features.

There's no doubt iOS 13 has dominated the talk around the Apple community this month. Since the announcement and release of the first developer beta, we iPhone users have had a treasure trove of new features and changes to explore and discuss. Now the fun continues with iOS 13 dev beta 2. Who's ready to start up the conversation all over again?

The first developer beta for iOS 13 is available to install on iPhone models, but the process for doing so may be a bumpy ride. Apple has not included configuration profiles for the developer beta yet, and many developers are having issues installing iOS 13 even with macOS 10.15 Catalina installed. Plus, since this is the first beta, there are a lot of problems with old and new features to work the kinks out of.

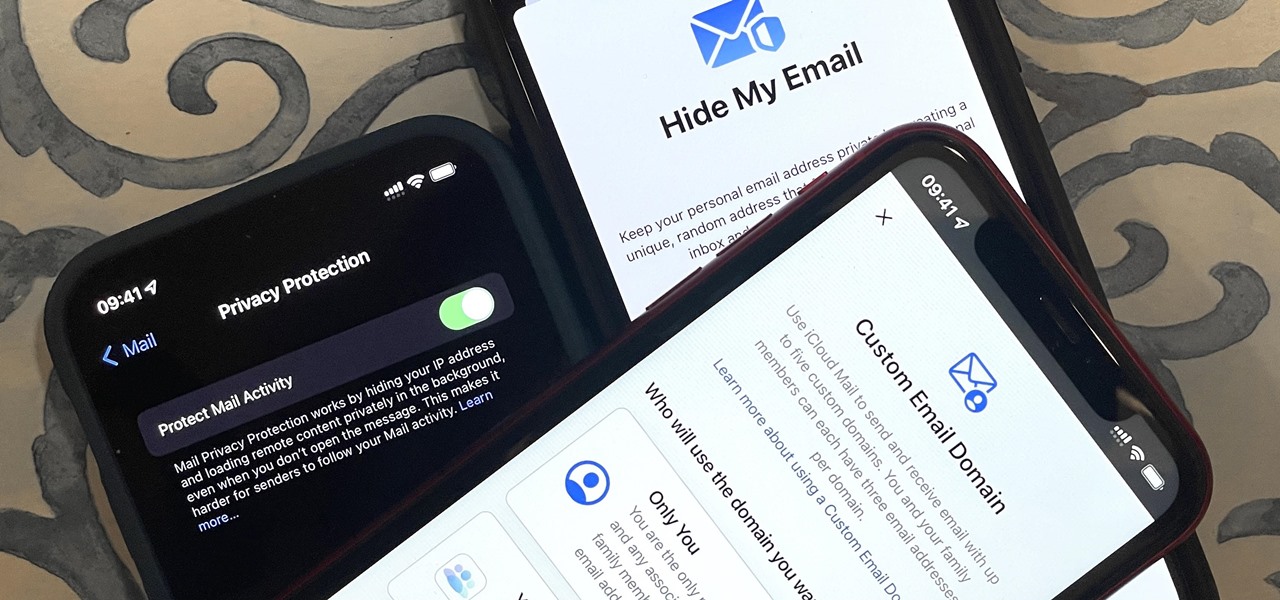
Privacy is a growing concern in the tech industry, but Apple has fallen behind many of its peers when it comes to email security. Fortunately, iOS 15 changes that. Your email address is the key to a vast amount of personal information, not to mention a stepping stone into your other online accounts, so it's great to see new features for iPhones that protect email accounts and their contents.

While Apple has been making strides in iPhone customization, it's still not up to par with what Android is and always has been. You can hide apps from the home screen now in iOS 14, but for everything that's still there, you can't add gaps between icons on the same page to segregate them where you want. However, some workarounds give that effect.

It can be very frustrating: You open your Messages app, send an iMessage, and then see that dreaded red exclamation point or horrible green SMS bubble. At this point, you may be curious whether it's just your iPhone or whether iMessage is broken for everyone, but how do you find out?
International Pet Travel: Taking Your Pet Animal to a Foreign Country If you are taking a pet to another country (permanently or for a visit), contact that country's consulate or embassy for information about any requirements that you must meet. A list of consulates can be found at Foreign Consular Offices in the United States

A degree in nursing from Kaplan University addresses the challenges and scenarios real nurses work through on a daily basis. Kaplan University’s Master of Science in Nursing (MSN program) is based on relevant material to help ensure our students are prepared for their careers. Our online nursing degrees are based on flexible coursework; students enrolled in the Kaplan University School of Nursing program are already nurses and there is no easier way to cater to the ever-changing schedule of a...

If getting Christmas presents ready ahead of time has never been your forte, be assured that it has never than easier than before to assemble together a last-minute Christmas gift for all your loved ones and favorite people (and maybe not-so-favorite people you are obligated to buy gifts for) on Christmas eve.

Kaplan University nursing alum Debra Eppley was already working in the nursing field when she started her RN-to-Bachelor of Science in Nursing completion program (RN-to-BSN program). Kaplan University’s flexibility and support offered her the opportunity to complete her degree online while continuing to work. Once she completed her Bachelor of Science Nursing online, she was able to make a career move that not only increased her salary, but also her level of job satisfaction.

People sometimes ask me about the IT industry here in the states. These folks are usually either trying to get into a certain field, or looking to switch or move into another one. Right now, you may currently be a Computer Science major that will be graduating shortly and are interested in the current state of IT security.

Before you start snapping away and submitting your photos, please take some time to read the official rules below!

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.