iPhones with Face ID all retail for at least $999, which many still believe is just too much for a smartphone. But that's okay, because Apple just introduced the iPhone 11 for roughly $700. It's not necessarily the best value, though, because the iPhone 11 already has some stiff competition in this price range.

With the defending champion Golden State Warriors and Drake's favorite team, the Toronto Raptors, set to face off in the NBA Finals starting Thursday, Snapchat has gifted hoops fans with a pair of augmented reality experiences.

With plans to compete with Niantic and other augmented reality game developers, game developer WarDucks has closed a $3.8 million funding round.
It was only a few years ago when the idea of a 5+ inch display on a smartphone was unreal. With most hovering around four inches at the time, a phone that big seemed impossible to hold. We've come a long way since then, but it appears another wave of large displays will soon hit us, and they are all at least six inches.

Now even muggles can see how they'd look chasing the Golden Snitch on a Nimbus 2000. That's because Snapchat is gifting Harry Potter fans with a 3D Bitmoji Lens that adorns their digital doppelgängers in the robes of the houses of Hogwarts.

The old school staple of many US homes with children, the remote control race track, has been given new life in augmented reality thanks to the Room Racer app for iPhones and iPads.

Location services company Mapbox has added new capabilities to its location-based gaming tool to fend off Google's challenge for the same mobile app category.

As if its users weren't already having enough fun with dancing hot dogs and face effects, Snapchat is upping the ante with a new kind of shared augmented reality content.

Less than a week after ARKit 1.5 became available to the public through the iOS 11.3 update, the App Store has its first app with AR features (Artsy) to leverage Apple's AR toolkit update.

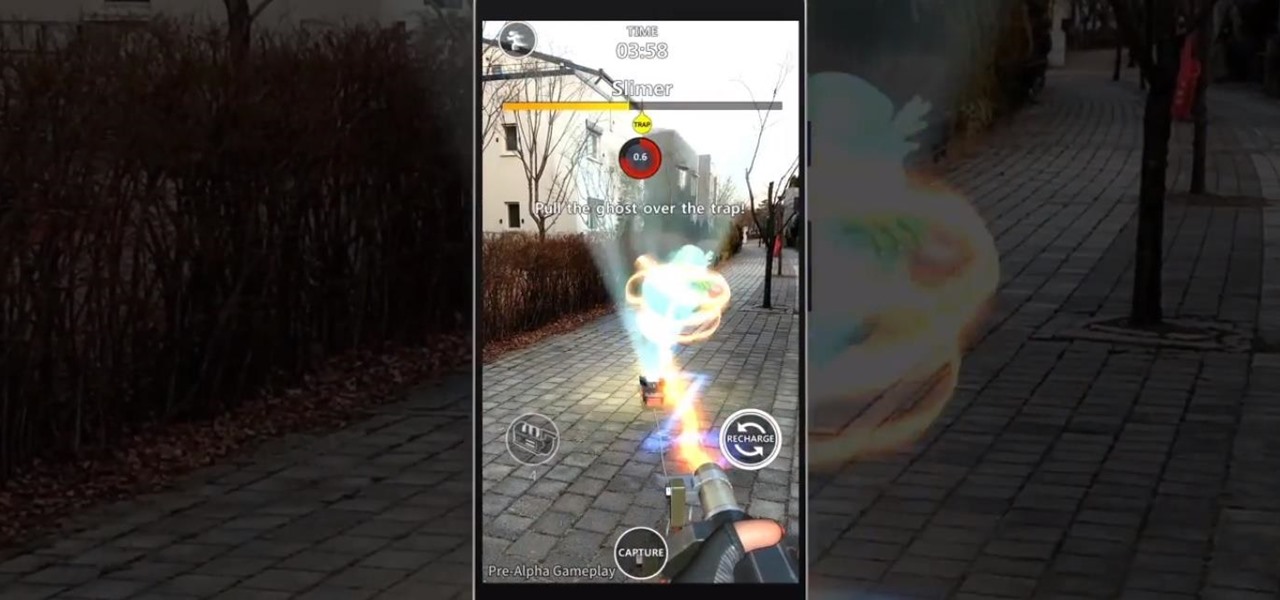
Sony's Ghost Corps, the caretaker of the Ghostbusters franchise, just released some pre-alpha gameplay footage from the upcoming Ghostbusters World location-based AR game to whet the appetites of would-be hunters of the paranormal.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

While augmented reality headset makers are faced with tackling numerous challenges before the category is truly ready for prime time, a start-up comprised of former Microsoft engineers may have nailed fast and precise tracking of hand gestures and full-body locomotion.

Soon, kids young and old aspiring to imitate Iron Man will only need to learn how to duplicate Tony Stark's snarky wit, because Hasbro will now supply the augmented reality helmet.

Enterprise augmented reality developer Atheer is bringing its AR solution for enterprise businesses to the HoloLens by way of a joint venture with fellow AR developer Design Interactive.

Lost among the latest laptops, smart assistants, VR headsets, and Motorola-branded gadgets that it brought to CES 2018, Lenovo has also introduced a new pair of augmented reality smartglasses.

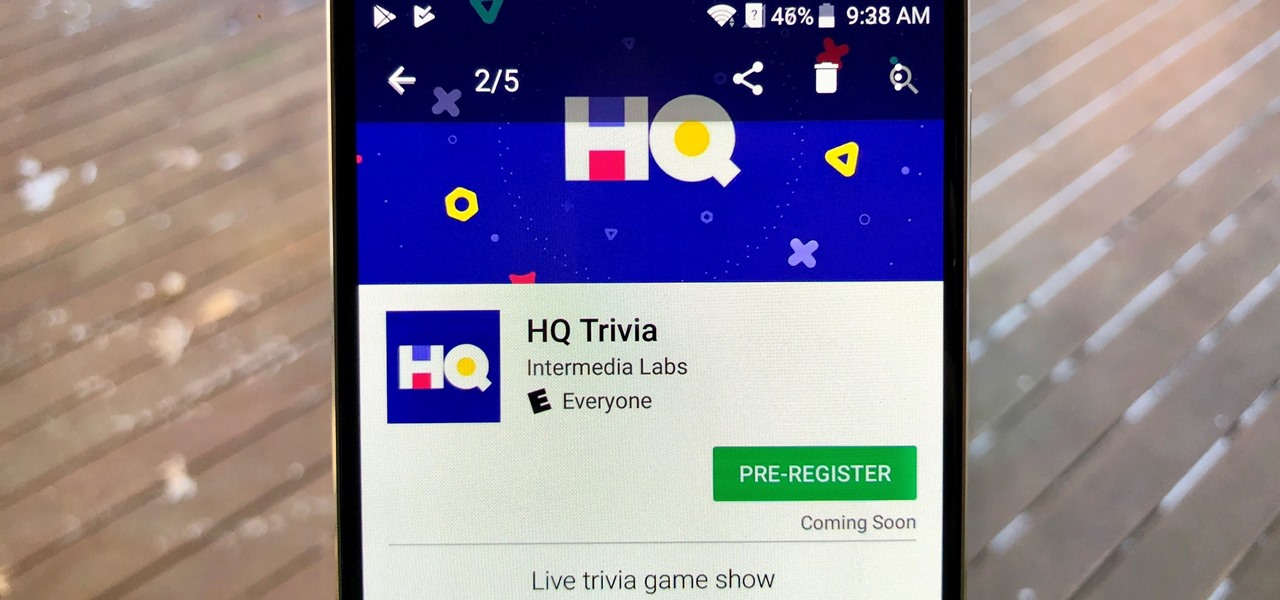
Attention Android users — the famously iPhone-only HQ Trivia is here! If you've been waiting for the worldwide sensation to come to your smartphone, now's your chance to dive into the excitement.

If you've been paying attention, you already know that ARKit can detect horizontal surfaces and estimate ambient light, but did you know that it can also help you improve your soccer game?

To create a destination for coffee connoisseurs, Starbucks has ordered up a venti cup of augmented reality to make the visit more interactive.

There are a lot of holiday tech deals starting to trickle out as Black Friday approaches. We've already rounded up some of the best deals for Android, iPhones, and headphones, but Google just dropped a big announcement for users of their Project Fi MVNO service. Now through December 17, you can earn yourself a free Moto X4 or Chromecast by referring your friends and family to Project Fi.

As it turns out, Apple did get AR hardware into its retail stores for the 2017 holiday shopping season, but it's not the headset we've been hearing rumors about for years; it's the MekaMon battle-bot.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

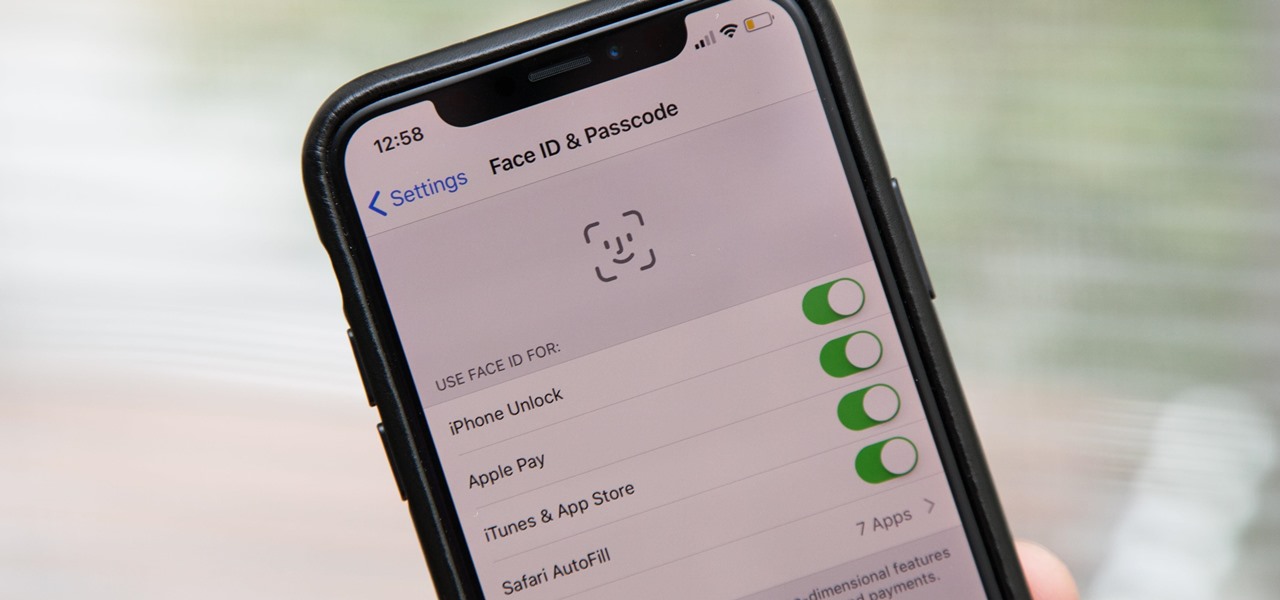
Aside from the second-generation iPhone SE, all new iPhone models since the iPhone X have had Face ID instead of Touch ID as the biometric authentication technology. While Touch ID can be touchy, Face ID is not without its own issues. If you can't get Face ID on your iPhone to recognize your face and unlock your iPhone, there are plenty of things you can try to get it working again.

Honeywell recently completed successful testing of virtual window technology that enabled drivers to maneuver an otherwise windowless combat vehicle on rough terrain at speeds exceeding 35 miles per hour.

The Pixel 2 is a solid upgrade when compared to the 2016 model, but we've reached a point where the latest generation of a smartphone is never leaps and bounds better than the last. It's hard to justify dropping nearly a grand on a phone when it doesn't improve your situation much — especially when a few software tweaks will give you most of the upgrade for free.

If you're a regular reader of this site, there's a good chance friends and family turn to you as their volunteer technical support staff.

As a long-distance runner off and on for the past, I absolutely detests hills. While there are many apps that can measure elevation and slope for certain routes, understanding spatial data on a line graph or even an elevation map can be difficult.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.

Over the weekend at IFA 2017 in Berlin, Huawei introduced the Kirin 970 processor, the first of its kind to include artificial intelligence baked into the chip.

Lenovo has been no stranger augmented reality, both in products for consumers and services for developers.

Artificial intelligence and augmented reality go together like spaghetti and meatballs, and Lenovo has some ideas on how to spice up the recipe.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

As you all journey along with me on my challenge to become some sort of Instagram expert, let me share with you one hack that is currently helping me out a lot. If you've ever wanted to put a line break in your posts, then keep on reading.

Earlier this month, Edgybees was the first game developer out of the gate with an augmented reality racing game for DJI drones called Drone Prix AR. Now, as the month closes, they are crossing the finish line with the first gaming app for Epson Moverio BT-300 Drone Edition smartglasses.

Universal Studios and Cinemark Theaters have enlisted mobile augmented reality game Seek to promote The Mummy, a reboot of the action-adventure film franchise starring summer movie mainstay Tom Cruise.

Sherif Marakby has returned to Ford as the VP of AVs & Electrification after a brief stint with Uber. Marakby's VP title will be effective June 12.

In a video released Tuesday, Microsoft arguably began to position the HoloLens and Windows Mixed Reality as the future of education. A smart tactic meant to coincide with their other education-related announcements made on the same day.

Microsoft announced yet another exciting partnership for HoloLens today — thyssenkrupp, an industrial engineering company best known for their elevators — continuing to prove how useful augmented reality is in the workplace.

All the news and rumors regarding the Galaxy S8 have finally coalesced and brought us to this moment, and it couldn't come soon enough. Samsung's flagships are making their official debut live on Wednesday, March 29. The stakes are especially high for the South Korean tech giant, following the Note7 debacle and the political scandals that plagued its highest echelons. Simply put, Samsung's fortunes are now riding on the Galaxy S8 and S8+. Will the Galaxy S8 and S8+ be the ultimate Android sma...

Australia is looking to the future and finding driverless cars and other autonomous vehicles to be a top priority. Spacial Source reports that the state government has put AU$10 million into their Future Mobility Land Fund "to drive local development of autonomous vehicle technology."

Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.