The creation of private browsing was brought upon by the backlash against ad tracking and other ways that sites and agencies take away users' privacy online. People were tired of getting spammed with ads for Vitamin C pills simply because they visited WebMD. Private browsing is now built into all of the major browsers and is used frequently. While private browsing is more infamously known as the "Porn Portal," and does prove to be a great way of keeping racy content out of the sight of others...

It's really no wonder why Christmas is the most popular and widely celebrated holiday of the year. Your whole family gets a chance to spend some much needed quality time together—and not just gorging on food like at Thanksgiving. But in all seriousness, that's not the reason at all... we're talking Christmas presents here.

If you have a lot of friends on Facebook, chances are that every day is at least one of their birthdays. If you took the time to individually post a message every time, you'd spend ALL of your time on Facebook, but you don't want to be a bad friend either. Let's face it, some people take this stuff personally.

For the vast majority of people, coffee is a must-have in the morning. It provides a stimulating effect that not only wakes you up, but sets your mood and attitude for the rest of the day. Personally, I wouldn't get anything done without coffee.
Fingers are very useful for many things in life—but fingers get dirty. With most smartphone and tablets using touchscreen technology, our fingers have become our greatest technological asset. But if you want to keep your phone or tablet from looking like this: Then you can try some of these awesome and easy DIY styluses.

Since the release of iOS 6, there has been a bit of an uproar over some of the new features (the new Apple Maps replacing Google Maps) and certainly over the glitches that always come attached with new operating systems. Downgrading Your iOS

Our server is primarily a fun server, so we don't often get huge, epic builds of amazingness. And yet that's exactly what we've got with Mgabrys's build, the Portland. Or, more specifically, Zeppelin City OR-2019 "Portland".

It used to be that you only had to worry about maids rummaging through your belongings in your locked hotel room. But now anyone with 50 bucks of hardware and some programming skills can hack their way in—as long as it's locked by keycard.

Thanks to everyone who submitted ideas in last month's Mad Science contest. The question called for your best idea for using Sugru, a temporarily malleable silicone modeling clay that self cures for a soft-touch permanent bond. It's a marvelous product for at-home quick fixes and for even making some cool DIY bumpers and grips for your electronics. William scoured through all of the comments and chose the two winners he felt best deserved a pack of Sugru.

Basically, the whole point of this video is to be really clear about how to get a Bear as a pet or any of the others available.

A pyramid is a three-dimensional figure with a polygonal base and a vertex. The base can be a triangle, quadrilateral, pentagon, hexagon, or other type of polygon.

SCRABBLE. To some it's just a game, but to me it's life or death. Well, not really, but it feels that way anyway. On a normal weekend, a game becomes much like Jon Thomas' "friendly game of death Scrabble."

The long wait is over — the best augmented reality device on the planet is finally available.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

One of the first steps in reconnaissance is determining the open ports on a system. Nmap is widely considered the undisputed king of port scanning, but certain situations call for different tools. Metasploit makes it easy to conduct port scanning from directly inside the framework, and we'll show you three types of port scans: TCP, SYN, and XMAS.

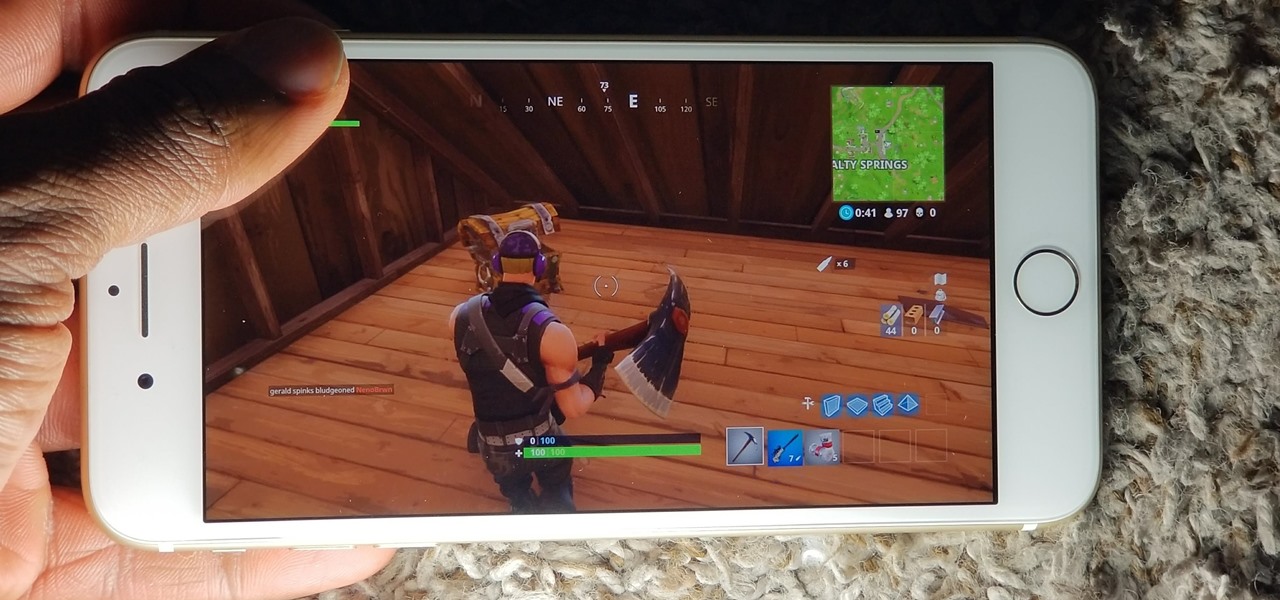
While playing Fortnite Battle Royale, you may have noticed a few players wearing different outfits or using fancy dance moves. These are cosmetic items that can only be obtained by unlocking them. However, unlocking items in Fortnite is a little different than many free-to-play games.

Tonic water, seltzer water, club soda, and mineral water: these 4 types of "bubbly water" are often, erroneously, used interchangeably. But the truth is that each possesses unique qualities and uses that set them apart from each other.

Welcome back, my amateur hackers! Many of you here are new to hacking. If so, I strongly recommend that each of you set up a "laboratory" to practice your hacks. Just like any discipline, you need to practice, practice, and practice some more before you take it out to the real world.

Welcome back, my novice hackers! The worst thing that can happen to any hacker is being detected by a security admin, the security technologies (IDS, firewall, etc.), or a forensic investigator.

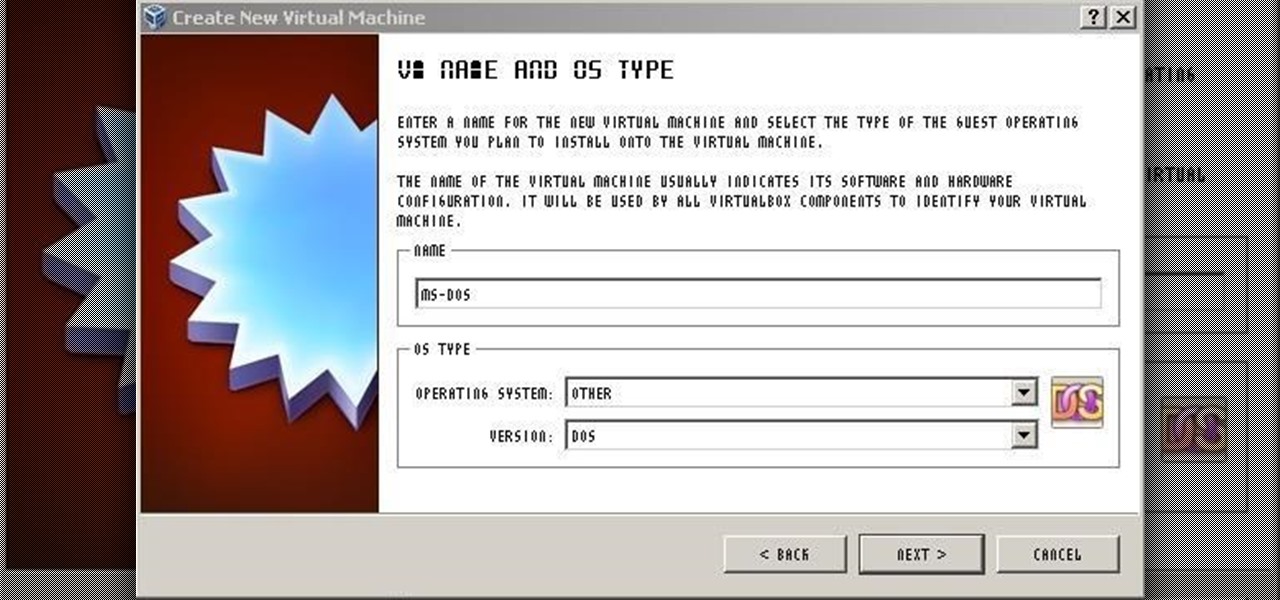
For those needing to replace old controller hardware on cutting mills, those into native retro gaming, or for those who want to see what all the fuss was about in the 1980's, or for those who just want a play with old but great technology, this tutorial shows you step-by-step processing getting the breakthrough desktop operating system running on the latest greatest hardware.

OSAGYEFO DR. KWAME NKRUMAH (1909-72) Founder and Father of the Nation Osagyefo Dr. Kwame Nkrumah, the first Prime Minister and President of Ghana, stands out not only among the Big Six but also among the greatest statesmen of history. It was he who canalized the discontent of the people of the Gold Coast Colony into the highly organized movement of protest against British rule, and within a relatively short period won political independence for Ghana on March 6, 1957. With Ghana independent, ...

In this tutorial, we learn how to get rid of stretch marks. When the stretch marks are still red, you still have a chance to get rid of them. If you purchase Palmer's cocoa butter, it helps cure stretch marks and get rid of them. Use this while you are pregnant and the stretch marks are still red. Use this on all parts of your body that have stretch marks. This is a little bit oily, so be careful you don't get it on your clothes. This is also great for your skin even if you don't have stretch...

In this video, we learn how to keep your backpack safe while riding on trains in Europe with Scott Dean. When you're on a long train ride, there are high chances your bag could get stolen while on a train. If you have to leave your bag in the back, make sure you use a bag lock on it. If you are able to keep it next to you, lock your bag onto a nearby rack or the shelf. You can find a number of bag locks at www.pac-safe.com, they make a ton of different locks and travel gear that's beneficial ...

Want to know someone's private website password? It's the biggest wanted hack: passwords, but how do you do it? Well, this tutorial shows you how to hack any password on any site with JavaScript. But this works best on public computers because multiple people log on to them, which means a better chance at unintentionally stored passwords. It helps to know a little bit about JavaScript before attempting this password hack.

If you've been struggling to get ChickHEN R2 installed and running on a PSP 3000, check out this video.

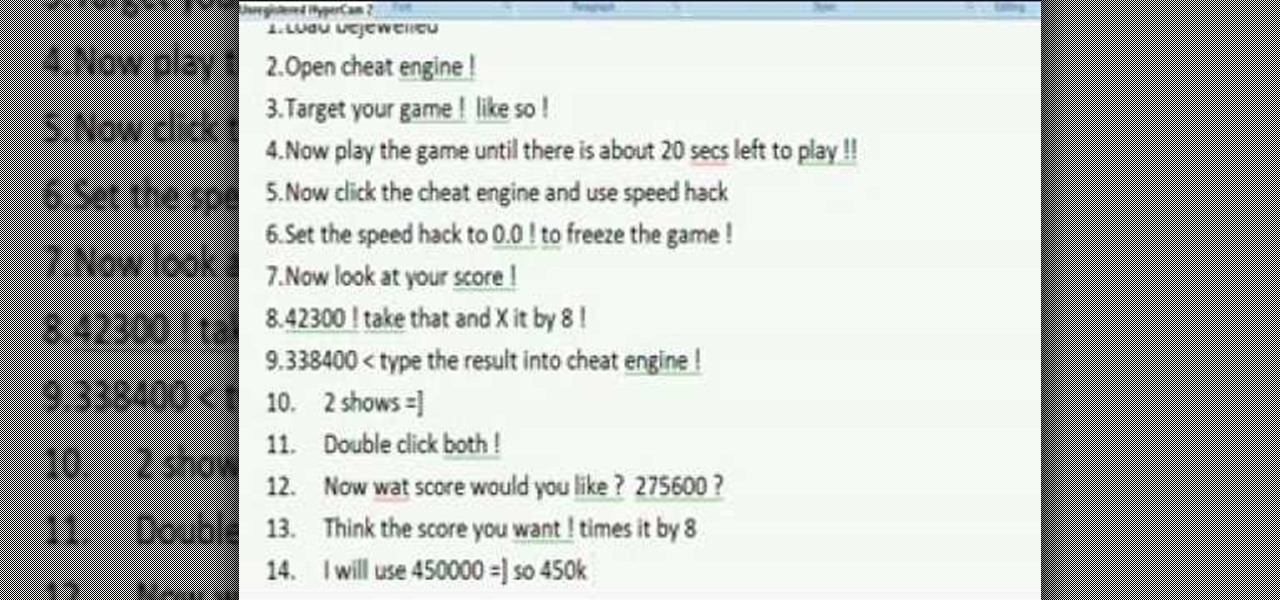
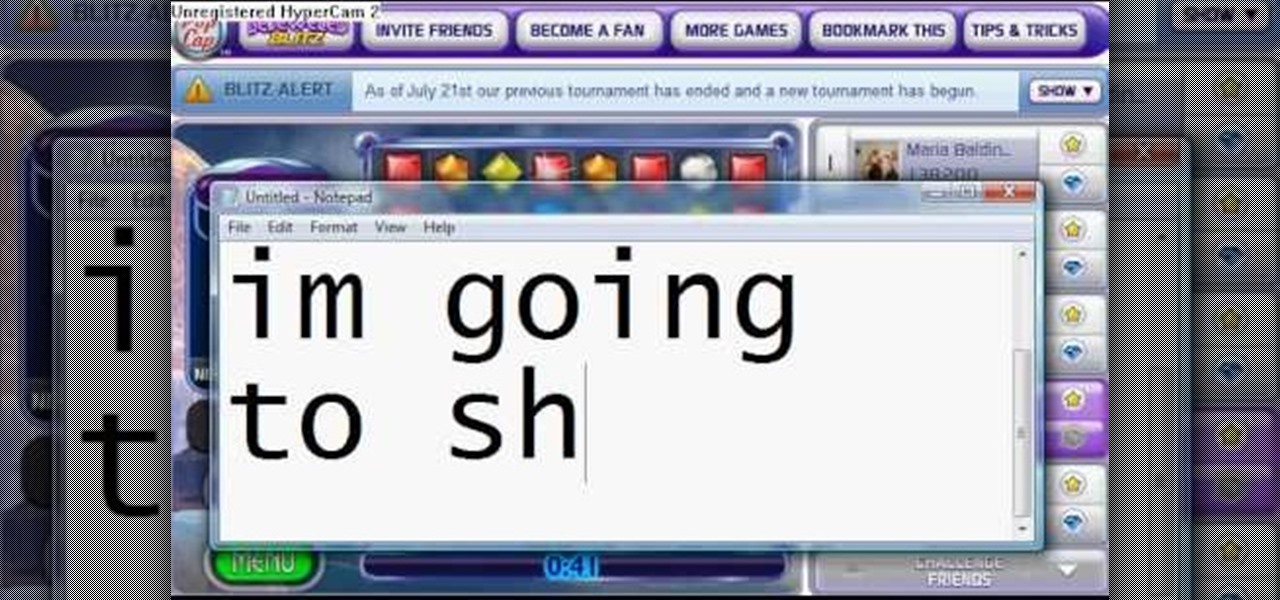
Bejeweled Blitz is a Facebook game. Learn how to hack Bejeweled Blitz with tricks, cheats, hacks. Watch this video tutorial to learn how to cheat on Bejeweled Blitz with CE (08/28/09).

Though apple skins are healthy, some recipes call for peeled apples. These apple peeling tips will show you how to remove the skin safely and efficiently. The first thing that you will need is a sharp paring knife. Now, before we continue, a quick safety tip: Whenever you are using a sharp knife you always want to cut with the blade facing away from you. If you are cutting with the blade toward yourself and you slip you will increase your chances of an accident.

You're trying to mow your lawn, but the engine on your pull-string push mower isn't turning over— why won't it power up? Well, if your lawn mower was stored outdoors for a large amount of time, chances are that the recoil has built up some corrosion or is simply sticking. This video will show you a very simple repair, where you only need to remove 2 or 3 screws to gain access to the mechanism, then grease with silicone spray.

This video shows you how to easily divide proper fractions. In the first step, you have to calculate how many times does the denominator fit into the numerator. You need to divide the numerator by the denominator. If the denominator does not fit into the numerator, you have to write 0, followed with a point, at the top of the calculation ("0."). Next, you add a 0 next to the numerator (multiply it by 10). Now, you have to calculate how many times does the denominator fit into the numerator ag...

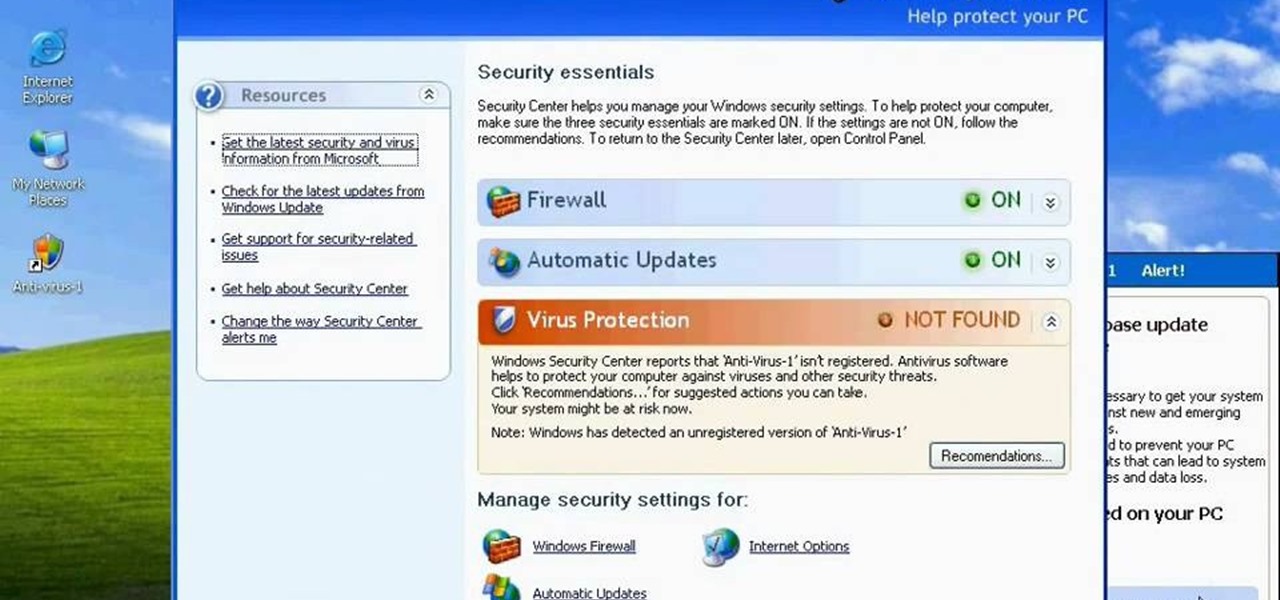
http://www.enigmasoftware.com/support... Having problems with your anti-virus software on Windows?

Bejeweled Blitz is a Facebook game. Learn how to hack Bejeweled Blitz with tricks, cheats, hacks. Watch this video tutorial to learn how to hack Bejeweled Blitz with Cheat Engine (07/25/09).

The big problem with sowing seeds indoors is that the light comes from one side and your seedlings will get 'drawn' (stretching towards the light). You can help to get healthy, sturdy seedlings and increase your chances of success if you make a simple box to reflect the light back to your plants. Use this with a propagator or just stand plants in pots in the box. You'll be amazed at how effective it is and it costs virtually nothing. All you need is a cardboard box, which is cut away on one s...

When an iPhone is lost or stolen, it's imperative to start tracking it via Find My as soon as possible, whether that's from a computer, tablet, or someone else's phone. However, if it's stolen, there's a good chance the thief or robber turns on Airplane Mode, blocking all communication with the iPhone. If this is a scary thought, you can prevent thieves from accessing Airplane Mode altogether.

Improving your experience online is getting easier every year. Browsing can be safe, easy, and boundary-less with the right VPN, and gaming online is working better than ever to connect and compete with other players.

Whatever industry you're in, there's a decent chance you've had to work with Excel — that number-crunching powerhouse that drives the accounting departments of countless corporations across the globe.

As the demand for realistic volumetric video for AR experiences begins to grow (along with the available facilities and services for capturing it), researchers at Google have figured out how to improve upon the format.