Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

On Wednesday, Scope AR, makers of Remote AR, the augmented reality video conference calling and remote assistance solution, announced that the app is finally available for HoloLens. Next Reality had a chance to talk with the founder and CEO/CTO of Scope AR, Scott Montgomerie, inside this new version of Remote AR.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

Verto Studio 3D is a 3D modeling package that has been in the works for a while now by Michael Farrell, the owner of Verto Studio LLC. Farrell has been working toward bridging the gap between XR 3D modeling and what we have become accustomed to with desktop 3D modeling packages like 3D Studio Max, Maya, and Blender.

Perhaps in tribute to the season premiere of Game of Thrones, Google Glass is demonstrating that what is dead may never die, as Alphabet's X (formerly Googlex) has revealed that the Enterprise Edition of the smart glasses are now available to businesses.

Dramatic new research may change the fate of the hundreds of people who wait for a kidney transplant every year. The study hinged on the ability to cure hepatitis C infections, a possibility that became a reality in 2014.

There have been a number of rumors about the iPhone 8 over the past couple of months, but the latest speculation about the device's dual FaceTime camera, that could take 3D selfies, has definitely grabbed our attention.

Usually, we think of vaccines as preventative, a shot we get to prevent the flu or some childhood disease like measles or mumps. But there are vaccines for other purposes, such as the ones studied by researchers from the Netherlands.

The words "leftover champagne" cause us to shudder slightly because, frankly, we are loathe to leave bubbly in the bottle. But in the event that we do have some left over, we put it to use in two egg-cellent ways: baked eggs and scrambled eggs.

I fry foods a lot. A LOT. We're talking wings by the dozen here. As a result, I go through a ton of frying oil. Now, frying oil isn't the most expensive ingredient out there, but it adds up when you fry regularly. Of course, I always reuse my oil, but straining it can be a huge mess and it gets to a certain point where enough is enough. It's time to start fresh.
Most of you lot would be aware what WPA/WPA2 is so I won't bang on about the encryption or protocols a great deal. In short WPA and WPA2 both have a maximum of 256bit encrypted with a maximum of 64 characters in the password. The encryption is really only 64bit but x 4 because of the way the authentication functions as a 4 way handshake.

Live wallpapers have dipped in popularity lately, with many users favoring a single, static image as their home screen background. But this is generally due to still photos offering a more sophisticated look, while traditional live wallpapers can sometimes seem a little less avant-garde.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

Hello friends. This is actually my first how to.

In the wake of Apple Music making its debut on Android devices, Google has finally released its highly anticipated YouTube Music app. With these two tech heavyweights throwing their hats into the ring, the streaming music world is about to get rocked.

Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.

Samsung has multiple built-in font styles to choose from in TouchWiz, but they're limited to just four types. While there are many font installers available on Google Play, they usually cost money and only replace some of the text on the device, not all of it, creating an inconsistent and erratic user interface.

Last time, I showed how to start putting together an AC arc welder from scavenged microwave parts, focusing on the transformer modifications. Now, I'll show you how to finish up your DIY stick welding machine by fixing up the electrical system and performing the finishing touches.

The advantages of rooting have been covered before, and with rooting comes flashing ROMs and mods to your device. The easiest method for flashing anything is to do it through recovery.

This software tutorial shows you how to create good renders from 3ds Max 8. It's one thing to create cool models in 3D Studio Max but if you can't get the lighting right and output a good render, then it's pretty useless. So watch this tutorial and get tips on creating a good render in 3ds Max 8.

This tutorial is for ultra beginners in .NET, it shows how to create a simple console output and simple form in VB.NET and C#. It is done through notepad and without any IDE.

This video will help you learn how to create an Explosive rainbow color swath in Photoshop. First open a new file, keep the width 845, height 475, RGB color mode and white background.

Download the P2 Step-by-Step Reference Guide. With Avid, editing footage captured with the Panasonic HVX200 camera is fast and easy. Avids system uses the same native file format as Panasonic P2 memory cards, so theres no need for any transcode, capture or file conversion process at all. You can edit directly and immediately from the P2 cards if you like or have Avid Media Composer create a rapid backup of your files. Nothing could be simpler or more immediate.

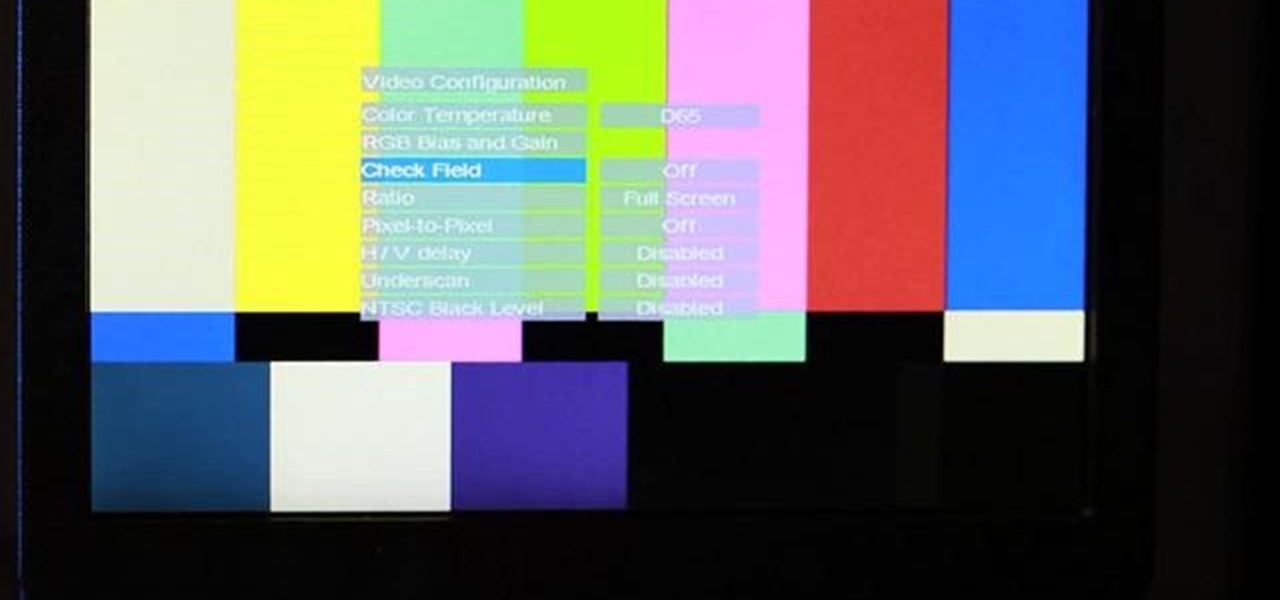
Check out this cinematography video tutorial on how to use calibrate an NTSC camera monitor, specifically a Marshall monitor.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

With the new iPhones coming out, many see the current mobile market as just another epic battle between Samsung and Apple. But let's not forget there are many other phones that run Android. And when you start to sift through the specs, one stands out as a competitive alternative to the iPhone XR, the LG G7 ThinQ.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

One of the primary marketing tactics used by Magic Leap in promoting the Magic Leap One was selling early adopters on the "magic" contained within the device. On Thursday, some of that magic was uncovered as the Magic Leap One was completely disassembled by repair engineers, revealing the delicate innards of the device and detailing how it delivers its augmented reality experiences.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

Termite poop and biofuels — what's the connection? New research into termites' intestinal comings and goings describes a process that may speed the development and lower the cost of fuels made from plant matter.

One of the only downsides to the Pixel XL is that Google's flagship phone does not have stereo speakers. But if Android's awesome development community has taught us anything over the years, it's that limitations like these can be bypassed with some creative software tinkering.

LG announced their latest high-end device on September 6 and its specs are pretty amazing: The new V20 sports three cameras, two displays, three microphones, four DACs for high-end sound, and it's all powered by a removable battery.

Welcome back! Sorry for the dry spell, but I've been rather busy setting up some side projects! If you remember back to a few training sessions ago, we covered basic file I/O. This is a very important step in making our scripts applicable in a real life scenario, and today we're going to further these concepts.