Have you ever wondered how to create an invisible folder? I mean an invisible folder, not a hidden folder. Nowadays, we are facing lots and lots of problems requiring us to keep our data safe and secure. There are millions of hackers all around the world that are trying to steal our information whenever we get onto the internet. Even some of our friends are trying to lay their hands on our personal and confidential information.

In this article I am going to show you how to quickly and easily make a professional looking trailer.

Inception may not be the lead contender for the 68th Golden Globe Awards, honoring the best movies and television from 2010, but Christopher Nolan's film still collected four nominations— Best Motion Picture, Best Director, Best Screenplay and Best Original Score.

So You're New to Counter Strike Source? So you're new to Counter Strike Source and you want to improve your gameplay? Great. You've come to the right place.

Put simply, SEO = more organic traffic. And more traffic is always good for a web page / website (unless of course, you are an underground drug-dealer selling drugs worldwide via a spooky website whose URLs are as search engine unfriendly as possible, so that no one accidentally discovers your page and informs the police, sending to heaven both an exciting career opportunity and the likely Al Capone's successor).

It's 1976. The hottest arcade game on the market is Blockade (or Blokade), an 8-bit maze game for 2 players. You and your opponent must move your characters around the screen in 90-degree angles, leaving a solid line behind them. Whoever runs into one of the solid lines first, loses. But soon you'll be able to play this fascinating game from the comfort of your own home—

The purpose of this stunt is to make a random fight between fast food characters and to see reactions between the managers as well as people.

So what's all the fuss about World of Warcraft? I guess the first question would be 'is there a fuss?' and the simple answer is Yes there is, very much so.

Hey wizards! As you have read in the gardening article I put up a few days ago, it requires the Test Realm! It's pretty easy to use the Test Realm, but there are a few very important limitations you have to pay attention to before using it. Many of you reading this may be pretty agravated. Here's how KingsIsle puts it:This Test Realm is available to Subscribers.

This tutorial shows you how to create a working piston in Maya. The key is to use constraints so that as one piece moves, the others move accordingly. Even if you don't want to make pistons, this is a good constraint example(something essential to creating skeletons and rigging characters). Create a working piston using Maya.

Mike and Rajo from the SubStream's "Film Lab" have some tips regarding pre-production and development for proper script format.

Do you find it hard to make your 3D characters walk naturally? In this 3-part video tutorial Larry Mitchell teaches the basics of true character animation showing how to animate a walk cycle in Poser 7. Check out how to create a good pose for your characters. Make sure to watch part 2 and be aware, some Poser knowledge will be helpful. Animate a walk cycle in Poser 7 - Part 1 of 3.

Animals and insects make great cartoon characters. So get ready to learn how to draw a worm that turns into a bookworm. All you need is paper, pencil, marker, colored chalks or colored pencils, and an eraser. Start by drawing a squiggly line. Come around and double the line, keeping an equal distance from the other. Draw a curved shape for a head at the end. Draw large circles for his eyes and connect them to give him glasses. Draw his pupils going all the way to the right. Add two small eyeb...

On June 23, 2003, Linden labs created a free client program known as Second Life. This program allows users, or residents, to interact with each other in a virtual world by using avatars. Thanks to this program, residents are able to explore, socialize, and create and trade virtual property, and services with each other. Second Life has become one of the most popular programs used by various age ranges from 16 to 60, but how do you enter this world and get your own avatar?

To create an elegant WordPress blog or website from scratch without being noticed that you're a complete beginner, you need that drive and pairs of eyes and ears. It may seem difficult at first but it can truly be fun and exciting.

Mark Schoennagel, senior 3D animator at Softimage|XSI, shows how to use the Generalized Attribute Transfer Operator (GATOR) in XSI to transfer UV coordinates and shape animations to and from completely different characters. Transfer UV coordinates and shape animations in XSI.

This video shows you how to use the InDesign Find/Change command. You learn how to search for characters and formats in text, and search for attributes and effects in objects, glyphs, and patterns. You also learn how to save a search to reuse later. Use the Find/Change command in InDesign.

In this Computers & Programming video tutorial you will learn how to encrypt a D-Link router with WEP password protection. First you connect to your wireless network. Open your browser and type in http://192.168.0.1. Type in your base station username and password and press OK. Under the SETUP tab, select WIRELESS SETTINGS, scroll down to 'Wireless Security Mode' and select 'Enable WEP Wireless Security'. Scroll down to WEP. Under WEP Encryption pull down menu select 128Bit. Now create a pass...

Are you an aspiring clown? Or maybe an aspiring magician? Or just simply want to entertain the neighborhood kids? This video will shows you how to make a balloon airplane with a driver in the cockpit and all. A perfect alternative to those typical balloon characters you get at every party. Now, you too can make balloon plane. Make a quick and easy balloon airplane.

This After Effects tutorial shows you how to create a voyage tracking animation. This is the same thing you see when you're on an airplane and the screen shows you how far you've come and how far you have left to go. It's also a popular techinique used in movies to show where characters are travelling and the pasage of time. This is a very simple tutorial that's great for After Effects beginners. Create a voyage tracking animation in After Effects.

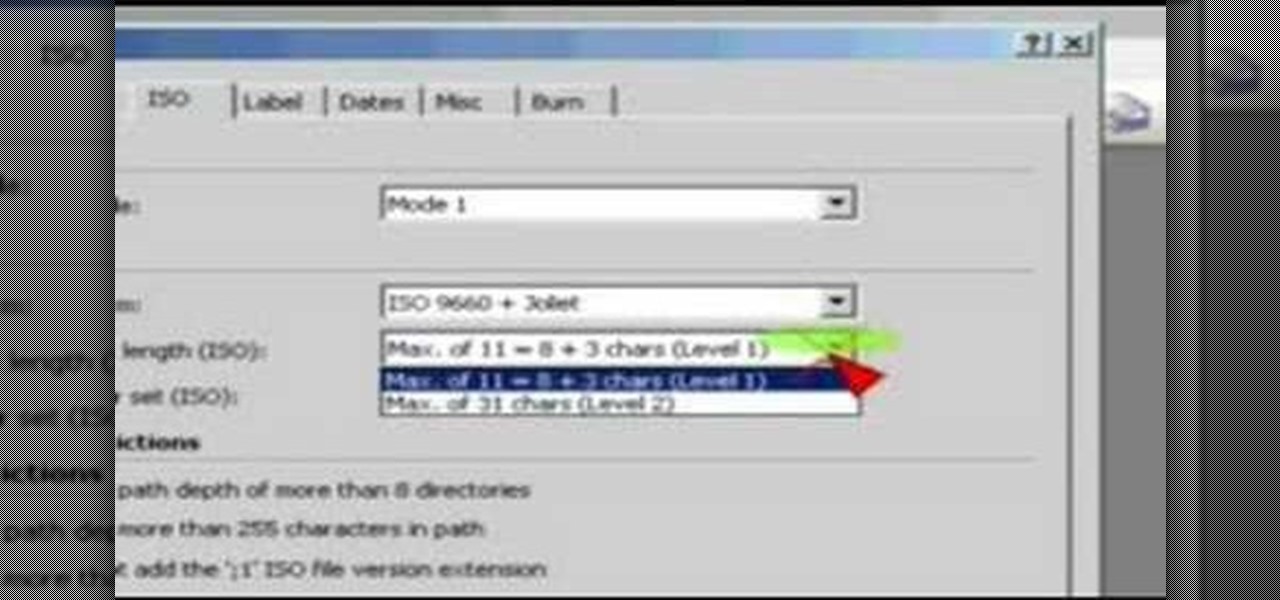
This video uses Nero Burning ROM. First you must open Nero. Then choose Burning ROM. Scroll down to the CD-ROM(BOOT) icon. Click it. From there you choose you ISO image. To do this just browse and navigate to the correct directory where your ISO image is stored. From there be sure to set the emulations to No Emulations and change your available sectors to 4. Next change to the ISO tab. Be sure that it is set to run ISO+Juliet and that the max characters are set for Level 1. Next choose the La...

Story, Characters, and Structure Note:

Dead Island (PC, PS3, 360) had the worst launch of any game in recent memory. The wrong version of the game was released on PC, matchmaking was down for three days on PC, saves were deleted without notice making people start from scratch, and the Feminist Whore (a file found describing one of the character's skills) fiasco. The game just wasn't ready for release.

These impressions are coming from a person completely new to the Final Fantasy Online world. Never played FF 11 or the FF 14 Beta. This game is not friendly to new people. The account creation is a Kafka like experience in things that don't make sense. For the game itself, the beginning tutorial is awful and does not really teach you the basics of combat. Here is a small breakdown of my opinions, with the good points first so that they don't get overshadowed by the negatives.

Following the first part in this series on advanced cracking techniques, we are going to go over how we can intelligently crack passwords using the old-fashioned bruteforce method. These unique cracking techniques aren't widely used, because most crackers are Script Kiddies who have no idea what the concepts are behind cracking passwords, thus, word won't get around too quickly.

Finished Act 1 (3 total) of Red Dead Redemption and it was disappointing. The act is divided into five important people who you have to do missions for in order to progress the story. Around five missions per person on average. Only Bonnie and the Marshall's story missions felt tied to the storyline. Dickens, Seth, and Irish's missions felt like they added nothing but padding to the game. Add that nothing that you do in the game affects the world around and it's like you never existed in the ...

Localizing a game is a task many do not fully understand. Not only do localizers have to translate the games they work on into a different language, but they have to translate it into a different culture as well. Oftentimes art assets, plot elements, and menu systems are changed to suit regional sensitivities. Japanese media tends to have their common drunkard characters removed or censored in American versions, for example.

Shadows of the Dammed (360/PS3) is a polarizing game. It's not shy of being crass and crude. Go ahead and judge the game by the following examples (click to enlarge):

Have an old-school tabula recta lying around? No? Then just print out the chart below. Nothing ensures better password security than this centuries-old cipher technique. Here's how it works, via Wikipedia:

Love this Rubik's Cube stamp with movable type Chinese characters by Shaun Chung. Chung laser-etched the characters from wood, and then adhered them to a regular Rubik's Cube to create verses from a traditional Chinese text.

In this article, I'll show you how to create a simplistic AES python based text encryptor. You'll need python 2.7 and PyCrypto (found here). The code is fairly simple, a user enters an encryption key (which basically tells the program how to scramble the text, using an algorithm), then the text to be encrypted. The program takes the key and text and inputs it into the "cryptograph" or code-based algorithm from PyCrypto. PyCrypto can use 16, 24, or 36 character encryption keys, but for the sak...

Kick Ass Review Part 3: Conclusions [Spoiler Alert! Plot points are discussed from the movie and comic in this section!]

Lifehacker posts an article on the art of cracking weak passwords, courtesy of Internet standards expert, CEO of web company iFusion Labs, and blogger John Pozadzides. Pozadzides certainly knows a thing or two about password logic. (Note: this information is not intended to hack into accounts, but rather to protect you from using weak passwords).
The Power of One is one of those books that I really should have read years ago. I’ve certainly meant to read it for a long time so this was a satisfying title to cross off my list. It’s stunning that this was Bryce Courtenay’s first novel. I look forward to reading his others because if this is where he started, he’s a talented writer.

In this article, I'll be exploring the basics of Python, i.e. variables, input and output. You'll need Python (2.7+), a computer, and some free time.

As per Alex's request, I am posting about generating word-lists in Python. However, this is my FIRST attempt with Python, so please provide me with critiques and any and all comments. I really want to know what you think as there was a little bump here and there seeing as I am transitioning from C#.

Well, we have had a pretty basic story structure in the previous couple of blogs. However, for the third act there is considerable leeway on how this story can play out. You can turn a story like this into a tragedy or comedy. Remember the line from the film Stranger Than Fiction "Tragedy, you die. Comedy you get hitched." Well in the Action/Adventure story, almost anything goes. For instance, GUY does not have to die, but CHICK could perish tragically. However, avoid cliches like someone jum...

People smile in this movie. This is a genius breakthrough Another day, another remake. Another safe choice during apparently rocky times - this wintry economic climate, don't you know - and we're off and watching Joe Carnahan's big-screen version of the A-Team. In 2010.

Introduction I will not go into some time-waster of a story about how I came to build this app. It was a prerequisite in a bigger project I am still tinkering with from time to time.