The day I picked up my iPhone 5S was a very exciting day. I had taken all the correct steps in backing up my old device so that after a quick restore-from-backup (which turned into half an hour), I was right at home on the new hardware.
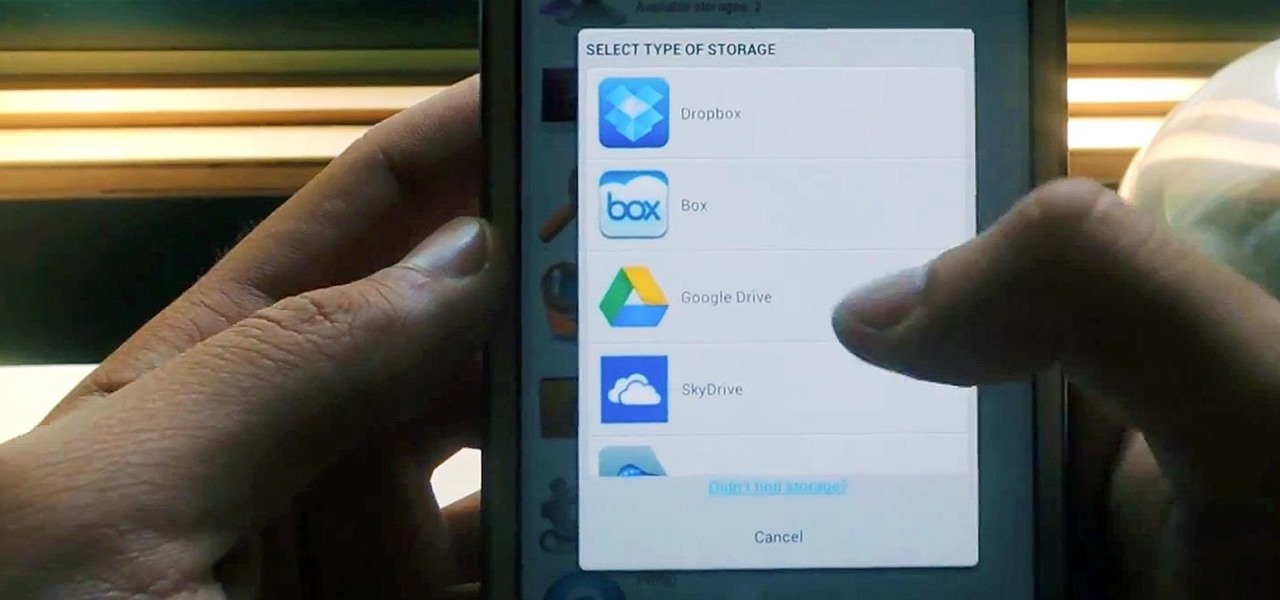
Cloud storage looks pretty good compared to the heavy restrictions that hard drives and other types of external memory carry. The cloud is not only limitless in what it can hold, but it can also easily be accessed from any device that has Internet—your smartphone, work computer, personal laptop, tablet, and more. While accessing a specific cloud storage system like Dropbox or Google Drive may be easy on your Samsung Galaxy Note 2, managing all of them individually can not only get confusing, ...

In a previous softModder tutorial, we installed CyanogenMod on our HTC Ones to approximate the look and feel of the Google Edition HTC One. Unfortunately, this rendered Beats and HTC's ImageChip (among other things) useless.

Managing multiple applications on an iPhone is as simple as double-tapping the home button, long pressing the app you want to close, and tapping on the minus sign in the red circle. If you're using Mac OS X, the dock at the bottom of the home screen plays the role of the multitasking bar on the iPhone, just not as sleek or simple.

For most people, the battery life on a DSLR is more than sufficient, but if you want to do a really long exposure or time-lapse, one charge might not last long enough to get the shot you want. You can always connect it to an extension cord to charge while you shoot, but that can be really annoying to work around.

One of the best things about the Samsung Galaxy S3 is the ability to modify the device in countless ways, as with any other Android device.

Needing to use your device in bright or low lighting can require an adjustment in the phone's built-in brightness settings. However, there are times when those default settings just don't do the trick.

There are tons of ways to make simple DIY lamps out of things you have lying around at home. If you've got an empty container, (even an orange or tuna can), there's probably a way to upcycle it into a lamp of some sort, and they can come in handy if you ever lose power.

One of the main reasons why the Samsung Galaxy S III has dethroned Apple's iPhone 4S as the best-selling smartphone in the world is due to Android's open-source operating system. The vast spectrum of customization that comes with Android has become one of its focal points, allowing n00bs and programmers alike to build and destroy. The open-source OS has allowed rooting and modified ROMs to flourish within Android community. The only problem with this is that rooting and installing your own RO...

There's a broken canister of mutant ooze leaking down into the sewers! But don't worry because this sticky slime is non-toxic, and it's so easy to make, a three-year-old can do it!

Whether you're making a poster, drawing a logo or designing a website, the font you use can make a huge difference in any visual design, and the ones available in most word processors can get pretty boring. There are thousands of sites online where you can download free fonts, and even a few that let you design your own. Here are some of the best.

There's a strange grey area for "guerrilla filmmaking" on YouTube. Generally, someone shooting a video needs to get permission from the people in it to show their faces. But on YouTube, that "rule" is more of a suggestion (and sometimes not even that).

In the following video, I demonstrate how to create a device capable of charging the body of anyone who wears it with static electricity, allowing a powerful shock to be discharged into anything that is touched. This grants the wearer the ability to do some pretty amazing things, some of which are shown in the first segment of the video.

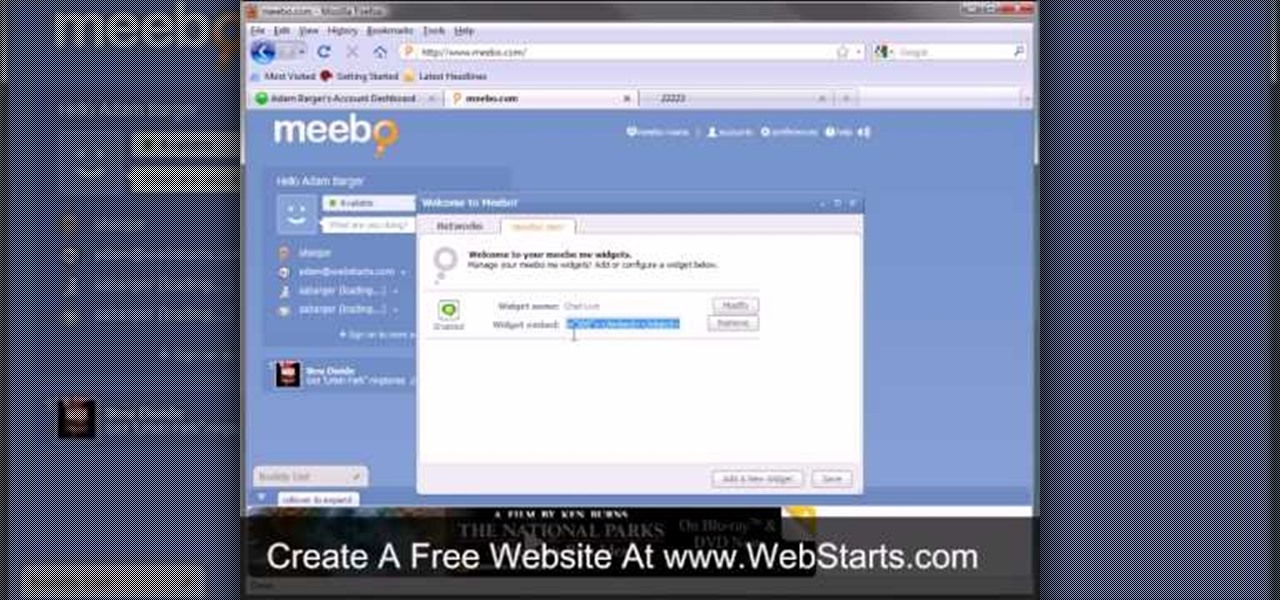
In this video, we learn how to add live chat to your website. First, go to the website Meebo and log into your account. Now, you will see the interface and the accounts you have associated with this client. There are several chat engines you can use through this interface. Once you have added all your chat clients, you can participate in the chats that occur on your website just from this one website. In order to add this widget to your website, go to preferences and choose the option for wid...

Already an impressive gaming machine, the Xbox 360 can be modified to play a wider variety of games. This instructional video demonstrates how to flash your Xbox 360 to play downloadable games from the Internet. This method only works on the Hitachi v0078fk drive and will void your warranty, but think of how cool it would be to pull this off.

This is a clever video that teaches you how to make a craft that is both fun to make, and also a useful item to have around the house- soap! This is from Living a Simple Life Blog and details how to make soap, just like the pioneers. To do this, you will need some equipment, a scale, scent, colorant, lard, lye, coconut oil, plastic containers to hold ingredients while you weigh them, a stainless steel pot, safety glasses, rubber gloves, a miter box, scraper, curing racks, a funnel and a plast...

If you've got a bobby pin and pair of handcuffs lying around, check out this video to learn how to modify your bobby pin to break into most locks. Using handcuffs, you can mold the tip of the bobby pin to allow the ability to open up things such as handcuffs and other locks.

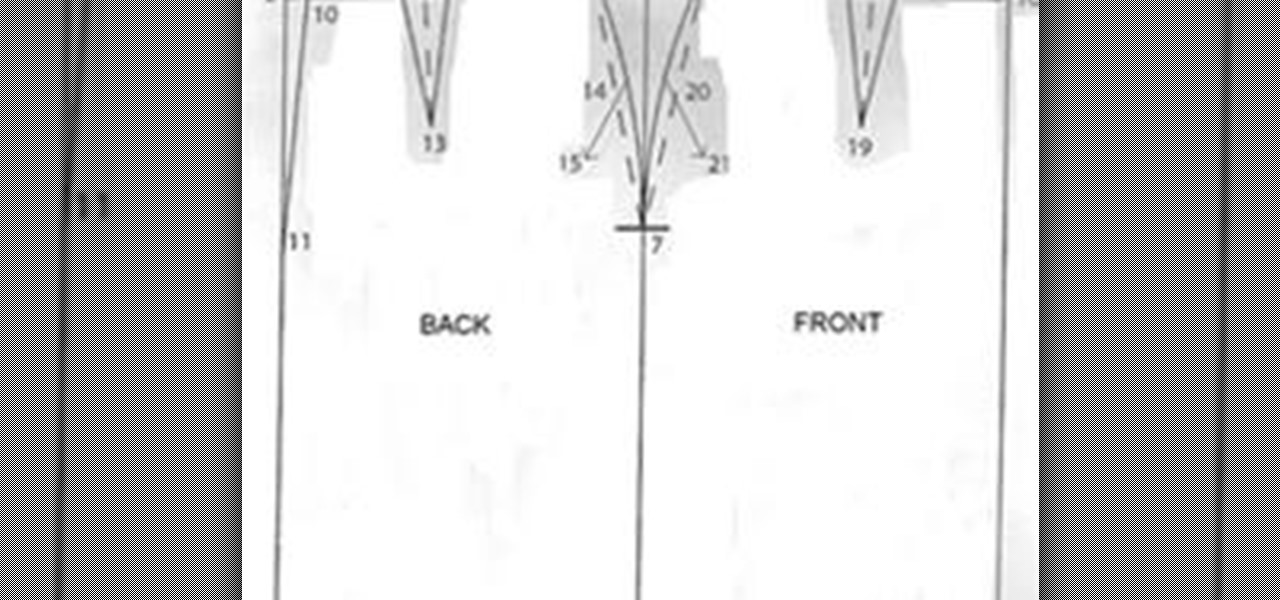
Written instructions on how to draft a basic skirt pattern with accompanying video. Take your correct measurements before you begin.

The best chemistry experiments are those you can perform with items already laying around your house. With only some sugar, salt substitute and an instant cold pack, you can make your very own gunpowder! Being able to make homemade gunpowder without a trip to the store can be a lifesaver, no matter if it's just for testing out a Civil War-era musket, blowing up stubborn tree stumps, or preparing for battle when imperialists overrun your country.

InuYasha is a Japanese manga series that follows a time-traveling high school student, a half-demon, a lecherous monk, fox demon, demon slayer, and nekomata. It takes place during the Sengoku period as they seek to find the fragments or the Jewel of Four Souls. InuYasha is the half-demon. DragoArt has this video tutorial on how to draw a Chibi InuYasha. Get more detailed instructions on the step-by-step cartoon drawing here.

This scorpion toy was constructed by Make Magazine with a Twitchie Robot Kit. If you're afraid of real life scorpions this friendly toy might help you get used to them. His plush body is made from some fabric aiming to make him look like an Arizona bark scorpion, which are tan/yellowish/translucent. Twitchie is Arduino powered and comes pre-programmed, so it's an excellent kit for beginners in robotics, because no programming is required! You can download and modify the code if you want, and ...

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

In a previous tutorial, we were able to measure horizontal surfaces such as the ground, tables, etc., all using ARKit. With ARKit 1.5, we're now able to measure vertical surfaces like walls!

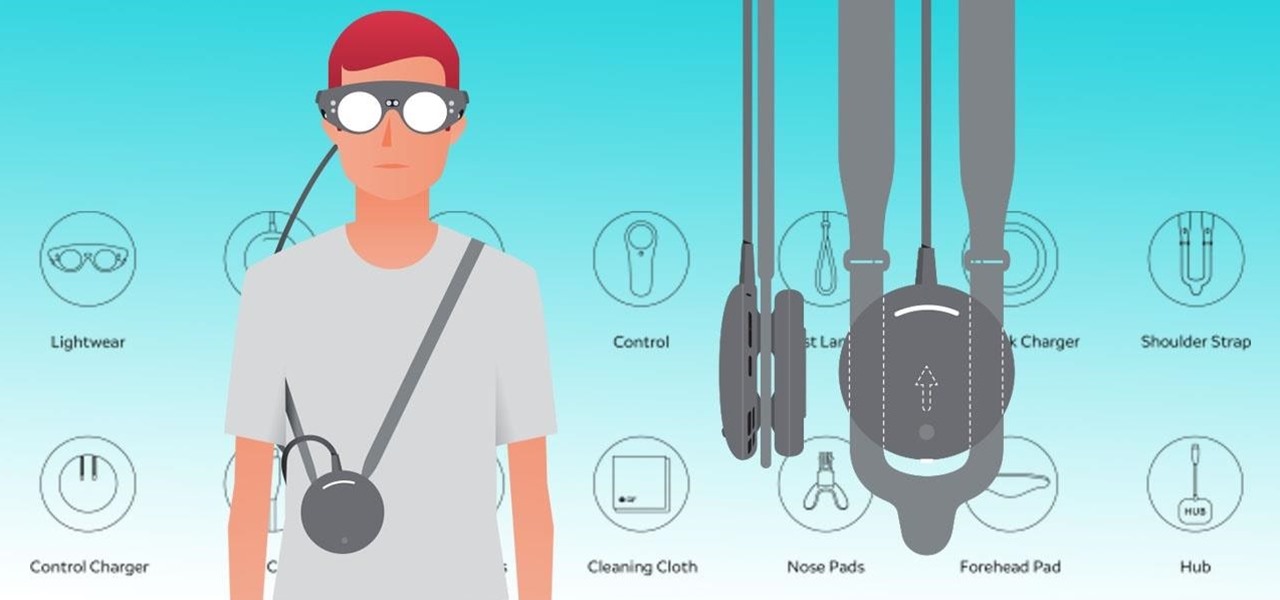
Now that the Magic Leap One is officially out in the wild, users are already beginning to find out exactly how it works and what it might be useful for in the augmented reality space. But there are still other, more unique questions that remain unanswered.

Hello, budding augmented reality developers! My name is Ambuj, and I'll be introducing all of you Next Reality readers to the world ARKit, as I'm developing an ARKit 101 series on using ARKit to create augmented reality apps for iPad and iPhone. My background is in software engineering, and I've been working on iOS apps for the past three years.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

We can add one more health effect of our gut bacteria to the growing list. Researchers from the UK have just reported that the gut microbiota plays a role, both directly and indirectly, on the toxicity and efficacy of chemotherapy. Their findings are published online in the journal Nature Reviews Gastroenterology & Hepatology.

Hear me out. No, really. Before you sharpen your pitchforks and give me anecdotal evidence of your Chinese restaurant syndrome, I think you need to know a few things about monosodium glutamate. First of all, it's a naturally-occurring chemical compound that can be found in anything from tomatoes to cheese, and is used in all kinds of foods from KFC to breakfast sandwiches. So spare me the comments on MSG and Chinese food—you probably eat MSG on a daily basis without even knowing it. (And also...

Cold brewing tea and coffee are all the rage, and for good reason: they're idiot-proof. I, personally, am a total dunce at brewing coffee. It either ends up strong enough to peel paint from a car or so weak that you can see through it. Meanwhile, I have friends who inevitably brew green tea to the point where it's painful to drink it.

Glow sticks, a popular favor at parties and outdoor events, and a must-have on Halloween, can be traced back to the United States Navy in the mid-1960s. The military desired improved visibility during night operations, and glow sticks, with their small-size portability and lack of batteries, were a perfect tactical solution.

It's all fun and games until the technology is actually put into use and you realize augmented reality is now part of Death Star.

Ever since the US Army awarded Microsoft's HoloLens a $480 million contract, the battle for enterprise augmented reality has heated up in earnest.

The Los Angeles Rams are the latest NFL franchise to introduce new or modified uniforms for the 2020 season, joining the Atlanta Falcons, Cleveland Browns, Indianapolis Colts, New England Patriots, Tampa Bay Buccaneers, and their neighbors, the Los Angeles Chargers.

In the pursuit of large displays with thinner bezels, Samsung has sacrificed some components. While the loss of the headphone jack gets all the attention, there are other victims — namely, the notification LED.

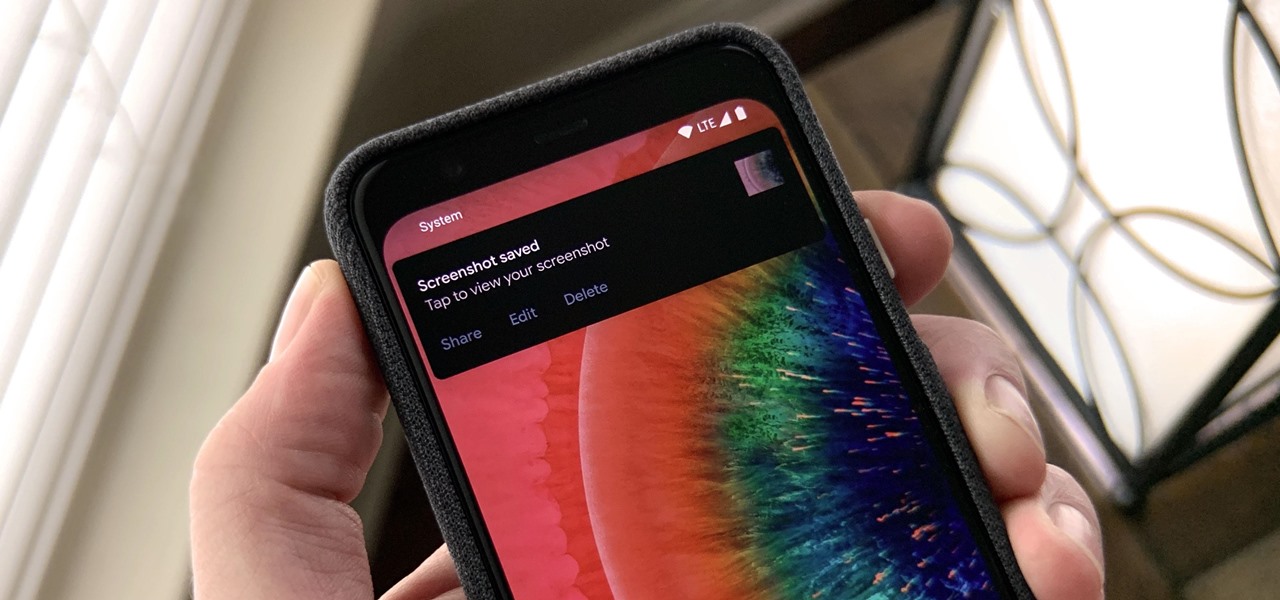
On stock Android 9 and 10, it is easier than ever to take a screenshot and quickly edit the captured image. However, the downside to that convenience has manifested itself in a heads-up notification that can also get in the way.

With all the talk about privacy concerns recently, Google's name keeps coming up because they are a very data-driven company. As an Android user, they know basically everything about you based on your device usage. That can easily scare some people off who are worried about their privacy and security. You do have some say in what personal data Google controls, but what if you want total control?