While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

Indie band The Script went from fledging, unknown band to Billboard 100 and massive concert sellouts after releasing their first big hit, "Break Even." A bittersweet message paired with strong guitar riffs and vocal stylization, "Break Even" captured the hearts of teenage girls everywhere.

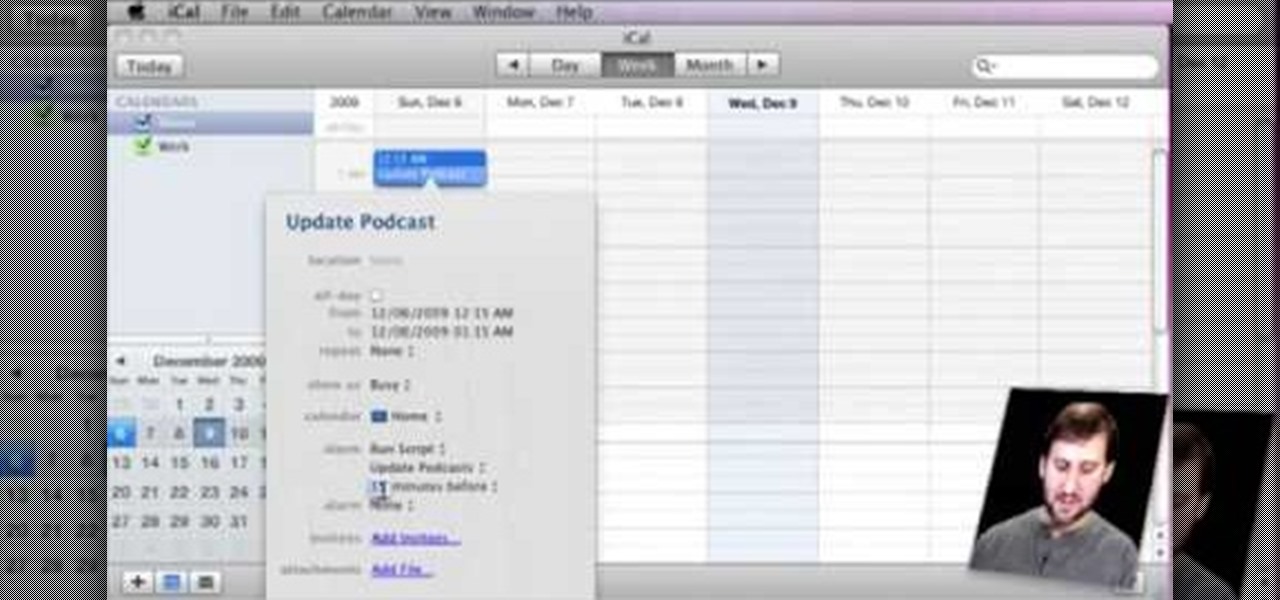
Gary teaches us how to schedule podcast updating with AppleScript in this tutorial. First, log onto the AppleScript Editor and run it. Next, type in "tell application "iTunes"". Then "activate", then "updateALLpodcasts", then "end tell". Now, click the compile button and then click run. Now, you will see iTunes pop up and it will download all the podcasts, then they will update on your computer. Now, save this script to your desktop or wherever you want it, and keep it in the format Script. O...

In this how to video, you will learn how to make an RSS feed as an alarm clock. To do this, you can use the Microsoft speech program. Open the alarm batch file. Modify the Perl script so that it downloads the RSS feed from the Digg website. It will strip all the tags and html so only the text is left. From here, you run a script that converts the text to a wave file. From here, the alarm m3u will start. You can then run the command prompt to schedule the alarm time. Go to schedule tasks to ac...

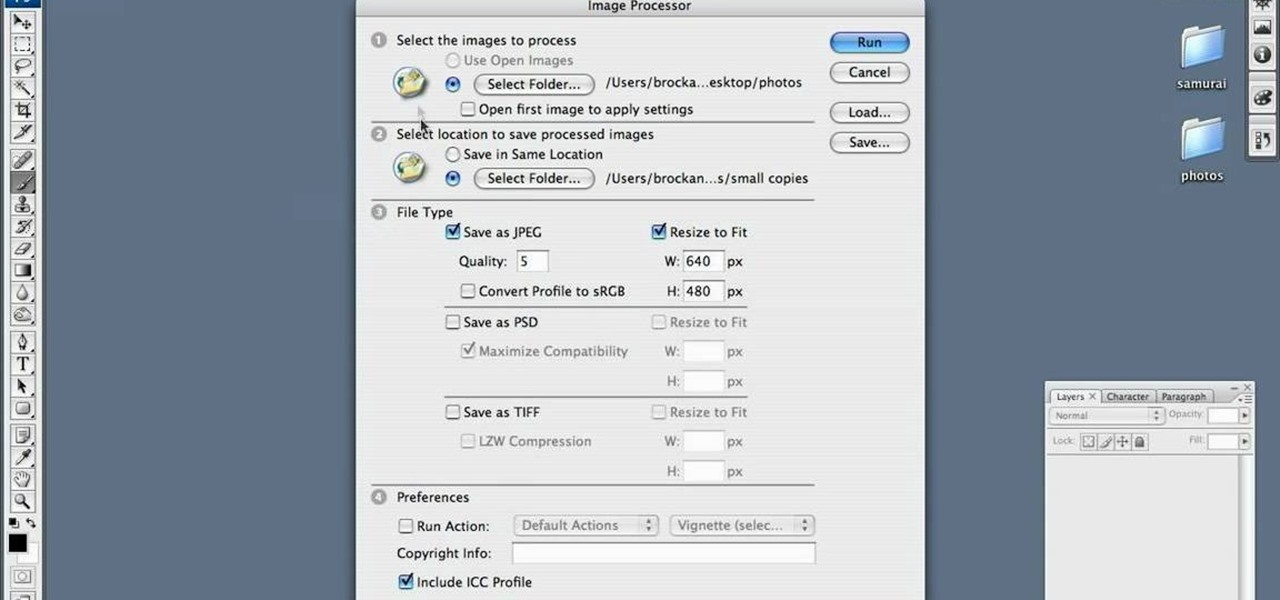
Are your high resolution photos taking too much space on your hard drive? Tired of getting file too large error when emailing photos? Don't worry Photoshop Samurai will help you batch resize your photos as fast as a ninja! You will need: Photoshop (Not Elements version), photos that need to be resized Go to file, then scripts and select image processor. Select the source folder (where your pictures are stored on your computer). Then select a destination location (where you would like the proc...

If you have a Samsung Galaxy S, Vibrant, Captivate, or I9000 and want to unlock it, this video will show you how to do it. Also, this method will let you do it with one click. You'll need your USB cable to connect to your desktop or laptop to download the necessary script. Enjoy.

Need to create Flash buttons? You've come to the right place. In this video, learn how to make professional looking, but easy to make, buttons with no scripting. The buttons featured in this tutorial are featured all over the web and on almost every flash site. Create the buttons you need for your web project with help from this step-by-step tutorial.

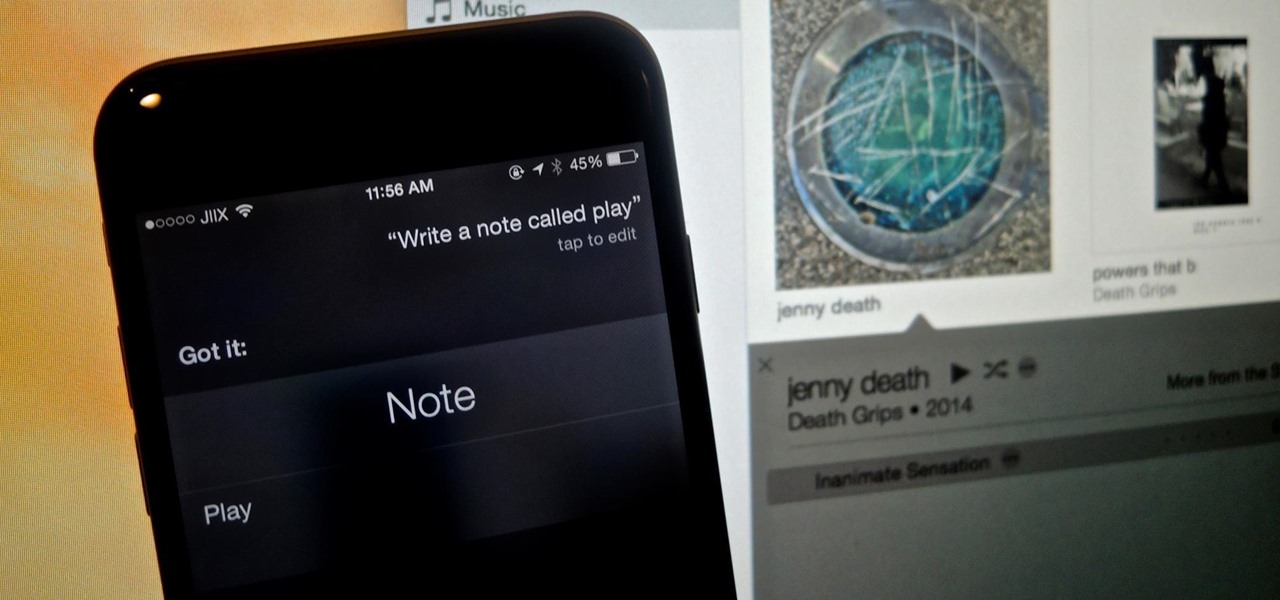
Back in its infancy, the App Store was filled with text bomb apps that allowed users to send a barrage of text messages to friends, family, and foes. It was a fun way to annoy people, but Apple quickly scrubbed the apps because of technical issues. Although text bombs are still banished, you can now use a Siri Shortcut to send text bombs through iMessage on your iPhone.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

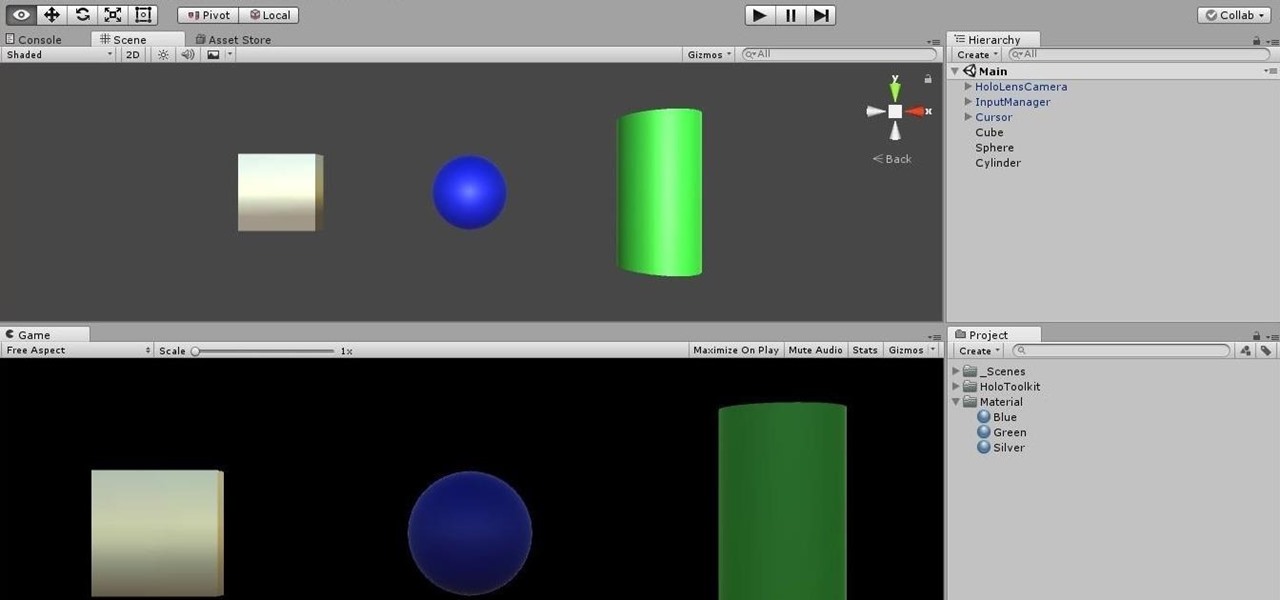
Being part of the wild frontier is amazing. It doesn't take much to blow minds of first time mixed reality users — merely placing a canned hologram in the room is enough. However, once that childlike wonder fades, we need to add more substance to create lasting impressions.

Hello again, ***UPDATE: Adding links to the other Two articles****

Recently I've been looking around our wonderful community and I've seen some absolutely hands-down fantastic python scripting articles. But, in the end, these series weren't very extensive. I've been wanting to do a series on teaching python for a while now, and I don't mean just the basics, I mean to make an extensive series that takes it all the way from "Hello, World!" to popular third party modules, and everything in between!

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

Sometimes our information important. So important that we have to encode it to keep it away from criminals. What better way to encode information than to make our own encoder with Python?

Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my novice hackers! This is the third installment of my Python scripting series. If you haven't read the previous two articles, take some time now to go back and read Part 1 and Part 2 before you proceed here.

While Apple's Continuity feature has certainly impressed me, I can't help but feel like it could be used to create a better connection between my iPhone and Mac. Sure, Handoff allows me to pick up where I left off in certain applications between the two devices, and it lets me pick up calls and send text messages on my Mac, but I want even more functionality.

When Yosemite was released, a more detailed boot screen came to your Mac. So now, just like on Apple's mobile devices, you will see a loading bar telling you how far into the startup process you are. Apple also decided to add a black version of this boot screen to newer Macs, leaving those of us who purchased a computer before 2011 out of the loop.

Welcome back, my budding hackers! Recently, I showed you how you could exploit the widely disseminated OpenSSL vulnerability that has to become known as "Heartbleed". Although the world has known about this vulnerability for over a month now, it will likely take many more months—or even years—for everyone to close this vulnerability.

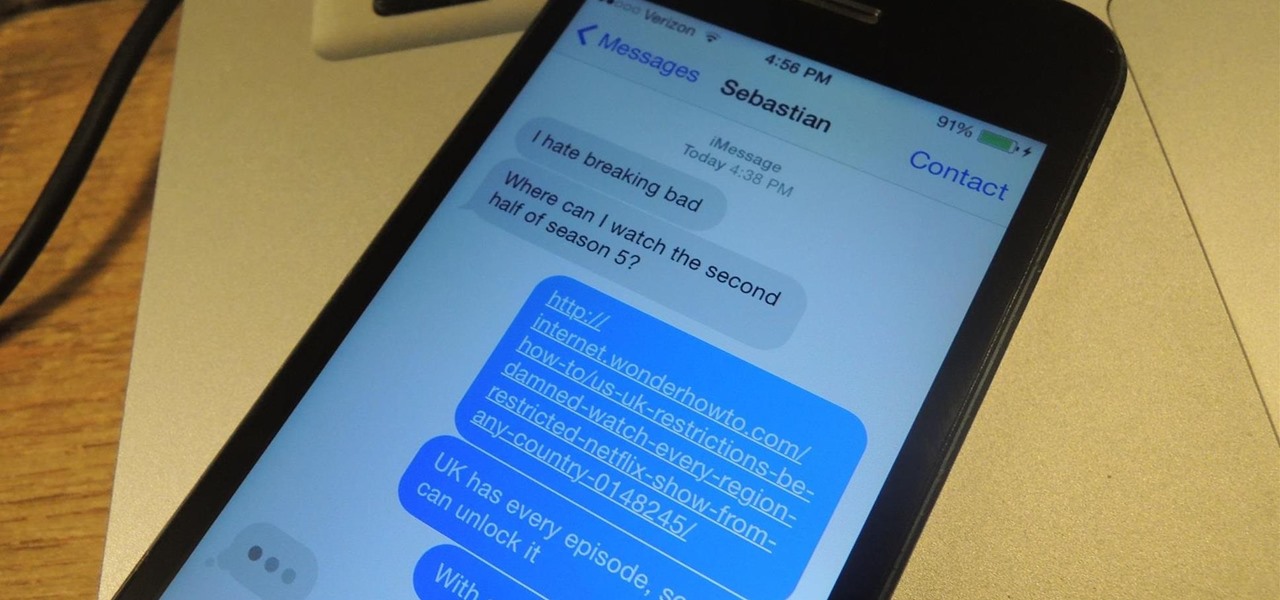
NSA aside, Apple makes it difficult for users to extract and download text messages from their iPhones onto a computer. For whatever reason (legal, devious, neurotic, etc), we've all found a time where we'd like to save backups of certain meaningful, important, or perhaps incriminating conversations (including all MMS or iMessage pictures and videos). While there are a handful of third-party applications that can help with this process, the majority of them cost money and implement certain te...

In order to build Google Chrome extensions, you will need to familiar with scripting and codes. These are small programs that add additional functions for programmers. It is a compressed directory. These files must have a particular name: i.e. "manifest" (manifest.json). An extension will have at least one of the following: browser actions, page actions, content scripts, and utility web files.

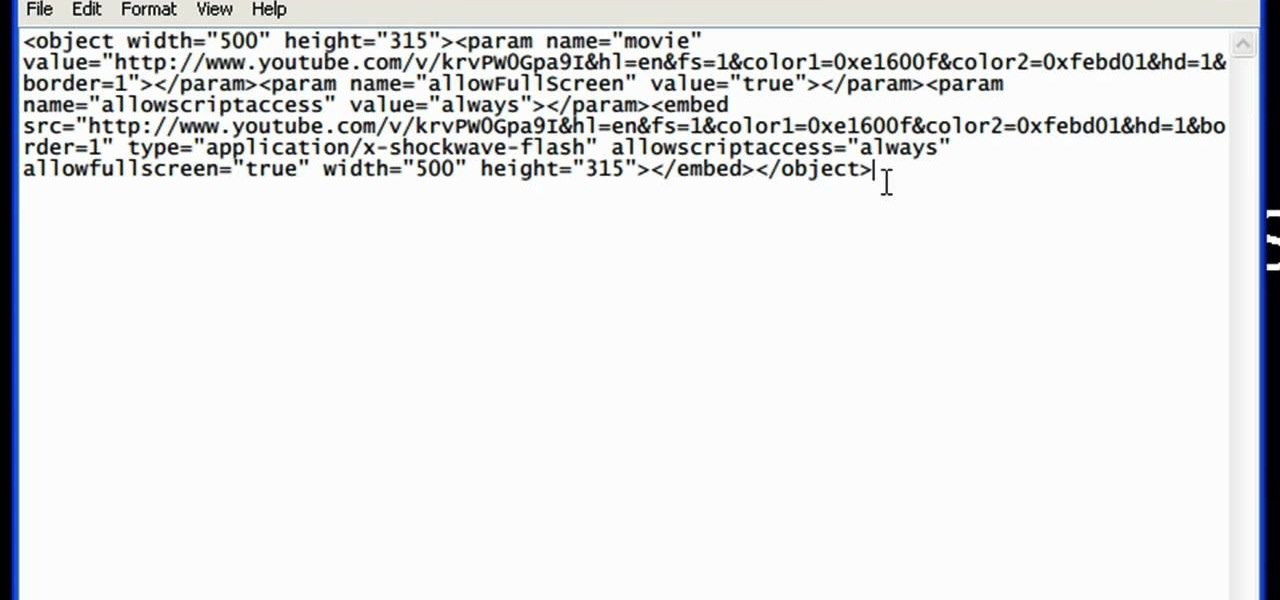
YouTube videos can also be embedded in your own website. These YouTube videos by default do not play and one should explicitly click the play button for the videos to stream. However you can change the embedded video settings so that the video starts streaming once your web page loads. This can be very helpful as it starts streaming immediately with out wasting time for the user to click on the play button. Go to the YouTube video that you want to auto play on the YouTube website. Copy the em...

This video shows the method to create a photo montage in Sony Vegas. Go to 'Options' menu & Preferences. Go to the 'Editing' tab & 'New still image length (seconds)' and put the corresponding value and hit 'OK'. Open the pictures from explorer and you have a montage in which pictures last for a few seconds when another one comes up. Go to 'Tools' menu and 'Scripting' option. Click on 'ApplyTransition_1_2'. Choose 'Standard Cross Fade' from the drop down menu. Fill in 'Overlap Frames' which te...

Learn how to enable Java script and Cookies in Konqueror in simple steps. First open the respective webpage and go to 'Settings' option and select the last option in it. Now select 'Java and Java Script' option found in the left corner of the page and click in the enable check box in both the tabs. Now go to the 'Cookies' option and check the 'Enable cookies' check box. Press on 'OK' to finish when everything is done.

In this video tutorial, Chris Pels will show how to configure an ASP.NET web site to use a specific version of ASP.NET/.NET Framework. First see how to identify what version of the .NET Framework a web site is associated with by viewing the script map in Internet Information Server (IIS). See how a script map is associated with the root in IIS and then with individual web sites. Next learn about the ASP.NET IIS Registration tool (aspnet_regiis.exe) used to configure IIS or an ASP.NET web site...

In this video the instructor shows how to make a simple flash click-through photo gallery with Action Script 3. First the instructor shows a sample gallery that you can make using this tutorial. To do this open a new flash action script 3.0 file. The first thing you have to do now is, in the right hand side change the document size to 750 by 500 pixels and give it a dark back ground color like dark gray. Now open the image that you want to use in this album by dragging them on to your flash w...

Bejeweled Blitz is a Facebook game. Learn how to hack Bejeweled Blitz with tricks, cheats, hacks. Watch this video tutorial to learn how to hack Bejeweled Blitz with cheat codes (07/21/09).

If you record yourself for a vlog or story post using your selfie camera, it can be challenging to stay on message. You might worry too much about the way you look or sound to focus on what you want to say. Using a script can help, but looking away from the camera to read is unprofessional, even on social platforms like Instagram. What you need is a teleprompter, and there are apps for that.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

Welcome back everyone. This article isn't going to contain anything related to scripting, but rather some updates about the series. We'll be quickly discussing what we've covered so far and what is to come.

Right, So i've been asking alot of questions here on Null-Byte and everyone has been really helpful to me.