
How To: Use BeEF and JavaScript for Reconnaissance
Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.


Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.

If you're completely new to Android, you're in for a treat with all of the software tweaks and customization options that your smartphone or tablet offers out of the box. But if you really want to take things to the next level, the ability to mod your device expands exponentially when you're rooted.

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

If you've been using Windows 10 for a while, you already know that Microsoft incorporated lots of new features into it. So you're probably familiar with Cortana (the new voice assistant), the Edge browser (their replacement for Internet Explorer), the newly resurrected Start menu, and all of the other big changes.

Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigators have a hacking background, but the best ones do.

It's that time of year again, folks. Each fall, Google debuts a new device alongside the latest iteration of its mobile operating system—but this year marked the release of three new Nexus gadgets.

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

Welcome back, my hacker wannabees!

Welcome back, my neophyte hackers! Several of you have written me asking how to crack passwords. The answer, in part, depends upon whether you have physical access to the computer, what operating system you are running, and how strong the passwords are.
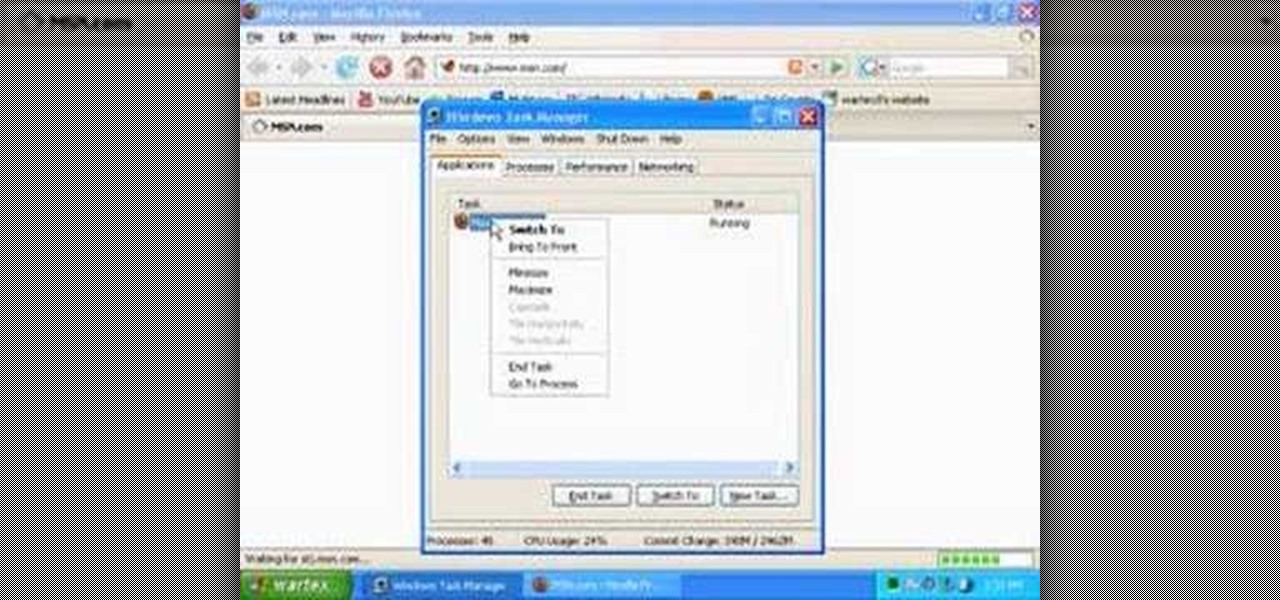
Programs aren't perfect. Either are operating systems. And when one or the other (possibly both) aren't working as expected, your program may freeze up and become unresponsive. If this happens to you in Windows frequently, you need to know how to force quit the application, so you can restart it and get back to work.
Forget keyboard commands, try out some simple mouse gestures to control your Windows computer. You can customize mouse gestures that let you take command of your PC in ways you never thought existed. If you prefer the mouse over the board, this is for you!

This video takes us through a process of speeding up our internet connection using OpenDNS.com. Open the webpage and go to solutions and click on the icon open the DNS page and it lists computer or router, she selects computer and list of operating system is listed, she selects vista. She goes to start and selects control panel, click on view network status and connection, in that select view status and then click on properties and on the networking page, go to internet protocol version 4 and...
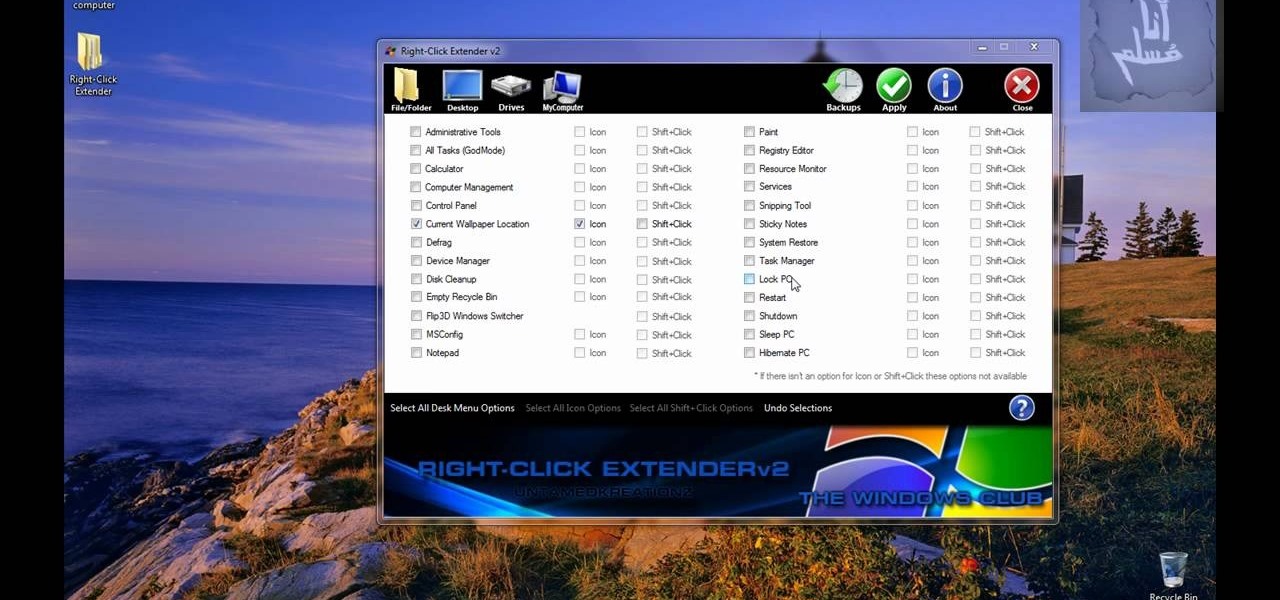
Tired of being limited with your right-click options in Microsoft Windows? There's a program that could help you out, and it's called Right-Click Extender. Insert many different additional items to the right-click context menu.

This video demonstrates how to make cotton candy using the Gold Medal X-15 machine. Plug in the three-prong chord in its own independent jack. Use a heavy duty three-prong extension cord if needed. Remove the clips from the net and spread the net around the inside of the pan, and clip it onto the sides of the pan in four places. Use commercially prepared floss mix, and carefully pour it into the spinner head while the machine is off. Cover the pan with the dome and turn the power on, setting ...

This how-to video is about how to make PS3 controller work on the computer that have either Windows XP, or Vista or 7 as their operating system.

Repetition, repetition, repetition. Brainwashing, is it real? Watch these absolutely stunning segments of hidden camera containing both Bill Clinton, and Barbara Bush. Probably one of the most debatable segments is the one featuring Clinton talking to Larry King behind the scenes. If you turn your volume up it is hard to disregard, that they both in fact knew, Clinton would be elected, and the corruption in media is also clearly demonstrated. There is a segment with Barbara, staring eerily fo...
Everybody is going digital these days, so everybody has a reason for software like HandBrake. You can save your entire DVD collection on your computer in digital files, and you can convert videos into different formats. Check out this video tutorial on how to rip DVDs and convert videos on Ubuntu Linux, Windows, and Mac.
There's plenty of reasons why one would want to convert a webpage to a PDF document. And there's numerous ways on how one can convert that web page (HTML) into a PDF file. Check out this video tutorial on how to convert webpage HTML to PDF on Ubuntu Linux.
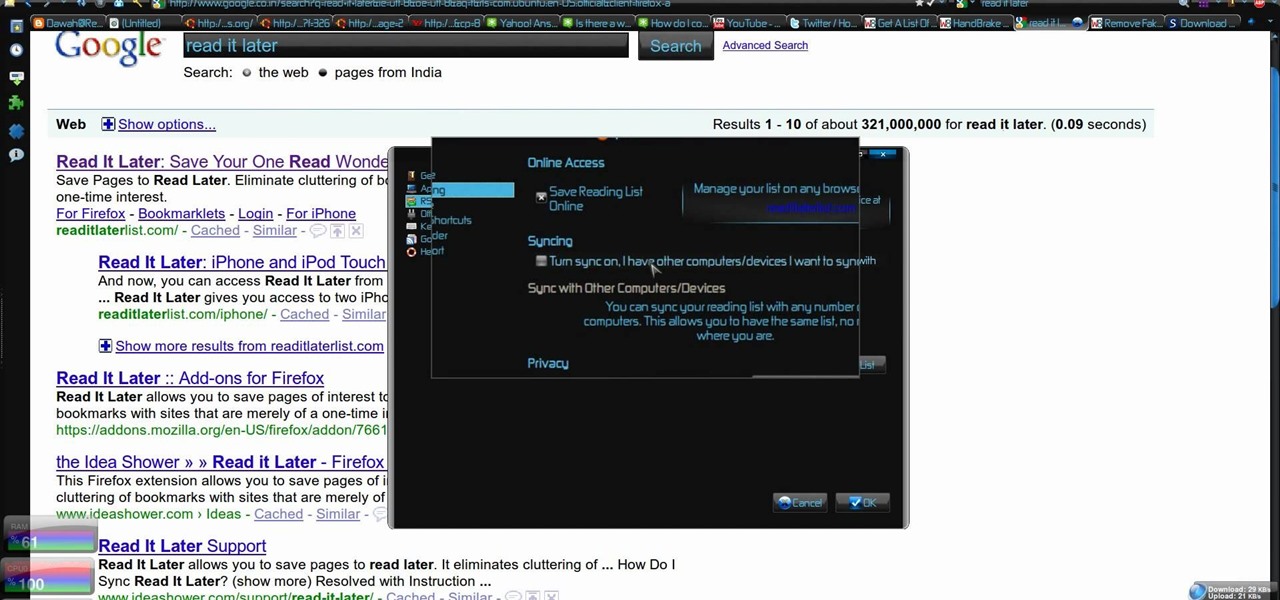
Is there another option for reading a webpage later than bookmarking? Nobody wants to bookmark something they're going to look at once and that's it. It creates clutter and confusion. But there is a way to stop that. This video tutorial will show you how to save pages in one click to read later on Firefox.
Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.

Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.
New to Windows? No problem... here's a beginner's video tutorial that will teach you how to prevent cut, paste, copy, and delete on Windows files.
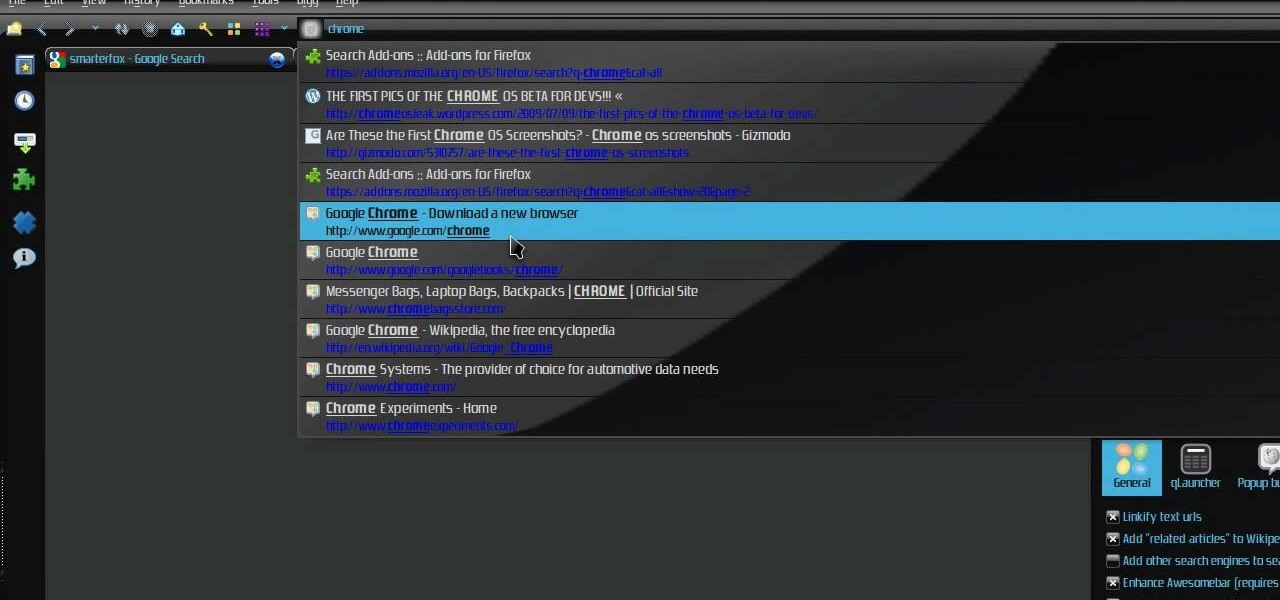
Check out this video tutorial on how to make your Firefox smarter using SmarterFox. Wikipedia sidebar SmarterFox adds a "related articles" sidebar to the left side of Wikipedia.

Safe motorcycle riding requires knowledge and skill. Testing two-wheel vehicle operators is the best measurement of the skills necessary to operate safely in traffic because people often overestimate their own abilities.

Here is the training video used to teach soldiers how to use the M-209 portable, mechanical cipher machine unit.

This quick video shows you the method for holding and operating a chain saw and also shows you how to correctly limb a tree, as well as what sort of cuts to use and what you should watch out for in the process.

This video shows how to enable automatic login for Macintosh Operating System users: 1.Click on the Apple icon in the top-left corner and select System Preferences.

This video provides a tutorial on how you can operate a Semi-Auto Quad ATV. The quad used in this movie is a Kawasaki Bayou 250cc 2wd.

In order to install a new hard drive in your MacBook Pro, you will need to save everything on Time Machine. You will need to be in a static free environment, a hard drive, and small screwdriver.

Radio communication is one of the oldest and most effective means of communication via technology, so it's no wonder it's still a popular way to send and receiver signals, especially on the water. Having a Marine radio can be critical when operating a boat on any type of water. There are many uses for a Marine radio, but the most important is to send a distress signal — here’s how to do it.

NTFS? What is it? It stands for New Technology File System, but what does that mean? Well, it's the standard system for filing in Windows NT, including all later versions, up to the current Windows 7, but Mac users can take advantage of this file system, too. If you’re confused when it comes to your hard drive’s format, this guide will show you the way to get the most out of your system.
In this thirteen part, comprehensive overview of Mac's new operating system, Snow Leopard, you will learn everything you need to know to get started. If you have recently upgraded or purchased a new system, you may benefit quite a bit from this series. Start at episode one and skip ahead if you need to, you will get a total step by step walkthrough and be up and running in no time.
This video tutorial from knif3r2 shows how to install and run Mac OS Leopard on PC using Virtual Machine.

This video tutorial from bobby93macboy shows how to install Mac OS Leopard operating system and make it bootable.
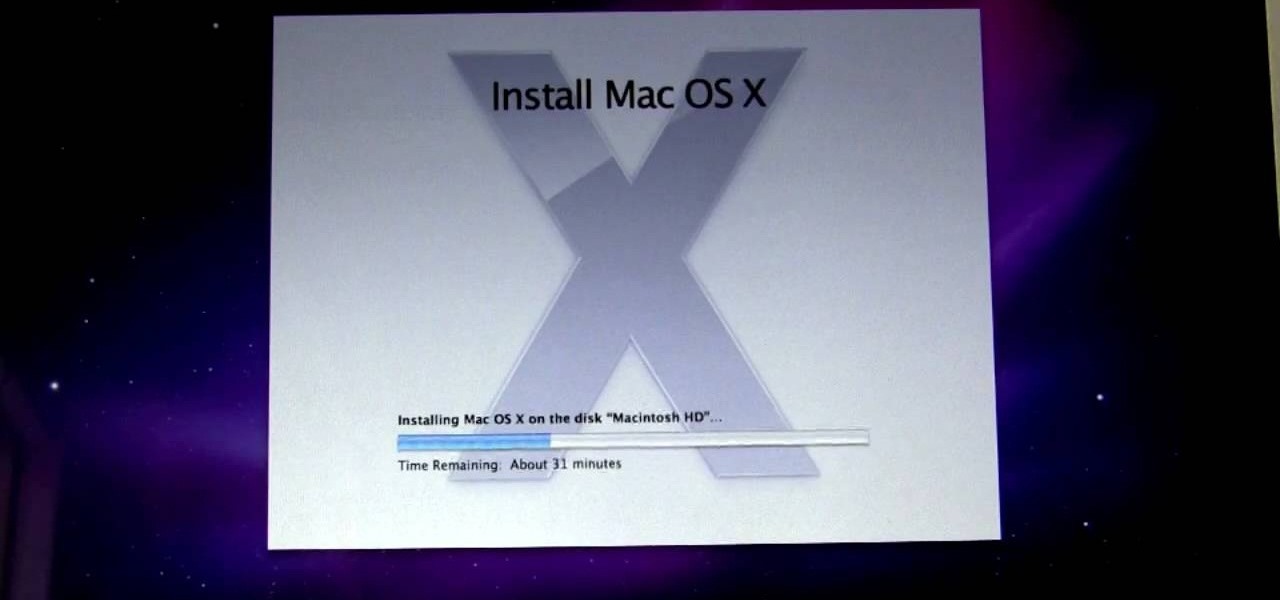
Michael of michaelsherlock.com demonstrates the installation of Mac OSX Snow Leopard onto a Mac with an Intel Core2Duo processor. We're reminded from the very beginning of the importance of backing up our entire system before beginning the installation. Once that's taken care of, it's time to insert the Snow Leopard disk. Once the disk is loaded, and we've agreed to the End User License Agreement, we are presented with a number of options to customize our operating system, including options s...