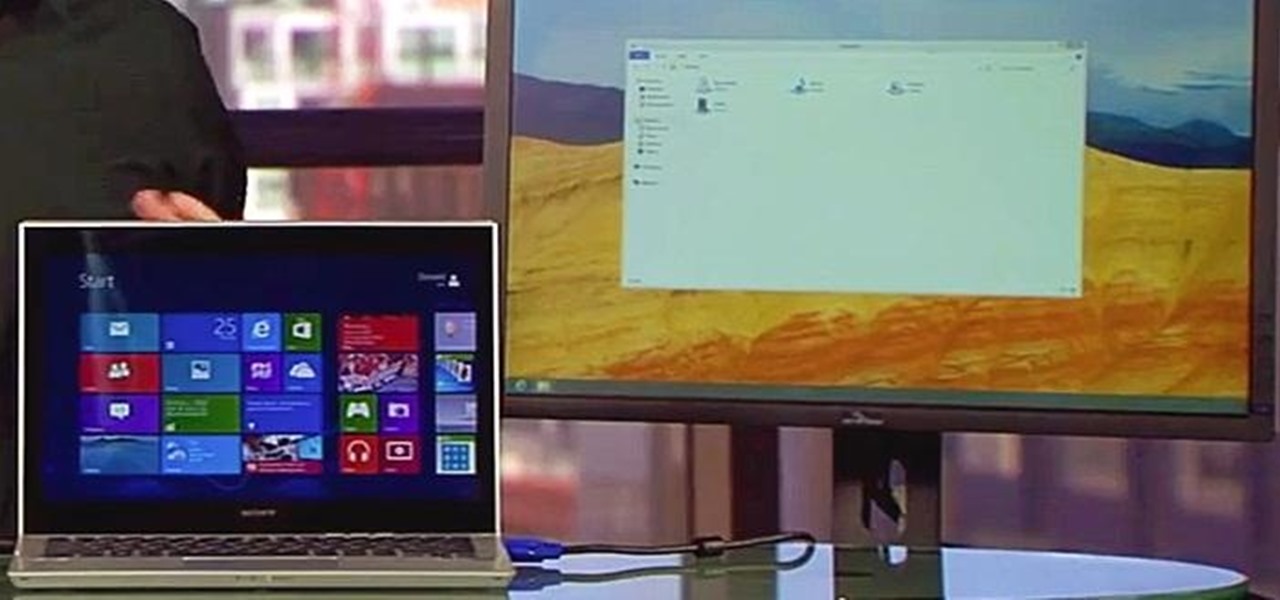
The new Windows 8 operating system pushes the Metro interface hard, but not all of your apps will play nicely in Metro, which means you'll need to resort to the traditional desktop environment for some of your favorite programs. As a result, it has left many users picking between the two—Metro or traditional? Fortunately, there's a way to run them both simultaneously with the use of second monitor. In the video below, Donald Bell of CNET explains how you can run both interfaces simultaneously...
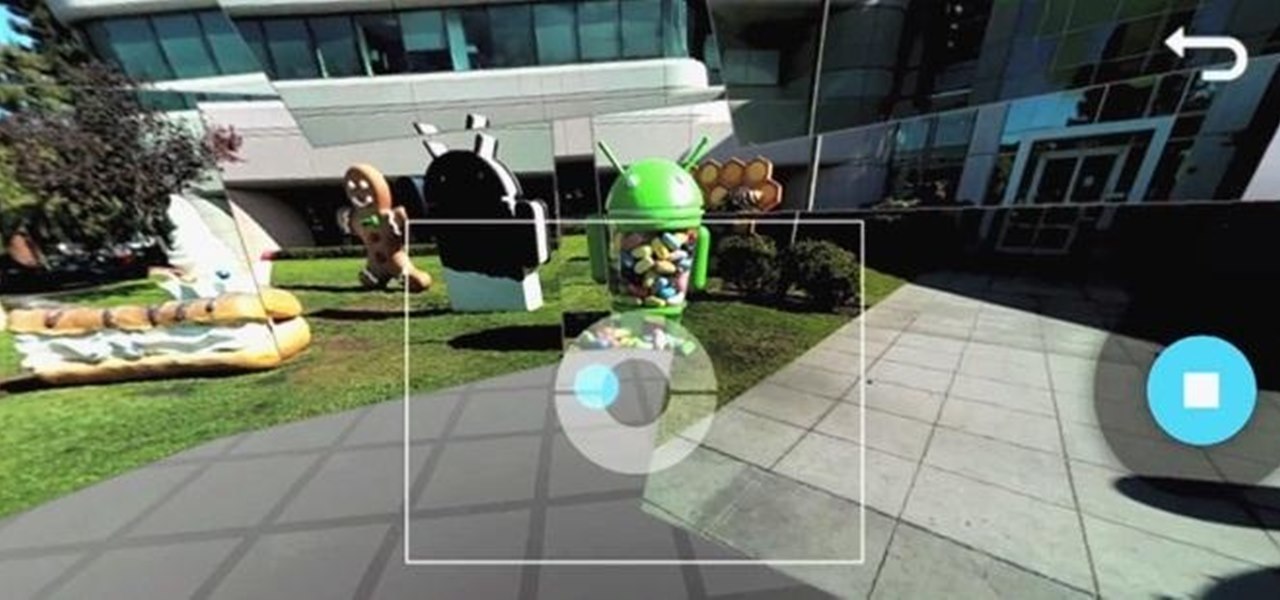
With some Samsung Galaxy S III owners still waiting for the Android Jelly Bean 4.1 update to hit their device, Google has wasted no time in releasing information on their next operating system update—Android Jelly Bean 4.2, which will come stock with the newer Nexus 7 and 10 tablets, and the all-new Nexus 4 smartphone. While the two Android updates are fairly similar, one of the big features in Jelly Bean 4.2 that sets the two apart is the new camera application, which has a feature called Ph...

One of the more innovative features about the new Windows 8 operating system is the ability to unlock the screen via a picture password. This new feature allows the user to select any photo they would like and use taps, circles or straight lines to unlock the device. The video below shows the picture unlock in action.

Microsoft's newest operating system, Windows 8, will hit stores everywhere on October 26th, and they hope this new version will shift the way we think about computers and their interfaces. In an effort to get as many early adopters as possible, Microsoft is even making their OS cheaper than usual, offering upgrades from previous versions for as low as $40 for a limited time.

One of the most played-up features of Windows 8 is that it's so much faster than previous versions. So fast, in fact, that Microsoft had to change the way that users access the BIOS because 200 milliseconds just isn't enough time to hit the right key. It may take some getting used to, but it's probably a welcome change for most people, considering that the "right" key is different depending on what type of computer you're running the OS on.

Dogs make great best friends, but anyone who's had one knows they can be the most high-maintenance friend you've ever had. Bathroom breaks, feeding schedules and walks are only the beginning. Even if you make your dog organic treats and teach it neat tricks, it still needs to play. And after that fifth game of fetch, your arm can get pretty tired.

Access your computer's BIOS settings

Along with rebranding Magic Leap 1 for enterprise customers, Magic Leap has gifted its developer community with some new toys with a tease of more to come in 2020.

With EA chief executive Andrew Wilson stating the official mobile version of Apex Legends won't arrive until the 2021 fiscal year, fans have to wait at least another year to enjoy their favorite battle royale game on the go. But for those who can't wait, there are ways to play the game on iPhone and Android right now.

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.

Watch this video tutorial to learn how to level hack Restaurant Life (12/05/09). 1. Open RL and Cheat Engine 5.5, then point CE 5.5 to the process of your browser.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

In this video tutorial, you'll learn how to use the Second Copy backup application, for the Windows operating system, to protect your most important data. For step-by-step instructions on installing and using Second Copy, take a look at this backup how-to.

VLC Media Player is one stop shopping for all your music and video playing needs. You can watch any audio or video formats from .flv, .wmv, .mov and more. If you are tired of having multiple softwares for playing different files, consolidate and use VLC Player instead. This tutorial shows you how easy it is to download VLC Media Player for any operating system.

This software tutorial shows you how to convert your Windows Movie Maker projects using conversion software so that they will play on a Mac computer or operating sytem.

Check out this video tutorial on Blender. You'll see how to successfully create a modeled skull in Blender.

In this series of video clips, you’ll learn tips and techniques for using various types of metal shears, including how to use hand-held and foot-operated types of metal shears, and how to use a metal press and metal hole punch. Expert Jon Olson offers advice on cutting procedures, the proper clothing and precautions, and advice on maintaining and cleaning metal shears. Jon also covers the electrical requirements for operating an electric shear, the various points of danger when operating the ...

This shows you how to make an eggnog cheesecake. Make a short bread crust to give your cheesecake a unique flair. Combine all your ingredients and substitute ricotta for mascarpone cheese to give your cheesecake a New England twist. Since the chief is from New England he wants to make a cheesecake with some flavors that make it unique. Also when your cheesecake is done you can put some homemade sauce on the cheesecake. This a fun festive recipe that you can make for the holidays.

Got video files on your computer? Watch them on your big-screen TV – using your Xbox! You Will Need

This step-by-step video tutorial shows you how to install CHDK onto your Canon digital camera. CHDK is a firmware enhancement that operates on a number of Canon cameras. CHDK gets loaded into your camera's memory upon bootup (either manually or automatically). It provides additional functionality beyond that currently provided by the native camera firmware.

Admit, you're curious. You want to know just what does it take to make a virus for the Mac OS X operating system. Check out this video to learn how to write a harmless virus for computers running Mac OS X.

Have access to a Battistella T220P ironing table and, however improbably, wondering how to use it? Well, you're in luck: With this video demonstration, you'll learn how to operate the Battistella T220P ironing table in the service of ironing a shirt. For more, or to get started using your own Battistella T220P ironing table, watch this video tutorial.

General Pipe Cleaners Easy Rooter Junior is the right machine to clear washtubs, small floor drains, roof vents and other medium-size drains. This video will give you a general overview of the operating instructions and safety procedures for the easy Rooter Junior. Take a look.

Cool project to show how a capacitor operates!

A transom window is a traditionally fixed window over a door or an operating sash window. In this how to video, the experts form the DIY network prep and install a transom window in this historic home. Watch this tutorial and you can be installing a transom window into your own home.

The Paslode Framing Gun is operated by a gas cartridge and battery so an air compressor is not needed. The tool also has a large range of nails available for different job requirements from 50mm To 75mm. Watch this video tutorial for a demonstration on how to use a Paslode impulse framing nail gun.

This video tutorial shows how to assemble an automatic Lego crossbow. Learn how to build and operate an automatic toy crossbow made out of Lego bricks.

If you've never heard of Blender, maybe you should get it and watch this video tutorial on how to use the curve tools in it. Great for 3D modeling and animating.

If you're going to do this, be careful, as your fingers get close to operating high voltage devices & potentially fatal current! Remember that TV's can store a lot of energy for a long time, so don't be poking your finger everywhere - even if the TV is off.

The Titan hitch receiver lock is a lock for all 2 inch receiver hitches. This is a simple padlock style lock. What you do to operate it is pull the protective cover off, take the key and give it a little bit of a turn. This video walks you through it.

When we think about operating systems, we tend to view them from the perspective of a user. After all, most of us have spent a substantial amount of time on our computers, and so we've become more than acquainted with the ins and outs of whatever system we have running on our personal device. But there is one operating system that, while being less commonly used on the user side, is behind a great deal of design and business technology: Linux.

Linux has been one of the most popular desktop operating systems for nearly three decades, ranking fourth in the world behind Windows, macOS, and Google's Chrome OS. The open-source operating system is loved for its quick, powerful, text-based interface and efficient communication tools.

Regardless of whether you're an aspiring or established coding pro, knowing just one or two programming languages and platforms is no longer sufficient if you want to be truly competitive in an increasingly popular and lucrative field. But before you spend an excessive amount of time mastering six new platforms, do yourself a favor and master Linux.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Downloading third-party screen recording apps can be dangerous. The primary function of these apps is being able to record everything on one's display, so it's easy to see how a malicious developer could exploit this for their own gain. That's why the addition of Android 10's built-in screen recording is so impactful.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

With Google's new Pixel 4, we now have another device in the pool of phones designed for normal-sized hands. The other major player in this segment is as big as it gets — metaphorically. Apple's iPhone 11 Pro is the small phone to beat, but can Google be the one to dethrone it?

With its 3D engine being responsible for approximately 60% of augmented and virtual reality experiences, Unity is continuing to place a premium on tools that not only keep developers working in its development environment but also make their workflows easier.

Every fall, we can expect a few things: leaves changing colors, cooler temperatures, and Samsung and Apple releasing new phones that fanboys and fangirls will argue about until the following year. This year, Samsung is mixing it up, releasing two phones in the Galaxy Note series. Let's see how the larger phones compare.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.