If you're interested in nabbing superhero memory strength, the secret behind training your brain is not necessarily what you might expect. Your standard G-rated brain strengthening exercises range from crossword puzzles to Sudoku to calculating fairly simple math problems to improve short term memory, but the real clincher used by some of the pros is essentially... porn. Yep, you read right.
When stories are told about people in need, the ones with happy endings include the details of someone that produced an action that caused the people in need to be better off than before. Do we have to wait for the identification of a need? Could we on purpose just plan to present products and services that cause our customers and client to see an improvement in their circumstances just because of the business interchange with an owner manager of purpose? The fair exchange of products or serv...
Sometimes you come across problems and glitches when you're playing FarmVille, FrontierVille, any of your facebook games, or even just using the internet for ordinary purposes! It might just be getting really slow, or you might start losing data or in-game items. As the Zynga customer support article will tell you, you sometimes need to clear you browser and flash cache! Here are some simple steps to do just that!

It takes talent and training to drive a semitrailer. See if you have what it takes to operate one of these rigs on the open road.

As we move toward the end of the year, the wheels of the augmented reality space continue to shift in major ways.

The last few weeks were fairly busy in the realm of augmented reality and remote meetings developments. Most of that activity was generated by some mammoth announcements from Snap and its Spectacles AR smartglasses, and Google, with its Project Starline experimental holographic video conferencing system.

Though Microsoft has had trouble keeping up with the demand for HoloLens 2, the company has been able to supply modified headsets to the US Army.

When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you even more protection against online threats.

What if you went to an art installation at one of the coolest venues in New York that you could then take with you anywhere in the world?

Filmed in what appears to be a single continuous shot, war film 1917 is now the front-runner to conquer the Best Picture category of the Academy Awards after bringing home the Golden Globe for Best Motion Picture in the drama category.

After recently renewed enthusiasm for the arrival of Apple's long-awaited AR wearables -- the subject of multiple reports and rumors over the past few years -- some of that excitement may now be dampened a bit.

OnePlus, whose phones always challenge for the title of best spec-to-price ratio, releases two main devices every year. There's the primary flagship in late spring, then an iterative update with the "T" suffix in fall. Typically, there's not much difference between the two, but this year, OnePlus is mixing up the formula a bit.

The growing stock of augmented reality apps filling up the Magic Leap store seems to be picking up pace in recent months.

Ever since Skynet took over the world in the Terminator film franchise, a large segment of the world's population has feared artificial intelligence.

With HoloLens 2 (hopefully) just around the corner, Microsoft has announced that it will no longer be providing any major operating system updates to the original HoloLens.

Next to map data overlays, one of the most often discussed concepts for apps that could propel augmented reality smartglasses into the mainstream is a real-time language translation app.

With the latest version of ARKit and a new set augmented reality development tools set to arrive this Fall with iOS 13, Apple has taken an unprecedented step in recruiting Chinese developers to fill the App Store with mobile AR apps now, likely with an eye to the future.

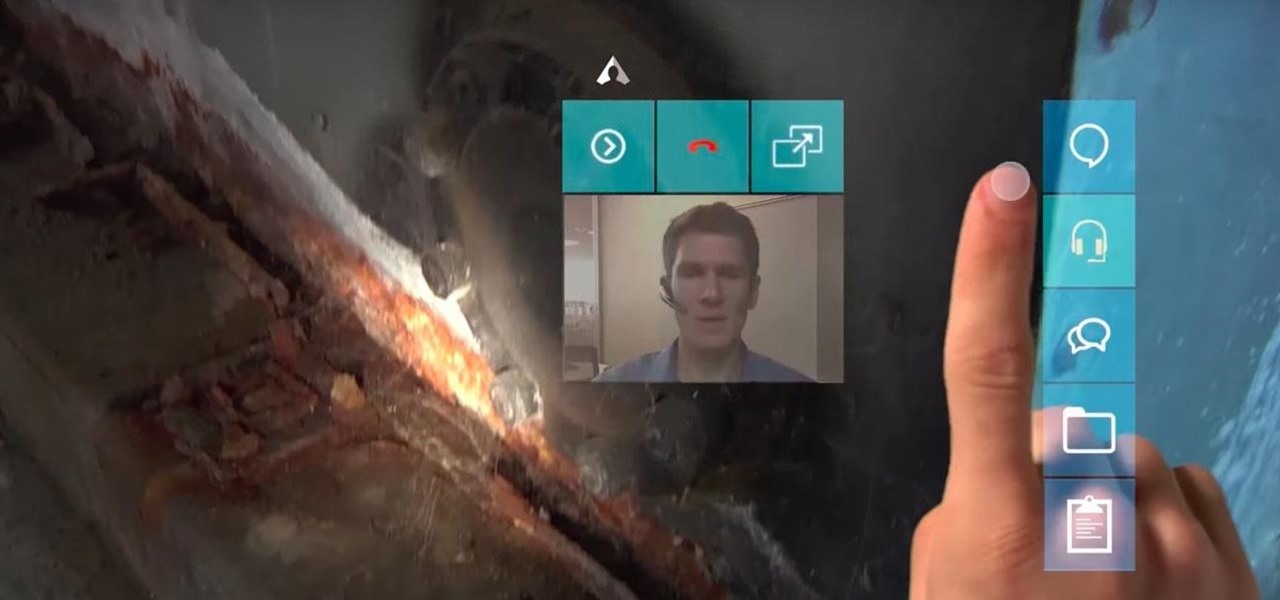
The idea of remote assistant apps in augmented reality has been taking off in the last couple of years, but Epson is introducing a differing kind of solution for companies that may benefit from a more straightforward dynamic before going full-on immersive with higher-end AR remote assistance tools.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

Not all enterprise augmented reality tools require a high-end headset and heavy computing power. Sometimes, a smartphone can do the job just as well. Along those lines, software maker Atheer is now bringing its workforce AR platform to iPhones and iPads via a native app.

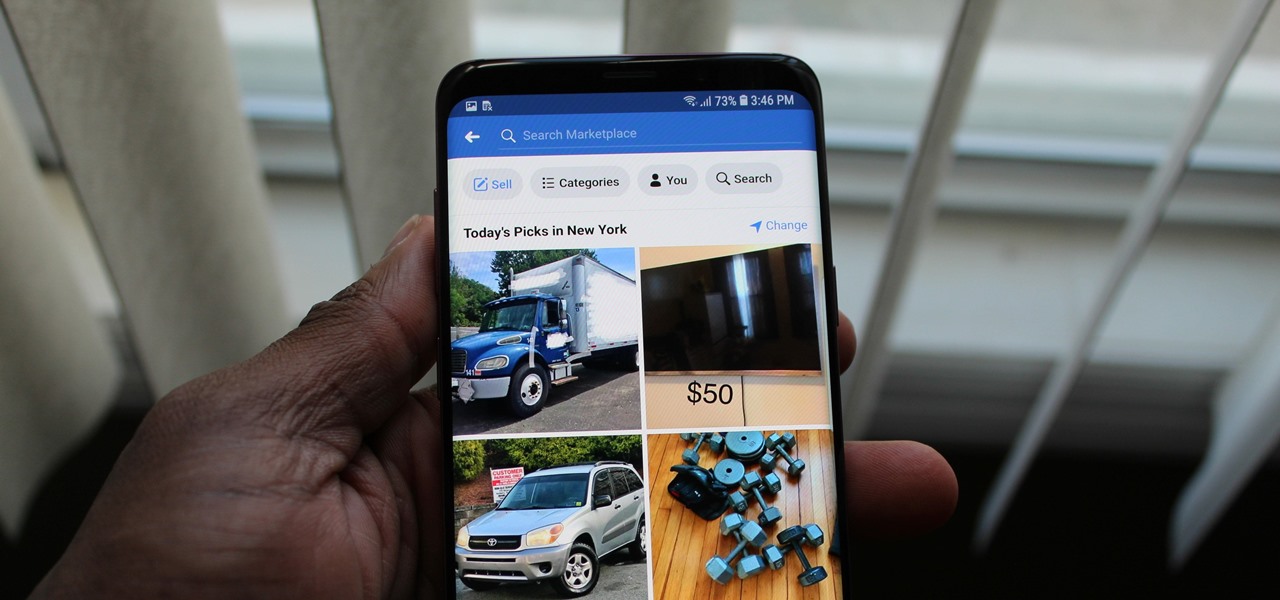
While many of Facebook's tools are well received as they enhance the experience, one which is often complained about is the Marketplace. The Craigslist-like feature which offers a way to facilitate transactions between users can be a little overbearing with its alerts. However, you can change that.

Despite the hype and potential of immersive computing, the augmented reality industry is showing that it is not invincible, as another AR hardware maker, this time Osterhout Design Group (ODG), is reportedly going out of business.

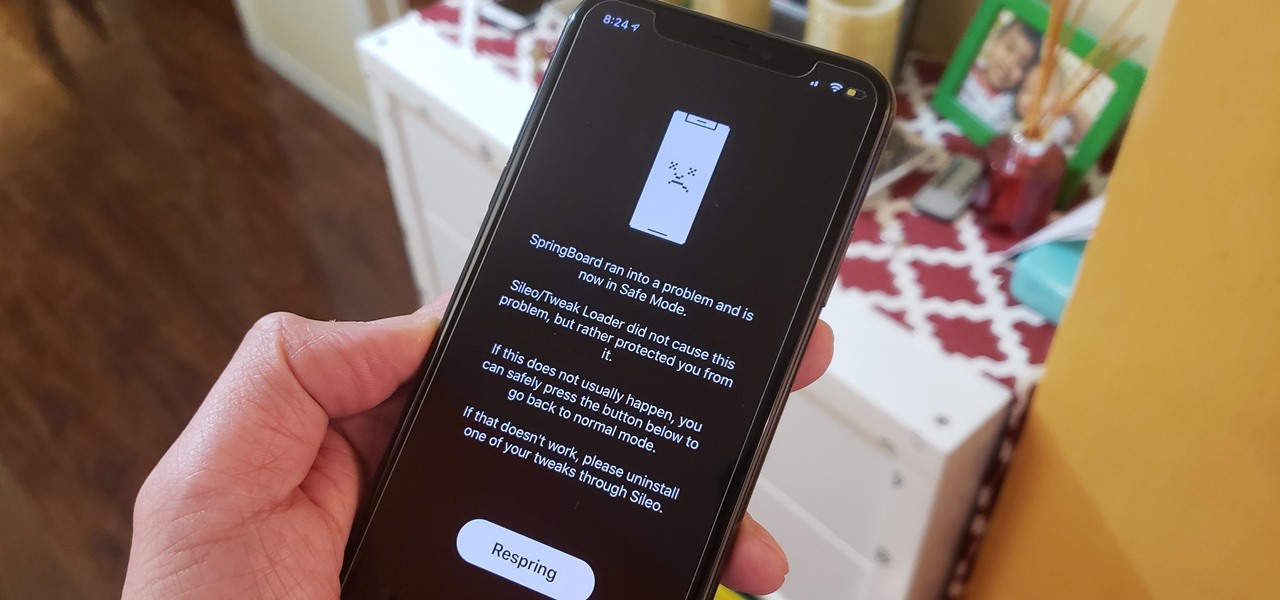
Removing unwanted apps from your iPhone is a straightforward affair — long-press an app's icon, then hit the delete button once it appears. Unfortunately, the same can't be said when it comes to uninstalling tweaks from a jailbroken iPhone.

While iOS 12 is arguably the best iteration of Apple's mobile operating system yet, one major fault so far is security. On Sept. 26, Videosdebarraquito discovered a passcode bypass that gave access to contacts and photos from the lock screen. Apple has since patched that security flaw, but Videosdebarraquito has discovered a new one that affects all iPhones running iOS 12.1 and 12.1.1 beta.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

A couple of months ago, I got the opportunity to get a sneak peek at a new media interface for ODG's R-9 Smartglasses, and the experience was impressive. Now, after weeks of keeping it under wraps, I can finally show off what I saw.

Nokia's calling card used to be camera quality, a small bright spot compared to the black hole that was Windows Mobile. Since Microsoft discontinued the rarely-used operating system, Nokia phones began to run Android — and now, they're getting back to their camera-driven roots with their Pro Camera mode. What's more, you can experience their camera app on any Android phone.

Apple's latest iPhone operating system is notorious for its frequent bugs and glitches. The latest iteration, iOS 11.3, is no exception, as users are experiencing not only 3D Touch issues but missing screenshot previews as well.

Google's AI investment arm, Gradient Ventures, has joined a $10.5 million round of funding for Ubiquity6 and its platform for shared augmented reality experiences, just weeks after Google's GV fund backed a competing AR cloud platform.

With its recent acquisition of 3D gaming engine PlayCanvas, Snapchat parent Snap, Inc. appears to be preparing a challenge to the existing players in the world of game development, particularly in terms of augmented and virtual reality gaming.

Just weeks after officially launching its mobile augmented reality toolkit, Google can now claim one of its first Android and ARCore app exclusives with the Curate app from Sotheby's International Realty.

Magic Leap has reached a major milestone in the lead-up to the launch of its Magic Leap One: Creator Edition by opening access to its developer portal and software development kit (SDK) to all developers.

If you're playing word association with the terms "augmented reality" and "automobiles," your first thoughts probably center on navigation displays in cars or virtual models of exotic vehicles.

Samsung's Galaxy S9 has the best smartphone display among any in its class, beating out the likes of the Google Pixel 2 XL and iPhone X. However, Samsung doesn't unlock the true power of its screen out of the box. To do that, you'll need to rummage through a few settings on your way to maxing out the resolution of your Galaxy S9 or S9+.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

Sure, you just got your Galaxy S8. But now, Samsung came out with their latest and greatest device — the Galaxy S9. While the S8 is still a great device, it's possible that the Galaxy S9 completely outclasses it, almost forcing you to pick it up. It is worth it though? That's a harder question to answer than you may think.

San Francisco-based 6D.ai is preparing to launch a beta of its AR cloud platform that's capable of constructing a real-time dense mesh from crowdsourced data for use in 3D mapping and multi-user AR experiences.

After receiving many requests for the feature, Signal introduced read receipts last year to its mobile apps. However, some users don't like the idea other people knowing when they've read messages. Luckily, Signal lets you disable this feature and reclaim a little privacy.

Medical training technology company CAE Healthcare has given birth to the latest example of how augmented reality can help to build practical operating room skills for doctors and nurses. The company's newest product is called LucinaAR, which harnesses the power of the Microsoft HoloLens.