Each generation of smartphones ushers in a new set of top-of-the-line specs, with processing power, battery size, and display resolution growing by the year. These headlining features get the most press, but there's one unsung hero that has the potential to make the biggest difference when it comes to real-world performance: RAM, or random-access memory.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

The big day has finally come—the new iPhone 7 and iPhone 7 Plus have been officially unveiled. Apple debuted their new flagship devices at a keynote event in San Francisco on September 7, and as we've grown to expect, there are tons of changes in store for the world's top-selling smartphone.

When Microsoft release an update to the HoloLens Development Edition at the end of May, there were a bunch of cool new features added in. Among them: New voice controls that make working in the HoloLens operating system much easier.

I'm an Android user. Over the course of the past seven years, I've owned ten different smartphones—all of them powered by Android. This isn't due to some blind trust in Google or some unfounded hate for Apple, either, because I've always made sure to get my hands on each iPhone iteration along the way to see what it had to offer.

It was definitely a shocker when Microsoft proposed cross-network play between the Xbox One and PlayStation 4 last month. After all, Microsoft and Sony have been competing for the same user base for more than a decade now, and this new feature might actually decrease console sales as a whole.

Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities appear to exist. If they do, it is your job to test whether they are real and can be exploited.

Hello NullByte! This will be my first How To series.

When anyone brings up Tasker, the first topic that always gets discussed is how powerful the Android automation app can be. But all of that power can be overwhelming for some people, so even if you're a Tasker pro, it's hard to share your awesome creations with friends that don't quite understand what's going on.

This year, Google released two Nexus phones to glowing reviews, and as we've grown to expect, the Android community wasted no time in coming up with a root method for both. In fact, legendary root developer Chainfire even devised an entirely new "systemless" method for rooting that should make updating a bit less complicated, along with a few other benefits.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

Google has finally released the next version of the world's leading operating system—Android 6.0 Marshmallow. This latest iteration isn't as much of a visual overhaul as Lollipop was, but it packs in more new functionality than almost any update before it. Awesome features like Now on Tap, granular permissions control, and a deep sleep battery-saving feature called Doze round out the highlights, but there is far more to it than that.

Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just one method.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.

Apple's grand reveal of iOS 8 at WWDC in San Francisco is still a few days away, but that doesn't mean there isn't any speculation as to what features and enhancements might come packed in the new mobile operating system.

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

Apple may have made Mavericks more accessible to Mac users everywhere at the fair price of zero dollars, but unfortunately, they made it trickier to create a bootable install drive of the Mac OS X 10.9 operating system.

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

This video tutorial shows how to use a semi automatic Lego gun (S-22). Learn how to operate and shoot Lego bricks with this semi automatic Lego toy weapon.

We've all seen the breathtaking, colorful photos of the Eagle, Egg and Cat's Eye Nebulae. You may not recognize them by name, but you've seen them, whether in astronomy textbooks, magazines, websites, album covers, or tee shirts. They are some of the most striking photographs ever taken from the Hubble Space Telescope (HST).

As a company, Facebook is not shy about talking up its AR smartglasses plans. The latest missive comes from two executives in charge of developing AR software and hardware.

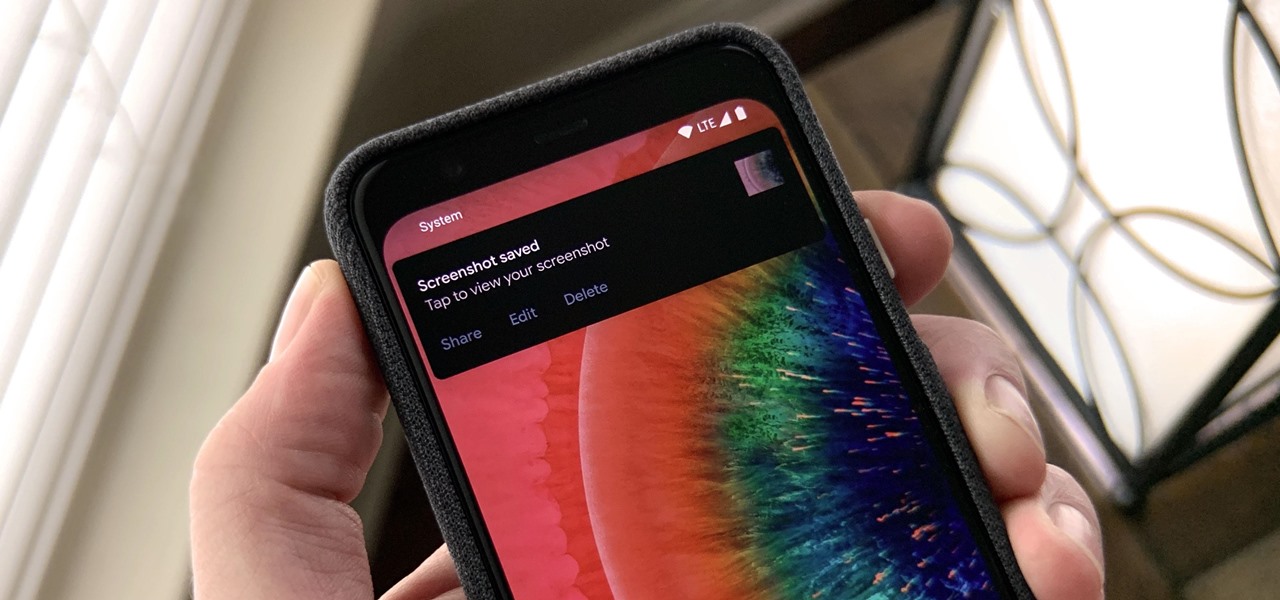
On stock Android 9 and 10, it is easier than ever to take a screenshot and quickly edit the captured image. However, the downside to that convenience has manifested itself in a heads-up notification that can also get in the way.

The still-unfolding story of China's Nreal augmented reality startup continues to develop, with each turn uncovering another unexpected wrinkle.

As a native of Alabama, Apple CEO Tim Cook has a special place in his heart for the state. He also empathizes with the struggles that African-Americans have historically faced in the state, particularly during the 1950s and '60s civil rights era.

The business world is currently figuring out how to deal with the coronavirus crisis, with many offices opting to work remotely for at least the next few weeks as a safety precaution. Predictably, this has thrown remote meeting software back into the spotlight, especially augmented reality solutions.

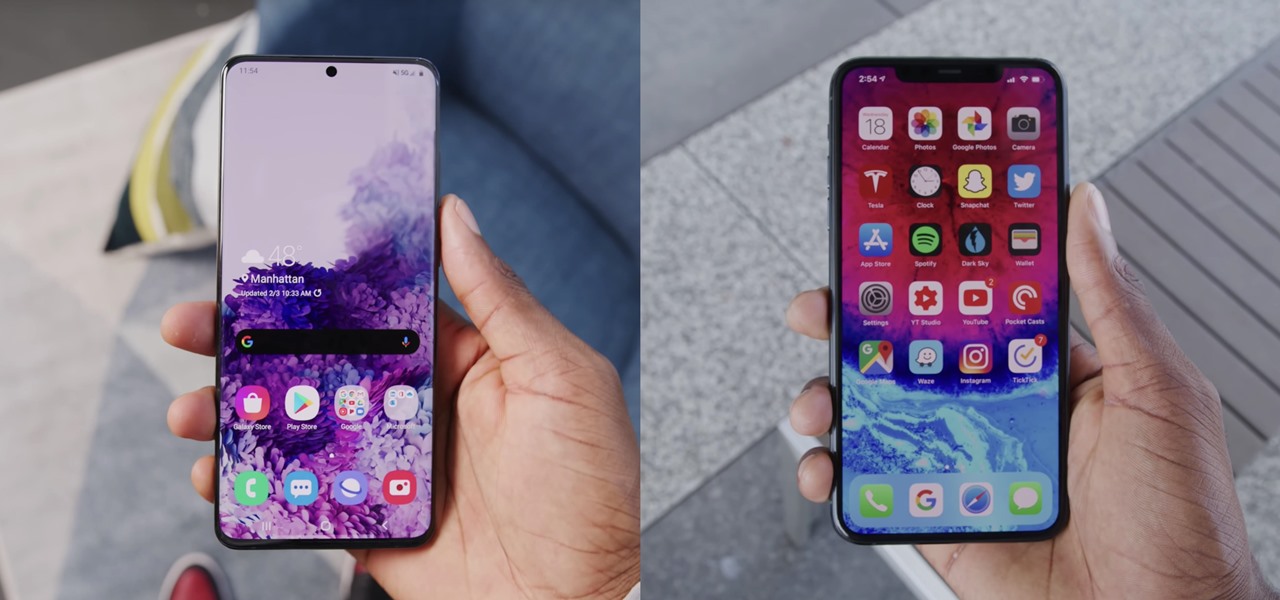
The time to wait for an absolutely killer phone from Samsung is over. They've released a giant of a phone known as the S20 Ultra, and at least on paper, it's a grand slam. But only a few months ago, Apple released its first "Pro" iPhone, and it was giant in its own right. So which is better?

Last December, Google unceremoniously killed off Google Glass Explorer Edition with a final software update, leaving the Glass Enterprise Edition 2 as the only remaining AR wearable from Google.

Some of the leading big tech companies are still working in the lab on actual products, but at least some of their leadership did have some thoughts to share on the future direction of the technology this week.

One of the hallmarks of augmented reality's coming of age is that the technology is starting to find a home in business categories that are less obvious compared to typical AR enterprise use cases.

As the demand for realistic volumetric video for AR experiences begins to grow (along with the available facilities and services for capturing it), researchers at Google have figured out how to improve upon the format.

Adobe is best known for its photo and video editing software, but they also have a number of lesser-known apps that you may be interested in. Adobe Fill & Sign, available on iPhone and Android, is the best way to electronically fill out important documents on your smartphone with a third-party app.

With the imminent arrival of the HoloLens 2 expected any day now, Microsoft is preparing new users to take advantage of its software from day one.

Apple revealed its newest line of iPhone models on Tuesday, Sept. 10, at its "by innovation only" event in Cupertino. While the release date for iOS 13 wasn't announced at the event, Apple issued a press release with the date. If you missed the event, you can still watch it from your computer, smartphone, Apple TV, and any other device that YouTube works on.

Until Star Wars-style 3D hologram projection technology becomes commonplace, the near future of certain kinds of remote work is in robotics. Now, a new dynamic is using augmented reality to give this kind of telepresence a kind of superpower.

The augmented reality space is brutal, and that means shifting directions quickly to meet whatever need the market demands.

In iOS 13, Apple is taking the Reminders app more seriously. With its long list of helpful new changes, the app finally stacks up to other task managers like Todoist or Wunderlist. One of the changes is small but mighty — the ability to add custom icons to lists. Doing so lets you personalize each collection of reminders to your liking and can help you identify lists with just a glance.

Years ago, in 2013, Occipital introduced its original Structure Sensor for iOS, a mobile 3D scanning device for measuring three-dimensional objects. Soon after, in an unrelated deal, Apple acquired PrimeSense, the company that made one of the components for Occipital's scanning device.