
How To: Hunt Down Wi-Fi Devices with a Directional Antenna
If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.


If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

You've just picked up your new Samsung Galaxy S20, S20+, or S20 Ultra — but wait. After you turn it on and restore your data, there a few apps you should install to get the most out of your updated phone. Installing these eight apps right away will help maximize your experience from the very beginning.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

The USB Rubber Ducky is a famous attack tool that looks like a USB flash drive but acts like a keyboard when plugged into any unlocked device. The Ducky Script language used to control it is simple and powerful, and it works with Arduino and can run on boards like the ultra-cheap Digispark board.
You watched the live stream, pored over the specs, and are now super excited for the Google Pixel 4. But specs don't tell you everything. After using the Pixel 4 XL for over a week now, we've found several things you wouldn't know without getting your hands on the phone.

I already know what you're thinking: this guide is blasphemy. I am showing you how to turn a Galaxy Note 10 or 10+ into an iPhone 11 Pro Max. And while I'd usually agree with you, hear me out. How can you know you don't like something until you try it? So here is your way of trying out an iPhone using your Galaxy Note 10.
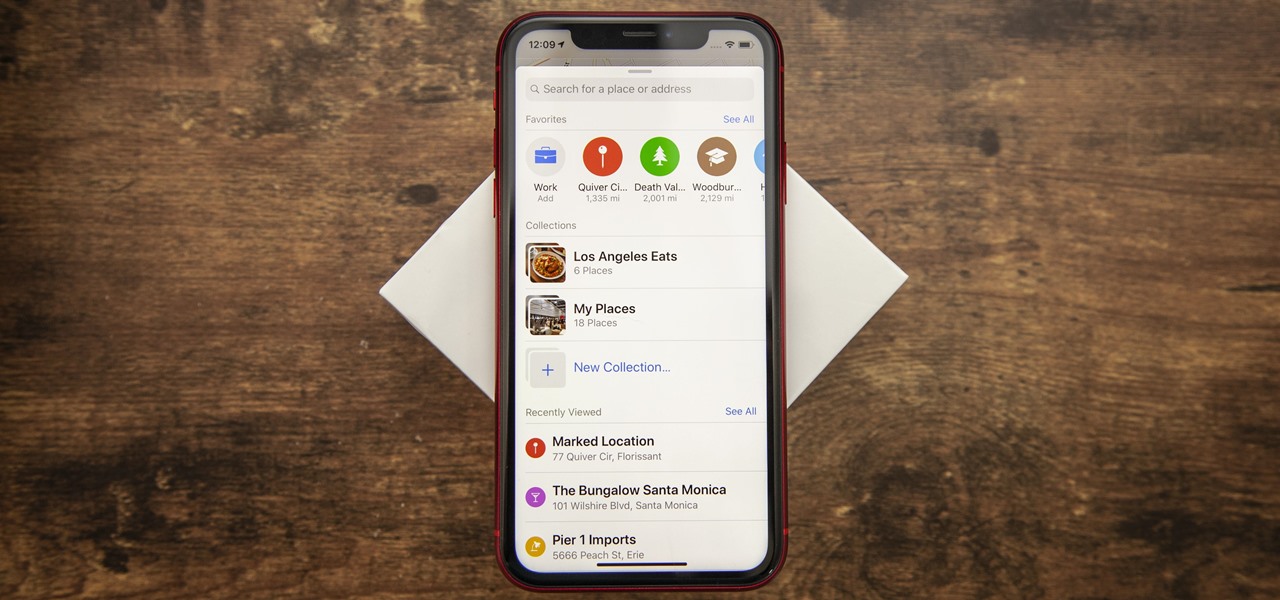
Apple Maps has had a rough lifecycle. After completely dropping the ball during its inception, Apple has been slowly improving its usability and feature set. After six and a half years, users still prefer third-party apps in iOS 12 over Apple Maps, with Google Maps stealing a large 67% market share. But iOS 13 for iPhone may finally close the gap.

If you've ever used the Find My iPhone and Find My Friends apps in iOS 12 and below, you may be surprised to hear that those apps have joined forces in iOS 13. Now, instead of two separate apps, they're combined into one convenient package. But what does that mean for you and your privacy and security?

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.
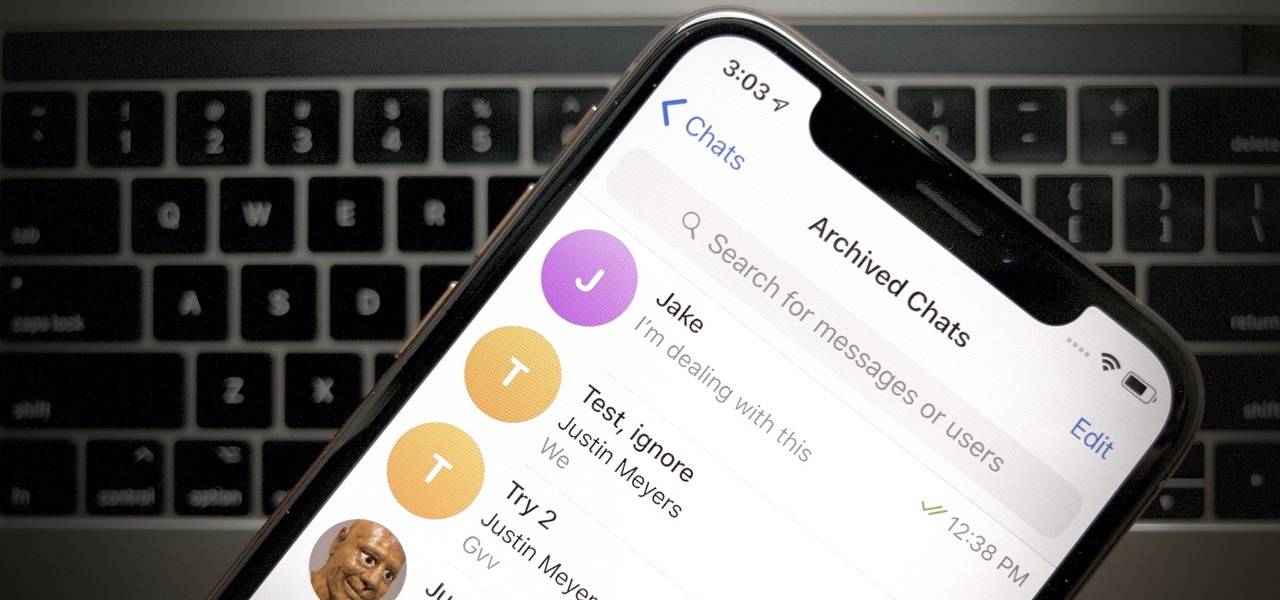
In Telegram — as with all instant-messaging apps — threads and conversations can pile up quickly. But you don't need to stare at all of your open chats on the main screen of the Android and iOS app. Instead, you can archive any conversation you like, keeping your main chats view relevant to your day-to-day communications without needing to delete any for good.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.
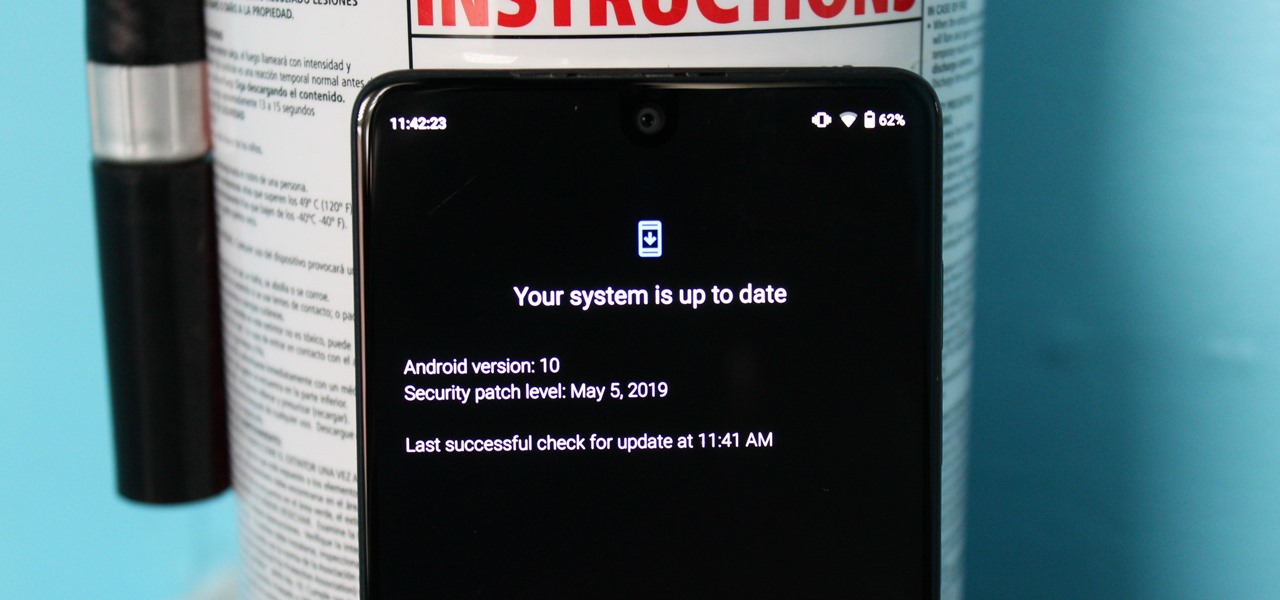
Like last year's beta release of Android Pie, Google has allowed the Android Q Developer Previews to support some non-Pixel devices. Announced at Google I/O 2019, there are 15 non-Pixel smartphones eligible for the Android 10 Beta, including 2017's Essential PH-1.

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.
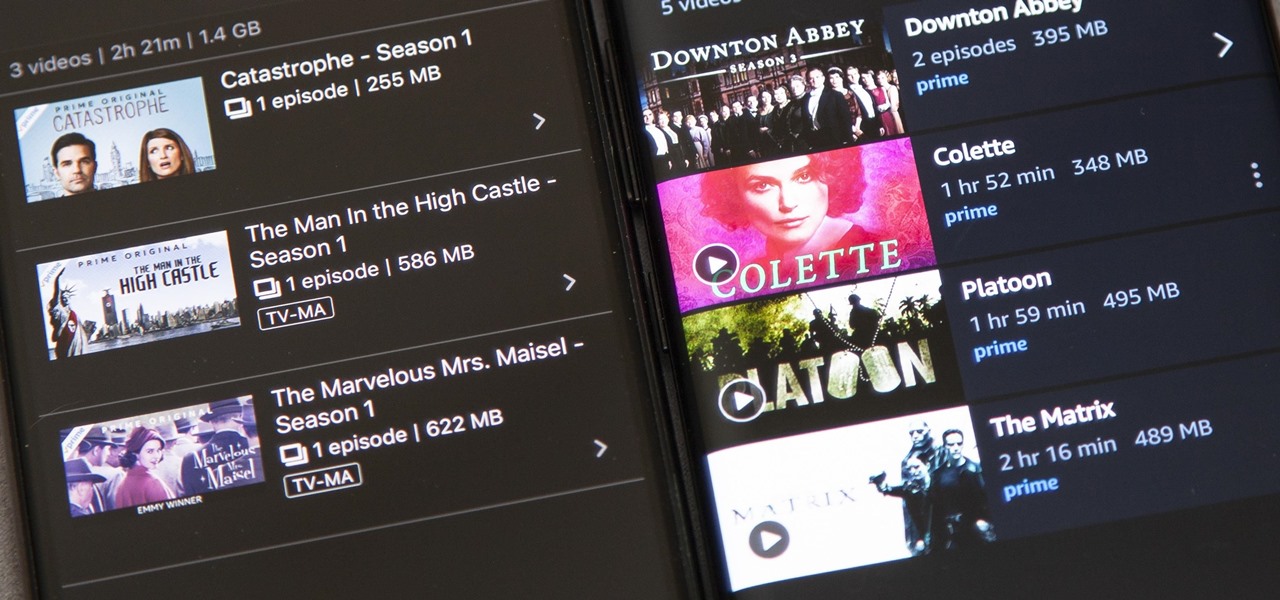
Back in 2015, Amazon Prime Video was the first subscription-based streaming service to introduce the ability to download movies and TV shows for offline viewing on mobile devices. For travelers and users with limited data plans that like to watch films and episodes on the go, this was a godsend. Amazon has updated its apps many times since then, but the process remains relatively the same.

If you've ever spent any serious time examining the Chinese tech startup world, you know that it moves fast — very fast. The tech startups hailing from Beijing and Shenzhen are moving so fast that they're now in serious competition with Silicon Valley.

For lack of a better word, a missing iPhone sucks. Not only do you lose a physical device that cost you a small fortune, but there's also the probability you'll never see your precious data again. Hackers and thieves might, just not you. To keep this from ever happening, there are preventative measures you should take, and the sooner you do them the better.
Similar to last year, LG is mixing up its releases. Instead of the G series in the first half of the year and the V series in the second half, LG is releasing both heavy hitters together. However, unlike last year, this is a true upgrade from its predecessor, the LG V50 ThinQ 5G.

By now, there's no way you haven't stumbled upon a TikTok video, whether it was on Facebook, Instagram, Twitter, or YouTube. Just watching these addictive short-form videos is enough to make you want to join up and make your own, and when you do, we've got some tips that will help get your TikTok account in order.

We recently set out to find the best phones for people whose primary usage revolves around social media apps like Facebook and Instagram. Samsung, Apple, and Google were the three brands that made our top five, and while the latter only had one finalist, the two bigger OEMs had a pair of phones each. What struck us, however, was that Samsung's phones edged out Apple's not once, but twice.
When Facebook introduced Stories in 2017, many users despised the Snapchat-like feature on their main page. However, despite the outcry, Facebook doesn't plan to let you remove it. But you don't have to settle for this. With the help of some third-party apps, you no longer have to deal with Stories.
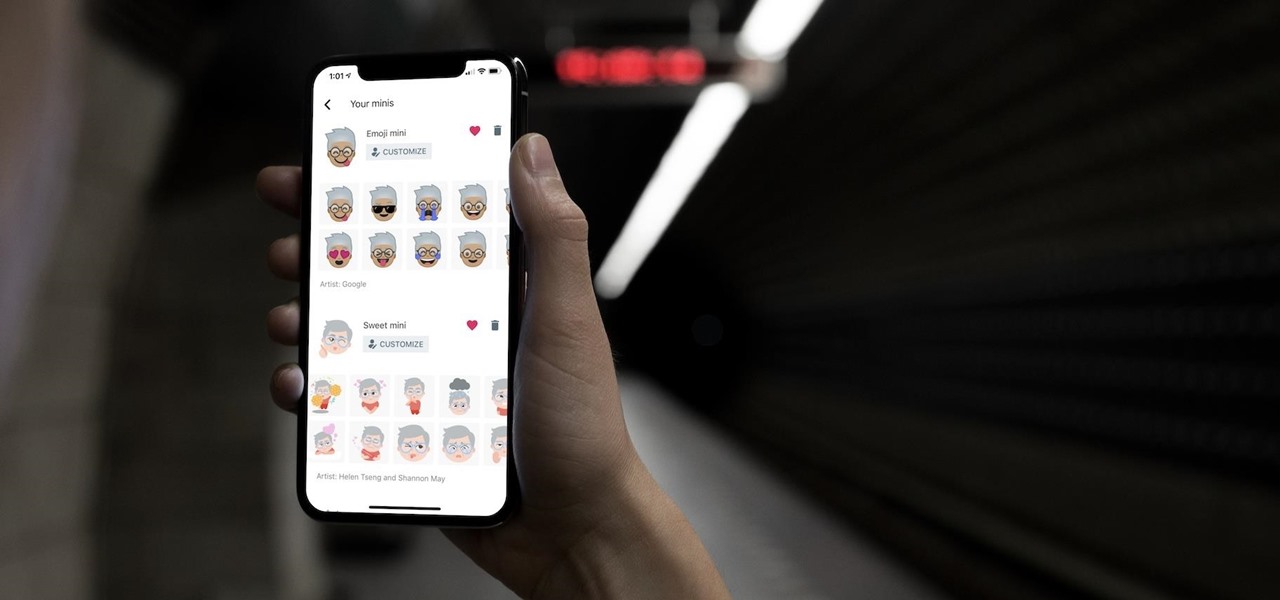
Expressing yourself during chats is much easier these days thanks to the steady rise of emoji. Now, products like emoji Minis for Gboard are taking the craft to an interesting yet familiar new level. With emoji Minis, you can automatically create stickers based off your own face. From there, you can further customize the stickers by adding key features such as glasses, earrings, and facial hair.

These days, it's easy to cut the cord. Thanks to a new crop of streaming TV apps, you can get the same service offered by a traditional cable subscription at a fraction of the price. After some extensive testing, we believe we've found the absolute best apps for cord cutting.

Google's next-gen cellular carrier, Google Fi, which replaces Project Fi, is making waves across the mobile industry. With super-cheap plans starting at only $20 and the ability to connect to millions of Wi-Fi hotspots across the globe, it's tempting many users to make the switch from AT&T, Sprint, T-Mobile, and Verizon Wireless.

Everyone from first responders to hotel cleaning staff use radios operating in the sub-megahertz range to communicate, often without even encoding the transmission. While encoding and encryption are increasingly used in radio communication, an RTL-SDR adapter and smartphone are all it takes to start listening in on radio conversations happening around you.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.
Rooting usually means sacrifice. With most root methods, you lose access to apps like Netflix and Android Pay when SafetyNet gets tripped. More importantly, you lose the ability to accept OTA updates, forcing you to manually flash new Android versions. But there's a way around all of this if you root the right way.

While many are familiar with Samsung, I'm pretty sure most Americans couldn't name the second-largest smartphone OEM. It's actually Huawei, and they recently released a spec-sheet dream of a phone in the Mate 20 Pro. So naturally, we wanted to see how it compared to the largest OEM's best offering.
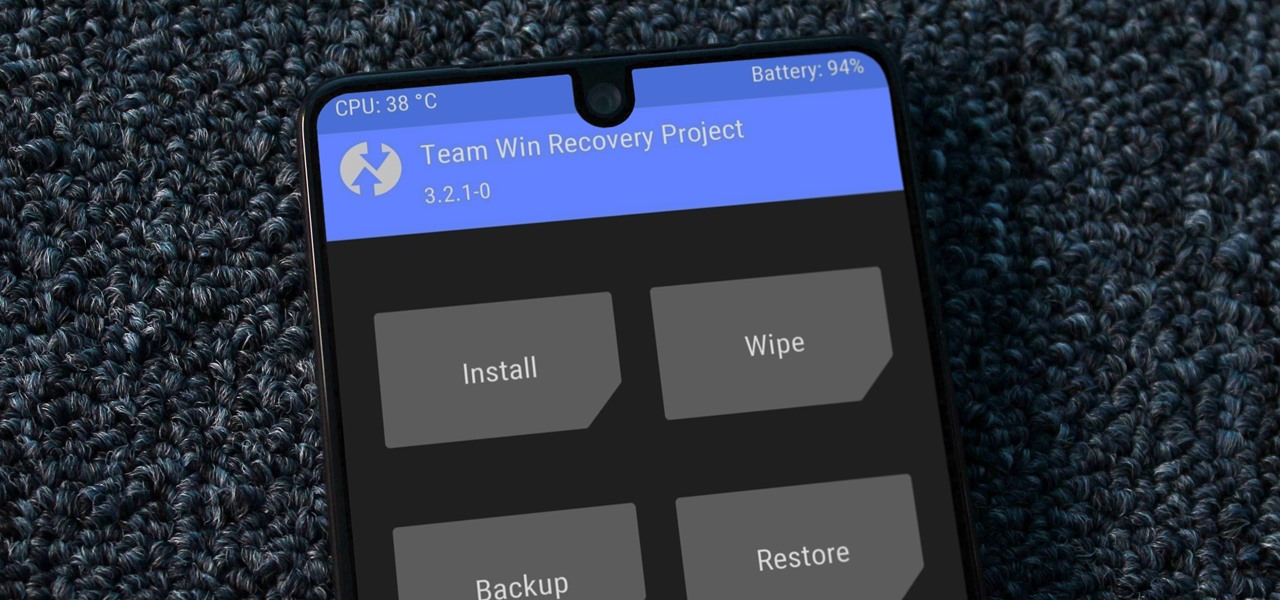
For modders, there are few tools more important than TWRP. TeamWin's custom recovery makes flashing mods like Magisk, Xposed, and custom ROMs incredibly easy, and it lets you root your phone at the press of a button. On top of that, it can make complete backups of your phone in case you mess up. That's why, for Essential users, this should be the first mod you add.

While the iPhone XS actually comes with a smaller battery than the iPhone X, Apple claims it, along with the XS Max and XR, offer users longer battery life than last year's first Face ID model. While that may be true, your new iPhone still ships without meeting its full battery-saving potential. There are, however, steps you can take to make sure your X, XS, XS Max, or XR makes it from morning until night.

If there's been one signature design element for Apple's iPhones, it was the circular Home button. It served as the "everything" button for each iPhone model until last year's iPhone X, but now, it's completely absent from the iPhone XS, XS Max, and XR. Should you be worried? Short answer: No.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

I was in college, and my 15-inch Sony Vaio laptop was my prized possession. It was my first PC and probably the most important thing I brought with me to my dorm — it was both how I completed my assignments and my primary source of entertainment. How could it turn its back on me in my time of need?