
Listen up, children, pregnant women, and lightweights: this particular KitKat variety is not for you. Well, with 0.8% alcoholic content per 2 KitKat bars, it's highly unlikely anyone will actually get drunk on these things. Still...

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.
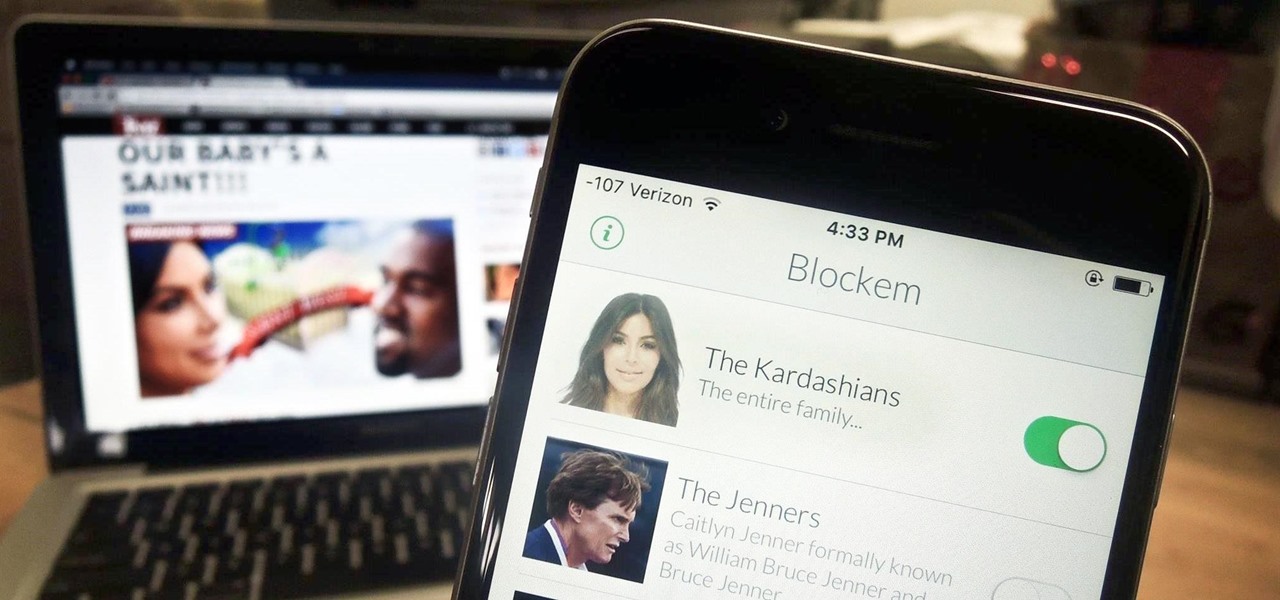
Kim Kardashian and Kanye West have fittingly named their second child "Saint," but I'm sure you don't care about that—and neither do I. Unfortunately, regardless of our pop culture interests, we're forced to know these types of stupid facts because the internet is so densely populated with Kardashian-related content that it's impossible to avoid. It's enough to make you puke.

With over 10,000 possible combinations, a four-digit passcode may seem secure, but it's fairly easy for someone to crack your code—no matter how clever you think it is. Luckily, there are many other options for securing your iPhone's lock screen—especially if your running iOS 9.

Fall is the time for comfort foods—and what is more comforting than crusty bread slathered in melted cheese? Owning a fondue pot is both convenient and wonderful, but not all of us have the luxury of space for nonessential kitchen appliances. However, there are plenty of ways to make an absolutely delicious, lump-free fondue without the traditional equipment.

Often, despite your favorite makeup mecca's rows and rows of endless colors, applicators, and brands, it's hard to find the perfect shade of lipstick—especially one at the price you want. Rather than resorting to what's available in stores, turn to your stovetop and a box of crayons.

Whether you are sending your phone in for repairs or finally selling it to upgrade to a new flagship, you are going to need to make sure all of your personal data is removed from your device.

You can beef up the security on your Mac all you want, but all the firewalls and antivirus apps in the world mean nothing when that can of soda tips over on your Macbook, destroying your laptop and all its data forever.

There is a huge myth that most Americans believe, and it might be the marketing triumph of the 20th century. We pay an absurd markup (Zero Hedge says as much as 280,000% for "designer" water) on something we can get for free because most of us believe that bottled water is healthier than tap water. But is it? Here are 5 reasons why tap water is probably better than that bottled stuff you drink. 1. It's Not Cleaner (& Might Be Dirtier) Than Your Tap Water

Saying that I was obsessed with Pokémon as a child would be a serious understatement, and even though I'm not the Pokémon fanatic I once was doesn't mean I don't love playing still. However, I do often find myself dumbfounded by all of the new features and characters in each generation.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

At last, what you all finally waited for! Hi! Fire Crackers,

Meet the Wonderbag. The "first non-electric slow cooker" uses an insulated bag made of poly-cotton fabric, polyester, and repurposed foam chips. You bring your one-pot meal to the desired cooking temperature, usually via the stovetop. Then you turn off the heat, pop the pot into the Wonderbag, and it will continue to cook thanks to the retained heat in the bag.

After you have registered to this site,sign in then to start missions. Basic Missions

bObsweep Standard and Pethair are made to easily transition between a variety of floor types, so they function efficiently in most spaces.

If you're feeling stressed, there are many home remedies you could use for relief. Meditation, yoga, acupressure, an ear massage, more sleep, shower soothers, playing video games… the list is endless. But a lot of these methods require a significant amount of time, so what do you do when you need immediate stress relief?

There are tons of greasy drippings that can be used to flavor up any dish, but none will ever be more delicious than animal fat. The bigger and fatter the animal, the juicier and tastier their fat is. For those of you who have had your fill of bacon-anything, here's your next obsession. It's called caul and its very existence will divide those that are serious about their animal fat flavoring from the pretenders.

No one ever wants to experience pain, whether it's as small as a stubbed toe or as great as recovering from surgery. Yet so much of our lives causes pain, lasting or brief in its form. With a few mental tricks and unusual home remedies, you can relieve some of the most common aches and ailments that arise painlessly.

Even if you've put aside your percolator and have gone the way of the pod coffeemaker, there are still dozens of ways to use your leftover coffee filters. Incredibly cheap, absorbent, and shaped with a ruffle, coffee filters are useful in the kitchen, garden, and around the house.

We are living in a golden age of craft beers. Originally invented by the ancient Egyptians, every culture now has its own tastes regarding beer. The process of making beer is so multi-faceted, it's a miracle that any gets made at all.

A little cooking mistake can lead to tough meat, spoiled food, and even a bacterial explosion in your kitchen if you're not careful. These five simple, easy-to-fix kitchen mistakes are some of the most commonly made in households around the world. Luckily, you can correct these innocent errors with just a few minor tweaks.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

Apple Pay has been available to use in stores, as well as in select apps and websites, ever since its first appearance in iOS 8.1. Now, with iOS 12, there are currently 13 different iPhone models that support Apple Pay functionality without the use of an Apple Watch, and the list of partnered stores that accept Apple Pay has only grown. Here's our always-up-to-date list to keep you in the know.

Every season of American Horror Story introduces characters who are truly terrifying. From the witches of Coven to the ghostly resident of the show's first season, each new chapter of the TV series offers a host of ghoulish and ghastly costume ideas perfect for scaring children on Halloween. Some grisly characters even span multiple series.

Amazon just announced its entry into the set-top streaming content marketplace with its new Fire TV box. Competing directly against Apple TV, Google's Chromecast, and Roku, Amazon is betting on big processing power and voice controls to stand out from the competition. Features include the following.

While we've already covered several good ways to tame the itch of a mosquito bite, you're much better off preventing them from biting in the first place than dealing with the itchy aftermath.

Applying for jobs can be a truly miserable experience. Sending out endless résumés, filling out those janky online applications, and creating cover letters can really wear a person down. So, any suggestions that make that process easier are always welcome.

With the the general computer users understanding of Information security rising (at least to the point of not clicking on unknown links), and operating system security getting better by default. We need to look for new and creative ways to gain a foothold in a system.

The Problem If you are working on a car restoration project, then you are going to faced with rust damage. This problem can’t be overlooked, as the entire project depends on repairing and eliminating rust. This would be like laying down new carpet to a house that was flooded, without cleaning the mess and making necessary repairs before laying the carpet down. The problem will still be there and the new carpet will be ruined.

I miss the days where my hardest assignment was drawing a Thanksgiving turkey using the outline of my hand and trying to stay in between the lines. It seems that there is some unwritten rule that adults shouldn't feel the need to draw. Well, not anymore.

You probably already know what you want to do when you grab your phone. More than likely, you're either going to make a call, send a text, or open an app. So why can't you just do that right from your Samsung Galaxy S3's lock screen?

Back when I was a kid, I didn't get many awards or trophies, aside from perfect attendance three years in a row. If only there was an award for procrastination. While there are apps out there for my iPhone like Clear and even the stock Reminders app, they still don't push me hard enough to get things done on time—or at all.

There's no reason to wait for Halloween to play with dry ice. It definitely creates a creepy fog-like effect when you add a little water to it, but there are some other really cool things you can do wit dry ice. Here are just 5 non-Halloween ways to use dry ice for tricks or pranks.

Nine times out of ten, when you pick up your Samsung Galaxy Note 2, you already know what app you're going to be using. If you only have Swipe to unlock enabled, finding that app is as easy as swiping and locating the app on your Home screen or in the app drawer.

Mixing water and electricity is extremely risky and potentially lethal, yet that's exactly what I did with the Scariac. In its simplest form, the Scariac is just a glorified version of two wires in a bucket of water, but it's actually one of the cheapest power controllers you can make.

For this project, I sacrificed some of my kids' clothes and a can of tuna to make some high-quality fire starter! Here's how to make a great batch of char cloth to add to your emergency survival kit.

In this video, I show you how to build tinfoil cars for crushing with toy Monster Trucks. My son Eston and I love monster trucks. One of the most exciting things when you go to see monster trucks live, is when they crush cars. Problem is, when you use your hot wheels or matchbox cars with your monster trucks, they don’t get smashed. So the realism isn’t there.

Life has many perils: parasites, predators, and pitfalls. Eventually, any organism will succumb, and if that organism has not first passed on its genes, those genes will face extinction.

Anyone that has ever watched a member of the opposite sex play a video game knows that the other gender does it wrong.

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.









































