I have been getting requests for this one since a really long time. So finally a few days back I decided to step up and create a video on nail care and help lots of girls out there who are facing nail issues on a daily basis.

A few weeks ago, Twitter announced that they would be creating an archive feature for its members, which they've been slowly rolling out to select users. After signing in today, I noticed the feature was finally available for my account, so I went to test it out.

Forgot the passwords to your email or your other favorite websites? If you typically store your passwords in Internet Explorer (IE9 or other versions) it can be tricky to get your passwords back -- but this tutorial makes it really easy!

It seems like every other day there's a new security threat or data leak in the news. Whether it's your credit card PIN or your smartphone's apps leaking your email address, no one wants their personal information out there, especially passwords. And if you use the same email address and/or password for more than one site, the effects of someone getting hold of your credentials can be catastrophic.

Over 2 million people are anxiously awaiting the arrival of their new iPhone 5, which has caused a few shipping problems, to say the least. There has been a considerable amount of confusion about when, exactly, the iPhone is going to ship, depending on where it was bought and how it's being delivered.

One of the biggest advancements in the new iPhone XS, XS Max, and XR is the dual SIM functionality that will let you use two cellular networks at once. Like Sinatra, however, Apple is known to do things its own way, so their dual SIM setup is a bit different than you might think.

If you've been getting that "Please update from the iOS 12 beta" alert continuously in iOS 12 public beta 9, Apple just issued a fix for it Friday, Aug. 31, with iOS 12 public beta 10 — just in time for Labor Day weekend. This marks the second update this week as dev beta 11 and public beta 9 were released on Monday. It's also just one day after Apple announced its Sept. 12 event.

In a surprise twist, Apple released iOS 12 public beta 8 to software testers on Thursday, Aug. 23, right alongside iOS 12 dev beta 10. The release comes as a bit of a shock, as the company released iOS 12 public beta 7 just three days earlier. The official build of iOS 12 now feels closer every day.

The bacteria in our gut — a community called the gut microbiome — have been in the spotlight a lot lately. What we're learning about how our intestinal bacteria adapt and grow with our bodies could help athletes perform better, according to researchers starting a company focused on creating probiotics that mimic athletes' microbiomes.

During the millions of years they've been on earth horseshoe crabs have developed a trick that can save our lives even now — and may be especially useful in the fight against healthcare-associated infections.

While no longer native to the United States, hospitalization from malaria occurs in this country more than most would believe. Why is that, and what can you do to protect yourself when you travel abroad to regions where malaria is active?

Humanity is standing on an infection precipice. As antibacterial resistant grows, we're running out of options, and a recent scary case of total antibiotic resistance is a frighting view of our potential future. In the end, it was septic shock that took the life of a 70-year old woman with an incurable infection. One of few such cases in the US, her death could nonetheless be the shape of things to come.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

What separates the work habits of the ultra-productive from us mere mortals struggling to check items off our never ending to-do lists? While the answer to that question is by no means simple, one undeniable factor in their success is a clearly defined, highly organized workflow.

Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.

This video is on how to install the LED light kit onto your Axon Racing anti-gravity razorback racer hover.

You’ve put in the work to grow wonderful greens in your garden and your ready to make a tasty salad. When you are ready to use your greens you can cut just a few of the outer leaves off at a time so the plant can continue thriving.

Snails can have a devastating effect on your garden but there are ways without using toxic chemicals to get your snail problem under control. You can use pick snails off by hand and throw them away, you can put out iron phosphate based bait, or you can put a bowl of beer out which they will be drawn to and away from your garden.

It is important to use mulch in your garden if you wish to slow the evaporation of water and keep your soil moist longer. Mulch looks nice and is helpful to put around newly planted plants. four to six inches of mulch will allow you to water your plants less.

Research says babies are comforted by scents associated with their mothers. Fragrances baby experiences with you regularly will remind her of you even when you're not right by her side, providing a feeling of comfort and "home." You can comfort your baby with just your scent with the tips in this how to video.

Train your dog to walk politely at your side. Choke chains and other forms of negative reinforcement might make the dog associate being by your side as a bad thing, but positive reinforcement techniques will keep both the dog and pet owner happy. Watch this video pet training tutorial and learn how to teach a dog to walk on a leash.

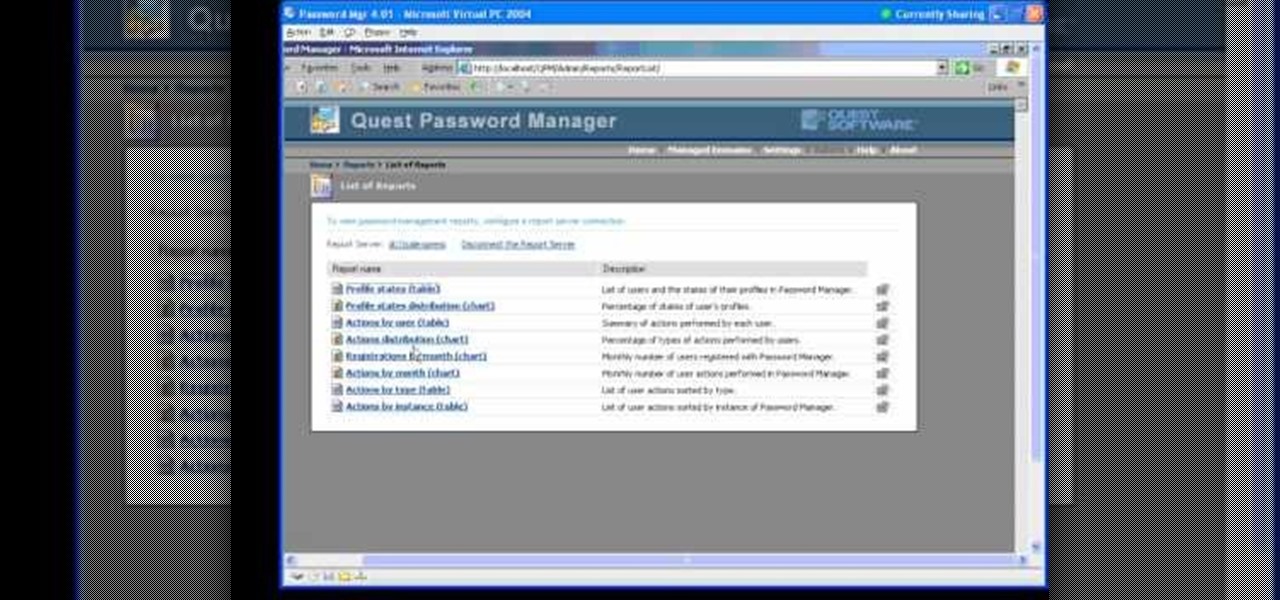
In this Webcast, Password Management for Windows and Beyond, you will learn how to: Increase security standards cross-organization by easily customizing and enforcing password policies for Windows, Unix, Linux, and Java users.

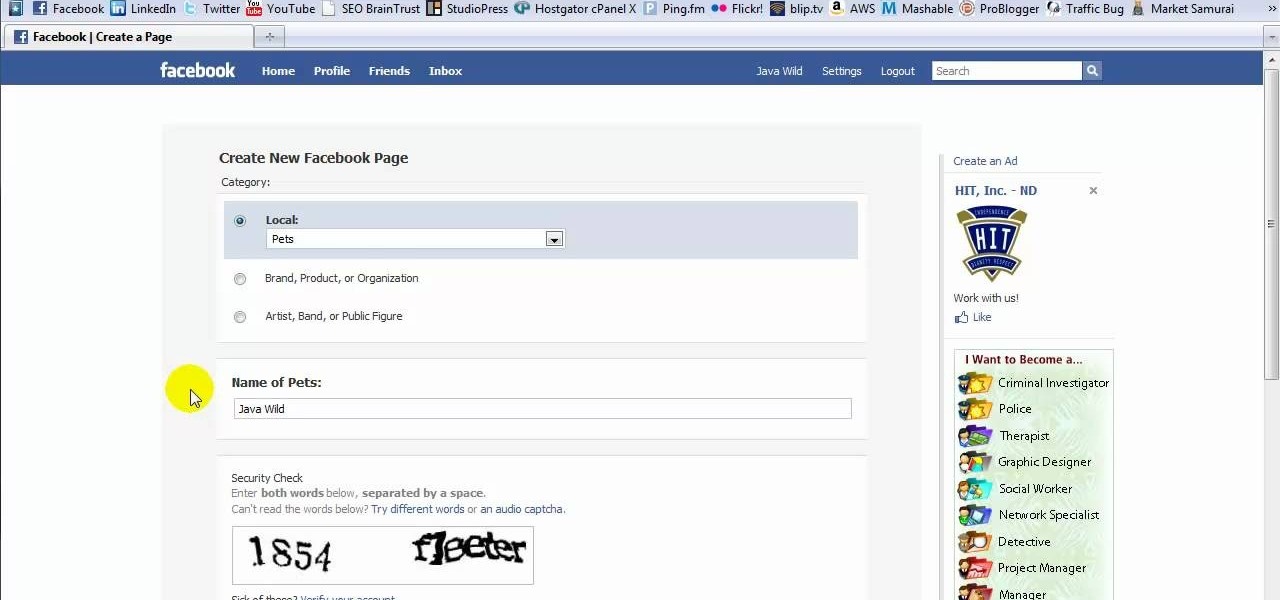
This tutorial is in response to mail to Facebook. Scott Wilde leads you through the process. You can start by creating a brand new profile page. In this case, Mr. Wilde created a profile page for his dog Java Wilde so he could have a fresh new page without having to alter his initial profile page. Fan pages are different than your base profile. Your base profile is not indexed, it is not public, it is private and limited to 5000 friends. A fan page is unlimited up to millions of fans and it c...

This video is on how to setup the axon racing anti gravity razorback racer. it involves receiver installation, zeroing your servo with the trims and lifting the horn, programming the esc, installing the lipo, testing the unit, initial turn on.

Congratulations, you've made it deep into the middle of flu season! If you're reading this, you're either a very smart preemptive sick day prepper, or already in the throes of fighting off a cold or flu situation.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

Apple developers, check your iPhones — Apple released the eighth developer beta for iOS 12 on Wednesday, August 15. This update arrives just two days after the release of dev beta 7, which Apple quickly pulled after complaints of unusual performance and stability issues.

It wasn't Christmas, but for Amazon Prime members, it was darn close: Amazon Prime Day, one of the biggest shopping days of the year, came and went earlier this week. Unfortunately, there weren't many Prime Day-specific deals to be had for augmented reality fans, but that doesn't mean AR-loving Amazon Prime members were completely left out.

In what's becoming something of a regular occurrence, Magic Leap has yet another internal, unforced error on its hands. Thankfully, this time it's not about legal skirmishes or theft, but a rather unusual break from company protocol that has been quickly swept under the rug.

On Friday, audio giant Bose emerged as the latest, and perhaps the most surprising company to announce that it's planning to release augmented reality smartglasses.

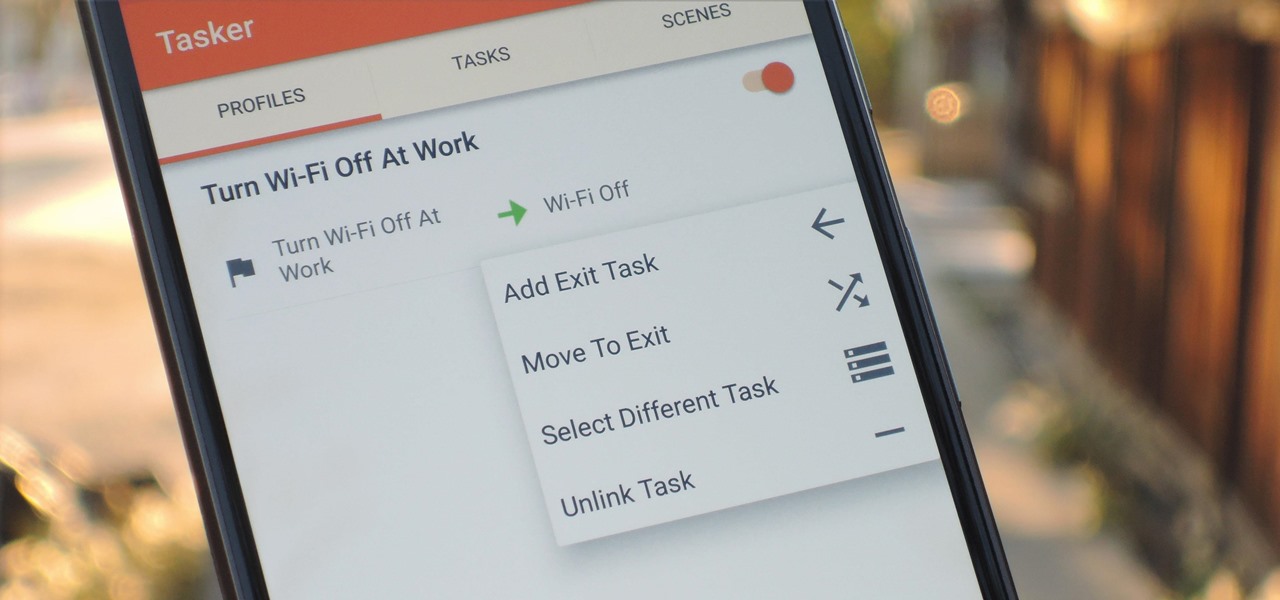
When you create a profile in Tasker, it will run a task as soon as all of the conditions in your profile are met. But what happens when the profile's conditions stop being met? By default, nothing will happen, but if you create an exit task, the automation tool will run that instead.

Most Android launchers limit you to three choices: Icons, widgets, and folders. It's better than nothing, but it's still pretty hard to find the best look without overcrowding your home screen. You could fill everything up with icons, but then you'd have an iPhone. You could toss everything into folders, but that would always require an extra tap. You could mix in some widgets, but that would take up valuable space. So what do you do? Action Launcher has the answer.

How can a drug used to treat cancer be effective against viruses, too? The answer lies in the drug's shared target — specifically, cellular components that control the activity of genes. A new research study showed that one such type of drug, histone methyltransferase inhibitors used in cancer clinical trials, has activity against herpes simplex virus, too.

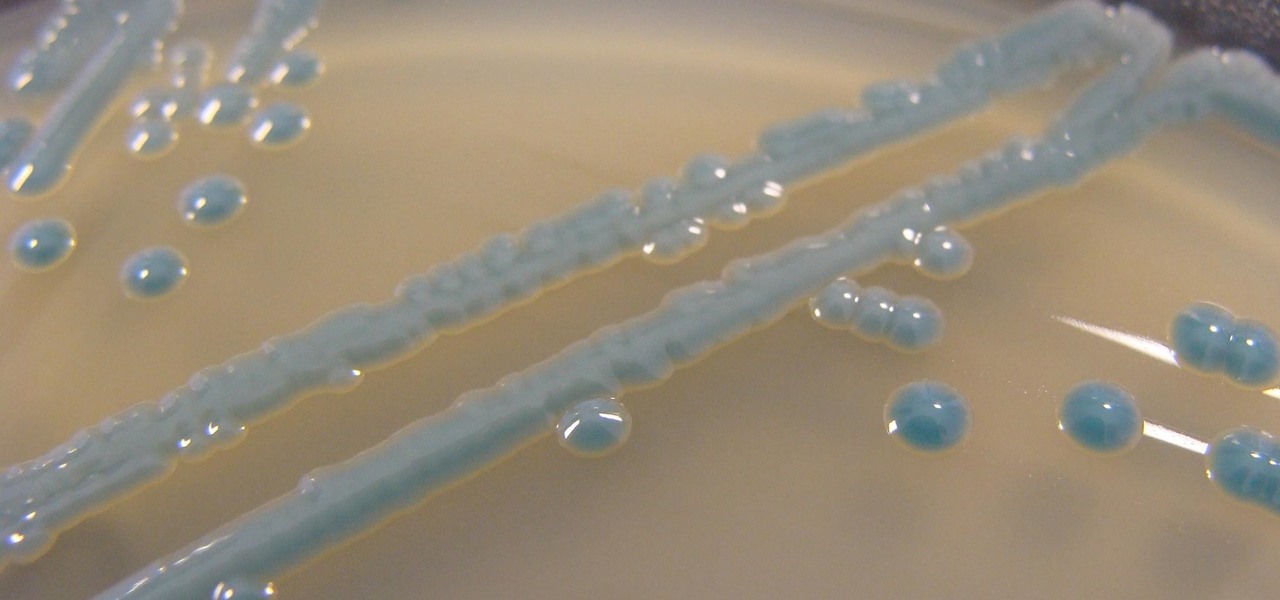
The growing list of dangerous antibiotic resistant organisms has just acquired three new members. Researchers have discovered three new species of Klebsiella bacteria, all of which can cause life-threatening infections and have genes that make them resistant to commonly used antibiotics.

The fatal crash of Air France Flight 447 is one of the most tragic accidents in avionic history — while it also serves as a stark reminder of what can go wrong when humans rely too much on driverless vehicles.

Wherever there are people, the party is sure to follow. Well, a party of microbes, at least. That is what scientists at NASA's Jet Propulsion Laboratory have found after a 30-day microbial observation of the inflatable lunar/Mars analog habitat (IMAH).

Foodborne infections often occur through the contamination of equipment, food-prep tools, and unsanitary surfaces. A recent report from the Centers for Disease Control and Prevention (CDC) reminds us that breast pump parts are part of the food-delivery chain — and they can become contaminated too.

Twelve-year old Rory Staunton took a dive for a basketball during gym class and came up with a cut on his arm. The school nurse applied a couple of band-aids, without cleaning the cut, and off he went. In approximately three days, hospital physicians told his parents there was nothing else that they could do for their son; he was dead.

Despite longer live spans, almost half a million people die of healthcare-associated infections (HAIs) each year, many of them preventable.