When it comes to making pancakes in the morning, most of us probably follow the instructions on the box. Mix all the ingredients together, pour onto a hot greased pan, and form perfect circular flapjacks one by one.

Icebox cakes are some of the most satisfying, easy desserts to put together. This version made out of ice cream sandwiches takes the cake, literally, because the layers are almost pre-made for you. Simple and pretty when cut and served, it will be love at your first creamy bite. Depending on whether you want a layer of chocolate crunchies in your ice cream sandwich cake or not, this could be either a two-ingredient ice cream cake or a four-ingredient one. If you don't need the crunchy layer, ...

If you have satisfying memories of slurping up the sweet milk left in the bowl after eating your cereal, then this cereal-infused milk will make you feel like a kid again. Although people have technically been enjoying cereal milk since the invention of cereal, it was recently made popular as a standalone drink by the playful and quirky Momofuku Milk Bar in New York City. Created by pastry chef Christina Tosi, it's a "recipe" that is both simple and brilliant. The original Momofuku brand cere...

How do you begin to explain the nostalgia that's felt when you play a game from your childhood? You can't. The only thing that will alleviate this feeling is experiencing it again.

Preppy fashions are associated with classic and conservative style of dressing and clothing brands. Get tips on properly dressing preppy from a fashion specialist in this free fashion video series.

Ebone’ Simone Johnsontake shows you in this instructional video series how to do basics of hip hop dance for beginners and those of you who are already dancing fiends but perhaps unfamiliar with the variety of styles and moves associated with rap and hip hop dancing.

Richard Buccola has been playing pool most of his life, and enjoys teaching it to others Trick shots in the game of pool are often associated with hustling, or sharking. During the mid-20th century pool halls were often given an unfair reputation as dangerous, seedy dens of sin (especially after the 1961 Paul Newman film “The Hustler”) where people would lose their money to unscrupulous pool sharks. But interest in the game has seen a rebirth of sorts in recent years, and most pool halls and ...

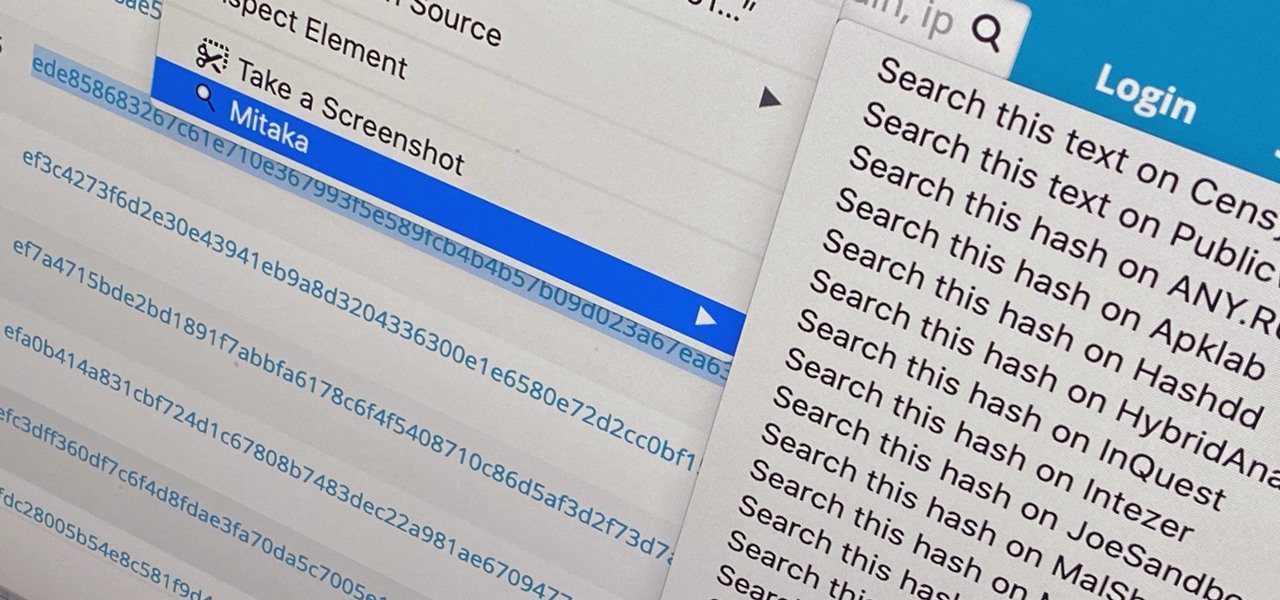
Web browser extensions are one of the simplest ways to get starting using open-source intelligence tools because they're cross-platform. So anyone using Chrome on Linux, macOS, and Windows can use them all the same. The same goes for Firefox. One desktop browser add-on, in particular, makes OSINT as easy as right-clicking to search for hashes, email addresses, and URLs.

There are times when physically interacting with your iPhone is less than ideal, like when you're cooking or driving. Fortunately, iOS 13 has you covered regardless of the circumstance you may find yourself in. With the new Voice Control feature, you can control pretty much everything on your device without even touching it.

The transcribing app can be an invaluable tool, especially if you're a student or are in a profession that relies on audio journals or interviews. These apps can convert important recordings like lectures and meetings into text for you to carefully read through to better comprehend.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Right on the heels of the iOS 11.4.1 beta 3 release, Apple pushed out iOS 12 beta 2 to registered developers on Tuesday, June 19. Public beta testers received the same version, labeled as iOS 12 public beta 1, six days later on Monday, June 25. Last year, the iOS 11 public beta opened up just five days after the release of iOS 11 developer beta 2, so iOS 12 is pretty much right on track in that regard.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

This is probably not the best touchdown celebration but certainly would be the most annoying. Touchdown celebrations are notoriously egotistical so if you want to keep with the tradition you can try out some of these your next touchdown.

The Family Guy's Stewie Griffin is one of the most recognizable cartoon characters on Fox today. This bundle of joy can make anybody league, no matter how old you are. Stewie is the youngest out of three children and seems to be the smartest as well. Stewie is sort of a villain in the making since he is the rudest, crudest, character out of the Griffin bunch. Now, many people don’t know this, but Stewie is supposed to be a 1 year old toddler and not a small infant at all. With a vocabulary of...

As NASA nears the launch of another mission to the Moon in 2024, and a subsequent mission to Mars in the 2030s, augmented reality is increasingly being woven into the normal space operations to test various capabilities.

One of the most iconic architectural landmarks on the planet, the Arc de Triomphe in Paris, France, will become a part of augmented reality history thanks to a new project from Snap.

In recent years, the tech innovation space has been dominated by the US and Asia, with Europe weighing in, but still being mostly lauded for its art history and architecture.

With non-fungible tokens (NFTs), particularly those that are 3D in nature, holographic displays are becoming more indispensable for those looking to show off their valuable works of art.

You don't need to work in the accounting department of a Fortune 500 company to use and appreciate Microsoft Excel. Although primarily associated with a wide variety of functions pertaining to accounting and finance, Excel is actually an incredibly powerful and multifaceted platform that can be found at the heart of many large-scale analytics environments.

The only thing better than programming MicroPython is programming MicroPython over Wi-Fi. So once you set up MicroPython on a microcontroller and have it on its own power source, you won't need to use a data cable to connect to it whenever you need to interact with it, program it, upload files, or grab data.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

There are times when leadership is tested. This is one of those times. As government and business leaders around the world are grappling with the unfolding coronavirus pandemic, the real-time responses to the crisis from many leaders have been great and, at times, less-than-optimal.

When you have a personal Instagram account but also manage other profiles — like ones for work, your entrepreneurial startup, an alter ego, or your famous pet, to name just a few examples — how do you manage them all from the same device?

As fun as Twitter is, it can also quickly turn scary. Anonymous, aggressive, and troll accounts can attack you for your tweets and stalk your every move. While you could make your profile private and block users, there are lesser-known privacy and security features that you can switch to improve your safety online.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

Action games encompass a wide array of categories, ranging from racing games that pit you against players the world over for track domination, to endless runners that push you to set ever higher scores, and RPGs that let you embark on adventures in fantasy worlds. With such a huge selection of titles to look through, it's all too easy to overlook a game you might otherwise like.

Many popular apps automatically share your personal data. While I have accepted a certain amount of data collection from Google, to know companies such as Facebook perform this without my consent bothers me. After some researching, I've found a great solution, and it doesn't require root.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

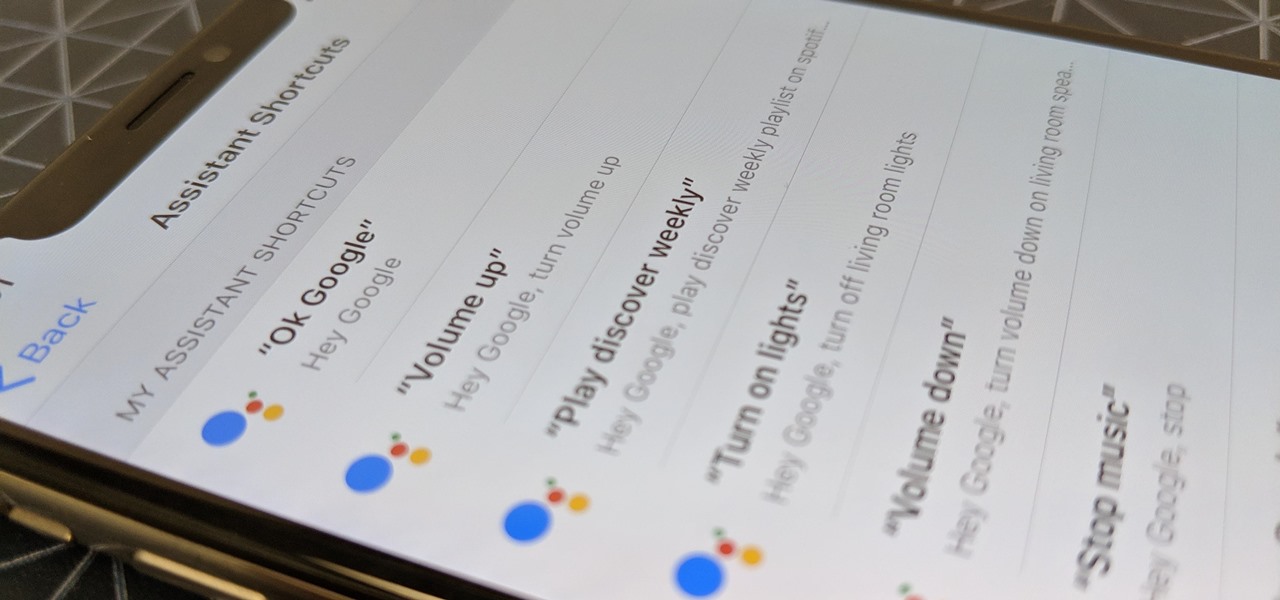
Using Siri to perform tasks on your Google Home device was never possible until Apple released Siri Shortcuts in iOS 12. Actually, it wasn't possible until Google added support for Siri Shortcuts for Google Assistant in Nov. 2018. No matter the timing, the important thing here is that you can use Siri to command Google Assistant which, in turn, can command Google Home.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Until very recently, Apple apps were among the only ones that would play nicely with Siri on iPhones. If you wanted to take advantage of the digital assistant to, say, compose an email, you would need to go with Apple Mail instead of the email client you actually use. As of iOS 12, this is no longer the case.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Waking up your Apple Watch to see "your heart has shown signs of an irregular rhythm suggestive of atrial fibrillation" might come as a shock. While your watch can send you warnings if it detects a fast or low heart rate, those messages are pretty vague, while the abnormal arrhythmia alert can downright scary. So what should you do if you receive one of these AFib notifications?

You're minding your business when your Apple Watch taps you. To your surprise, the watch claims your heart rate dipped abnormally low. The news might come as a shock — especially if you have no history of a heart condition — but before you panic, you should take the time to fully understand what this alert is really saying and what you can and should do about it.

This week, Next Reality released the fifth and final set of profiles on the NR30 leaders in augmented reality, with this chapter focusing on the influencers in the industry.

Like many things associated with Magic Leap, the start of the company's first annual L.E.A.P. conference got off to a unique start. Taking the stage on Wednesday morning in Los Angeles, the company's CEO, Rony Abovitz, gave a brief introductory speech welcoming the crowd and outlining the mission of Magic Leap.

Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all of it.