Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

The hype train that left the station years ago has reached its first stop, and now we finally have access to the Magic Leap One, the device many have claimed would revolutionize the augmented reality space at launch. But is that really true?

While many of you were off surfing and lounging on some sandy beach or trying to figure out how to balance work with sky-high summer temperatures, I've been talking to all the companies that make augmented reality what it is today.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

So, your grandmother finally wants to ditch her flip phone for a shiny new smartphone? Congratulations. But helping her get used to her new device, even when it's an iPhone, is no small task. Grandma mastered checking her email in late-2012 and just recently learned there's a thing called "Facebook." But we love grandma, and thanks to this guide, we can definitely make this happen for her.

It looks like the dust is finally starting to settle on Google's POLED PR nightmare. The Pixel 2 XL — one of the most hotly-anticipated phones of the year — has been plagued by screen issues and worries. While it is certainly not without its faults, Google has created several software fixes and is offering a 2-year warranty for screen burn-in, so we can rest a bit easier about purchasing Google's latest Pixel.

Microsoft recently released "Seeing AI," an app aimed to help the blind understand their surroundings. As Microsoft puts it, "the app narrates the world around you by turning the visual world into an audible experience."

If you use the Google Assistant on your Android device, you can easily send a text message to any one of your contacts. But even though that same Assistant is powering the Google Home, you can't use the smart speaker to accomplish the same task — at least, not without some tinkering.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

The biggest problem with Netflix (which is hardly a real problem) is the overwhelming amount of content available for streaming. Browsing through profile-specific categories might help narrow down your search on something to watch, but some of those categories come and go without warning, and it's impossible to find them again—but not anymore.

With T-Day on the horizon and approaching rapidly, you are probably in one of two camps. The one that is eagerly awaiting the holiday feast with barely-contained drool. Or the one that involves breathing heavily into a paper bag while worrying about your lack of oven and stovetop real estate, while also bemoaning the lack of multiples of you to get all the prep work done.

We are most certainly not machines. We all need some downtime every once in a while to set our sanity scales back in balance, which in turn, makes us more productive workers. This is a premise that several forward-thinking employers fully understand, but these types of companies are few and far between in corporate America.

Organizing contacts is a bitch, especially on the iPhone. Some contacts will have multiple entries, you can only delete contacts one by one, and certain types of contacts can't be deleted at all. If that isn't enough to make you pull your hair out, then I don't know what will.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

Eating vegetarian isn't just for vegetarians. There are plenty of reasons, health and economics-wise, to consider forgoing the meat for a meal or three. Rather than get deep into the world of fake meat (although there's many a tasty alternative to be found there, to be sure), you should consider getting to know your humble-seeming fungal friend: the mushroom. Thanks to their hearty flavor, cooks tend to treat mushrooms like meat, albeit one with its own unique characteristics. Mushrooms are e...

In recent years, Hollywood has taken a shine to hackers, with hackers appearing in almost every heist or mystery movie now. This can be both good and bad for our profession. As we know, whichever way Hollywood decides to depict our profession is how most people will perceive it.

With a November 2013 release, Disney's Frozen just missed Halloween. That means that everyone had to wait an entire year to dress up as their favorite princess or snowman — and that time has finally come.

Staying healthy is a progressive challenge we all face throughout our lives, and figuring out just how to do that can be a challenge when it's not your job. For doctors, however, it is. Here's how they keep themselves healthy day to day.

Gatorade: its popular red flavor can stain the whitest fabric, and its sweet taste is oddly refreshing after breaking a sweat. If you've ever participated in a sport, you probably spent halftime at games and practice breaks chugging the stuff. Though it made its name as a sports drink, Gatorade is also a well-known hangover helper—but its beneficial and interesting uses don't end there. The brightly colored drink can do so much more than just hydrate you.

It's universally known that broccoli, kale, Brussels sprouts, cauliflower, and all cruciferous vegetables (also known as brassicas) are good for you—but you probably don't know exactly how good they really are.

Although your friends might roll their eyes every time you talk about playing Clash of Clans, Call of Duty, or Candy Crush Saga, your excessive gaming habits might actually be making you healthier than everyone else.

When you know how to cook it, tofu is a delicious dish in and of itself—truly. Too many people have been subjected to poor quality or badly cooked tofu and told to eat it because it's a "healthy alternative" to meat. Usually what they bite into is a bland, rubbery mess coated with a random array of flavors.

Two slices of whole-wheat toast with lots of butter. Two eggs, poached to a firm yet custardy texture. The yolks should absolutely not be hard-cooked and the whites should be tender, not rubbery. That's my idea of the perfect breakfast.

Those of us who lived our childhood through the '90s remember the rapid advancement of console gaming. From the Nintendo to Game Boy to Dreamcast to PlayStation, we were consistently greeted with newer and better technology on a year to year basis.

Hello there, people. Today, I am going to show you how to extract the essence from a useful plant, using either alcohol or olive oil. This is how you take a plant and turn it into a useful (and preservable) medicine. For those of you who know nothing about herbal medicine, let me explain it for you in a nutshell...

Living in Los Angeles has given me the opportunity to attend a bunch of really cool events. I've been to Dodgers, Lakers, and Clippers games, a few concerts at the Staples Center, and a plethora of smaller joints.

This is a simple pattern, designed to produce a well-fitting mitten. Both the right and left mittens worked the same up to the shaping for the top of the mitten. A slight adjustment for making one right and one left, then they are worked the same. The gusset for the thumb constructed with the increases made in the center of the gusset, rather than on each side. This makes it easy with a minimal amount of counting stitches as you go. I have been crocheting for 56 years. In doing research for w...

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

The latest software update for iPhone has a few new features you should know about, including an enhanced security feature to protect your Apple ID account from phishing and other attacks. Keep reading to see everything new that's included with iOS 16.3 for iPhone.

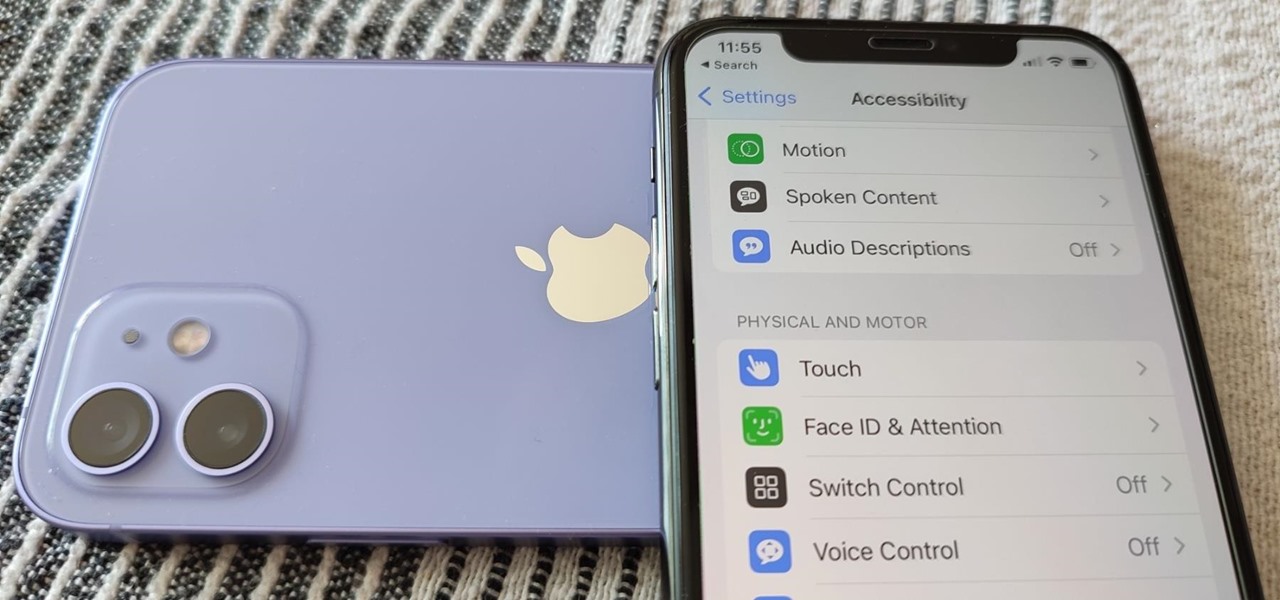
While it's not usually the first thing everyone looks at after installing a new iOS software update, I'd give the new accessibility features on your iPhone priority attention because there are some highly valuable tools that even users without disabilities can enjoy.

Apple's latest big software update includes an entirely new Apple app, a controversial change in the TV app, better Siri control, an improved Shortcuts app, interesting Safari upgrades, Apple Music Sing, and more. Keep reading to see what iOS 16.2 has to offer your iPhone.

Live Activities is Apple's hottest new feature for iPhone, but it's not always straightforward. Sometimes you'll trigger one without realizing it, but it may seem frustratingly impossible to start one when you really want it.

The COVID-19 pandemic has practically shut down all sports except for World Wrestling Entertainment, which has continued staging matches without an audience, leaving us sports fans with nothing much to cheer for. While they can't replace live games, smartphone games provide an alternate reality to live out our competitive entertainment in the absence of the real thing.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

Word games fit perfectly with the on-the-go nature of mobile gaming. They're easy to pick up whenever you feel like exercising your brain, but they're also fairly easy to put down when you need to get back to the real world.

SCRABBLE. To some it's just a game, but to me it's life or death. Well, not really, but it feels that way anyway. On a normal weekend, a game becomes much like Jon Thomas' "friendly game of death Scrabble."

Apple just released its biggest update to iOS 17 yet, and there are 60 exciting new changes for your iPhone. With iOS 17.2, you get a brand new app, more Apple Music enhancements, upgrades in Messages, and a new security feature that was announced last year, as well as changes for Weather, notifications, Apple TV, Books, and more.