It may seem strange to find the director of engineering at a question-and-answer site all of a sudden pick up and lead a new driverless startup, but to Kah Seng Tay, both engineering tasks require building the right infrastructure to handle large amounts of AI data.

Unity 5.6 was just released on March 31, and it will be the last entry in the Unity 5 cycle. With all of the new features, it looks like Unity 5 is going out with a bang.

Baidu Inc, the "Chinese Google" search engine and technology company, which has been actively pursuing self-driving cars, reported that a gang of hackers recently attempted to steal its driverless car technology.

A new Windows Insider Preview, version 15055, was released on Friday, March 10. Along with the normal collection of bug fixes and new features came a secret addition to the Mixed Reality Portal in the update. Windows Mixed Reality, along with Cortana, can now teach you how to use the platform, and, hopefully, usher in with it some understanding of what mixed reality is.

Despite the availability of a vaccine against it, almost 50% of men aged 18-59 in the US are infected with the human papillomavirus (HPV). Why?

With the height of the flu season ahead, there are some good reasons to keep a flu vaccination in mind.

The HoloLens is the world's first untethered holographic head-mounted computer, which Microsoft has been rather proud of—and they have every reason to be. Of course, as soon as we developers get adjusted to the idea of keeping the scope of our projects inside the bounds of the HoloLens' processing power, Microsoft hits us with the Holographic Remoting Player.

Mirror, mirror on the wall, who's the smartest of them all? Since Max Braun's Medium post went viral back in January of 2016, smart mirrors have been appearing on tech blogs in all shapes and sizes. Some are technically sound, some incredibly easy, but all are visually compelling. However, we've never seen one with a fully functional operating system and gesture support—until now.

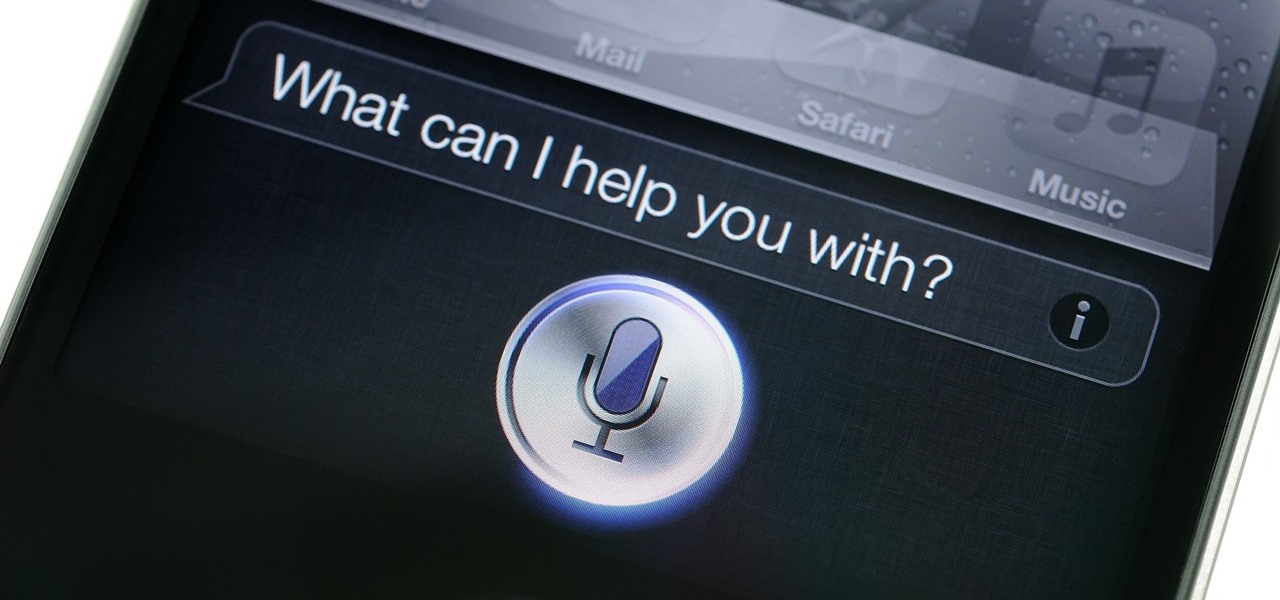
If you follow tech, you're probably familiar with Siri, Apple's personal voice assistant, which has been integrated heavily into iOS ever since iOS 5. But you might not have known that Siri is capable of performing some tasks when the iPhone is in a locked state. The default state of iOS is to allow access to Siri from the lock screen, most likely for the convenience of hands-free access to the phone.

A 2D film can show you something, but a 3D film in virtual reality can make you feel it. If done right, you'll feel immersed in a new world that surrounds you. If done wrong, you'll get nauseous and uncomfortable. SilVR Thread, a 360-degree VR video company, figured out a few important ways to get the feeling right.

The HoloLens opens up new, digital locales within our physical world, so it was only natural for the HoloLens Challenge to ask developers to create a portal into one. One developer rose to the task and gave life to wall art, turning it into an interactive game called Future Boy.

Despite its battery issues, the Samsung Galaxy Note7 is one impressive piece of machinery. Packed to the brim with loads of RAM, a top-notch GPU, and one of the best processors on the market, this thing should be able to zip through any task you throw at it with lightning-fast speed.

Mixed reality can give you the feeling that you've uncovered a hidden world layered into the physical one you already know. This can happen in so many ways, from a trading card that births a hologram or a first-person shooter with robots blasting through your walls. Xperiel—a California-based augmented and mixed reality company—wants to create a platform to make that a whole lot easier for developers.

We're inching closer towards the singularity—that point where technology advances to the steepest slope of the logistic function S-curve and simply skyrockets at a rate we've never seen before. Somewhere along the way, the line between humans and the tech we rely on will become blurred, and MIT's latest project might very well be a step in that direction.

Snapchat has already found a compelling way to create advertisements in augmented reality with their branded filters, but they continue to experiment with new ways to monetize the bridging of the real and digital worlds. Their latest idea, which requires users to "snap" an image to unlock content, could succeed where QR codes haven't.

Keyboards and mice work fine for computers, but in a holographic environment you'll want to do more than just point, click, and type. While we can still benefit from these input devices, complex hand-tracking methods are necessary for the evolution of mixed reality user interfaces.

Mixed reality headsets have limited hardware capabilities and naturally imprecise interfaces. While that works just fine for games and entertainment, can they actually function as a tool for productivity?

Onion scrubs, salt and olive oil blends, a baking soda slurry... despite the many methods already out there to clean your (old or brand-new) cast iron cookware, there's one you may not have considered: using a potato.

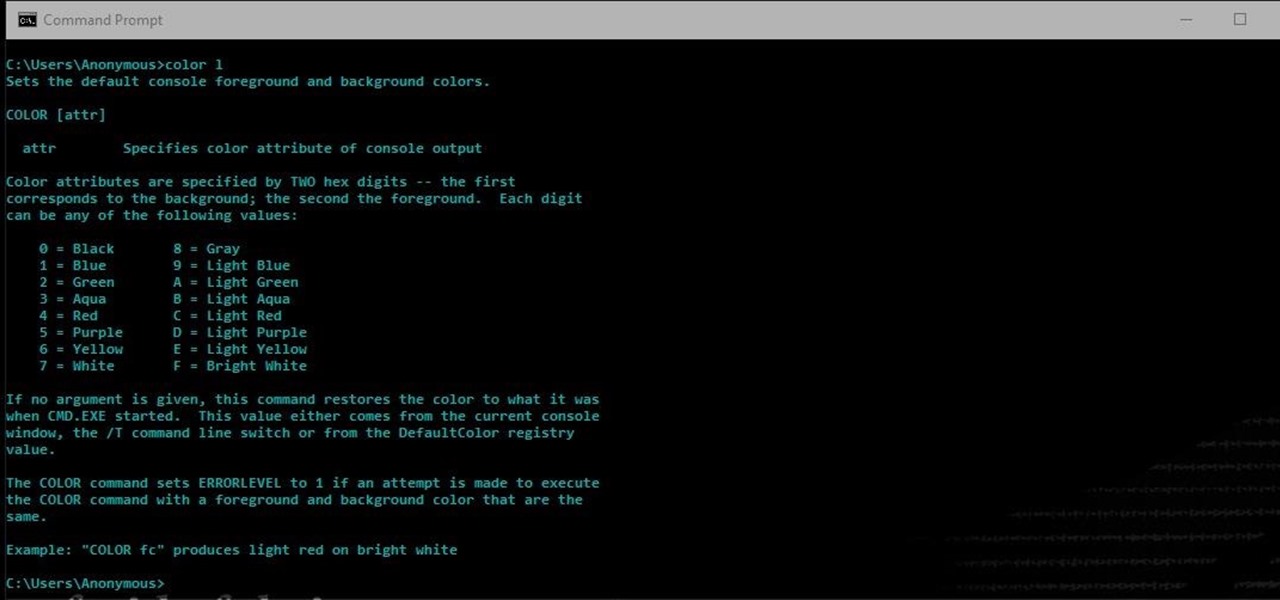
Another series I am now starting, might have to slow down on all of these series, but why tf not. What Is CMD?

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

I have gotten comments from my last tutorial on not being able to do anything because of a lack of a monitor. In order to address this problem I'm gonna show you how to connect and control the Rasberry Pi through a SSH client on Linux, Mac, Windows, and Chromebook computers. This will probably we a long tutorial so please bear with me. Anyway, lets get to work.

Hola my fellow hackers! I promised you the tutorials on setting up RAT's and Botnets, but before jumping into those, i want you to know about the precautionary measures and detection of RATs which might be on the system without your prior knowledge. Of course the Anti-virus do most of the job but there are some RATs which slips past the Anti-viruses (This is where Hacker's skill come into play).

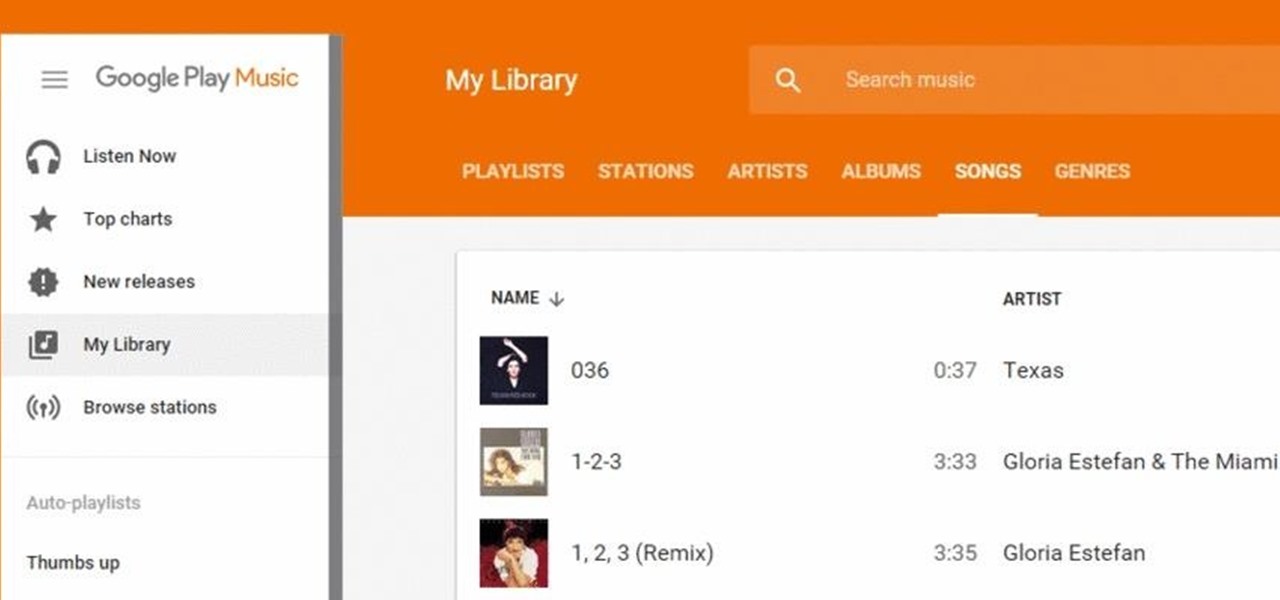
Google Play Music has been my go-to music service ever since its release. The free cloud storage for 50,000 songs and full access to Songza-powered radio stations make it a great music app, even without the $10/month streaming service.

The dock in Mac OS X is intuitive, customizable, and aesthetically pleasing, which is a stark difference from its clunky Windows alternative. In fact, in Windows, it takes both the Start menu and taskbar to accomplish what Apple's dock does—but it doesn't have to be like that. Below, I'll show you how to add an OS X-inspired dock on any PC running Windows XP or higher. Step 1: Install Aqua Dock

!!!WARNING!!! !!!Because of misleading informations please wait for the new post about this same argument instead of reading this post!!!

Hello, fellow hackers. I'm sure we've all seen it somewhere: the undying question of "How do I hack the game so-and-so?" And the answer usually is, "Come back when you actually know how to hack!" But how does one even go about "hacking" a game? What could that even mean?

Your brain holds a lot of precious information and is capable of great feats. However, there's one quality that doesn't lie among its strengths—memory security. Yes, that's right, your brain can be hacked, and it doesn't take a psychologist to do it. Anyone with the right know-how can change your memories for their own personal benefit, and you can do so to others, too.

Who doesn't love the world of Game of Thrones? Whether you're a fan of the hit HBO show, or can't wait for George R. R. Martin's next novel installment, it's a story loved by nearly everyone. It's an excellent source of inspiration for Halloween costumes too, ranging from the disturbed to the beautiful. Lady Stoneheart, Catelyn Stark risen from the dead, is the perfect scary choice—bloodied, battered, and carrying a desire for vengeance.

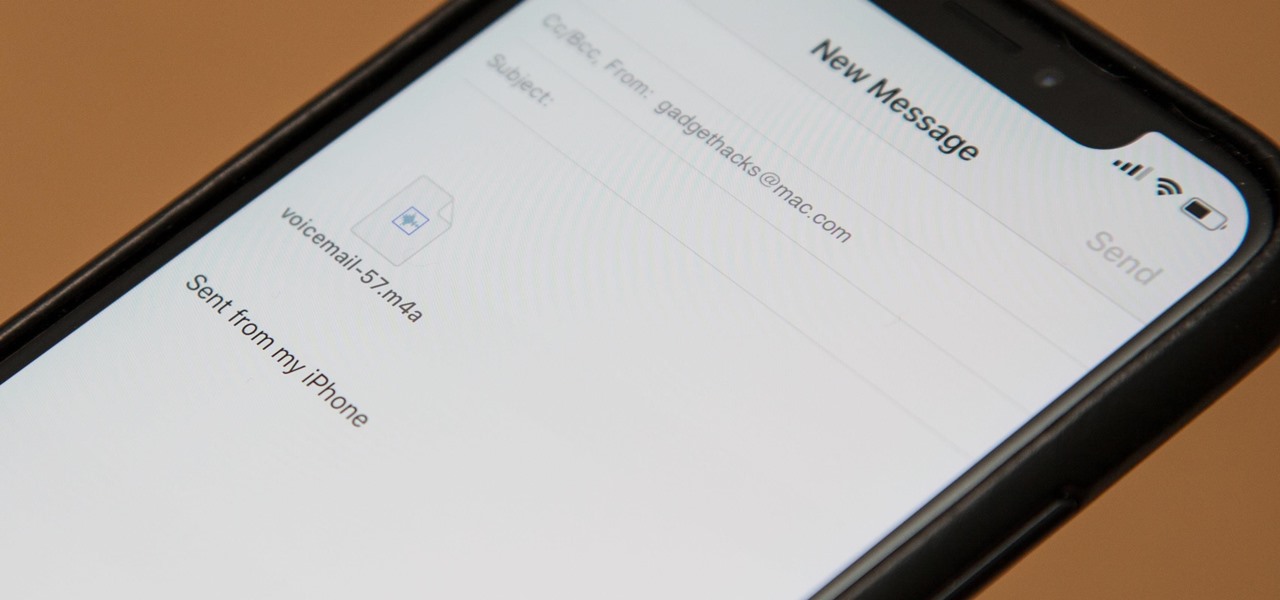
Eventually, your voicemail inbox on your iPhone will get full, and you'll have to delete some messages in order to make way for new ones. If all the voicemails you currently have are super important, you're not going to want to delete them before saving them first, of course. Luckily, this is a super simple task, and you can even forward them to someone else if needed.

Cupcakes are special treats by themselves, so surprise-inside piñata cupcakes are extra special for birthdays and special occasions. You can customize these with any flavor of cupcake and any type of candy or chocolate treat you want to stuff them with.

MagicTree is often the go-to tool for data collection and reporting for many pentesters. It organizes data in nodes in a tree-structure which is very efficient at managing host and network data. Reports can be completely customized to meet the user's needs. Also, MagicTree allows you to import XML data and has XSLT transforms for Nessus, Nmap, OpenVas, Burp, Nikto. MagicTree comes pre-installed in Kali.

From day to day, it can be difficult to remember everything that's required of you. I tend to forget exactly where it is I'm supposed to be during my busiest moments, and it's even easier to delete each day's events out of your brain when there's so much else that dominates your mind. Yet taking the time to remember exactly what it is that happens during each of our days can be a vital part of our memory—and with nothing more than 15 minutes, we can strengthen our brains and remember more tha...

Who doesn't experience food cravings? Whether you're trying to adhere to a strict diet, or simply hoping to avoid sugary, fatty foods, curbing cravings can feel like a monumental task.

Shrimp is one of my all-time favorite foods. It's versatile, delicious, and incredibly fun to use in the kitchen.

Cortana, Microsoft's personal assistant for its Windows Phones and Windows 10, will soon be released for Android. That is, officially released. It's hard to keep a good thing locked away, and to that end, Cortana for Android has been leaked, thanks to APK Mirror.

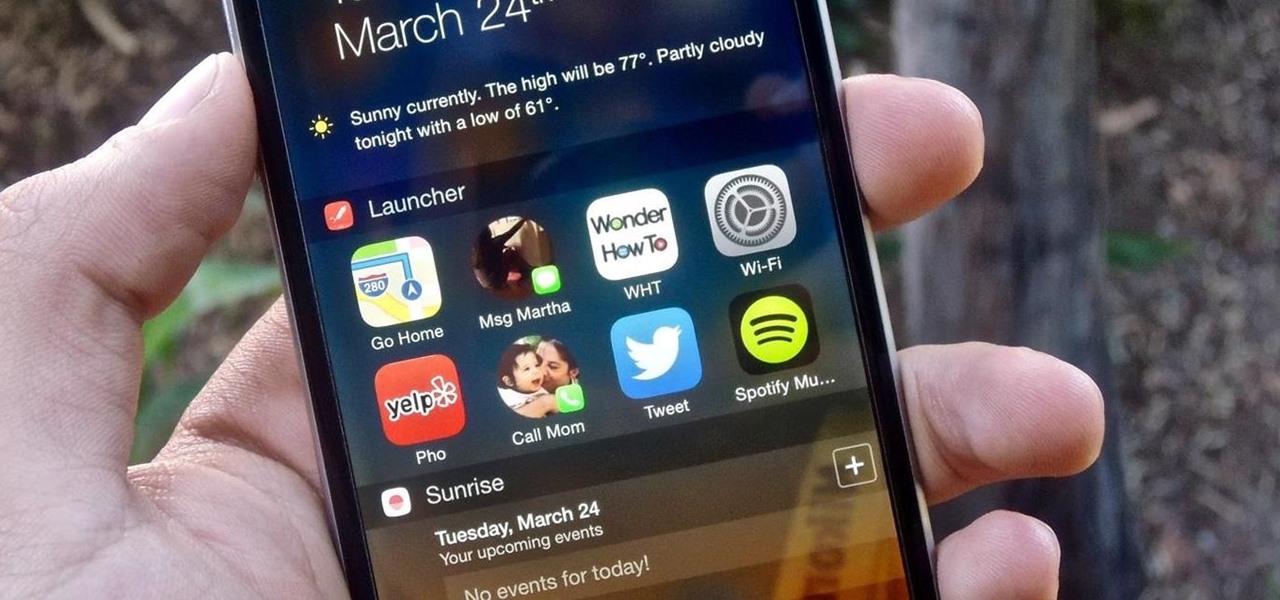
An app called Launcher was released for iOS 8 last September that let users open any installed app directly from a widget in the Notification Center pull-down. For some reason, Apple didn't take too kindly to this and banned Launcher from the iOS App Store just a few days after its release.

Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.

We've all been there: you're staring at a fantastic-looking salad or sandwich full of your favorite ingredients. You take a bite, and you taste only one thing—raw onion. A glass of water, a toothbrush, and an hour later, and your breath still tastes like only one thing—raw onion.

There are a number of ways to give your productivity a kicktstart, from taking a break from your distracting smartphone to just taking a break, plain and simple. Yet finding the motivation to start working doesn't require any effort at all—just a little bit of green.

One of the many additions that appear on Android 5.0 Lollipop is a handy menu that lets users correct for or simulate different types of color blindness. While Google didn't flip the switch on this new feature until Lollipop was released, it turns out they had been working on it for quite some time.