Hello Hackers/Viewers, It is a new day, and you might be thinking, It is so boring, why not try to be cool with computers in front of my friends? That is why, I have made this tutorial to make fake viruses using notepad to look cool!

I have a lot of favorite kitchen tools. My seven-inch Global chef's knife is my baby. My pasta maker is my dance partner on any given Friday night. My girlfriend's stand mixer is my favorite toy in the apartment.

If you're feeling stressed, there are many home remedies you could use for relief. Meditation, yoga, acupressure, an ear massage, more sleep, shower soothers, playing video games… the list is endless. But a lot of these methods require a significant amount of time, so what do you do when you need immediate stress relief?

Your Apple Watch is a fantastic tool that can help you perform daily tasks on your iPhone. Notifications get filtered through it, you can respond to messages on it, and you can even use Apple Pay to purchase goods and services. Your Apple Watch is also a valuable asset when it comes to finding your lost iPhone, too.

Whether you drive a new or used car, discovering a new dent, scratch, or scuff mark can send you into a frustration spiral. While there are many DIY ways to deal with dents, scratches and scuff marks are trickier because using the wrong stuff could make your car's paint job look even worse.
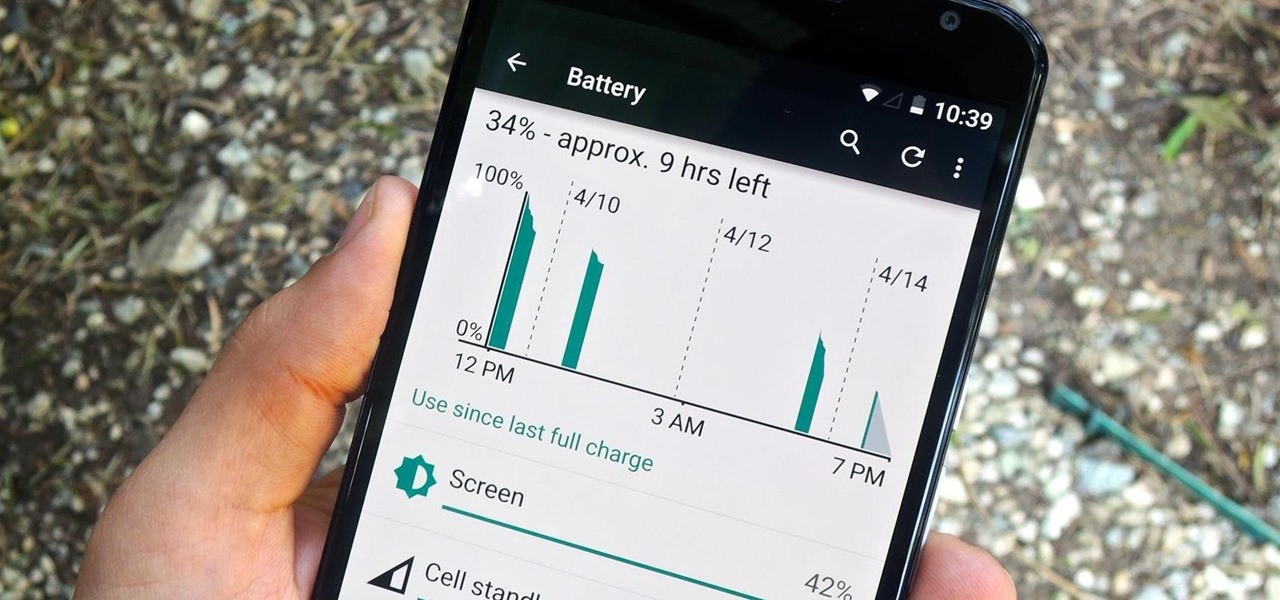
When purchasing a new phone, one of the most vital features to consider is battery life. Everyone wants to know how long they can use their device without needing to hug a wall. Increasingly, more and more manufacturers ship their devices with some variation of a "battery saving" mode, which can help combat dead-phone issues in times of dire need for battery life.

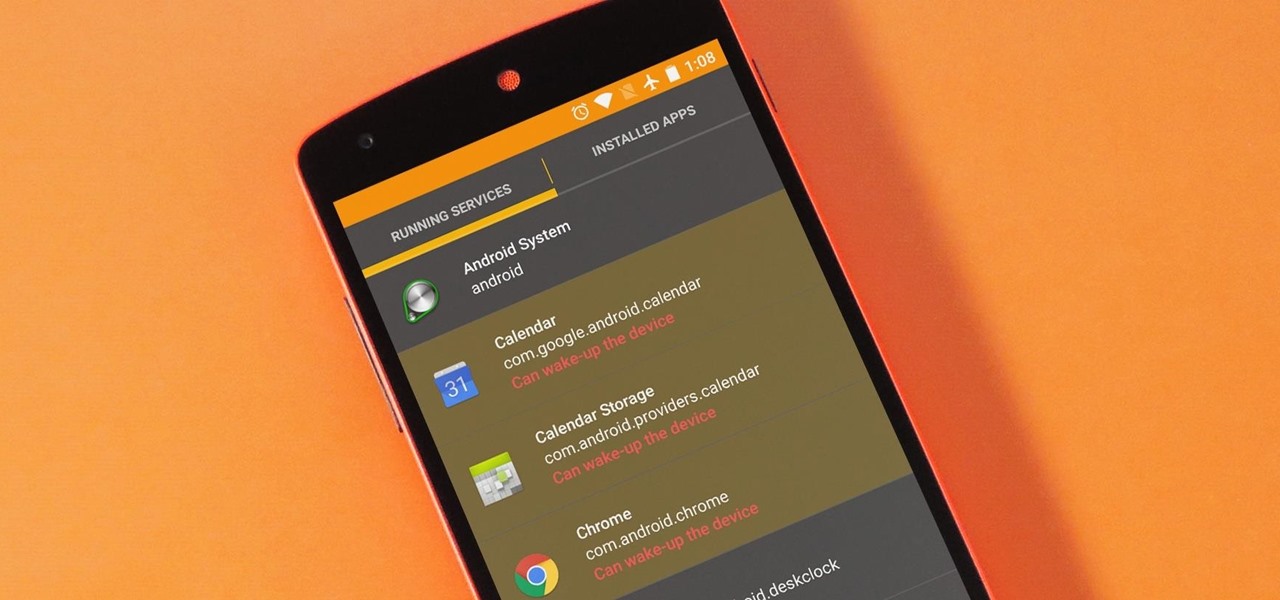
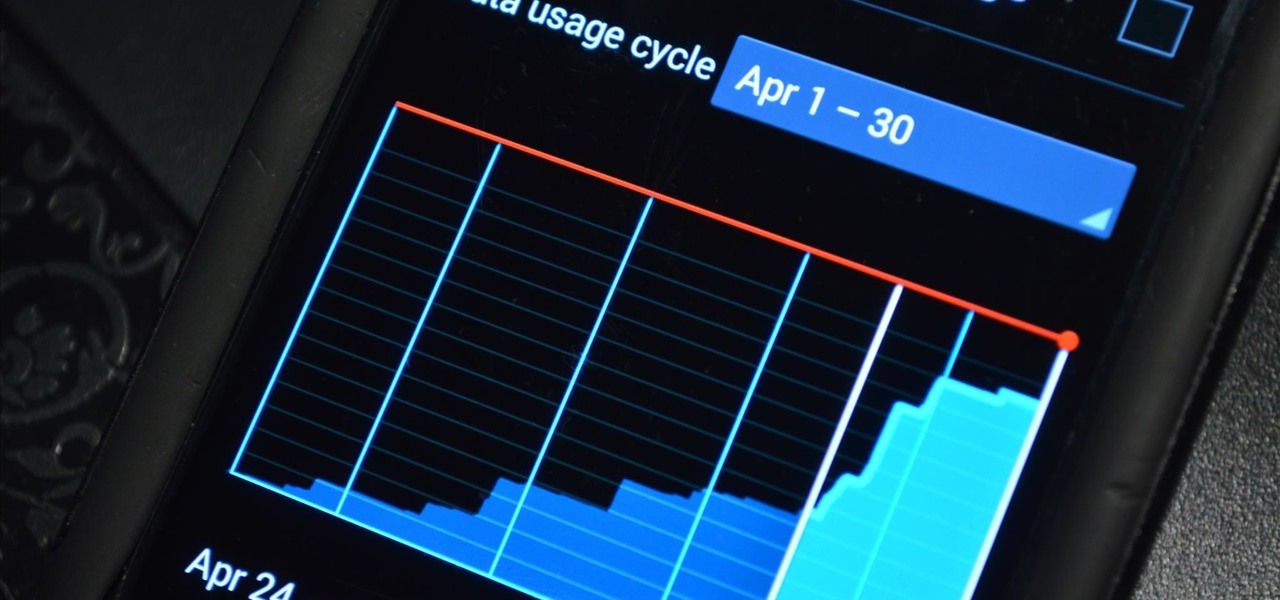
The vast majority of Android apps use background services to sync data, check for location updates, and perform various silent tasks. These background services can start up whenever they'd like, and they continue to run in the background even when you're not actively using the app that they originated from.

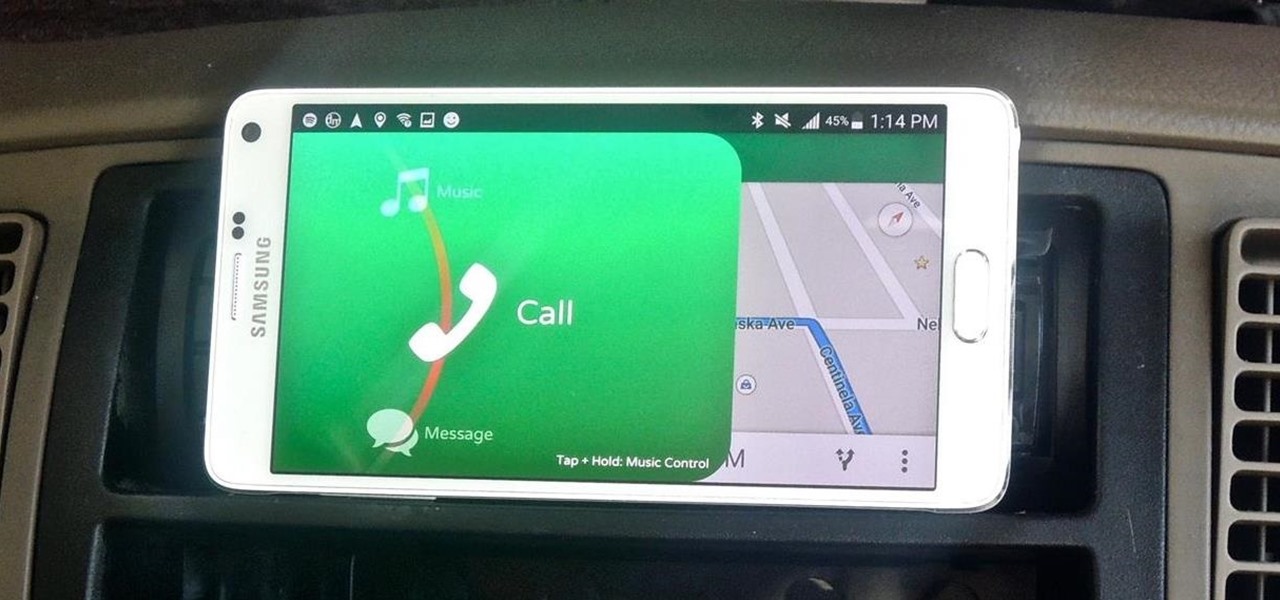
Most new Android devices come with at least one feature that helps control navigation, music, and more through voice-controlled, hands-free communication. While they usually don't end up being completely "hands-free," these apps do stop people from using both hands to perform tasks on their smartphones while driving, therefore distracting them less overall.

Android has a system-wide user dictionary file that any third-party keyboard can utilize, if it so chooses. This file contains all of the words that you've added to your keyboard manually, and of the big-name players, Minuum, TouchPal, and the Google Keyboard call on this file to determine their user dictionaries.

No one ever wants to experience pain, whether it's as small as a stubbed toe or as great as recovering from surgery. Yet so much of our lives causes pain, lasting or brief in its form. With a few mental tricks and unusual home remedies, you can relieve some of the most common aches and ailments that arise painlessly.

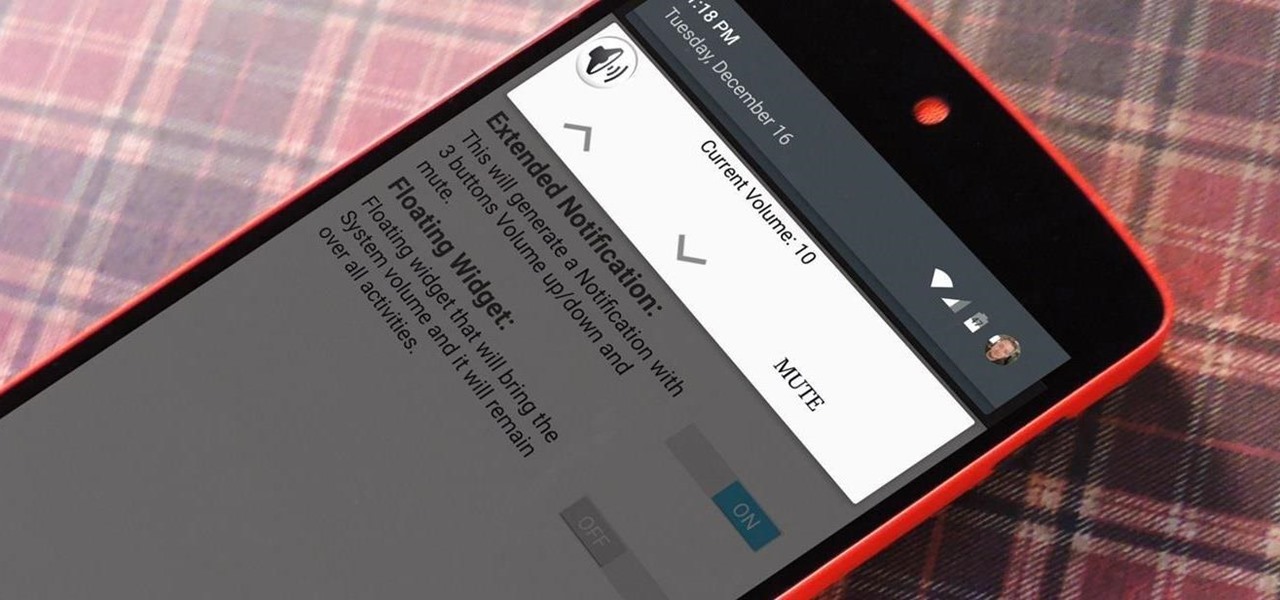
As touchscreen phones continue to evolve, the need for physical buttons seems less and less pronounced. While hard keys may seem like an endangered component on mobile devices, save for the Samsung Galaxy line, it'd be difficult to fathom a world where volume keys are absent.

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

One of the most mind-blowing meals I ever ate occurred when I was 12 years old. The main course and sides were good, if unmemorable, but my jaw dropped during dessert when my friend's mother whipped out a blowtorch—as in a bona fide welding torch from the hardware store—to finish off the crème brûlée.

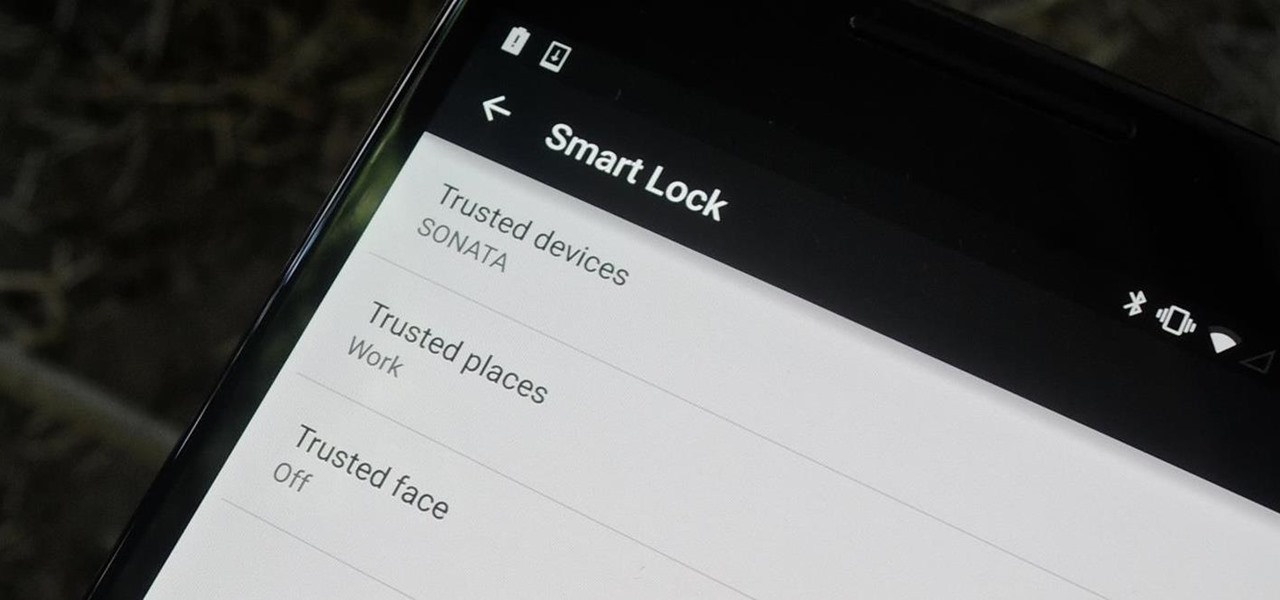
Keeping expensive mobile devices safe and secure is a priority for most of us, but the process of repeatedly unlocking a phone or tablet can seem like a pointless task. This leads to disabling the lock screen altogether, especially when in a safe place (e.g., home, office, car, etc.).

Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method.

Like most people who cook in a small kitchen, I'm very wary of adding anything to my drawers and cabinets unless I'm sure it's going to be essential to my cooking arsenal or that it can be used in multiple ways.

A little cooking mistake can lead to tough meat, spoiled food, and even a bacterial explosion in your kitchen if you're not careful. These five simple, easy-to-fix kitchen mistakes are some of the most commonly made in households around the world. Luckily, you can correct these innocent errors with just a few minor tweaks.

Are you stranded in a hotel room with no kitchen, but craving the comfort of a home-cooked meal? Fear not, I have found some interesting ways to cook food without the luxury of an oven, stove, microwave, or even a toaster!—also known as "hotel room cooking."

Finding the motivation to make a change can be tricky. It's difficult to resist the urge to procrastinate, or even give up when goals seem distant and difficult. If you wish you could stick to your New Year's resolutions, or maybe even just commit to pursuing smaller goals, you might want to consider making a small change to start: just create a new password.

You've probably tried just about every method of hanging your holiday decorations: nails, thumbtacks, sticky hooks, and, in desperation, even tape. Each method can leave a host of complications when removed, though, from chipping paint to visible holes.

If you've ever taken apart an electronic device that uses physical buttons, you already know why these types of input methods are destined to fail. The rubberized contacts used in physical press-and-release buttons like those of a gamepad or keyboard are incredibly frail and can easily wear out over time.

Some nights, I'm a lazy cook and only want to chop one clove of garlic for my immediate needs instead of prepping a giant batch and freezing it the way I normally do. The only problem is if I'm already feeling that lazy, I really don't feel like dirtying a whole cutting board. However, I still want my garlic to be finely minced so it suffuses my dish with its wonderful, one-of-a-kind flavor.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

One of the few areas where Android lags behind iOS is a comprehensive backup solution for apps. Root tools, such as the popular Titanium Backup, are capable of backing up all of your apps and their data, but not everyone wants to root their device and potentially run into issues with voided warranties.

Stock Android is a great experience, and it's probably one of the biggest reasons that people purchase a Nexus device over other Android phones. Without carrier or manufacturer modifications to the core software, the entire user interface feels a lot more clean and snappy, and this also means that developers encounter fewer compatibility issues when creating flashable ZIPs and custom ROMs.

Spills happen in the kitchen, and while every good cook knows to clean as you go, not every cook has an endless supply of cleaning materials. Besides, one spill can exhaust your entire stockpile of sponges, paper towels, and rags in a matter of minutes. Particularly egregious mishaps can make everything they touch feel sticky and gross.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

Aside from the occasional "creative" collage, most of your friends on social media are content with pretty basic image and video posts. You can easily one-up them with celebrity cameos or awesome time-lapse videos, but to truly outshine them, try your hands at some creative double exposures.

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...

There are several reasons why restaurant food tastes so good. One is that the cooks know how to make reductions, which involves cooking down large amounts of liquid until it becomes a pool of thick, glossy sauce. While this technique isn't hard to learn, it can be time-consuming.

All Android web browsers are not created equal. Some, like Chrome, have slick interfaces and quick rendering, but are not very robust. Others, like Firefox, boast tons of functionality and support add-ons, but are lacking in the interface department and could use a boost in performance.

Last week's tech roundup featured iPhone 6 clones, an all-in-one sleep tracker, Xbox One updates, and other cool gadgets. This week, there's a lot more to show off, and a bunch of stuff that I need to get my hands on! Everything from app updates to putting stickers on your favorite items, I can't help but squeal at how much the "future" is right now.

The newest version of iOS 8 beta is now out. Almost three weeks ago, in the iOS 8 beta 2 release, we saw podcast integration, full-screen caller ID, new assistive touch toggles, and a "disable all" button for app notifications, among other things.

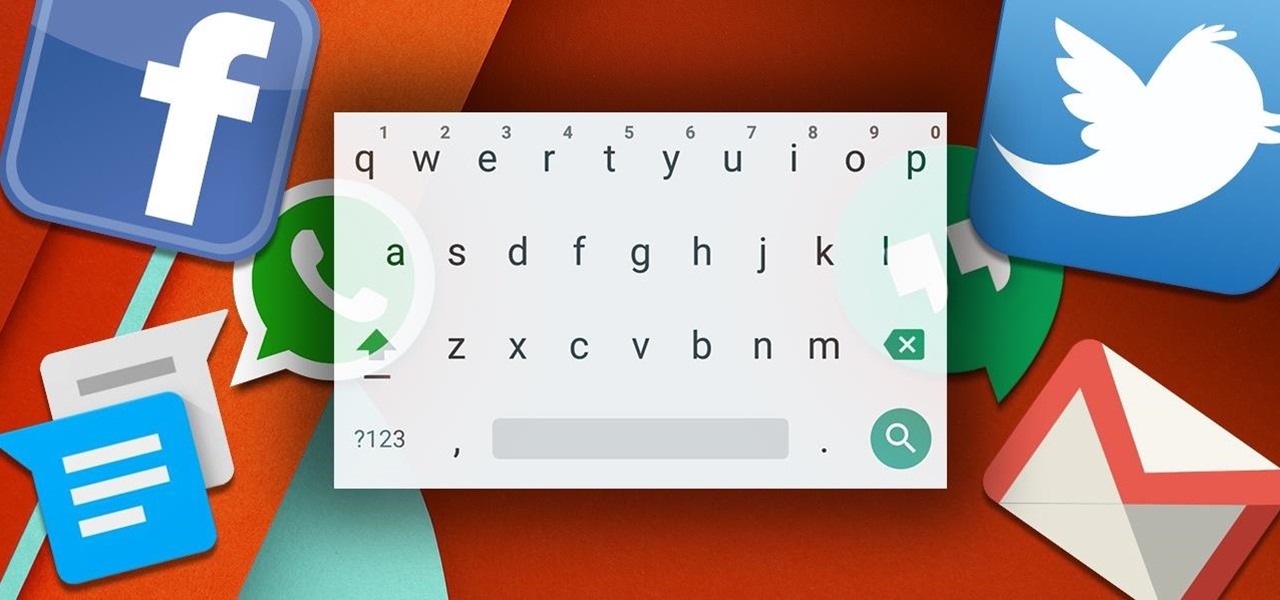
Text input on a touchscreen device is constantly evolving. From early beginnings of pecking out each individual character to today's predictive text and gesture keyboards, we've already come a long way.

Admit it, you wish Siri was on your Mac, and so do I. She stole my heart on iOS, and now every time I open up my MacBook, I feel something missing. Wouldn't it be great if we could, I dunno, hack Siri onto our Macs? Yeah, it would!

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

While you may look ridiculous doing the potty dance and crossing your legs back and forth, holding it in can be worth the discomfort when you've got an important decision to make.

It's been over two whole years since the Samsung Galaxy S3 was released, so let's face it—our beloved GS3, once an iconic heavyweight in the tech arena, is almost as washed up as Sylvester Stallone.

I have an embarrassing habit: I type with six fingers. Just as your grandma pecks at the keyboard with her two index fingers, I rely solely on my index, middle, and thumb fingers only. But it's not as slow as you think, and I'm not the only one out there that does it.

While rooting your Galaxy Note 2 certainly has its advantages—everything from increasing security to relieving the Power button of its duties—it's definitely not for everyone.