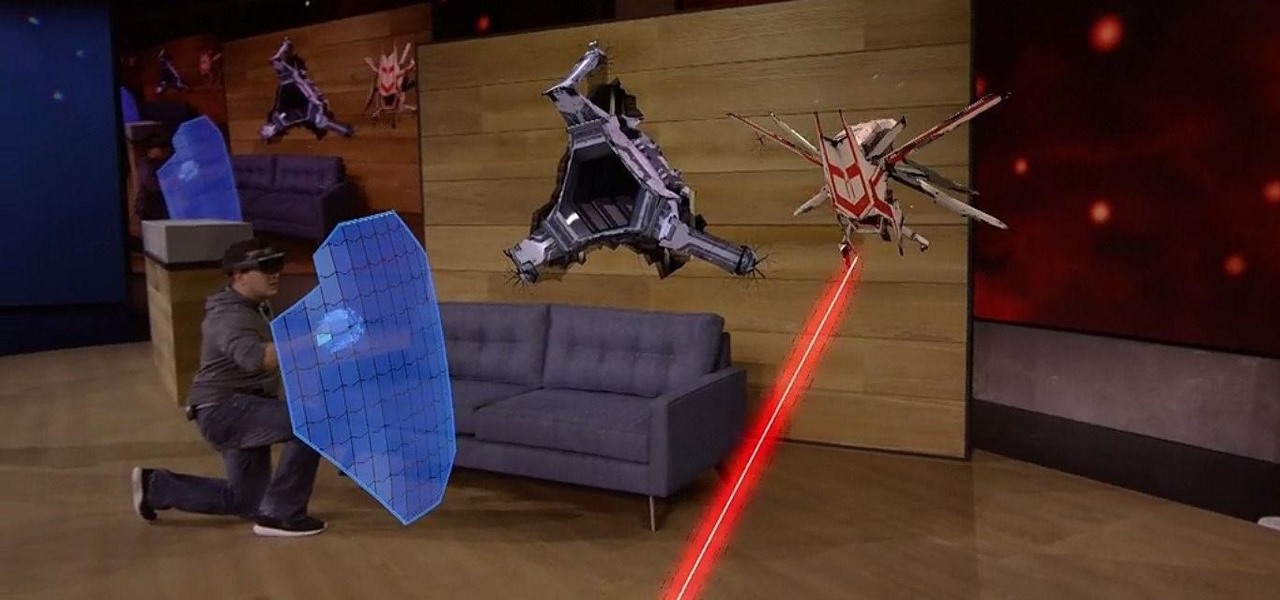
Microsoft's HoloLens has many applications in the business world, both large and small, but what about gaming? Initial demos gave the impression that we could expect amazing first person shooters, platformers, and even Minecraft. Yet, as Newsweek noticed, the HoloLens was nowhere to be found at E3 this year.

Considering how much smartphones cost in the first place, we're understandably reluctant to throw them out when we've bought a newer model. And this is probably the best practice, too, as there are many great uses for an old Android device.

I was skeptical when I first heard about GifWidget, an Android widget that lets you place GIFs on your home screen. As much as I love GIFs, did I really need to see this, this, this, or this, or even this, forever repeating on my phone?

Smartphones tend to struggle when it comes to recording video in low light situations. Danish phone manufacturer Lumigon included a good camera capable of shooting 4K video on its latest phone, The T3, but the real interest lies in the second camera, which is a dedicated night vision shooter.

Microsoft's HoloLens is certainly a leap into the future of mixed reality interfaces, but it's not without drawbacks.
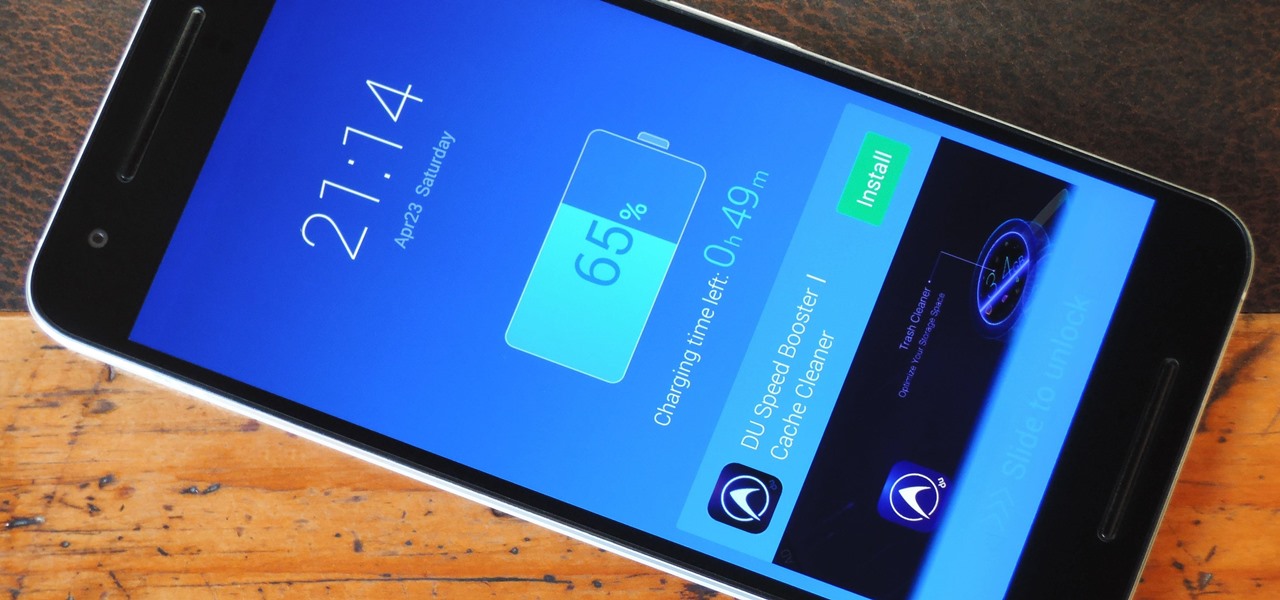
There was a somewhat recent outbreak of malware on Android, and it came from an unlikely source—the Google Play Store. Several established apps have received updates a few months ago that contained an unwanted add-on called either DU Quick Charge, DU Battery Boost, DU Boost Charge, DU Speed Charge, DU Speed Booster, or another name starting with DU.

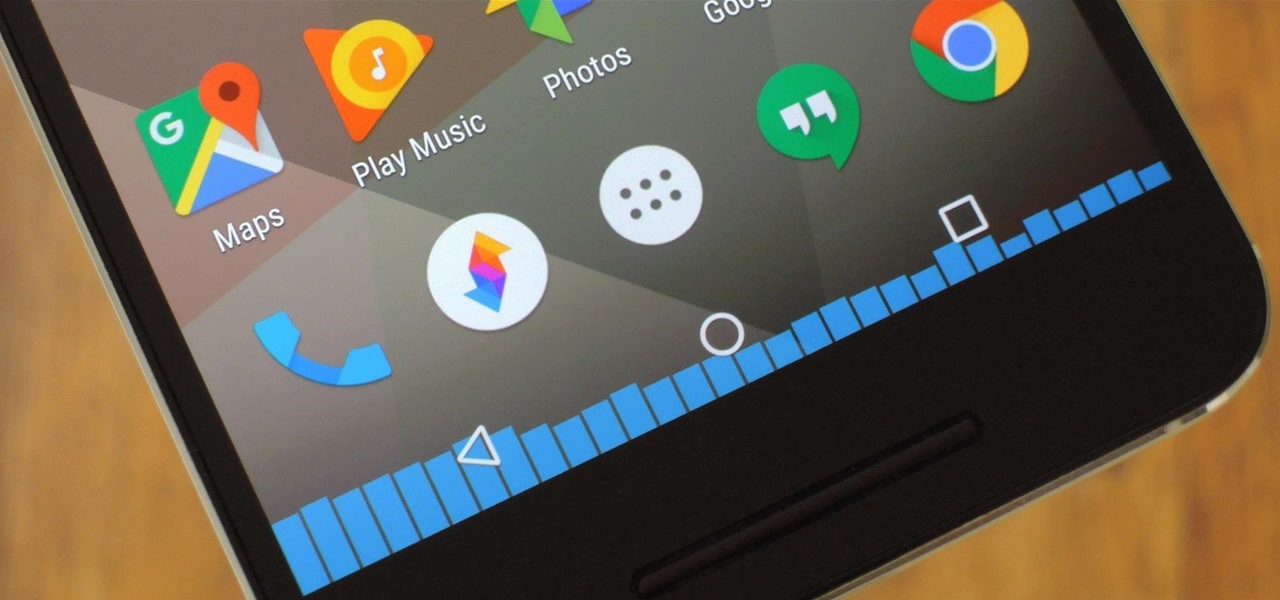
CyanogenMod, the popular custom ROM available for many Android devices, has a nice little feature that displays a music visualizer beneath your on-screen navigation keys while you're listening to your favorite songs. It's a subtle touch, but it makes for a more immersive experience when you're jamming out while using your phone or tablet.

HTC's newest flagship smartphone, the HTC 10, has been met with nearly universal acclaim despite a weak amount of sales over the last few months. Most reviewers point to the device's gorgeous hardware as its main attraction, but at the same time, it certainly has some nice software to match, as this year's Sense 8 may be one of the best manufacturer skins ever.

Augmented reality (AR) holds much promise for how we'll interact with technology in the future, but we still have many hurdles to clear before that dream fully comes to fruition.

This week has been quite a successful one for Google, thanks to non-stop news coverage of their developer-focused I/O conference.

Having your phone on during a movie is a major annoyance to the majority of moviegoers, a fact that some theaters learned the hard way. One major film release is taking a different approach, however, and actively encouraging you to turn on your smartphone—during the end credits, at least. That film would be The Angry Birds Movie, and it's hitting theaters on Friday, May 20th, 2016. Rovio and Sony have been heavily promoting this upcoming 3D animated comedy, and the two worked closely together...

The VLC Player app for Android has a really nice feature that allows you to adjust brightness and volume by sliding your finger up or down on the left or right side of your screen, respectively. It helps keep you immersed in the video while you're in full screen mode, since you don't have to mess around with any popups or overlays to perform these basic functions.

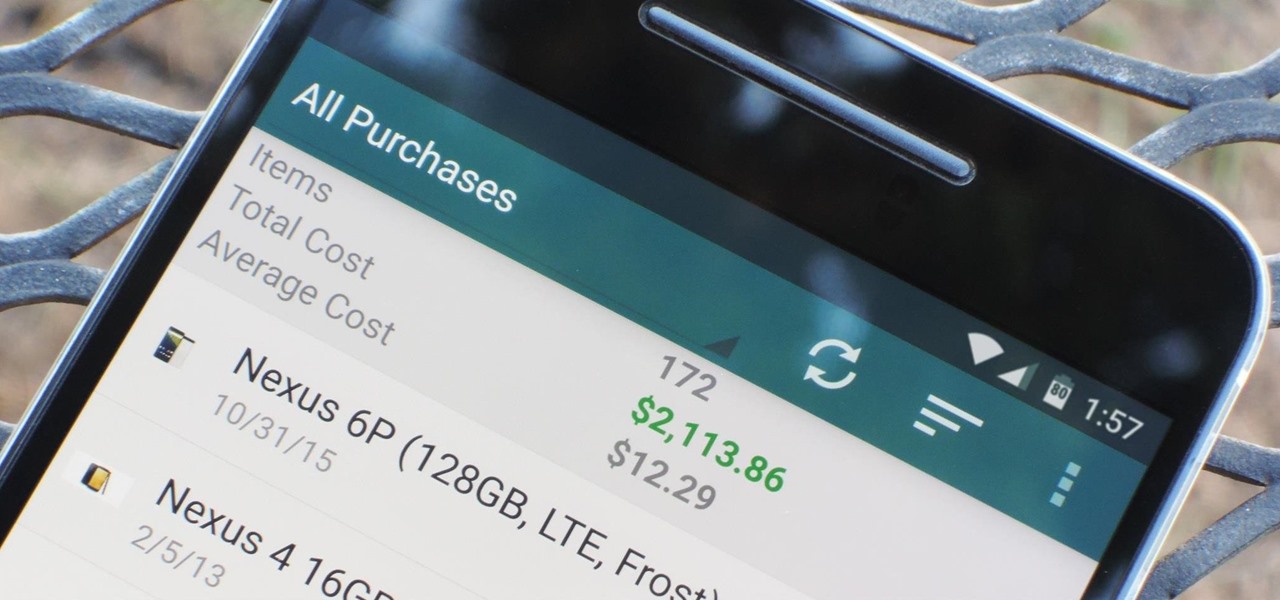
We tend to think of Google Play as Android's app store—but there's far more to it than that. Not only does it allow you to purchase apps and games, but you can also buy movies, music, books, and even devices, plus there's always those pesky in-app purchases that it also handles.

With the FBI getting access to iPhones, and apps like Waze being used to track people's locations, you've got to wonder just how safe and secure your smartphone is... or isn't. When you consider everything you do on your phone, from taking and sharing pictures to mobile banking, keeping your information safe is a crucial step that may seem out of your hands.

Much like the Chromecast, Android TV devices such as the Nexus Player and Nvidia Shield TV have always had those beautiful background images as their default screensaver. However, unlike the Chromecast, these "Backdrop" images, as they're called, weren't always customizable on Android TV.

Welcome back, my greenhorn hackers! In many cases when a computer, phone, or mobile device is seized for evidence, the system will have graphic images that might be used as evidence. Obviously, in some cases these graphic images may be the evidence such as in child pornography cases. In other situations, the graphic images may tell us something about where and when the suspect was somewhere specific.

Welcome back, everyone! In this lesson, I'm going to go over the use of the echo function and variables, as well as basic syntax.

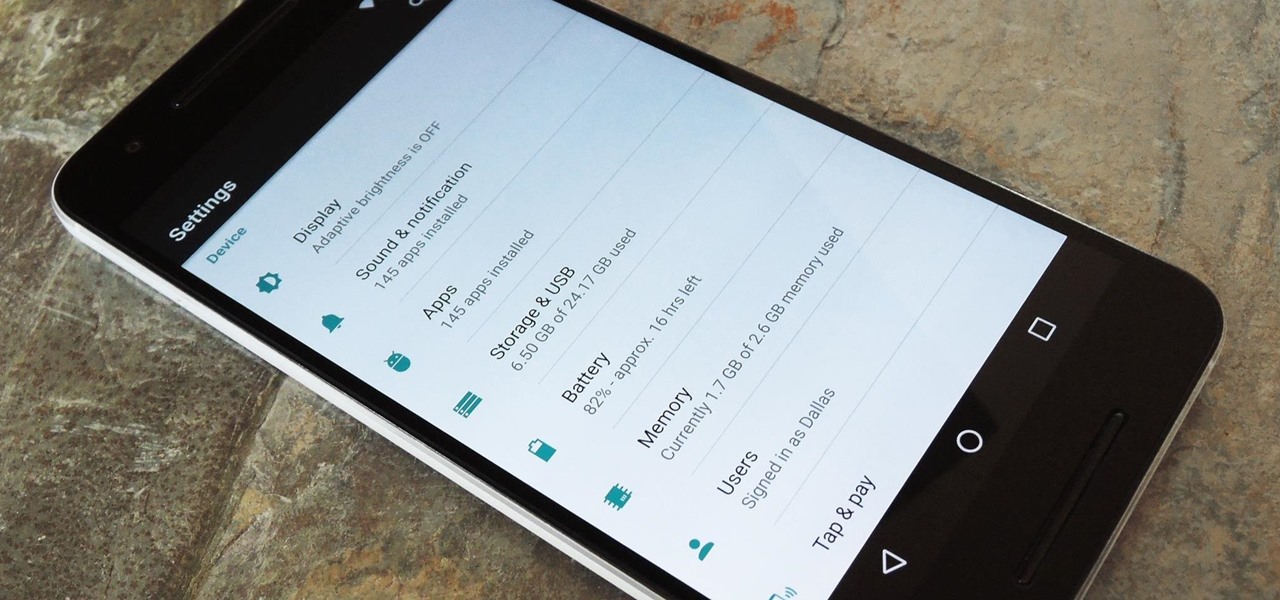
When Android N is officially released sometime later this year, it will bring a lot of cool new features along with it. We've already had the chance to play around with some of these, thanks to a preview build available to Android beta testers, and one change that we like in particular is a revamped Settings menu. Among other things, each settings entry now has subtext beneath it that shows relevant info at a glance.

Since its purchase by Microsoft in 2014, Minecraft has regularly been pushed to new platforms such as Windows 10, Wii U, and Fire TV. In that spirit, Microsoft-owned Mojang has been developing virtual- and augmented-reality versions of the blocky sandbox game.

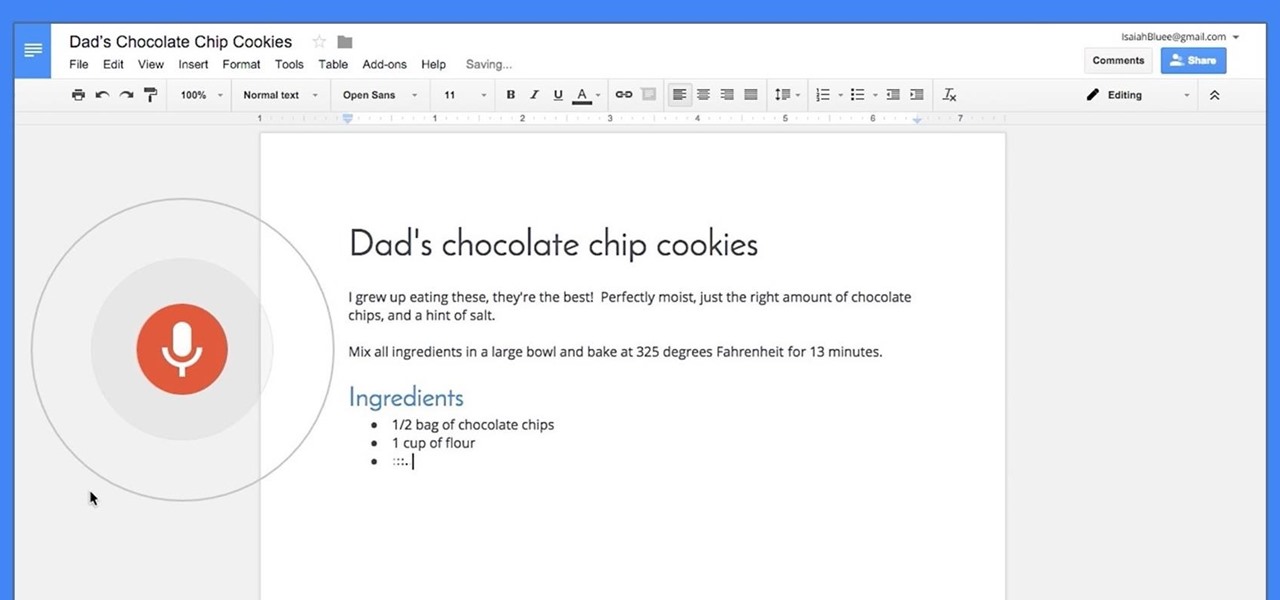
Google launched voice typing for Google Docs last Fall, and followed that up about six months later with voice commands that let you format and edit text as well. You can do things like select text, apply format settings like alignment and headings, and add and edit tables—all with your voice.

In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need

The VLC media player just celebrated its 15th birthday in February 2016, marking a decade and a half of hassle-free video playback for hundreds of millions of users on virtually every major operating system. The free and open-source player is so powerful and easy to use that it has almost completely vanquished all would-be competitors in its rise to the top.

Sony's Xperia smartphones are some of the most beautiful Android devices out there—but unfortunately, they're rarely promoted in the U.S. and are seldom available through major carriers (aside from the new Xperia Z5 devices), so not many Americans are aware of how awesome these devices really are.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

Android's copy/paste menu and text selection options have traditionally been downright terrible, but things are starting to get better with some recent improvements made in Marshmallow. That being said, there's still a lot left to be desired, and there's always plenty of room for more useful functionality.

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

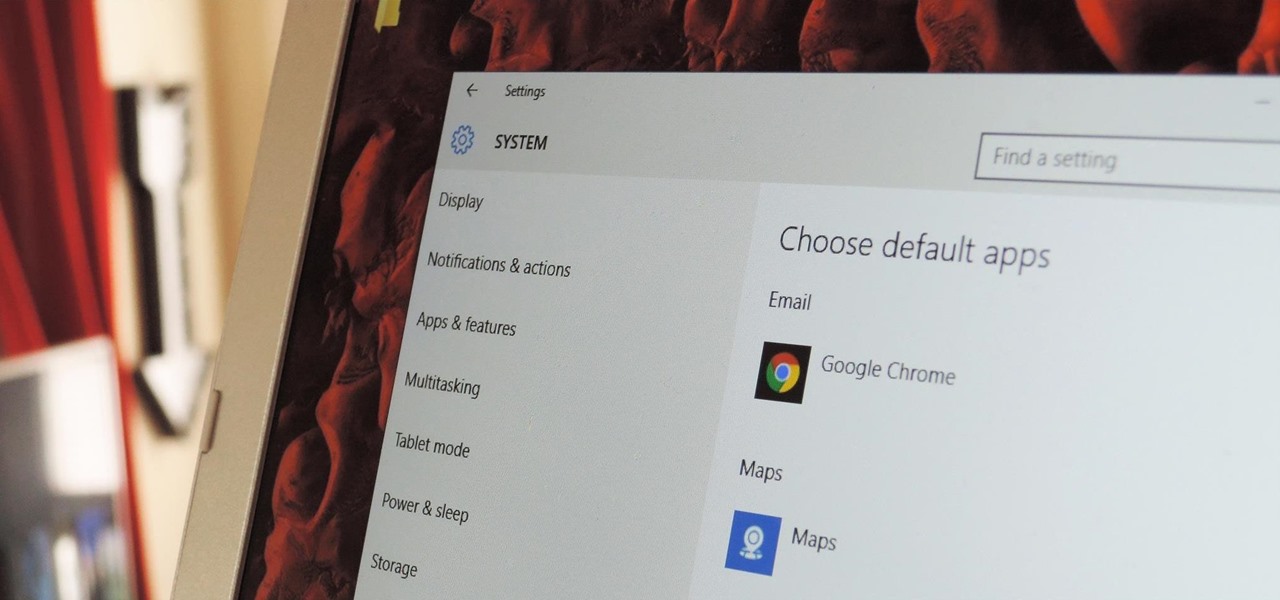
The first time you launch any type of file, Windows 10 will usually prompt you to select an app to open it with. Occasionally, though, this "Open with..." screen doesn't show up, and instead Windows will use a pre-installed system app to launch the file without ever giving you a choice in the matter.

A video showing what is alleged to be the new Apple iPhone 7 has appeared online. The uploader of the video claims that it was shot on one of Foxconn's assembly lines.

The notification light on phones and tablets is slowly disappearing. The once staple feature is now only found on a few devices, and a bevy of other notification systems have sought to fill the gap. The most popular of these systems is Ambient Display, which has grown in popularity with OEMs over the last couple of years; even Google's own Nexus line of phones have made the plunge.

This is a little c++ program that I thought would be handy in the future. Although, I apologize in advance for any errors in the code since I haven't had the chance to compile it yet. Anyway, please if you are a script kiddie please do me a favor and at least read this article fully. :)

Google Play Music has been my go-to music service ever since its release. The free cloud storage for 50,000 songs and full access to Songza-powered radio stations make it a great music app, even without the $10/month streaming service.

Google Maps, in conjunction with the Android operating system, is a powerful tool for navigation that is often underutilized. While it's no secret that it can get you to wherever you're going and back, some of you might not know that you can use Google Maps without even having to touch the screen. Not having to touch your display means you can concentrate on other things, you know, like driving or eating that jelly-filled donut.

With over 10,000 possible combinations, a four-digit passcode may seem secure, but it's fairly easy for someone to crack your code—no matter how clever you think it is. Luckily, there are many other options for securing your iPhone's lock screen—especially if your running iOS 9.

There was one company at the 2015 LA Auto Show that had everyone intrigued. They didn't have a big booth, and they only had one car on display, but they definitely had everyone's attention.

The Xposed Framework was just recently made available for Android Marshmallow, but everything isn't quite back to status quo just yet. Sure, some Xposed modules function properly, but others are a bit buggy, and several don't even work at all. This is mostly a result of changes to the Android system that Lollipop modules relied upon, and such modules will need to be updated for Marshmallow compatibility.

You need a good microphone on your computer in order to make audio recordings, voice chat, or use speech recognition. However, not every computer comes with a built-in mic, and not every built-in mic works great.

Greetings all. I'm back with another informational review of the diversity of utilities for use in the sphere of hacking at your disposal. Today we are going to cover the insides of CUPP (Common User Passwords Profiler) in its entirety. The tool is very basic in nature, as there is little to no configuration needed to get cracking (worst pun ever). So let's get started, shall we?

Hello, fellow hackers. I'm sure we've all seen it somewhere: the undying question of "How do I hack the game so-and-so?" And the answer usually is, "Come back when you actually know how to hack!" But how does one even go about "hacking" a game? What could that even mean?

The new iPhone 6S and 6S Plus models have a really cool feature called 3D Touch that lets you perform app-specific Quick Actions from the home screen for apps that support it. The only downside is that this awesome new feature is not available on older iOS devices.