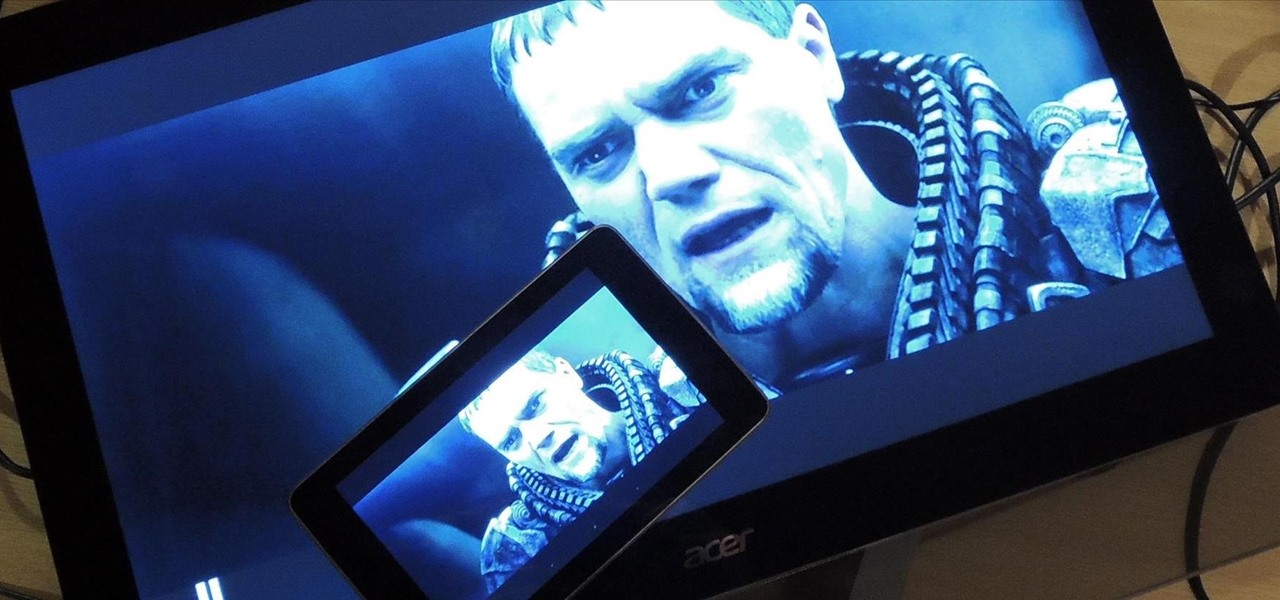
Google announced Android L to the masses at their I/O event, and with it they introduced their new "Heads Up" notification system. These notifications are part of the new Material Design UI and are sure to change the way we interact with notifications on our devices.
When Yahoo! purchased the home screen replacement app Aviate back in January, many were wondering if the internet giant intended to continue development of the launcher or if the transaction was just another acqui-hire.

The Moto X introduced tons of cool features that have slowly been ported over to other phones, like Peek notifications and always listening "OK, Google" detection. Another such feature allows you to twist your wrist to bring up the camera app from any screen—even with the display turned off.

With its growing popularity, it's clear that the Chromecast isn't going away anytime soon, with options for casting games, cloud files, music, and much more. But not all content providers are in a hurry to add support for the device, and SoundCloud is one of them. While My Cloud Player is by no means an official SoundCloud app, it comes pretty darn close.

Last week, I showed you a peek at the not-yet-released Galaxy S5 Active, the more rugged version of Samsung's current flagship. The man behind those leaks, TK Tech News, has now brought another goodie from the device, and it's one we can have on the Galaxy Note 3.

Amazon's Fire TV set-top box has been out for over a month now, and the hacks are starting to come together. Sure you can play your Amazon Instant Video, Hulu, and Netflix content without any issue, but what about your personal media, like movies and music?

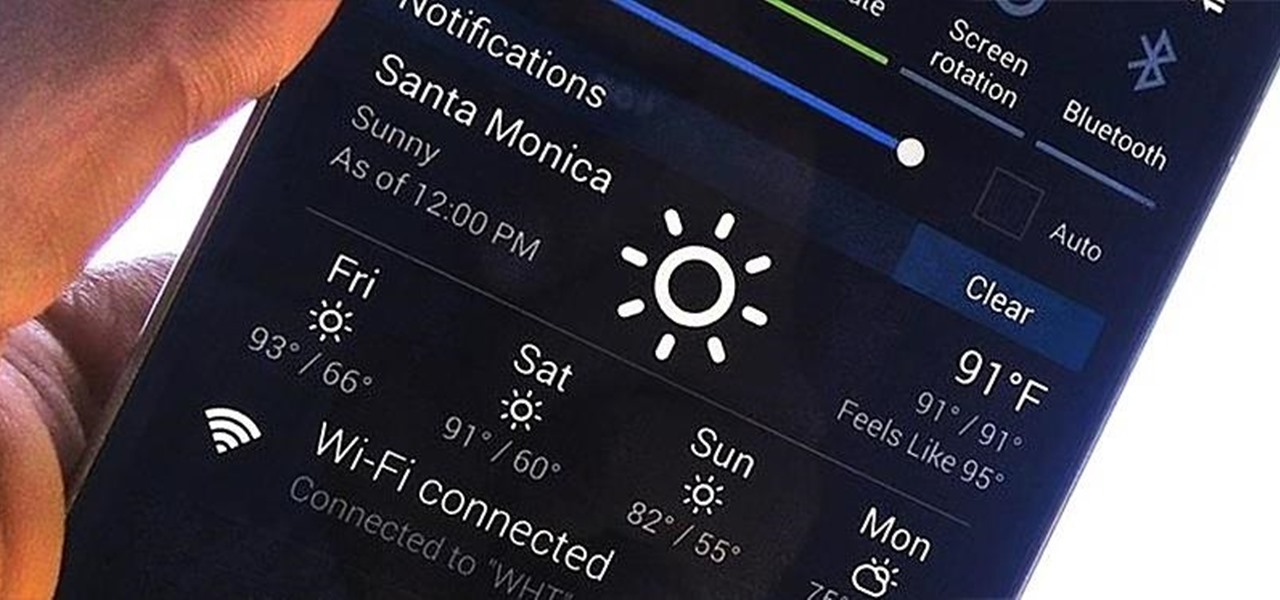
When looking at weather applications and widgets, one major characteristic I look for is efficiency; something that will separate it from the rest of the herd. The stock weather widget looks great on my home screen, but I have to exit whatever app or game I'm in when someone asks me about the weather.

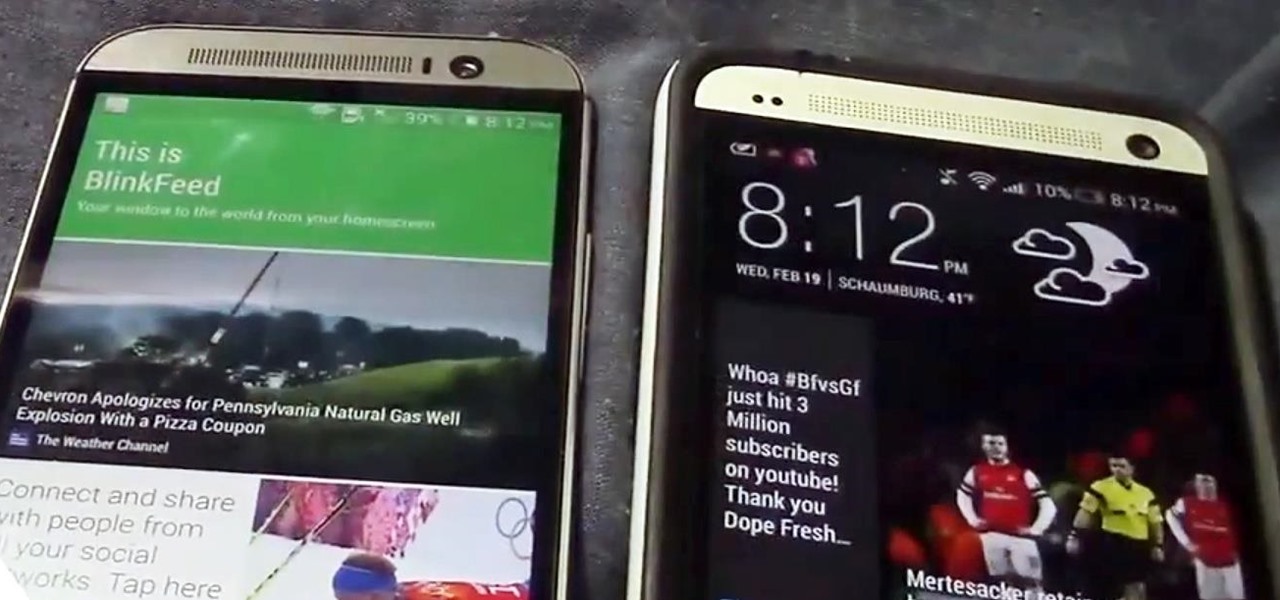
HTC's Sense 6 has been out for over a month now with the One M8, and most of you have probably played around with its better known features, like the new Camera app and Harman Kardon audio.

Veering from common practice, XDA commenter, "the_commenter", discovered a changelog for the upcoming version of Android 4.4.3 tucked away on Google's servers.

The "Knock Knock" features on LG's G2 phone have proven popular and useful enough to spawn various apps and mods cloning these abilities for other devices. Porting the "Knock On" feature to our Samsung Galaxy S3 isn't as easily doable, since developers would need to create a modded kernel, like they did for the HTC One. The "Knock Off" function, on the other hand, is a lot more manageable.

Amazon just announced its entry into the set-top streaming content marketplace with its new Fire TV box. Competing directly against Apple TV, Google's Chromecast, and Roku, Amazon is betting on big processing power and voice controls to stand out from the competition. Features include the following.

I love my status bar. Not only does it tell what time it is and how much battery juice is left, but it gives me cellular connection info, text alerts, and app update notifications. However, one thing is does not give me is customization. Since you're looking at it all the damn time, why not personalize it?

As the Chromecast becomes more and more popular (it's even available overseas now), the market has seen an avalanche of Chromecast-compatible apps. We can play games, cast TV stations, and even mirror our screens, but today I'm going to show you a multifaceted tool that'll do everything from broadcasting your camera to displaying your documents.

If you use your Nexus 7 like me, then you're constantly downloading APKs, installing new games from Google Play, taking a million photos, and using multiple apps at the same time.

Muzei Live Wallpaper is a popular Android app that refreshes your home screen background at set intervals, turning it into blurred pieces of artwork or photography while keeping your icons and widgets in the spotlight.

If you have a limited or restricted data plan, monitoring your usage can be the difference between escaping the month without overage fees or emptying out your wallet.

Confirming a lot of what we already knew, now we have a physical walkthrough video on HTC's new flagship, the M8. Or, maybe the "New HTC One", but let's hope that's not the name of the final product. Before we get to the video, here's what we already know:

Unless you're using something like 360 Vault to store photos and videos, people you lend your iPhone to can easily browse through the gallery without you knowing. It makes me anxious just thinking about it.

With the the general computer users understanding of Information security rising (at least to the point of not clicking on unknown links), and operating system security getting better by default. We need to look for new and creative ways to gain a foothold in a system.

If somebody really wants to gain access to your iPhone, they'll get in. Phone thieves (and mischievous friends) can easily figure out your passcode just from looking over your shoulder or tracing over the oily smudges on the screen. And if you're using popular passcodes, birthdays, and addresses on your iPhone, you might as well disable lock screen security entirely.

Apple's iOS 7 is riddled with annoying features, and some of them can't be toggled off in Settings. For example, I really don't like having labels directly underneath my app icons, and there's no way to remove them. Sure, it may be nitpicky, but it's my device, and it should behave the way I want it to.

I have Verizon, America's largest 4G LTE network, as my cell service provider, but there are times when I find myself with a pretty shitty signal, rendering my upload and download speeds substantially slower than usual.

It's been a great week for Chromecast owners. First, Google released the development kit, allowing devs to install the casting code into their apps. Then, CyanogenMod dev Koush updated his AllCast app to support the Chromecast. That means you can shoot personal movies, music, and photos directly from your Android device over to a Chromecast-connected display.

The inclusion of the parallax effect caused a shitstorm amongst iPhone users when it was released in iOS 7, especially when it came to creating custom wallpapers. It was hard to control, and even disabling it didn't fully get rid of it, making it one of the most hated new features in Apple's latest mobile OS.

One of the best things about iOS 7 is the Control Center, which gives you quick access from anywhere on your iPhone to turning on or off Airplane Mode, Wi-Fi, Bluetooth, and more. It also makes it very easy to adjust the brightness of your display, and gives app shortcuts for your Flashlight, Calculator, Timer, and Camera.

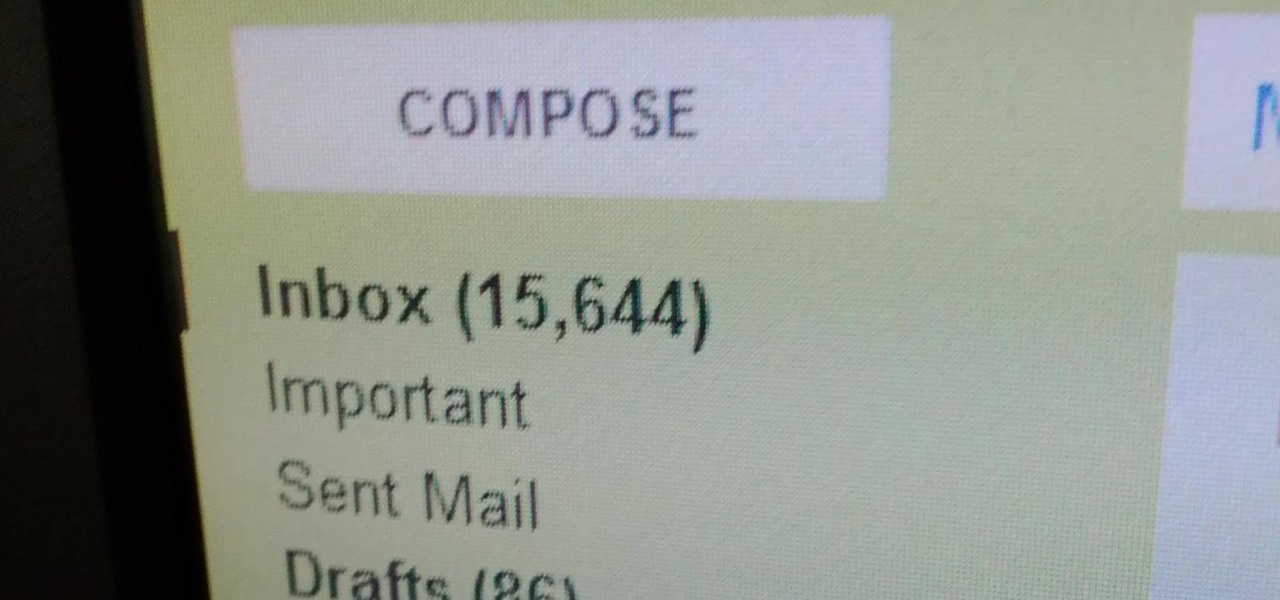
As of this week, Gmail is going to start letting Google+ users email each other using a new option called "Email via Google+." There's nothing wrong with making it easier to get in touch with people you want to hear from, but the default setting allows anyone with a Google+ account to send a message to your Gmail inbox. After the feature is in use, Gmail will start to suggest Google+ connections along with your other contacts as recipients. Email addresses will not be displayed for Google+ co...

Apple has released the third beta of its iOS 7.1 software to developers, just a few weeks after their second beta introduced us to button shapes, a new calendar list view toggle, a hidden Car Display control and several other tweaks and performance improvements.

We have shown you how to get CyanogenMod on your HTC One and Samsung Galaxy S3 in only a matter of minutes. But when modding your phone by installing custom ROMs, you'll often lose your access to Google Apps. Since Google's Apps are very useful (Gmail, Chrome, and Maps to name a few) most people will prefer to have these apps on their custom ROMs. While you can scour the internet searching for individual .APKs, it's hard to find the correct versions to work with your particular system (and do...

For a photo- and video-sharing app based around privacy, Snapchat sure has a lot of security holes floating around. At one time, you were able to take screenshots of Snapchats in iOS 7 without the sender knowing, which is something that you can still do on rooted Android devices.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

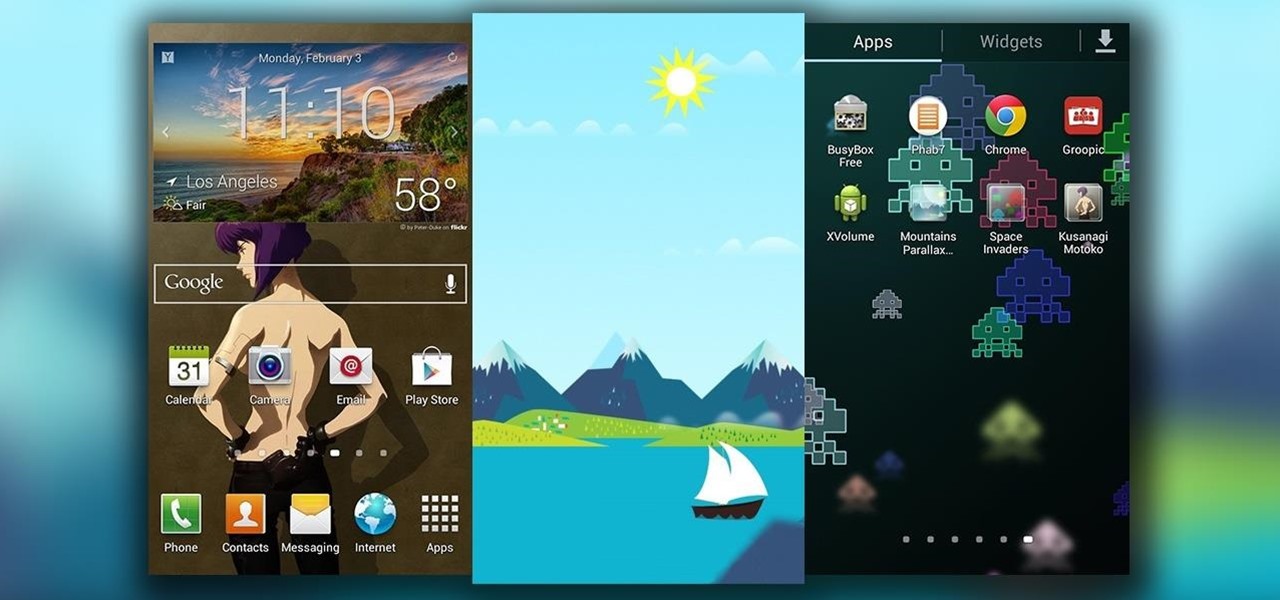
Change is something everyone needs every now and then. President Obama used it as his campaign slogan and adult movie stars use it to hide their real identifies. Change is in itself versatile. You never want to have the same thing day in and day out, and that's why us Android users appreciate the massive amount of customization available.

If you're not acquainted with 500px, you should be. One of the more preeminent photography communities out there, 500px takes you through a journey of incredible shots—anything from nature and urban explorations to cities and architecture to the abstract. Whatever your preference is, you can be sure to find it on 500px.

When life gets boring, you change it up. A little tweak in your schedule goes a long way in making your existence fresh again, and it could be anything from putting on deodorant to seeing a movie with someone you don't know. The more flexible you are in life, the more dynamic it should be.

If you're a self-described multitasker, Samsung has a feature that's perfect for you called Multi-Window, which lets you display two apps on your Galaxy S4's screen simultaneously.

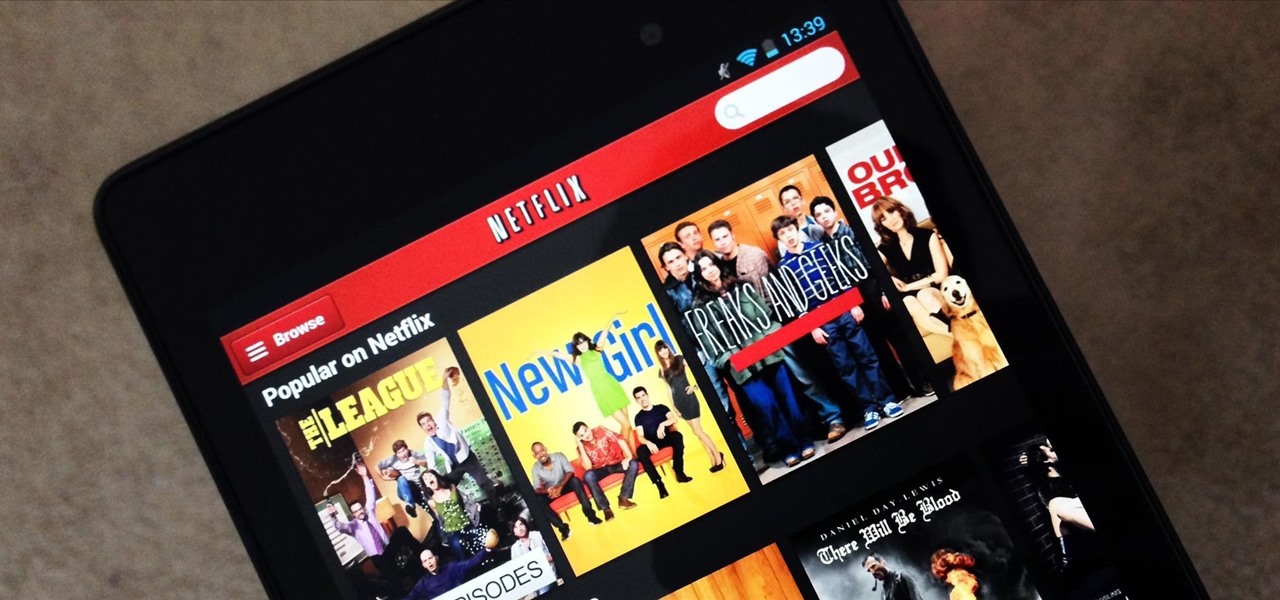
Netflix is more popular now than ever, but it still has a ways to go before satisfying everyone. Whether it's a lack of availability, buggy or unattractive apps, or just not being able to find anything to watch, lots of people have their complaints.

Probably the most favorite custom ROM among softModders is CyanogenMod, a theme-friendly take on stock Android that not only makes it easier to customize your device, but also increases performance using a variety of system tweaks and enhancements.

Android gets a lot of love for its immeasurable amount of customization, and for the most part, you don't even have to do any heinous hacking to swag out your Samsung Galaxy S3 or other Android device.

The new Moto X is still a couple of weeks from being released here in the United States, but that doesn't mean we can't play around with a few of its cool features.

Welcome back, my fledgling hackers! Nearly every commercial enterprise worth hacking has an intrusion detection system (IDS). These network intrusion detection systems are designed to detect any malicious activity on the network. That means you!

Running multiple applications at the same time is one of the Samsung Galaxy S3's and S4's biggest advantages over Apple devices, and it's a fact that Samsung certainly harps on constantly in their well-targeted commercials.