
News: Verizon's $80 'Unlimited' Plan Actually Has Lots of Limits
Verizon launched the $80 unlimited prepaid plan this week and we've found that it actually isn't as limitless as they would have you believe.


Verizon launched the $80 unlimited prepaid plan this week and we've found that it actually isn't as limitless as they would have you believe.

Electrical impulses course through our heart and keep it beating. That's why a jolt from an automated external defibrillator can boost it back into action if the beating stops. But new research says there may be more to keeping a heart beating than just electrical impulses.

We know your time is valuable to you, so starting this week — and continuing every Wednesday — we are going to release weekly Dev Reports that quickly highlight important news and updates that augmented and mixed reality developers should know about.
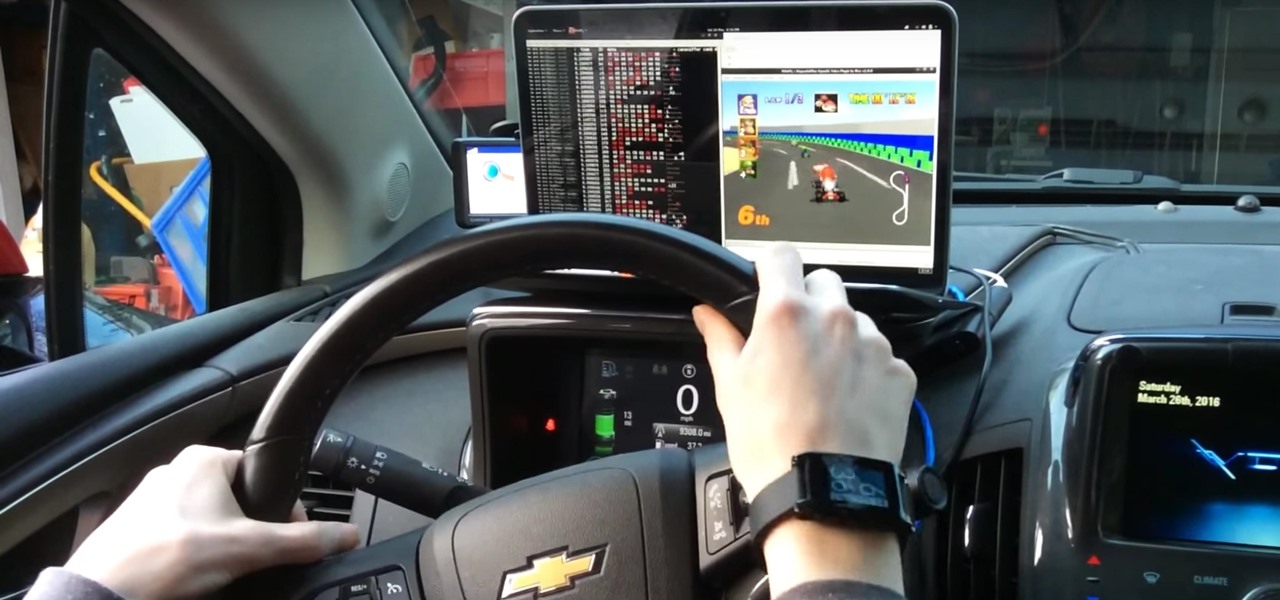
Oh, Mario. The guy that's been a part of our lives since as long as we can all remember. Well, Adam Ringwood and his friends did something pretty cool with one of Mario's most exciting games at the HackIllinois event in February 2016—they hacked a Chevrolet Volt's steering wheel into one big Nintendo 64 controller for Mario Kart.

Some bacteria can already do it—generate electric current, that is—and those microbes are called "electrogenic." Now, thanks to the work of a research group from the University of California, Santa Barbara, we know how to easily turn non-electrogenic bacteria into electricity producers.

In the perpetual search for a renewable and convenient energy source, our bacterial friends have once again stolen the limelight.

For some time now, there has been quite a bit of speculation as to when the selection of augmented and mixed reality head-mounted displays would begin to trickle out to the public. Pricing, availability, and software selection are all issues that will have to be addressed before widespread adoption will start.

How do I get rid of these zits?! Whether its pimples, blackheads, or whiteheads, the name is the same, and the name is acne.

Emojis, for better or for worse, have essentially taken over online forms of communication. And now, thanks to a recently discovered feature in iOS, they are going to change the way you search for nearby places.

The new USB Type-C standard was supposed to revolutionize smartphone charging, but so far, it's done more harm than good. Many cable and charger manufacturers are struggling to keep their products in line with the proper USB-C specifications, so as a result, we now have to check to see if a cable is compliant before purchasing one.
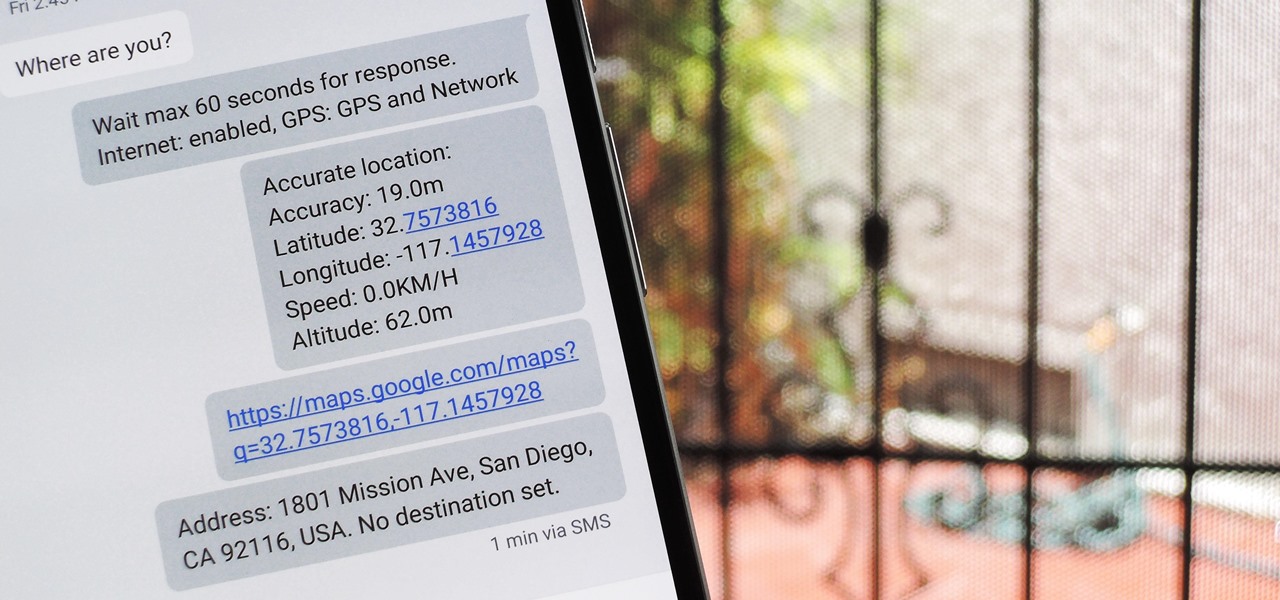
When you're driving, the last thing you need to be doing is messing around with your phone. But these days, people expect you to be available at all times, so the text messages continue to flow in while you're on the road. It's a terrible distraction, and one that is responsible for 25% of all car wrecks in the United States.
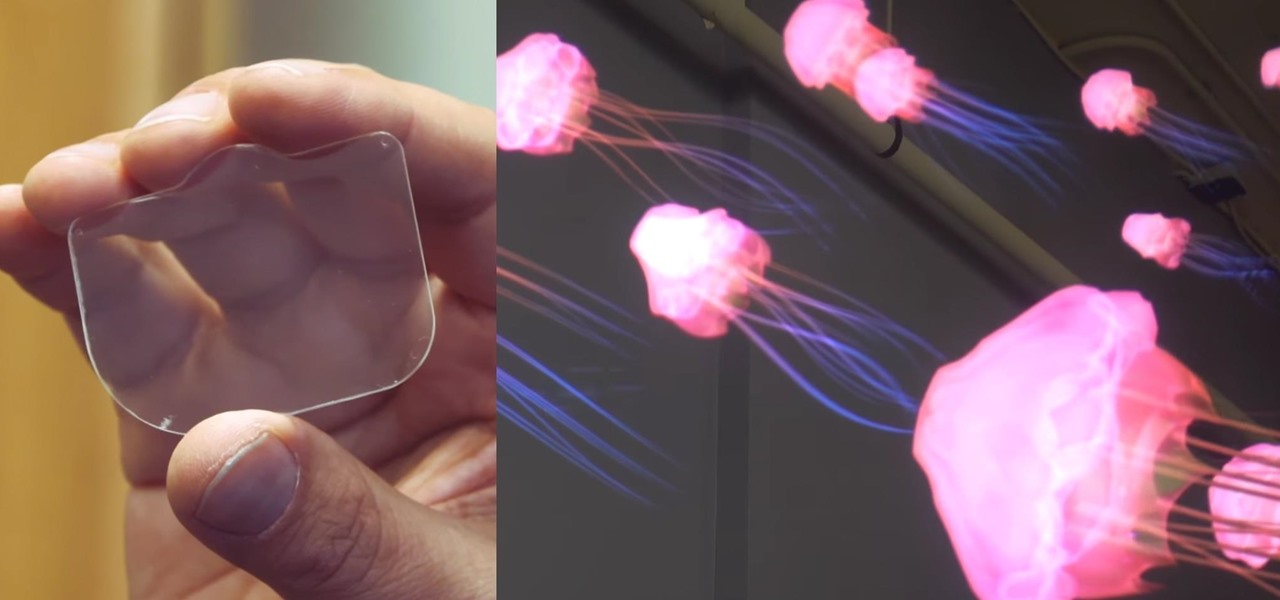
Virtual reality headsets are all the rage these days, and among the menagerie of tech companies gunning for the top spot, there's one mysterious startup that is ahead of the game—Magic Leap—and you can tell just by watching their latest demo video of their product in action.

Video: . For the first prank you're going to need an empty container, preferably black, a smoke bomb and a lighter. I gotta say though this prank is not for just anybody so prank at your own risk. Let me show you how its done, first apply some hot glue on the bottom of the smoke bomb, then stick it inside the container.

A crick is a sudden, spasmodic pain and stiffness in the neck caused by tight muscles that can absolutely ruin your entire day. It can last for more than one day and can be triggered by the smallest movement of the neck, such as a simple pandiculation, aka a yawn-stretch. Although you can't always prevent them, there are many natural ways to lessen a painful stiff feeling in the neck.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

Brought to you by Purdy Paints The art of painting requires excellent tools. And with so many options on the market, it can be hard to find a brand that works for you and your DIY project. That's where Purdy comes in.

When I was in college, I invited a girl over for a date. It was a glorious spring day, and I thought it would be the perfect time to fire up the unused barbecue that had been sitting on my patio all school year. I prepped all the food, chilled all the beer, and then I realized I had no way of lighting the coals for the barbecue.

Welcome back, my nascent hackers!

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

Having someone send you flowers will almost always lift your spirits. Wilting, dying flowers, on the other hand, aren't so great to look at and smell even worse. While there are time-honored tricks to keep flowers alive longer (change the water regularly, put a penny in the bottom of the vase, and cut stems diagonally are three that come to mind), it turns out that a few items in your kitchen are pretty useful at making sure those blooms stay perky.

The drinking straw isn't just there to help you make annoying noises when you get to the bottom of your soda. That little tube of plastic is extremely versatile and can make your life a lot easier with a little know-how. Curious? Read on to find out more.

I'll freely admit that I'm a SwiftKey diehard. I've used the keyboard since its inception in 2010, and it was one of the first apps I ever paid for back in the days of my beloved Sprint Evo 4G. Since then, I've kept up with all its beta iterations, and have unabashedly installed it on various friend's devices.

The use of smart phones is not limited only as a mode of communication now-a-days. There are many things that can be done with the help of a smart phone.

Assuming that you're not going to knit a sweater and celebrate New Year's Eve with Ryan Seacrest and Jenny McCarthy on ABC's “New Year's Rockin' Eve," it's a pretty safe bet to say that you're probably going to consume alcohol—a considerable amount of alcohol.

So, here we are with the second part to whats going to happen to Minecraft in 1.7 (you can see the first part here). Let's start off with the new biomes.

Wondering how to get long hair naturally? How do you grow your hair? In this video Rachelle and Sam give you 10 tips to get those long locks naturally!

Here's how to make dry-ice at home, or wherever you feel like it! All you need is a pillow case, and a CO2 fire extinguisher.

A common problem on bumper covers is that the tabs that attach the bumper to the car get broken. This is critical, as this is what secures and aligns the bumper cover. Many times, a broken tab is all that is wrong with the bumper cover. With the cost of these plastic parts $200 to $700, the replacement cost can break the bank.

There is never a dull moment when it comes to the internet. You can find practically anything you want, whenever you want it. To make that process even smoother and more direct, companies have created a bunch of apps designed to help you find what you're looking for, or enlighten you on a subject you may not have even thought of yourself.

Winter is coming... and if you don't get that Game of Thrones reference, it's okay, you're still cool in my book.

Hello! My latest interest is screenwriting. I would like to share a few hints I find quite useful. I am a newbie, so the following post will not be taken from the treasury of many years of experience. Just plain facts,.. Thanks for reading! Step 1: In the Beginning
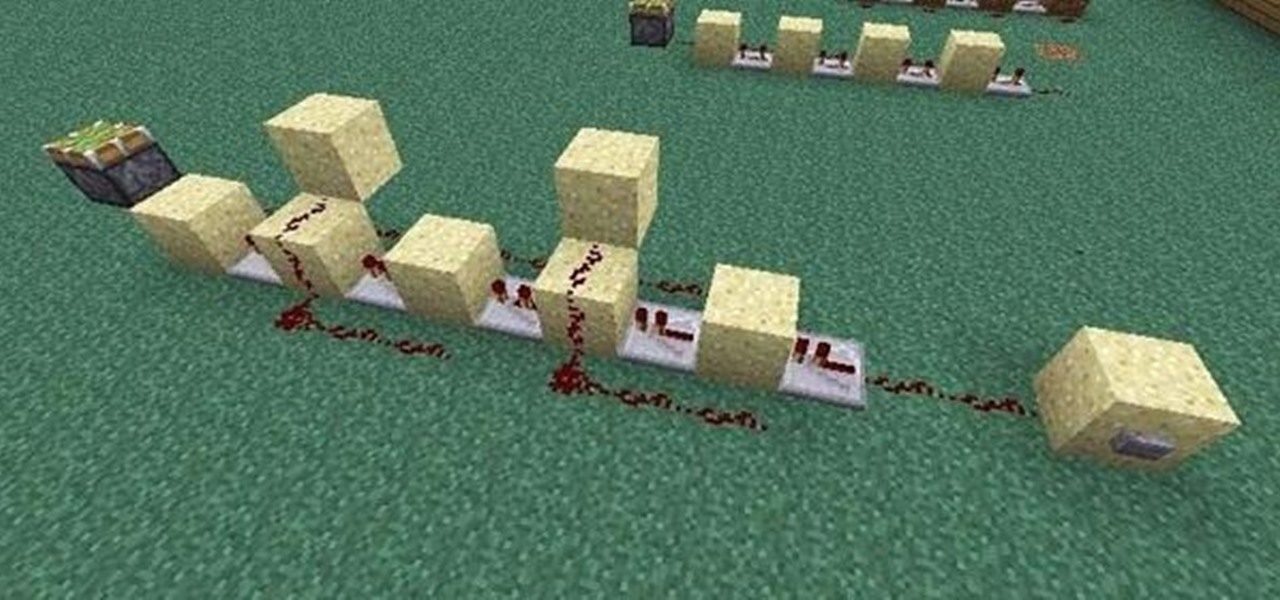
If you're like me, the words 'monostable circuit' mean nothing to you. Until just recently, I had no idea what a monostable circuit did, or why anyone would ever need to use one.

What's the first thing you would do once you realized you were lost in, say, a desert? If you're like me, you would immediately pull out your cell phone and start dialing every number. But what if you have no service? What if your battery is dead?
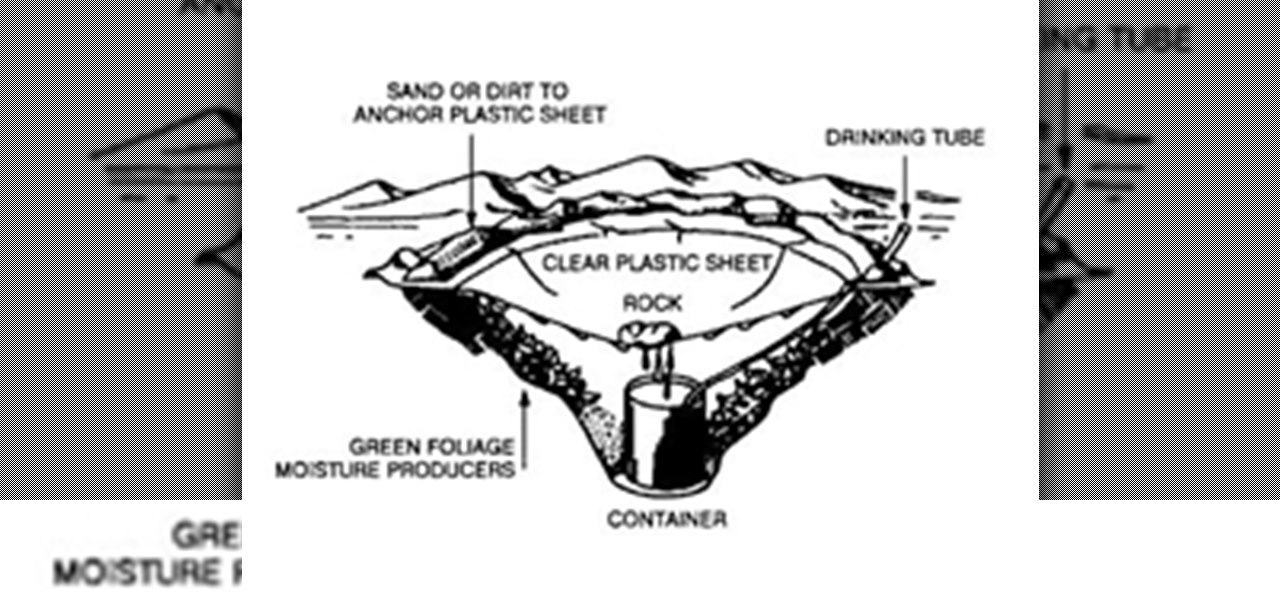
It’s called Urophagia—the art of consuming urine. There could be any number of reasons for having the desire to drink your own urine (or somebody else’s). There’s the so-called term “urine therapy,” which uses human urine as an alternative medicine. In urine therapy, or uropathy, it’s used therapeutically for various health, healing, and cosmetic purposes. There’s also those people who drink urine as sexual stimulation, where they want to share every part of each other. And then there’s the o...

Keeping your golf bag neat can save you a ton of time on the course. If you aren't quite Tiger Woods and don't have your own caddy, check out this tutorial. In it, you will learn the best way to organize your bag and keep the game flowing. When arranging a golf bag, it's important to separate the clubs into three sets, including the woods, the middle clubs and the short irons. Find out how to arrange golf clubs in a descending order with the short irons in front in this helpful clip.

In this video tutorial, you'll find a video demonstration of ironing a suit jacket with the PRIMULA Flex 1242 table and a Vapormat steam generator.The PRIMULA Flex 1242 ironing table has a working surface 120x42cm with a sleeve ironing buck. The board also features suction and blowing with stepless adjustment of air flowing, automatic interchange suction or blowing from the working surface to the buck in addition to heating of the working surface and buck. The technical parameters are as foll...

Once again, Samsung has certified its flagship Note series with an IP68 rating. With this rating, the Galaxy Note 20 and 20 Ultra have some degree of dust and water resistance.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.