Solutionsbyscott teaches you how to organize and declutter your closet. You start out by taking all of your clothes out of the closet first. You then place them in piles of things you wear daily, things you only wear sometimes and things you don't need anymore. You have to be honest in order to make room in your closet. Now you only have one horizontal pole for hanging clothes. To make more room you elevate the first pole and add a second one. Now you have doubled the space in your original c...

Need to know how to hold your pool stick? Well, learn these effective finger positions to elevate your game to a new level. Open bridges are for limited use only! Have you ever seen a professional pool player with an open bridge only?

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

Personification of the Infinite Consciousness. Lord of Hosts. Master of the Universe. These are just three of the hundred-odd titles of the Hindu god Ganesha. Luckily, drawing the Hindu deity Ganesha isn't so complicated.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

Android 9.0 Pie moved the status bar clock from the right corner to the left to accommodate phones with notches, but there's one major downside for Samsung users: since no Galaxy phones have a notch, all this did was take away space for the notification icons that would otherwise start from the left corner.

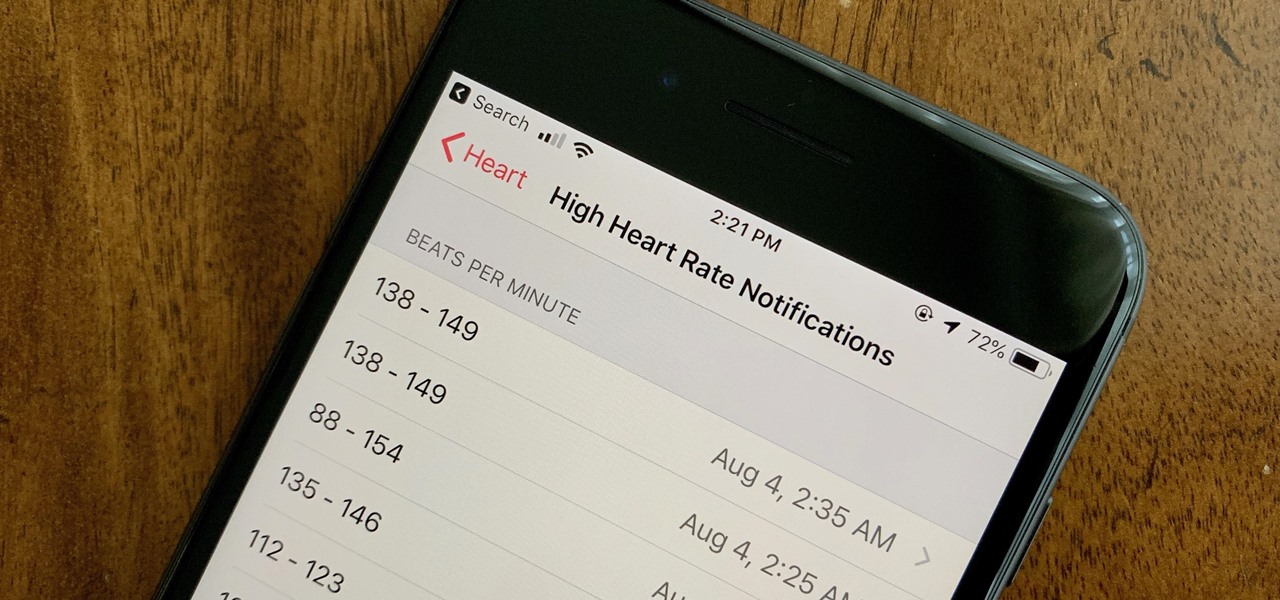
Your Apple Watch sends you notifications from friends, family, and the apps that are important to you. Occasionally, however, the watch may scare the heck out of you with a notification warning of an abnormal, elevated heart rate. If you have no history of heart conditions, this alert might come as a shock. Why do you have a high heart rate, and what are you to do with the information?

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

HIV-infected people who are treated long-term with antiviral drugs may have no detectable virus in their body, but scientists know there are pools of the virus hiding there, awaiting the chance to emerge and wreak havoc again. Since scientists discovered these latent pools, they have been trying to figure out if the remaining HIV is the cause of or caused by increased activation of the immune system.

Backdoors are convenient to leave behind once you've already found a way into a server, and they can come in handy for a variety of reasons. They're good for developers who want a quick way into machines they're working on, or for systems administrators who want similar access. Of course, backdoors are also a hacker's best friend, and can be added in a variety of ways. One good tool for doing this is Weevely, which uses a snippet of PHP code.

Coffee mugs: nothing proliferates more quickly in my kitchen cabinets. People are always handing them out as gifts or as swag, plus I always seem to find a vintage model or two at a garage sale that I'm compelled to buy. I used to do a yearly purge of my excess muggage, but it turns out it's a good idea to hold on to one or two extras.

While holographic Whitney Houston is hitting the road, a new mobile app is bringing volumetric captures of up and coming performers directly to the iPhones and iPads of fans.

Thanks to improvements in technology, AR has become more prominent on our phones. With all the power of the Galaxy Note 10 and Note 10+, Samsung decided to add some pretty nifty AR features. One of these is the new AR Doodle mode, a feature that will make your videos pop.

The S Pen in the Galaxy Note 10 and 10+ has improved to make remote usage even easier. Controlling your phone with just the stylus is no longer a party trick, as you can now move around and take actions in both first-party and third-party apps. One of the best examples of this is the Camera app.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

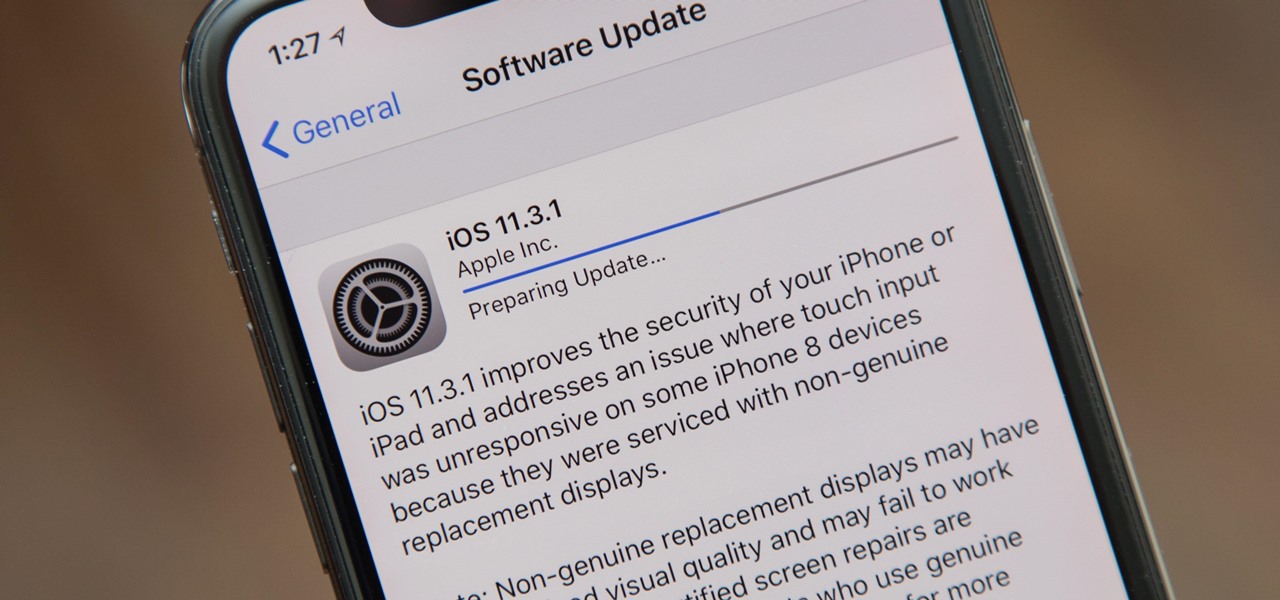
Apple released the iOS 11.3.1 update for iPhones on Tuesday, April 24, 26 days after the official release of iOS 11.3 and eight days after the iOS 11.4 beta 2 update. It is the first minor update to iOS 11.3, and the biggest thing in it is a fix that lets displays fixed by third parties work again.

We may not know what Magic Leap's product looks like. And we haven't received even a "save the date" for its launch. But we know that it will display mixed reality comics from Madefire when whatever it is arrives.

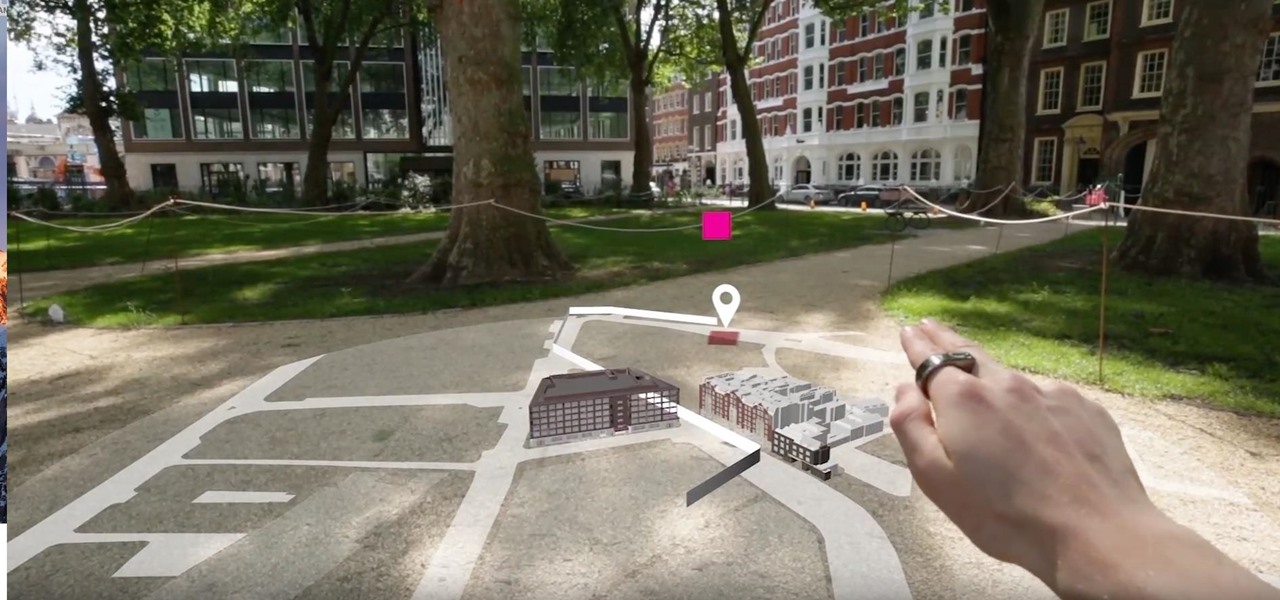
Forget what you know about controlling augmented reality experiences. "Scroll" lets you interact with augmented reality using a much more subtle approach: A ring.

A new study shows the Zika virus is present in saliva — but it may not be enough to make you sick. The Centers for Disease Control and Prevention notes there is "no evidence that Zika can be transmitted through saliva during deep kissing." Given the results of research published in the journal, Nature Communications," the agency may need to revise its guidance.

The number of households in the US that go hungry because they lack money for food hit a high of almost 15% in 2011. While that number continues to decline, nearly 13% of American households still go hungry.

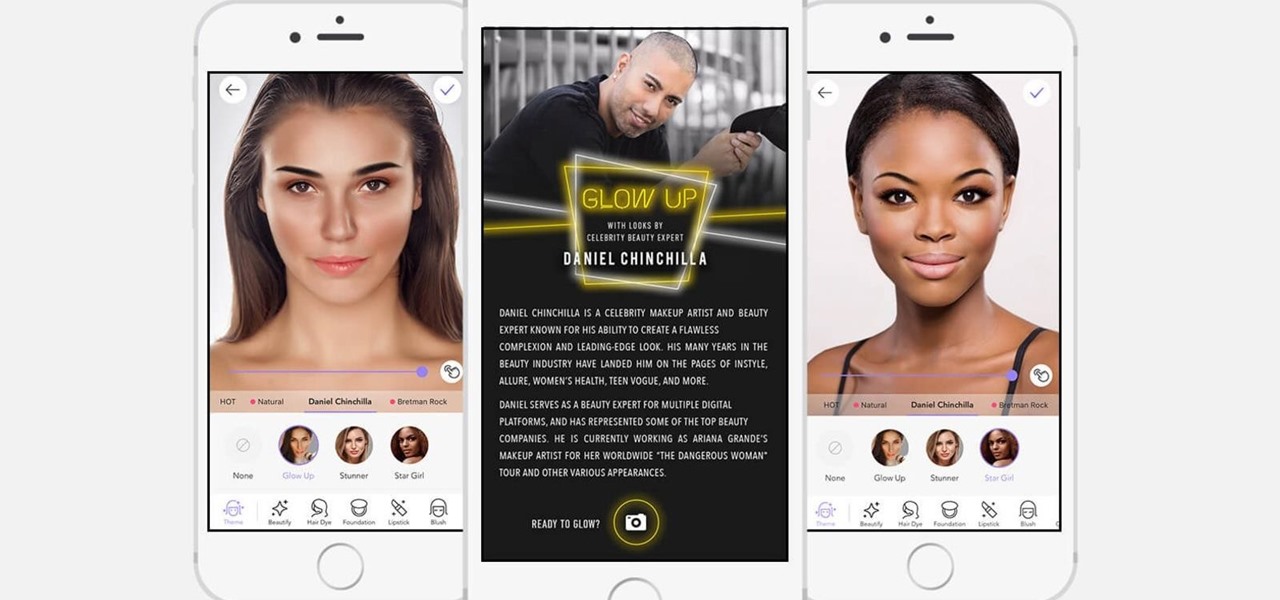
If it's not official by now, it really should be: if you're going to sell cosmetics, you need an augmented reality app. Of course, that's not all augmented reality is good for. It can be used to animate medical models and engage sports fans. Read on below…

The evidence is mounting and is becoming indisputable: Gut bacteria play a role in strokes and heart attacks. The link may seem a little far-fetched, but cardiovascular disease may have less to do with what we eat and more to do with what chemicals gut bacteria make from the food we eat.

It's hard to argue with the notion that wine and pasta are a winning combination. I mean, millions of Italians can't be wrong.

While seltzer water is commonly consumed as a beverage (and a healthier alternative to carbonated soda), it is less known as a fantastic addition to many familiar recipes. The bubbles in seltzer water expand when heated, and when added to certain foods, it instantly allows them to be lighter in taste and texture.

In my household, we are frugal and somewhat picky eaters, so we have to be a little creative with the things we buy. We like to purchase items that can be used in multiple dishes to reduce cost—and because it's just more practical. Pancake mix is a favorite because it can be used in various dishes where any type of breading may be involved. To help inspire you, here are some of my favorite ways to use pancake batter at home.

Nowadays, it feels like you can't talk about eating healthy without bringing up quinoa. Quinoa (KEEN-wah) has been the "superstar" of the health movement for a while; 2013 was declared the International Year of Quinoa by the United Nations, and has only continued to grow in popularity with both health nuts and culinary experts alike through the past few years. The true testament to quinoa's success has been its eventual integration into our everyday lives. Quinoa is now very accessible to fol...

My French press is one of the most important tools in my kitchen. It's indispensable, and it's no small exaggeration when I say that I use it on a daily basis thanks to my coffee addiction. However, it gets used for a lot more than just my morning cuppa (and my second morning cuppa, and my late morning cuppa, and my... well, you get the picture).

Onions add essential flavor to almost any dish, whether it's a sauce, main dish, or salad. They are one of the humblest "superfoods," full of vitamins and nutrients but generally inexpensive, which is why they're also one of the most widely eaten ingredients in the world.

There are certain ingredients that chefs regularly use to elevate their food beyond the status of what us mere mortals can create. Shallots are one. Good, real Parmesan cheese is another. And the rind of that real Parmesan cheese just so happens to be one of the culinary world's biggest kept secrets.

Every year, when summer rolls around, I get excited because it's grilling season. And every year, when summer comes to a close, I get sad because grilling season is ending.

I've always had an affinity for pretty wine bottles. When I was younger, my parents and my siblings would give me their empty wine bottles so I could collect them, and I loved every single one.

When I was in college, I invited a girl over for a date. It was a glorious spring day, and I thought it would be the perfect time to fire up the unused barbecue that had been sitting on my patio all school year. I prepped all the food, chilled all the beer, and then I realized I had no way of lighting the coals for the barbecue.

Summer is right around the corner, which means it's time to switch from perfect hot coffee to perfect cold coffee. A nice icy glass of cold coffee is wildly refreshing and just plain delicious. In my opinion, it's the key to enjoying any sunny day (warning: if you don't already drink cold coffee, you may find yourself drinking four or five glasses a day very quickly).

Beef: it's what for dinner. And if you really like the taste of it, it can be what you season the rest of your dinner with, too.

Perhaps the best part about Easter is the fact that, even after the day is over, there's usually still a lot of candy left. Jelly beans, gummy bears, Cadbury eggs, peanut butter cups, marshmallow peeps — there's no end to the sugary goodness in your awesome Easter basket. Yet as much as I love stuffing my face with brightly colored candies, it's easy to get sick of them halfway through the basket.

Planning a Super Bowl party, or any football-themed party for that matter, can be fun for even the most craft-adverse host, as almost anything brown can turn into a football with just a little decoration. With a little planning, you won't be serving up any Pinterest fails this Sunday night.

Potatoes are one of cheapest, most nutritious whole foods that you can make and eat. Is it any wonder you can find budget-friendly, low-fat potatoes in every cuisine in the world?