This is a very exciting time for mixed reality developers and fans alike. In 2017, we have seen a constant stream of new hardware and software releases hitting the virtual shelves. And while most of them have been in the form of developer kits, they bring with them hope and the potential promise of amazing things in the future.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

Thanks to Project-Infrared, there's now a pretty straightforward way to add motion tracking to the HoloLens: Connect it to a Kinect.

As one of the most powerful Android apps for connecting your phone or tablet to your other devices in various ways, Pushbullet had always been a fan—and Gadget Hacks—favorite.
As a hacker or an aspiring one, You need to be careful and anonymous if your doing anything illegal. But you slipped up. Now someone is tracking you! Well luckily you read this post ahead of time and have a backup plan!

NFC, or near-field communications, is a hardware feature that has been built into most Android phones for the last four years. It's essentially a low-power data connection that can be used to initiate a quick command by bringing your device within range of a compatible receiver, be it tap-and-pay with Google Wallet, a file transfer via Android Beam, or a Tasker profile triggered by a specific NFC tag.

Watch to learn how to replace the HEPA filter on a Dyson DC07 vacuum. This Dyson spare parts video we show how to remove and replace the Dyson DC07 Pre Motor Filter and Dyson DC07 HEPA Post Motor Filter. This vacuum maintenance video also outlines the Dyson airflow path as well as removal and replacement of the Pre Filter Housing, Post Filter Lid and Filter Seals. Prevent loss of suction and motor cut out by changing the filters on your Dyson.

Watch to learn how to remove and repair a Neff oven door. You'll remove and replace parts on an oven door, as well as how to remove the oven door. This oven maintenance video demonstrates removal and replacement of the oven door outer glass, oven door inner glass, door hinges and door handle. Use a professional oven cleaner and ceramic scraper to remove burnt on stains from the oven inner door glass.

Watch to learn how to replace the door seal on a Neff refrigerator. You'll remove and replace the fridge door seal on a Neff fridge. Replacing the fridge seal is an energy saving tip: If there is a fridge door seal gap, you will not create the correct fridge temperature to store food. To increase fridge efficiency fit a new seal. As part of this fridge maintenance video we also replace the fridge door bottle shelf and use a professional fridge cleaner.

Watch to learn how to replace a knob on a Neff gas hob. You'll remove and replace a gas hob knob on a Neff gas hob. Replacement knobs as well as burner caps and flame spreaders are easy hob spares to replace. As part of hob maintenance we also use a specialist hob cleaner to get a nice clean hob. This hob maintenance video clip illustrates the many different hob parts

Download the P2 Step-by-Step Reference Guide. With Avid, editing footage captured with the Panasonic HVX200 camera is fast and easy. Avids system uses the same native file format as Panasonic P2 memory cards, so theres no need for any transcode, capture or file conversion process at all. You can edit directly and immediately from the P2 cards if you like or have Avid Media Composer create a rapid backup of your files. Nothing could be simpler or more immediate.

This video is on how to install the LED light kit onto your Axon Racing anti-gravity razorback racer hover.

Bridge is one of the most popular games in the world. The rules may seem overwhelming, but all you need are a few easy steps to learn the basics.

Farmington (MN) HS head softball coach Heather Ballstadt demonstrates a full arm drill to warmup for throwing. Throwing and catching a ball is an essential part of softball. Follow along in this sports how-to video to learn how to catch with two hand and over your throwing shoulder. Catching over your throwing shoulder is a good strategy as it allows for a good setup to be in position when playing catch.

An overview of the setup process for Windows SharePoint 3.0 2007.

Boner Jones from bonersgames.com shows his setup for recording his gaming with his computer. He uses a tv tuner card.

This is a tutorial on how to secure your wireless network. This tutorial shows you how to setup a WEP encryption key for your wireless network.

Video shows how to setup a Nano tank for fish. Subtitled steps and clear demonstrations will have your Nano tank up and running in no time.

Video covers the steps into giving your cat a bath. Subtitled steps and clear demonstrations will have your cat looking cleaner than ever.

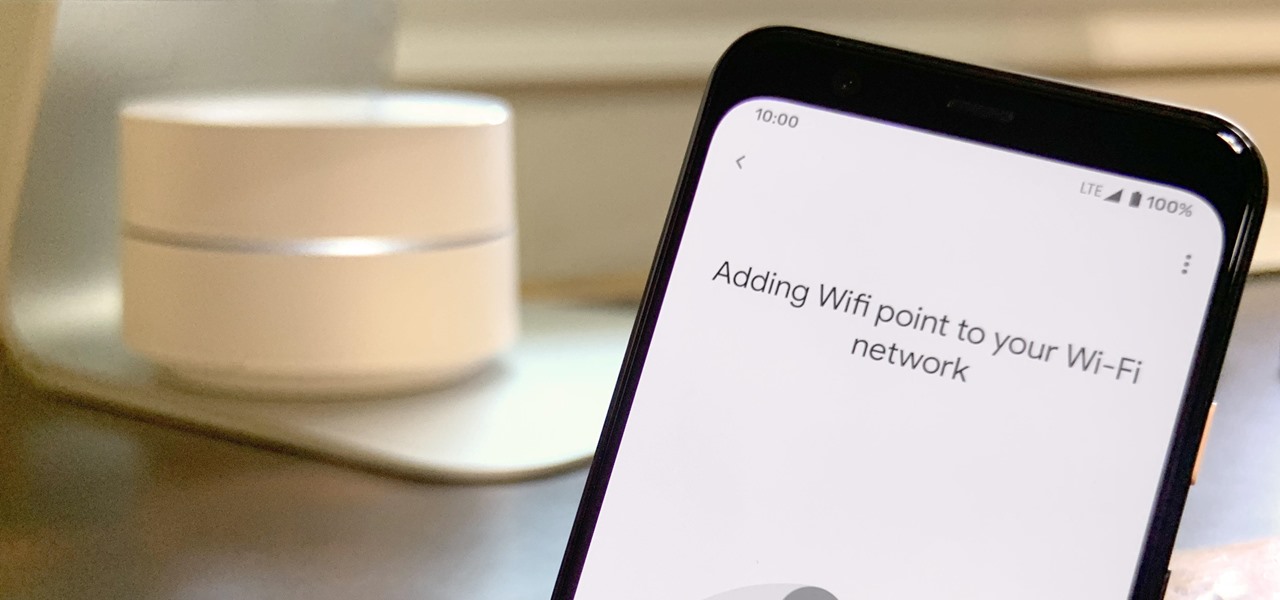
Google recently released a new mesh router known as Nest Wifi. The updated and rebranded Google Wifi brought many improvements, such as faster processing power and an increased level of wireless security called WPA3. But while it's not enabled by default, you can still get the new WPA3 security on your original Google Wifi.

Google is known for merging older products into a new one's ecosystem for ease of use. The transition can take time, and that's the case with the old Google Wifi system now that Nest Wifi is out. Google is working on phasing out the dedicated Google Wifi app in favor of using the Google Home app for all your IoT needs.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

It's new phone season — new handsets are releasing every few weeks, we're seeing endless software updates, and the holidays are right around the corner.

The triple camera system on the OnePlus 7 Pro is the best setup they've ever done so far, but it could always be better. The primary sensor packs a whopping 48 megapixels, but as history has taught us, megapixels don't equal better photos by default. In fact, with where we are in terms of hardware right now, it's the software that determines a phone's camera performance.

Though many were hoping for it, a notification indicator around the Galaxy S10's front camera punch hole never came to fruition. Since then, we've been finding other uses for the camera cutout, from turning it into a circular battery meter to using creative wallpapers. Thankfully, there's now an app that will give you LED-style alerts with a ring around your S10's camera.

If you ever want to root your OnePlus 6, install TWRP, get Magisk and Xposed, or flash a custom ROM, the first thing you'll need to do is unlock your bootloader.

Essential just dropped the Oreo Beta Program for their flagship PH-1 phone. Users have been eagerly awaiting this update as the early Nougat builds of the PH-1 software have suffered from numerous performance issues and lag. The good news is that you can grab the Oreo update today with a few simple steps.

Alright, let's dig into this and get the simple stuff out of the way. We have a journey ahead of us. A rather long journey at that. We will learn topics ranging from creating object filtering systems to help us tell when a new object has come into a scene to building and texturing objects from code.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

In the music world, it's safe to say electric instruments are more versatile, but they lack the portability of their acoustic counterparts. However, with the aid of your smartphone plus an audio interface, you can play your electric instrument anywhere — with all the pedal effects you please — and even record your efforts.

The LG G6 was officially announced by LG at Mobile World Congress 2017 in Barcelona and released in the US on April 7, 2017. The device is almost exactly what we've been expecting from all of the rumors and leaks building up to its release. The modular design we saw in the G5 is gone, taking the removable battery with it. However, we do gain waterproofing, an improved dual-camera setup, a larger screen with smaller bezels, and Google Assistant.

We recently covered an app called Fingerprint Quick Action that let you use your fingerprint scanner to expand your notification tray like the Google Pixel, along with a few other actions. It's definitely a useful mod, but there's a similar app can make your fingerprint scanner do almost anything—literally.

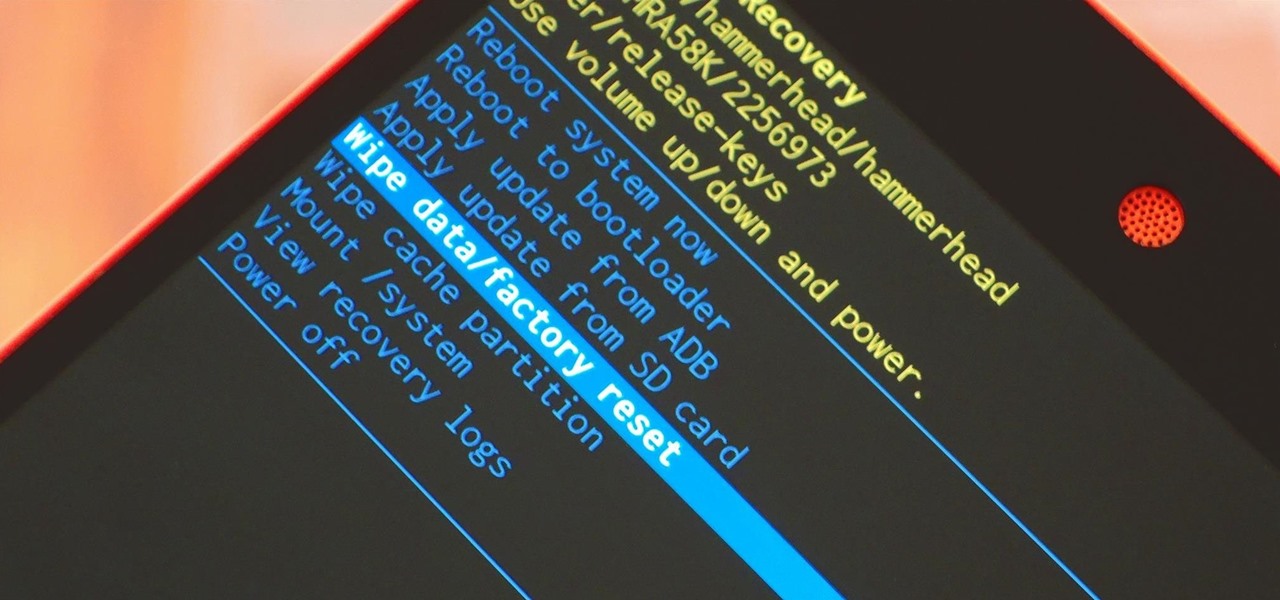
When it comes time to sell your smartphone or trade it in for your annual upgrade, you'll have to make sure that all of the sensitive data the device accumulated while you owned it is properly erased so that no one else can access it. This process is referred to as a "Factory Reset," and regardless of if you own an iPhone or Android device, like a Samsung Galaxy model, HTC One, or Nexus, I'll show you how to do it below.

When most people think of "gaming computers," they're probably thinking of Windows-based PCs. They offer a huge variety of devices with better equipped software and hardware for a cheaper price, and there are more available games than there are for OS X-based systems.

If you remember last time, we successfully uploaded picture with a small hidden PHP command executer embedded in it onto a server. Now, our goal is to take this a step further and get an interactive shell. To do this, we need to upload another file that either binds a port for us, or connects back. For this tutorial, we will use a Python reverse Meterpreter shell.

When it comes to getting your computer and smartphone to work well together, there's no service more robust and capable than AirDroid. For years, it's been the go-to tool for users looking to transfer files between their devices or access contact lists and call logs from their computer.

Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.

One of the more talked-about features of Google's new flagship device is the fact that all of the data on the Nexus 6 is encrypted by default. At face value, this certainly seems like an added bonus for the 6-inch phablet, especially in this day and age with growing security concerns abound. It's definitely something that the FBI is none too pleased about.