
News: What Google's Upcoming Andromeda OS Means for Android & Chromebooks
Google is working on something so big they had to name it after an entire galaxy: A new operating system that merges Android and Chrome OS into one unified front.


Google is working on something so big they had to name it after an entire galaxy: A new operating system that merges Android and Chrome OS into one unified front.

Salad isn't very exciting—and neither is salad dressing. You're either eating rabbit fodder drenched in a too-sour vinaigrette or too-heavy, leaf-wilting dressing like Thousand Island or French.

For me, the smoky brilliance of a good barbecue can't be beat. The way the smoke flavor seems to permeate every part of the meat is, in my opinion, the closest thing we have to food magic. Throw a piece of meat in a smoker with some select wood choices, wait a few hours, and suddenly you have something rich, complex, and bursting with smoky flavors.

Watching an ice cream pro build you a custom frozen treat mixed with your favorite fruit, candy, and/or toppings makes buying a cone even more exciting. But why go out for ice cream when you can create your favorite combinations in your own kitchen? While you might not have an expensive frozen slab for ice cream topping your kitchen counters, you can mimic the creamy consistency and customizable options from Cold Stone Creamery and Marble Slab any time you're craving it. Best of all, you don'...

Pokémon GO, the global augmented reality game that's brought fans out of their homes to catch Pokémon across the planet, has brought about plenty of real-world positives. Unfortunately, when players get power hungry and start taking game hacks too far, we all get a little screwed—both digitally and in real life.

Pokémon GO made waves as the first augmented reality game to gain popular adoption. In fact, it was so popular that it only took a few days to uncover some the benefits and serious issues with combining physical and digital worlds.

Gas stations may be convenient for travel snacks, but the cost of shopping there sure can add up. If you're looking for easy, on-the-go snacks that fit into your travel budget, look no further. We've got 12 kid-friendly, portable food ideas you can make before leaving on your journey. You'll be amazed by how much money and time you will save with these satisfying travel snacks.

Our future technology has a lot of amazing possibilities, and few have more promise than augmented and mixed reality headsets. But these advancements come with several concerns over privacy, and if we don't understand them, we may lose control of our own data without even knowing.

The sweet aroma of cooked fruit filling your kitchen is one of the trademark scents of summer. Yet attaining the perfect consistency for homemade jam can be difficult to master. Often it ends up a watery mess or over-solidifies into thick mystery goo that is destined for the trash, not topping your toast.

With the weather warming up and the days getting longer, fruit salads are starting to appear at backyard BBQs, beach picnics, and pretty much everywhere else. Often these sweet side dishes are unremarkable, with each colorful bowl blending into the next. Luckily, there are easy ways to spice up your fruit salads so that everyone will still be talking about them next summer.

During our high school years, one of us (hint: her name starts with a B) worked at Cold Stone Creamery. She loved working there, and from this love emerged a fascination with adding creative ingredients to plain ol' vanilla ice cream.

When alcohol tastes bad, there's little you can do to save it—or so you think. While it might seem easier to toss your entire bottle of old, opened wine, or to give up and drink crappy vodka anyway, there are creative ways to turn a spoiled or just plain bad boozy beverage into one you actually want to drink.

When you're trying to cut some calories or just eat more veggies, it's important to enjoy what you're eating. If all you're doing is telling yourself "no" and focusing on what you can't eat, you are pretty much destined to fail at your diet.

Whether you're a seasoned wine drinker or just beginning to explore the wondrous world of fermented grapes, finding fantastic wine on a budget isn't as difficult as one may think. With these 8 tips, you'll see how and why you need not shell out $45 to get a great-tasting, high-quality bottle of wine without settling for vino.

Make delicious candy for Easter from the comfort of your kitchen with copycat versions of your favorite classics: Marshmallow Peeps, Cadbury Creme Eggs, Reese's Peanut Butter eggs, Almond Joy bars, and chocolate bunnies. The best part is that you get your sugar fix without the preservatives.

There was lots of new tech to check out at CES 2016, but you could argue that the majority of the big-ticket items weren't the most unique things in the world. Thankfully, there were a few innovative, unconventional ideas on display, and here are some of our favorites.

Unless you like boxed wine, your wine bottles are going to either be sealed with a cork or a screw cap, the latter of which should not be frowned upon, especially if it's white wine. However, most wineries still prefer corks over screw caps, and that means you'll need a corkscrew.

Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operates, I'd like to take this moment to explain the philosophy around the Linux operating system.

Hard as it is to imagine, there are people out there who loathe garlic and onions. Some might have allergies or medical conditions like IBS, or are supertasters (i.e. people who carry a certain gene that makes them extremely sensitive to how certain foods taste). Others might just be picky eaters.

A friend of mine has a crazy amount of Reddit karma and gold, and yesterday he let me in on his secret. This person, who will remain unnamed for obvious reasons, created a Python script called Reddit Karma Crawler that finds rising posts before they get too popular.

If I had to guess, I'd say your waffle maker is probably collecting dust on the highest shelf in your kitchen, or deep in some cabinet you haven't opened in years. And that's assuming you even have a waffle maker.
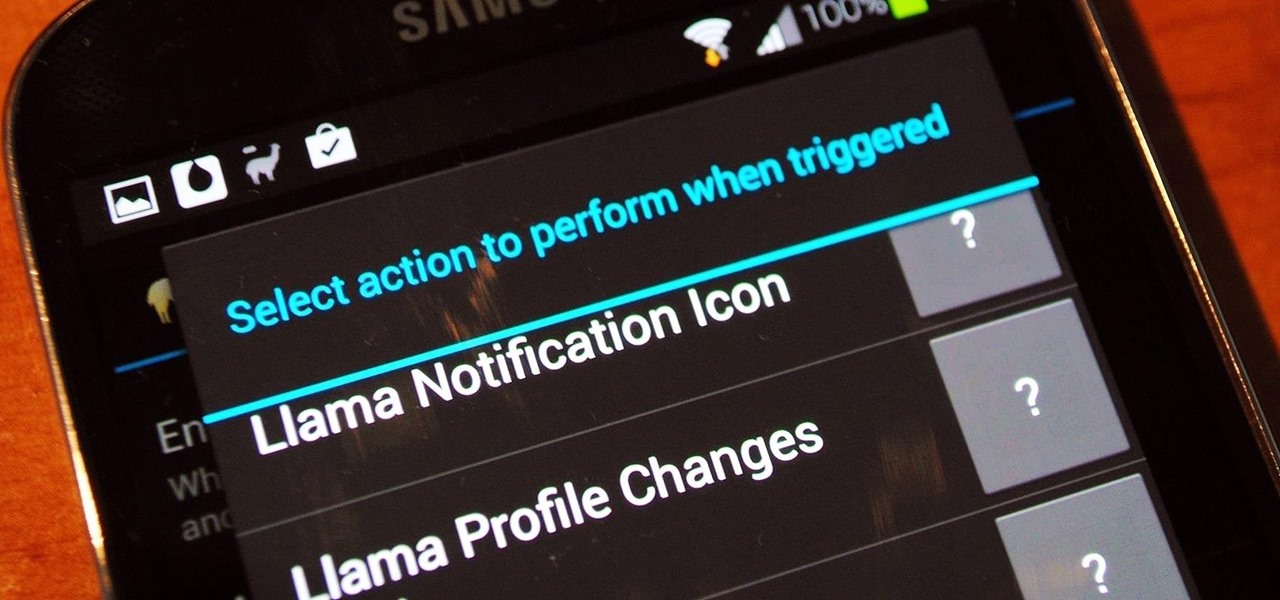
Automation is everywhere in our daily lives. Faucets and hand dryers that turn on for you when they detect your presence. Automated teller machines to handle your bank account. Timed sprinklers to water your lawn every morning. DVRs to record your favorite TV shows when you're not home.

I've never had a black eye, but I was in a car accident that turned my entire ear dark purple a few years ago. Believe me; it was enough to get more than a few funny looks.

At one point in the '90s, about fifty percent of the CDs produced worldwide had an AOL logo. About fifty percent of the CDs in my home still have that AOL promise of 500 free hours on them. Though they never got me to join their internet service, I did get a lifetime supply of coasters. Thanks to the rise of high-speed internet access and bigger and better hard drives, there's no reason for companies to snail mail any more of those obnoxious plastic discs.

Unwanted advertising is everywhere. Annoying pop-up ads, overly loud late night commercials, spam...it never ends. And before spam, there was junk mail. Junk mail is even worse because unlike TV commercials and internet ads, it's physical. You can't just delete or ignore it—and it's an awful waste of paper. So what can you do about it?

If you've never heard of geocaching, it's kind of a grown-up treasure hunt you play everywhere in the world. GPS coordinates are given as clues and the players must find the cache box. There is usually a log book to write your name and a small toy or present to collect.

The augmented reality passthrough abilities of Facebook's Oculus Quest were only fully opened to independent developers recently.
The experience of actually using the HoloLens 2 can be difficult to describe to anyone who hasn't had a chance to directly interact with the device in person and be blown away by its immersive capabilities.

I consider myself a master of emoji, crafting complete sentences and paragraphs using strictly ideograms and smileys. However, everyone seems to have their own interpretation for each little image, so my elaborately clever emoji-only sentences can get lost in translation. But there's an easy way to translate emoji into their exact meaning, as well as decode everyone's mystifying emoji talk.

Can lightning strike twice? Niantic is betting that it can with its latest augmented reality game based on the best-selling multimedia franchise Harry Potter.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Hi everyone. Recently I've been studying some topics about Assembly, memory and exploitation, and thought I could write something nice, easy and fast about it, just because I like to share what I learn, and probably sharing what you learn and trying to explain it to a stranger is the best way to learn it better. It worked for me, and I hope it will be useful for you too.
Some iOS and iPadOS apps offer alternative app icons you can switch between. Beyond that, you'd have to create aliases in the Shortcuts app to customize the look of the app icons on your Home Screen. But that would mean two icons for each app in the App Library. Now, in a new software update, Apple has given us a middle ground for Home Screen icon customization.

What does it mean when a software company obsessively focused on innovating the way we use our mobile devices to see and communicate with the world adds virtual voice agents? Possibly e-commerce magic, with a powerful layer of augmented reality.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.